Today we’re going to look at the ‘forward scout’ of the cybercrime world – the exploit kit. An exploit kit is a software package – usually bundled together with various pieces of ransomware and sold on the dark web. It is designed to first find vulnerabilities on a machine before exploiting them.
There is an entire ecosystem of various exploit kits, but today we’ll focus on RIG because there’s been some exciting recent developments with this variant.
Recently: In late March this year, 40,000 illegal subdomains were taken down in a joint effort between hosting provider GoDaddy, RSA, and a team of other security firms.
These malicious subdomains were created after domain owners’ credentials were stolen in a process known as ‘domain shadowing’. After being set up, the subdomains acted as ‘gates’, redirecting victims to IP addresses—mostly in Eastern Europe—hosting the exploit kit.
RIG was one of the primary exploit kits affected in the takedown, as can be seen in the below graph from Palo Alto:
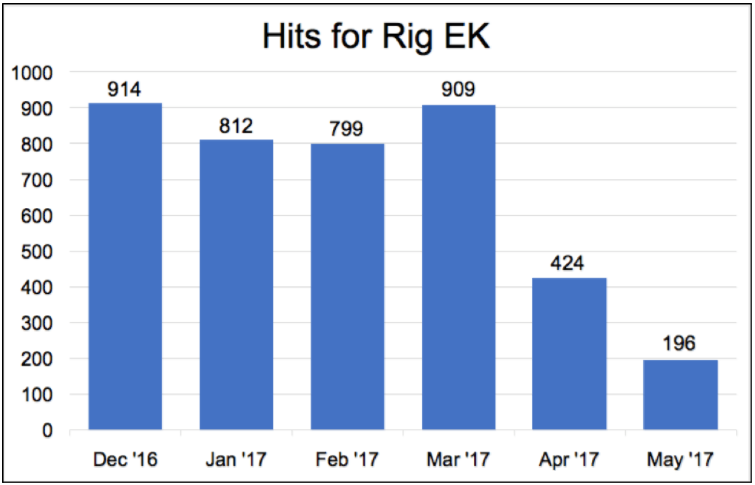
Note the steep decline after the March subdomain takedown.
Despite the effort’s obvious success, researchers warn that it will be impossible to completely eradicate RIG’s illegal subdomains.
Propagation:
To understand the RIG exploit kit, we first have to look at how it spreads. The diagram below illustrates this:
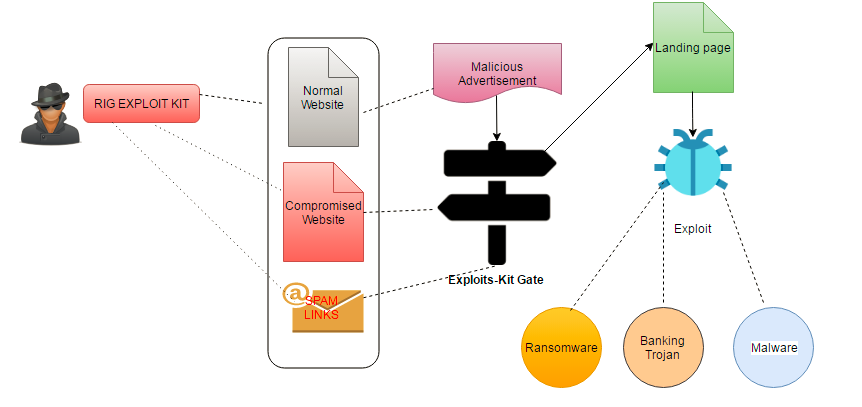
RIG is known to use malvertising redirection to hijack legitimate traffic (normal website) and send it to the exploit kit gateway. Similarly, malicious URLs/shadow domains (compromised website) and spam (spam links) also send traffic to gateway. Once here, traffic is then redirected to the landing page where the relevant malware, based on the victim’s specific vulnerabilities, is identified and executed. We’ll look at this in further depth later.
Technically:
The reason the takedown had such a drastic effect is that despite also using malvertising and spam to propagate, shadow domains were RIG’s primary traffic redirection method. That said, let’s take a closer at how RIG channels traffic.
The below code is the LoadURL function which is invoked for driving the traffic to the landing page:
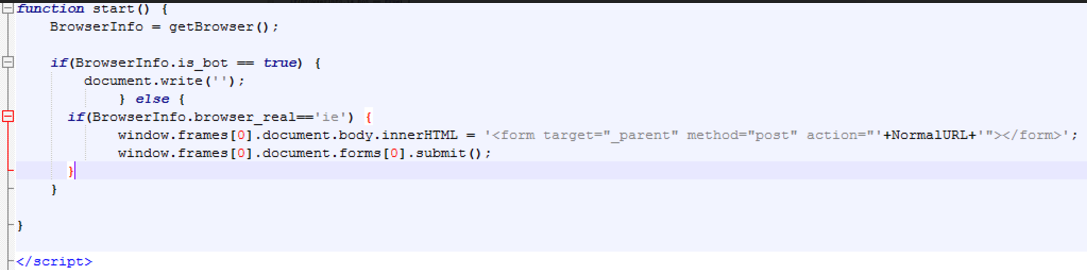
Next, the exploit checks which browser the victim uses:
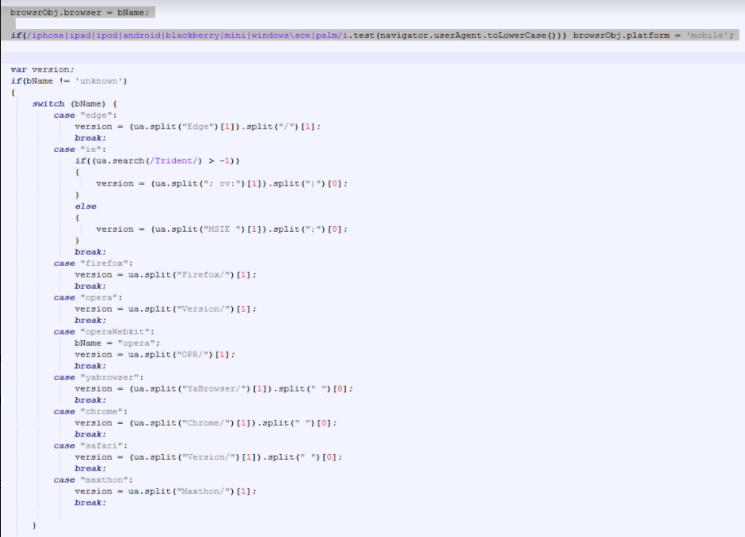
Once the browser check is complete, the URL redirector is invoked to send traffic to the exploit landing page:
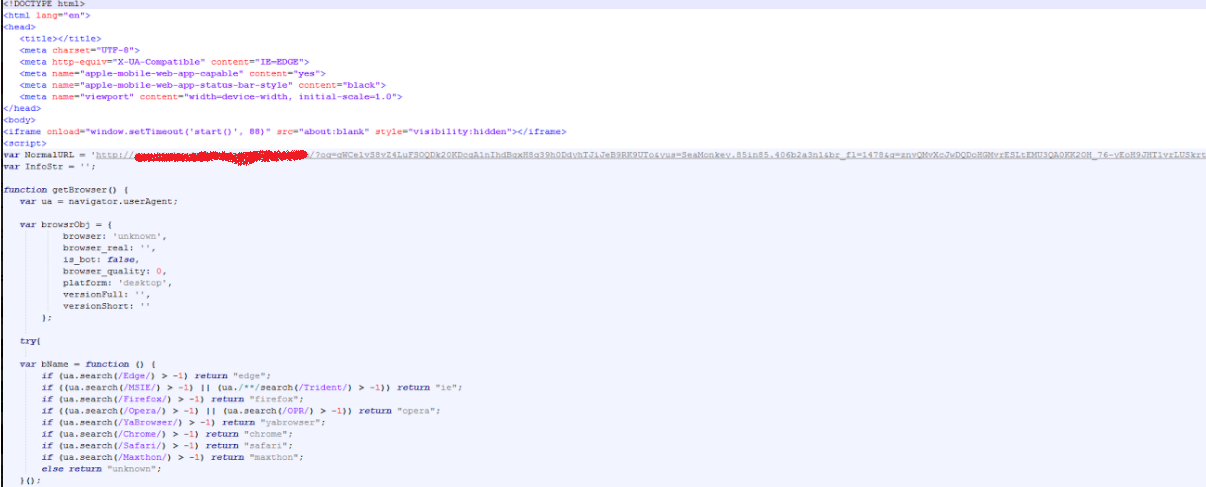
As mentioned earlier, the landing page is where the actual exploit is loaded onto the victim’s machine. One such Flash vulnerability scenario is outlined below:

Parameter ‘param name=FlashVars’ is followed by an obfuscated value. The object type on which the exploit is applicable can be seen in the highlighted object type, ‘application/x-shockwave-flash’.
We also looked into the major malware and ransomware variants RIG has dropped onto victim machines and found:
• DreamBot
• Philadelphia Ransomware
• Locky ransomware
• Cerber
• Nemucod
• Cryptomix
• Matrix Ransomware
• Zloader
Prevalence:
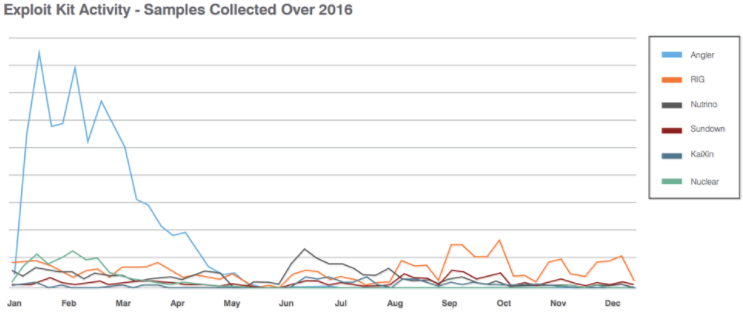
The below graph from Proofpoint shows RIG’s popularity throughout 2016: