ACTIVE DEFENSE in ACTION
Let’s use a real-world example to show how Active Defense stacks up. Deep Panda, or Shell Crew, continues to be a formidable threat group, actively attacking organizations and stealing data. Deep Panda is a prime example of an advanced persistent threat that is able to breach networks and then remain inside enterprises for years before detection.
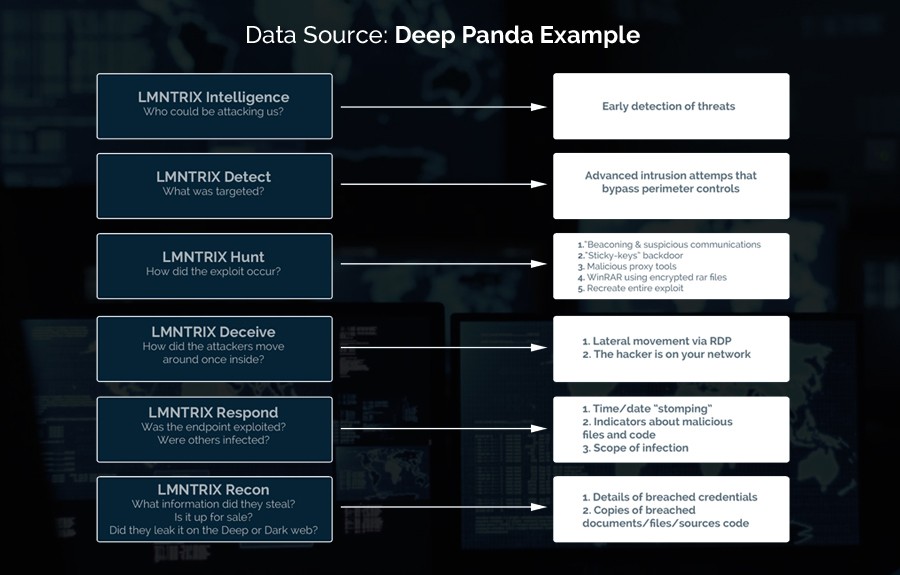
The following diagram uses the Deep Panda threat profile to show how each element of the LMNTRIX Active Defense works together to deliver unmatched threat detection and response.
In the security community, Deep Panda/Shell Crew is also known as WebMasters, KungFu Kittens, SportsFans, and Pink Panther. Intelligence from RSA has found that Deep Panda’s general tactics, techniques, and procedures (TTPs) include;
● Prevalent use of Web shells to maintain low level persistence in spite of determined remediation efforts;
● Occasional use of Web application framework exploits to achieve initial entry as opposed to traditional spearfishing attempts;
● Lateral movement using compromised credentials with RDP, psexec, or network connections in conjunction with scheduling jobs with the “at” command;
● Abuse of Code Signing infrastructure to validly sign custom backdoor malware;
● Exploiting systems using different SETHC.exe methods accessible via Remote Desktop Protocol (RDP);
● Long history of IP/DNS telemetry allowing for historical research and link analysis;
● Placement of malicious proxy tools introduced into the environment on Windows server based proxies to bypass proxy logging;
● Extensive use of time/date stomping of malicious files to hinder forensic analysis; and
● Malware leveraging compromised credentials to bypass authentication NTLM proxies (proxy aware).
● Exploit known Web vulnerabilities
● Upload web shell and other tools
● Move laterally using Pass the Hash and other tools/techniques to gain Admin credentials
● Further Entrenchment using webshell, remote access, customized malware, etc to ensure persistence
● Stay undetected and Access Trade Secrets
● StickyKeys is an accessibility feature to aid handicapped users on Windows computers.
● StickyKeys is activated by pressing the shift key five times in sequence.
● Works on networks where the systems have Microsoft Remote Desktop Protocol (RDP) enabled.
● Attackers exploit this vulnerability


