HOW WE DO IT
- PEOPLE -
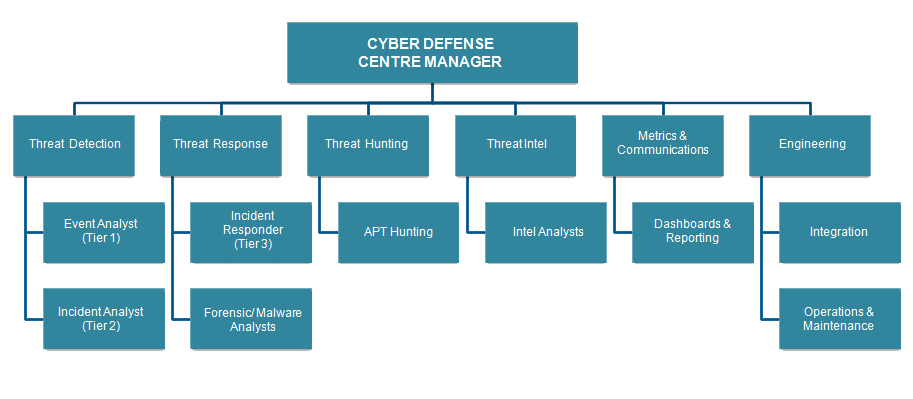
People are the most important aspect of LMNTRIX. It’s a cliché in virtually all areas of business, but it’s true.
In cyber defense one good analyst can do the job of 100 mediocre ones and so at LMNTRIX the quality
of our intrusion analysts is vastly more important than analyst quantity.
Moreover, while analysts can be trained to use a tool in a rudimentary manner, they cannot be trained in the mind-set or critical thinking skills needed to master the tool. As such at LMNTRIX we exercise great care in hiring and retaining our intrusion analysts.
A typical intrusion analyst at LMNTRIX is skilled in software development, scripting, ethical hacking, forensics, incident response, malware & threat analysis, reverse engineering, threat intelligence, PCAP analysis, network security and possesses multiple GIAC certifications.
possesses deep experience in IT, offense & defense
out-of-the-box thinking like the adversary
our mission and our customers networks
credibility, strong customer connections
Quality not Quantity