LMNTRIX Active Defense
Elevating Your Cyber Defense
Reinventing Cyber Defense with First Principles Thinking
At LMNTRIX, we’ve revolutionized cyber defense by embracing a First Principles Thinking approach. By deconstructing the complexities of cybersecurity to their most fundamental truths, we’ve crafted a solution built from the ground up—free from outdated assumptions. Instead of relying on traditional log or SIEM-based methods to build a SOC, we asked ourselves:
“What are the undeniable facts we know to be true?”
From these core truths, we engineered an innovative solution that challenges conventional norms.
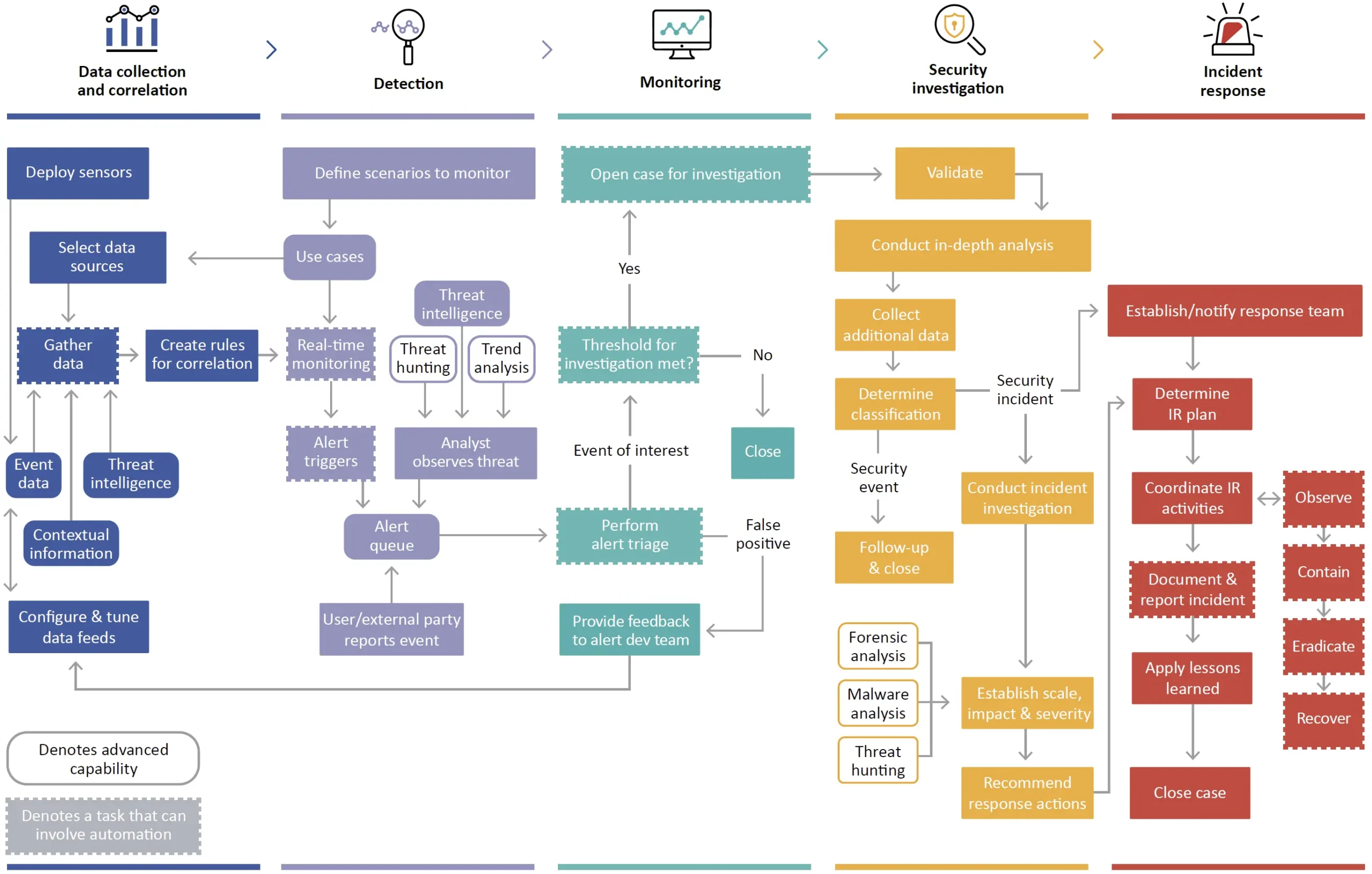
LMNTRIX Active Defense is based on multiple Detective, Responsive, and Predictive capabilities that integrate and share information to build a security protection system that is more adaptive and intelligent than any one element. The constant exchange of intelligence between the XDR components and the broader cybersecurity community enables LMNTRIX to keep abreast of the tactics, techniques, and procedures (TTPs) of the most persistent, well-resourced, and skilled attack groups.

Assuming Breaches to Stay Ahead
A fundamental principle of LMNTRIX Active Defense is the assumption that existing security controls can be easily bypassed. We don’t rely on them for threat detection. Instead, any logs collected from your current security measures are used solely for Digital Forensics and Incident Response (DFIR).
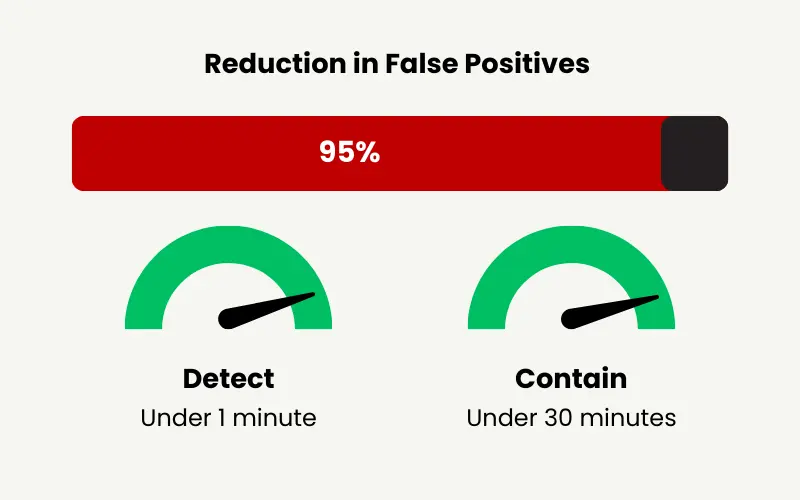
Measurable Risk Reduction

Exceptional Results You Can Trust
We handle the entire Incident Response (IR) lifecycle for you, much of which is automated. Every threat is validated, investigated, contained, and remediated swiftly and effectively.
Measurable Risk Reduction
- – 95% Reduction in False Positives: Focus on real threats without the noise.
- – Rapid Detection and Containment: Over 90% of incidents are detected in under 1 minute and contained within 30 minutes.
Detecting the Undetectable Across All Vectors
We deploy advanced techniques to identify threats that routinely evade traditional security controls across multiple threat vectors—including APT, email, web, network, endpoint, cloud, mobile, and encrypted attacks. Our exclusive focus is on threats that penetrate your defenses, not those that are blocked. Without collecting any logs from your environment, we layer in our own detections. This empowers our platform and team to validate and investigate every single threat that slips past your existing security controls.
Active Defense Strategies for Holistic Cyber Defense
Block The Noise & False Positives
Outer Shell Construction:
Establish a robust perimeter defense to shield your network
Baseline Measures: Implement essential tools like Next-Generations Firewalls(NGFW), Email security and web security
Defense in Depth: Utilize a multi-layered security approach to protect your assets
Post Breach Strategy for Detecting Threats
Comprehensive Coverage:
Monitor email, Web, host, network, cloud, mobile and Operational Technology (OT) environments.
Advanced Detection Tools:
Deploy Intrusion Detection Systems (IDS), Machine Learning Algorithm and encrypted attack detection
Proactive Measures: Utilize bot mitigation, Network Detection and Response (NDR) and Threat Intelligence
Behavioral Analysis:
Implement retrospection, antimalware solutions and advanced behavior analysis to detect anomalies.
Post Breach Strategy for Detecting Threat Actors
Deception Tactics: Use deception technologies to mislead and identify threat actors.
Dynamic Defense: Employ moving target defense strategies to make systems unpredictable.
Identity Protection: Strengthen identity management to prevent unauthorized access.
Lateral Movement Detection: Detect and stop internal movement.
Insider Threat Mitigation: Monitor and manage internal risks.
Post Breach Forensics for Evidence Preservation & IR
Network Forensics: Collect and analyze network metadata to trace attack vectors.
EDR: Implement tools for real-time threat detection and response.
Comprehensive Logging: Maintain detailed logs for forensic analysis and auditing.
Threat Intelligence: Leverage underground intel.
Assume Breach
Active Threat Hunting: Continuously search for and identify threats within your environment.
Proactive Threat Management: Engage in proactive measures to detect and neutralize threats before they cause harm.

Early Detection
- Advanced Threat Detection: Utilizing our proprietary LMNTRIX XDR platform, we monitor all network activity in real-time. Our advanced analytics and machine learning algorithms identify anomalies and potential threats before they can cause damage.
- Comprehensive Visibility: We provide a 360-degree view of your network environment, integrating data from multiple sources to ensure no threat goes unnoticed.
Proactive Engagement
- Threat Hunting: Our expert threat hunters actively seek out potential threats within your network. By continuously hunting for indicators of compromise, we can identify and mitigate risks before they escalate.
- Deception Technologies: We deploy decoys and honeypots to lure attackers away from critical assets. These deceptive measures not only divert threats but also provide valuable intelligence on attacker tactics and techniques.


Rapid Response
- Automated Incident Response: Our automated response capabilities ensure swift action against detected threats. Predefined playbooks and workfl ows enable us to contain and remediate incidents with minimal impact on your operations.
- Expert Intervention: When a threat requires human intervention, our team of experienced cybersecurity professionals is ready to step in. We provide 24/7 support to manage and resolve incidents effectively.
Intelligence-Driven Defense
- Threat Intelligence Integration: We leverage global threat intelligence to stay ahead of emerging threats. By integrating real-time threat data into our defense strategy, we ensure our clients are protected against the latest attack vectors.
- Continuous Improvement: Our approach to Active Def ense is dynamic. We continuously refine our tactics, techniques, and procedures based on the latest threat intelligence and attack trends.

Why Choose LMNTRIX for Active Defense?

Holistic Security Approach
We go beyond traditional cybersecurity measures by incorporating advanced technologies and proactive strategies.

Proven Expertise

Cutting-Edge Technology

Tailored Solutions



