LMNTRIX® RESPOND
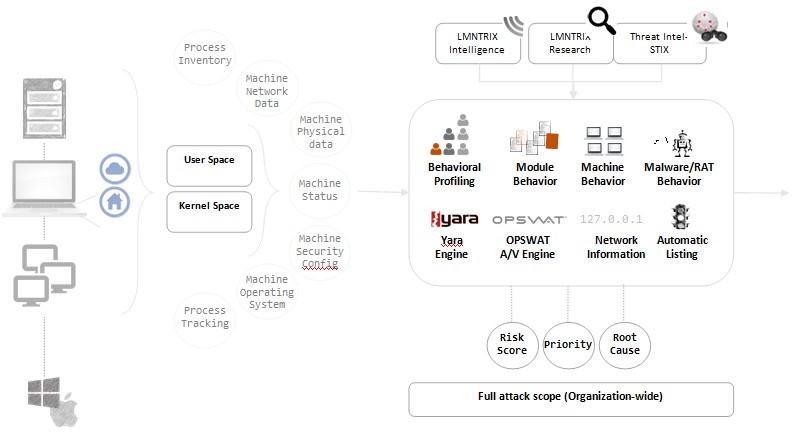
The LMNTRIX Respond service is a comprehensive solution combining NGAV+EDR, utilizing a lightweight custom agent deployed on all your endpoints. This agent captures detailed state information to prevent a range of threats, including exploits, malware, file-less attacks, phishing, injection, macro-based attacks, ransomware, credential theft, and adversary tradecraft. Additionally, our Cyber Defense Center employs it to continuously monitor all endpoint activities, conduct adversary hunting, validate breaches, and investigate, contain, remediate, and detect encrypted attacks. The inclusion of Managed Detection Response (MDR) enhances our capabilities in proactive threat detection and response. Using a lightweight sensor allows our intrusion analysts to delve deep into the inner workings of endpoints and expose anomalous behaviors.
Our techniques encompass live memory analysis, direct physical disk inspection, network traffic analysis, and endpoint state assessment. In the realm of EDR cyber security, our service distinguishes itself by not relying on signatures or rules. Instead, through the utilization of unique endpoint behavioral monitoring and advanced machine learning, we delve deeper into endpoints. This approach enables us to more effectively analyze and identify zero-days and hidden threats that other endpoint security solutions might entirely miss.
Armed with this information, our intrusion analysts employing active defense cybersecurity instantly identify similarly infected endpoints and rapidly expand their visibility into the full scope of a compromise. Once an intrusion is confirmed, we proactively disrupt malware-driven tactics, techniques, and procedures (TTPs), actively limiting attacker lateral movement by quarantining and blocking the threat
Detection
Response Time
endpoint sensor
Response.
Hunting.
Validation.