Although cyber security and hacking are both relatively new fields, there are still certain tactics we’d consider ‘old school’.
Malicious macros are one of them.
For those unfamiliar with the term, macros enable a user to group together a series of tasks into a single command. This allows you to automate repetitive tasks.
Macro becomes ‘malicious’ when an attacker preloads a series of commands onto a word document and convinces a victim (most often via phishing email) to open the document and enable macros. The commands loaded onto the document then execute.
Once such an attack has a hold of a computer, it then downloads additional malware – typically a credential stealer or ransomware.
While there are numerous attacks that use malicious macros, we’ll focus on the infamous Hancitor downloader due to its recent resurgence.
Recently: In May this year, customers of electronic document vendor DocuSign, were targeted in a Hancitor-slinging phishing campaign after attackers successfully pilfered an undisclosed number of email addresses from the company.
Customers were then sent emails, highly crafted to look as though they were sent from DocuSign, asking them to follow a link to a word document which had Hancitor waiting within the macros.
This attack was particularly interesting as attackers updated their phishing emails halfway through the campaign after DocuSign sent a PSA to its customers.
Prevalence: Following a lull last year, New Year’s Day 2017 brought with it an increase in the number of campaigns deploying Hancitor.
This revival began in January, when researchers from the SANS Internet Storm Center first started tracking an uptick in Hancitor spam.
Technically: While malicious macros have been around for a while, it is worth unpacking how these attacks work because they are a quintessential cyber attacker tool. Plus this latest sample comes with an interesting tweak which I’ll touch on shortly.
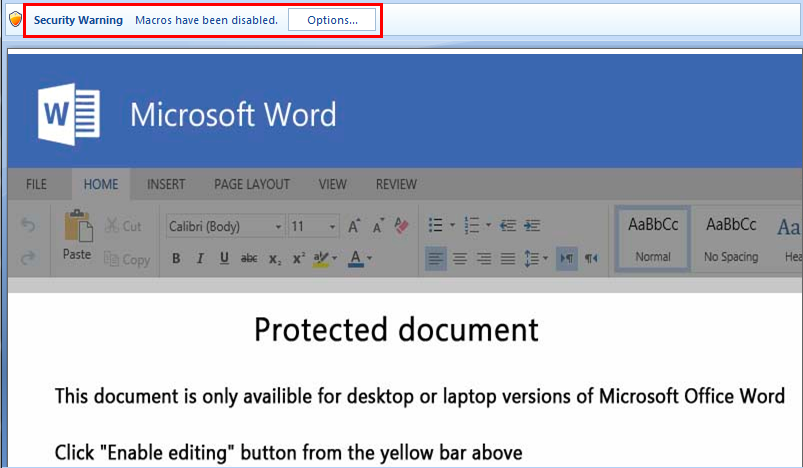
First though, as mentioned earlier, Hancitor kicks into life when a malicious document is opened, and macro is enabled as displayed below:
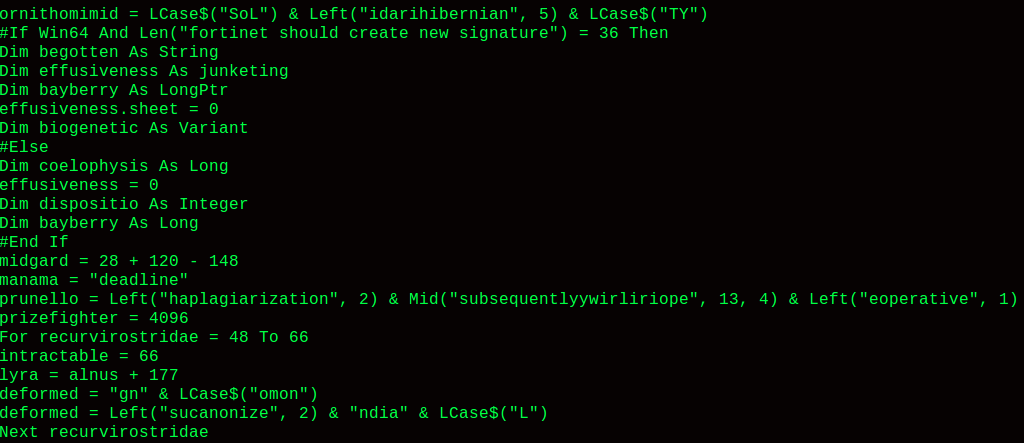
One of our first steps was to try read the macro code, but it was highly obfuscated:
Once executed, the shellcode within the macros launches “explorer.exe” as a sub-process through code injection:

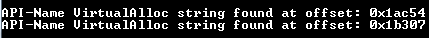
For every instance of shellcode executed, memory must be allocated. ”VirtualAlloc” is a Windows API used to administer memory allocation.
The sample’s embedded shellcode queries for this VirtualAlloc API, as shown below:
Simultaneously, the document macros also search for a string called STARFALL. This string loads malware from the shellcode and injects it into explorer.exe, as shown in the screenshot below:

If successful, these steps create a backdoor, allowing any malicious software to be installed on to the machine.
In the DocuSign attack, for example, the payload was primarily credential-stealing malware like Pony and Evil Pony.
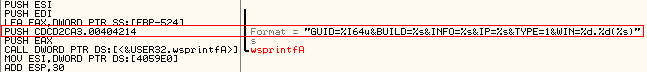
In a new twist for Hancitor, we witnessed our sample (MD5: CDCD2CA36ED9A2B060DD4147BC5F7706) steal network credentials itself by targeting the system’s unique GUID. Previous iterations didn’t contain this feature.
In Windows 7, user credentials are stored in multiple files with random names (generated using GUID) inside both APPDATA and LOCALAPPDATA locations.
Based on the type of password and application, one of these locations is chosen to store the corresponding credential file. For example, Windows Live Messenger and Remote Desktop login passwords are stored at LOCALAPPDATA.
The unique GUID below helps Hancitor decrypt the credentials:
Additional analysis:
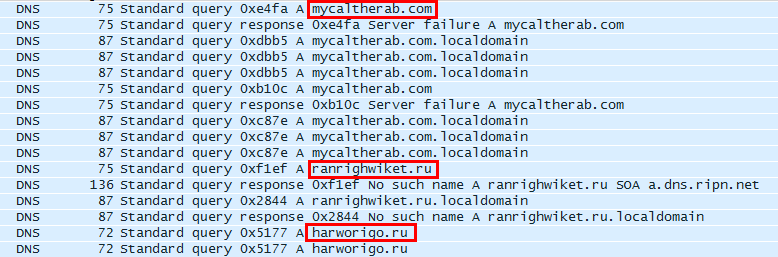
During our analysis, we saw Hancitor call out to the below Command and Control (C2) Servers:
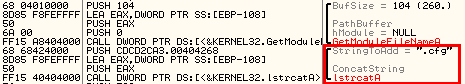
Interestingly, we also found a command which can update the list of C2 servers. The updated list is encrypted and written to a file with extension “.cfg”:
The reason these cyber-attack methods always return after falling out of favour is because they’re successful. I don’t know how many times the security industry will have to shout ‘don’t open suspicious emails’ until the message gets through… if my mother’s predilection for opening clearly malicious emails is anything to go by, we’ll be shouting for some time.


