
Jaff ransomware was first discovered around spring of 2017, but it was largely neglected by the security community as that was the same time that WannaCry was the lead story covered by the press. Since then Jaff ransomware has lurked in the shadows while infecting machines worldwide. In this LMNTRIX Labs analysis, we will look into some of the common ransomware techniques used by this malware, and how it represents the ransomware’s infection routine in general.
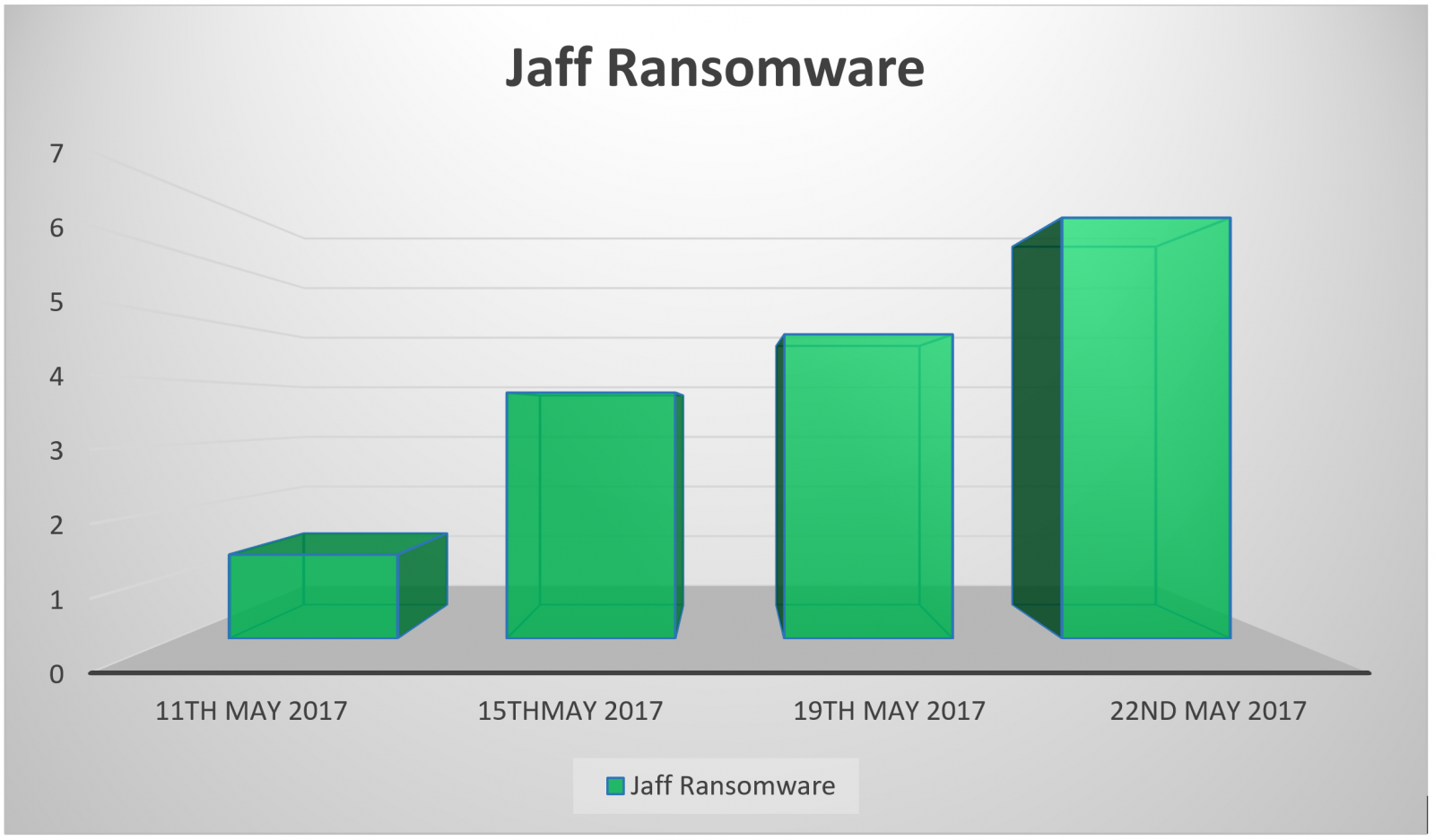
Jaff Ransomware is another. It first appeared on May 11, 2017 – one day before WC. Since then, we have seen its appearance steadily increase, reaching a peak on May 22, 2017. As illustrated in the graphic below.
Our sample is based on the Malspam Campaign targeting our global network of customers.
Delivery:-
There’s no points for creativity here so I won’t dwell on the delivery method too long. This Jaff ransomware campaign is using MalSpam with a malicious attachment.
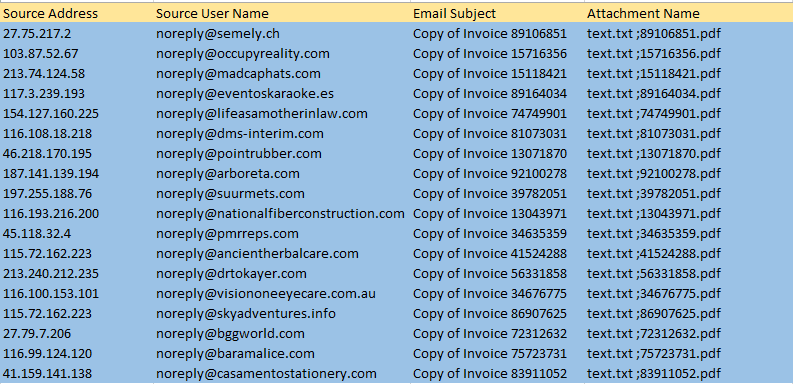
Our samples show the chosen subject line as “Copy of Invoice” followed by, “The sender email address is spoofed”.
An example of the spoofed emails used to target our clients is listed below:-
Dropper Analysis:-
This analysis is of a PDF attachment:
Filename: 17897740.PDF
MD5: e2b9ffb93c982e05238a30af016a2eed
A list of malicious embedded objects were trigged upon execution:
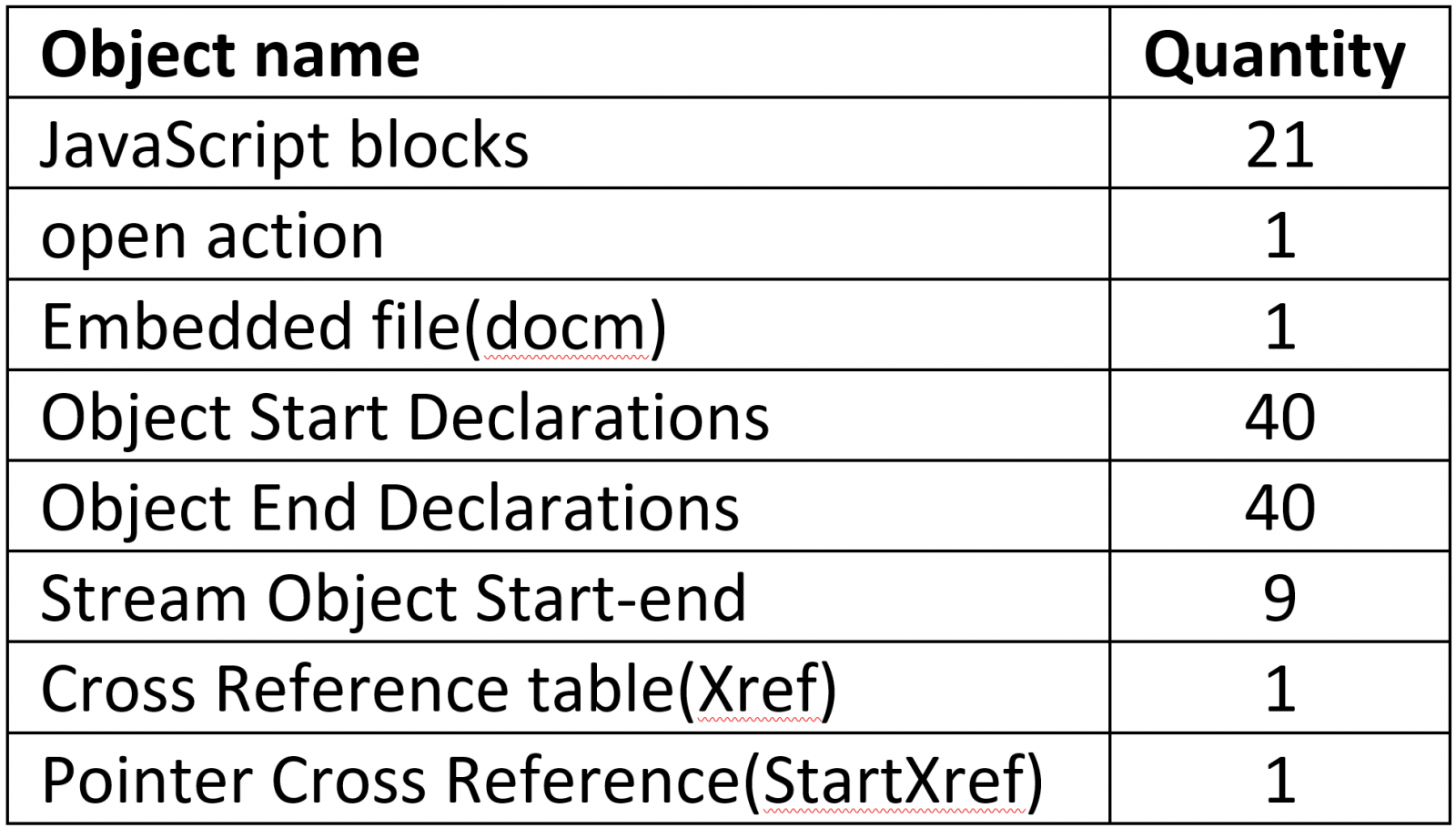
In the above sample, the combination of automatic actions and embedded JavaScript is an immediate red flag.
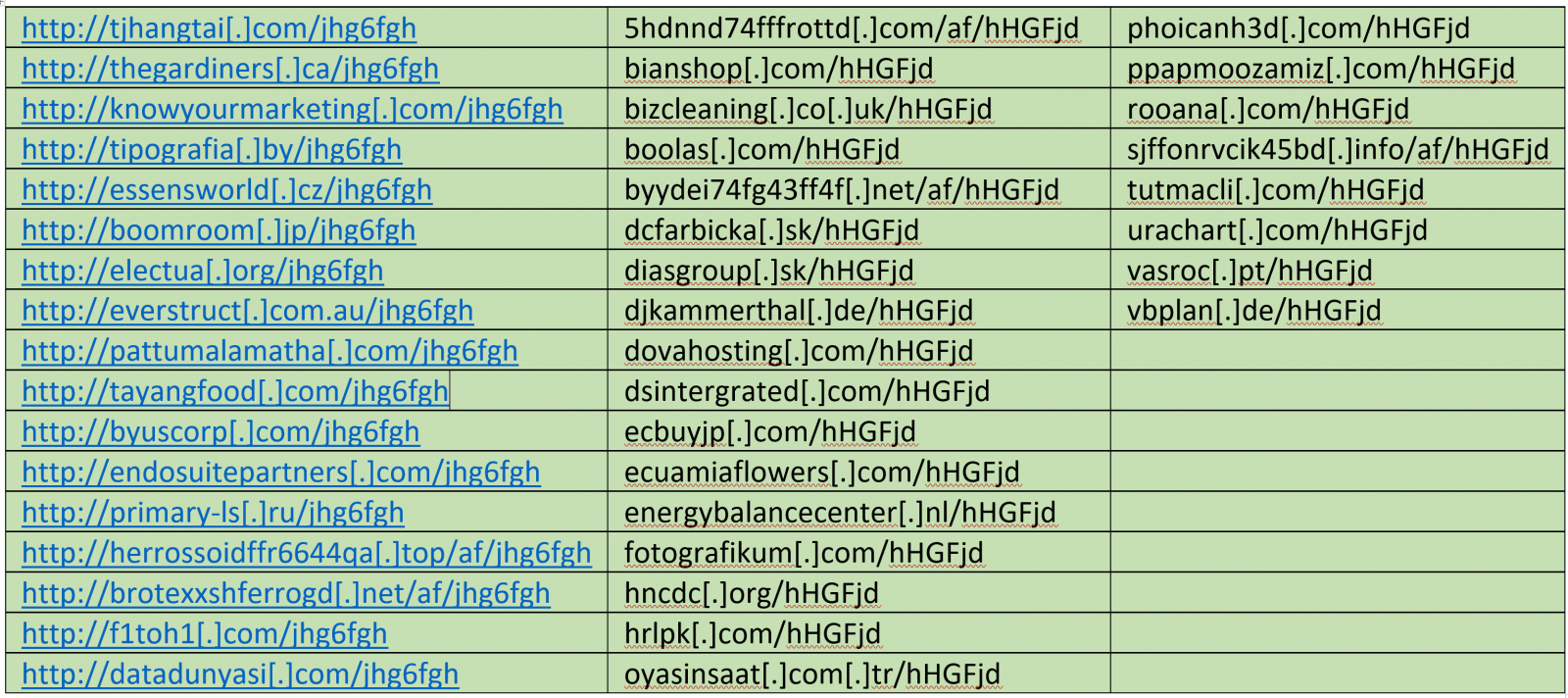
Upon execution, the file’s primary drop is a macro file named ’QDLCPQkk.docm’. This file has been hardcoded with a number of Command and Control (C&C) domains which download an encrypted text file.
Below is a list of (C&C) URLs found on the macro.
Indicator of Compromise:-
Once downloaded, the encrypted file is being converted to the Windows PE executable. In the recent campaigns, we have identified the following Windows PE file after conversion.
Filename: buzinat8.exe
Md5: 132d56f533f3a074b441cebff98e7742
This is the original ransomware payload that injects number of “.dll” files, making source API call to ‘\ThemeApiport”. A DNS request follows, in turn making a HTTP/GET request to the following domain:-
trollitrancessions.net IP address: 217.29.63.199
Now is the Windows Directory’s turn::-
“buzinat8.exe” touched file “%WINDIR%\DtcInstall.log.jaff”
“buzinat8.exe” touched file “%WINDIR%\HomePremium.xml.jaff”
“buzinat8.exe” touched file “%WINDIR%\IE10_main.log.jaff”
“buzinat8.exe” touched file “%WINDIR%\IE11_main.log.jaff”
“buzinat8.exe” touched file “%WINDIR%\PFRO.log.jaff”
“buzinat8.exe” touched file “%WINDIR%\setupact.log.jaff”
“buzinat8.exe” touched file “%WINDIR%\setuperr.log.jaff”
“buzinat8.exe” touched file “%WINDIR%\Starter.xml.jaff”
A number of files are encrypted with “.Jaff” extensions, ultimately revealing the below ransom message on the listed Onion URLs.
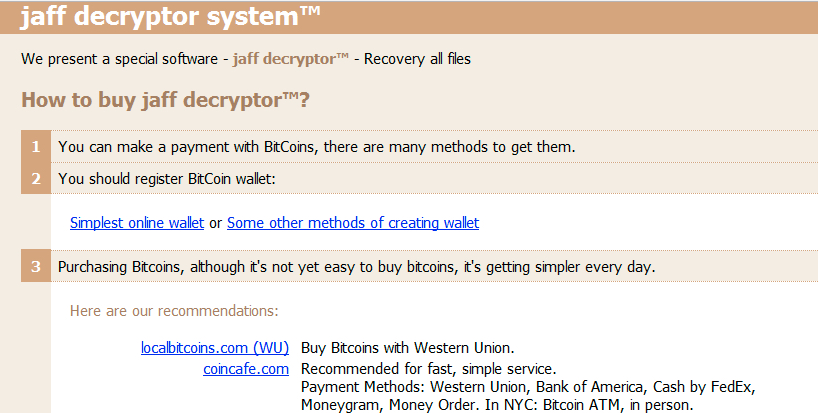
It seems since March we’ve witnessed a new ransomware iteration almost every month.
These attacks are clearly successful. It is safe to assume these attacks will continue to increase in sophistication and scope, and that the next ‘NHS’ attack is around the corner.


