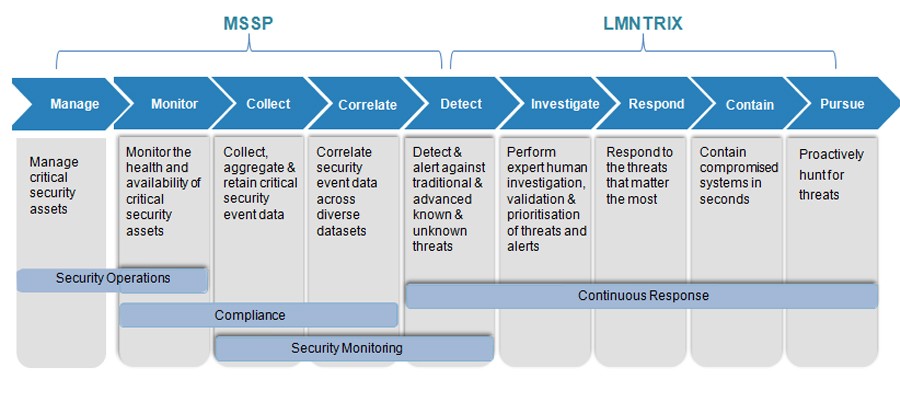
LMNTRIX® VS MSSP
The MSS model was conceived in the late 90’s and not much has changed since then in the way MSSP’s manage and monitor customer networks. During this same time period, the way attackers work to target, compromise, and exploit organizations has changed significantly – in favor of the adversary. LMNTRIX was borne as a necessity to help close the gap left in the market from the traditional MSSP model.
Gartner’s definition of Managed Detection and Response (MDR) services best characterises the business that LMNTRIX is in:
A focus on threat detection use cases, especially advanced or targeted attacks that have bypassed existing perimeter controls (e.g., next-generation firewalls [NGFWs], secure web gateways [SWGs], network intrusion detection systems [NIDSs], endpoint security). Compliance use cases are not a focus and commonly not addressed at all.
Delivery of services usually using a vendor-provided stack of network- and host-based controls (e.g., commercial, open source or provider-developed). These tools are not only positioned at the traditional internet gateways, but are also inward-facing to detect the threats not typically discovered by traditional perimeter security technologies.
These tools, where deployed, are managed and monitored by the provider to improve an organization’s ability to detect threats. The types of tools and detection methods used by the providers vary in the use of logs, network flows and traffic, and endpoint activity. For example, some vendors rely solely on network security monitoring while others only on endpoint agents to generate logs or detect threats, and others rely solely on the logs generated by a customer’s existing security tools.
Security event management and analysis technology that utilizes threat intelligence and advanced data analytics is commonly, but not exclusively, at the core of these services. It is fed events from the stack of vendor-supplied controls, customer log and event sources, or some combination of the three.
24/7 monitoring, analysis and customer alerting of security events with preliminary triage performed by a person (e.g., not relying just on automation to add some context to an event).
Incident validation and remote response services, such as hunting for additional hits on indicators of compromise (IOCs), reverse malware engineering, and consulting on containment and remediation are included in the service, without the need for an incident response (IR)-specific retainer or agreement. Retainers are reserved for onsite breach response services. Assistance with remediation actions in bringing the environment back to some form of “known good” is sometimes included or available as an additional service.
The following table provides details of the major differences between the approach an MSSP takes compared to the approach used by LMNTRIX:


