This PDF file was received in a suspicious email from an unknown sender:
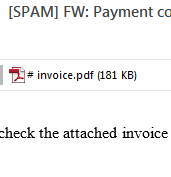
When we checked the hash value of the file on the Virus Total website to determine whether it had been flagged as malicious, the file was present, but it’s detection rate was 0/56. Here is that link. We have continued to monitor and as of the latest analysis, the detection rate had increased to only 15/56 with many of the leading antivirus tools failing to detect.
We have dissected the file to look for any malicious content inside.
Static Analysis:
We found the following suspicious code:
<<
/Type /Action
/S /URI
/URI (https:
/ /bit.ly
/2p9sWKu )
>>
/StructParent 0>
Note the link: bit(.)ly /2p9sWKu (short url)
Expanded URL: hxxp://democrats(.)ge/images/stories/august/documents(.)php
Dynamic Analysis:
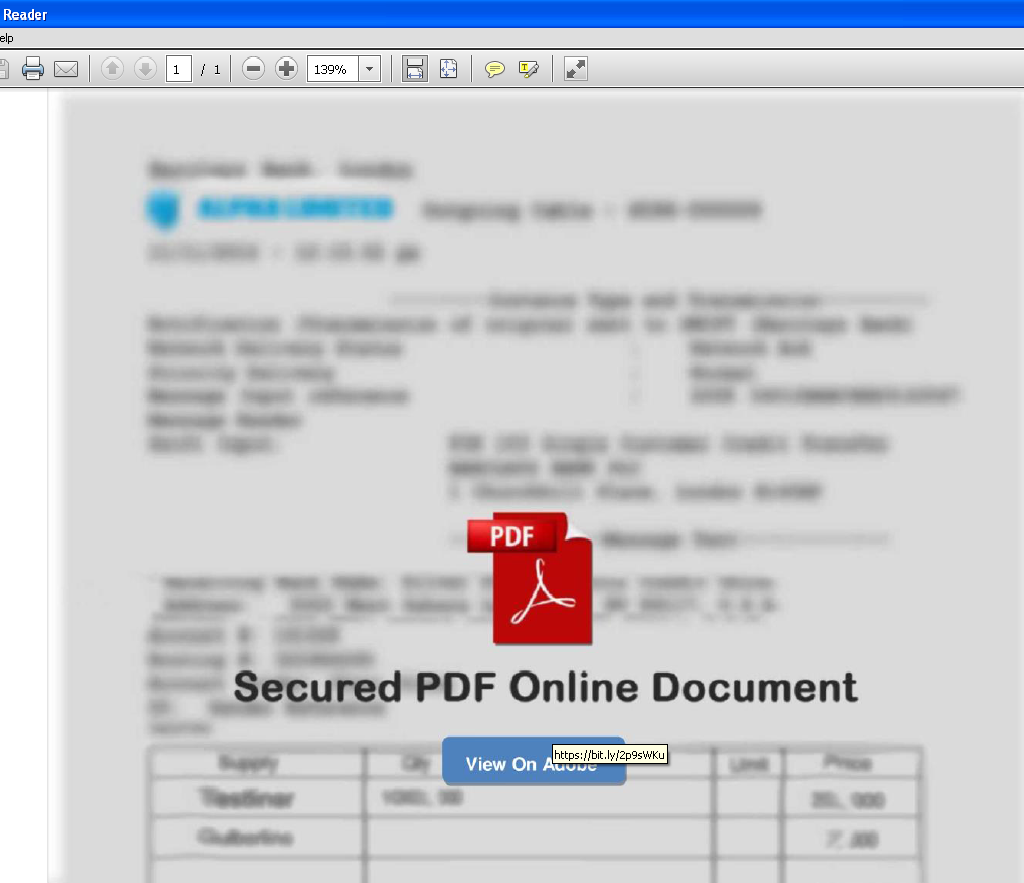
When we executed the suspicious PDF file, a message reads that it is a “Secured PDF Online Document” which can be viewed on the Adobe site. The same shortened URL is found to be the online site here.
Website and Code Analysis:
The Virus Total result of the above URL identifies that it is malicious and a phishing site. See that link here.
We visited the site and downloaded that php code for analysis. It was heavily obfuscated.
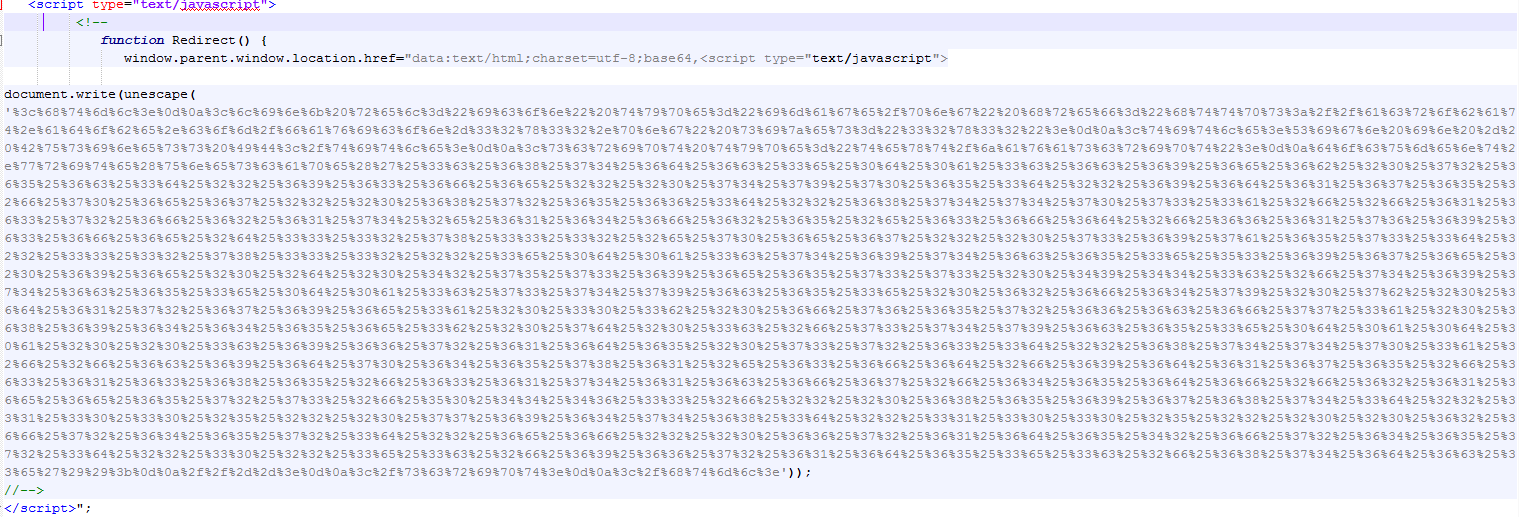
So, we de-obfuscated the code and found the following code.
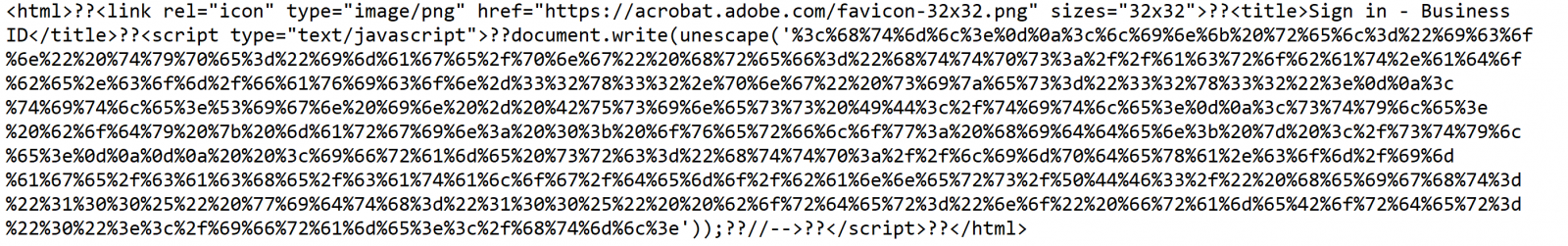
When we de-obfuscated it a second time, we found the following:
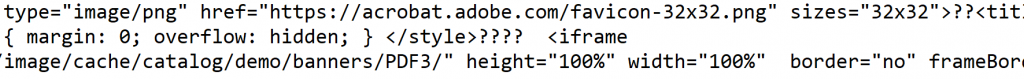
This is an iframe injection. We checked that site hxxp://limpdexa(.)com
Virus Total also identifies it as a malware site. See that link here.
This is also flagged as a malicious website: https://urlscan.io/result/2077850e-e12a-4e75-a598-a2374ffcffb3#summary (a malicious site according to Google safe browsing).
A screenshot of a similar landing page.
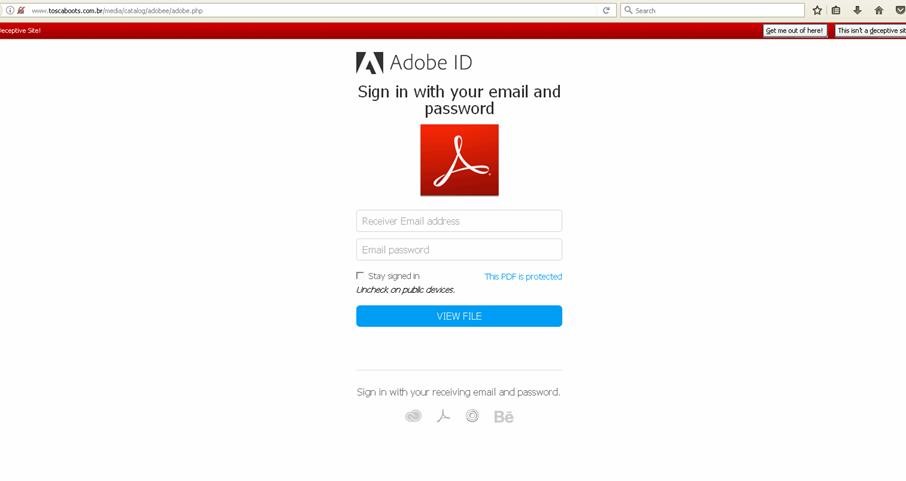
Conclusion:
We believe this is a phishing, password stealer using Adobe as the main vector, and one that is not being universally identified as can be seen by the ongoing lag in detection as reported by Virus Total.


