
Ransomware has been hitting the headlines lately and the latest variant to make the rounds has been dubbed ‘Dcry’. This strain is interesting as it encrypts data with .qwqd extensions and propagates through fake software updates which exploit software vulnerabilities to infect the target system.
Let’s take a closer look:
File details
| Dcry.exe | |
| File type | PE (portable executable) file |
| Md5 hash | 4067933609a560b044fd43800f37c627 |
| SHA1 hash | b06e25ff233ecbefe5266e97651d63a507578932 |
Static Analysis
The first thing static analysis showed us was that Dcry has a suspicious entry point:

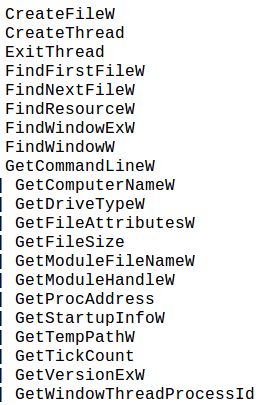
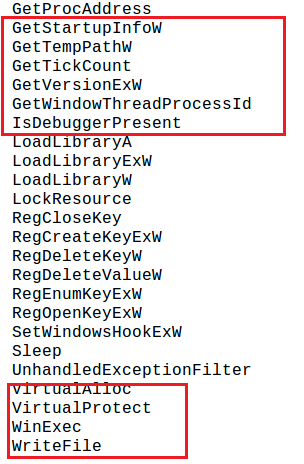
A number of Import Address Table alerts then scan the system for computer name, startup information, %TEMP% directory, debuggers and the presence of a virtual machine, etc.
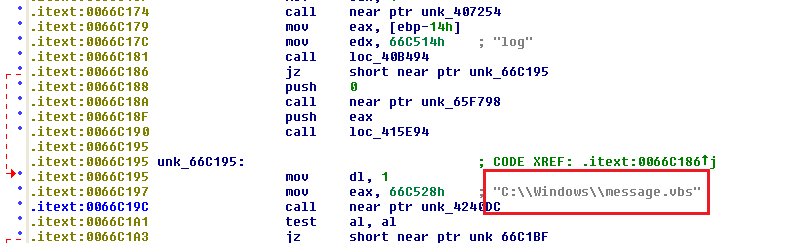
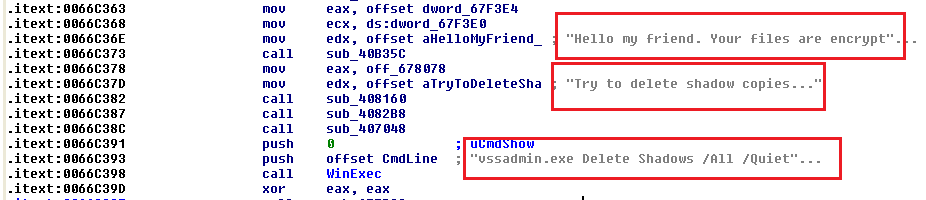
Having completed this process, the malware then drops a “message.vbs” file:
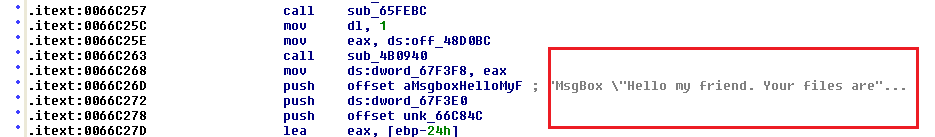
Below, we can see this contains the ‘ransom letter’:
Now the encryptions begins via .qwqd extensions and the execution of a .vbs file:
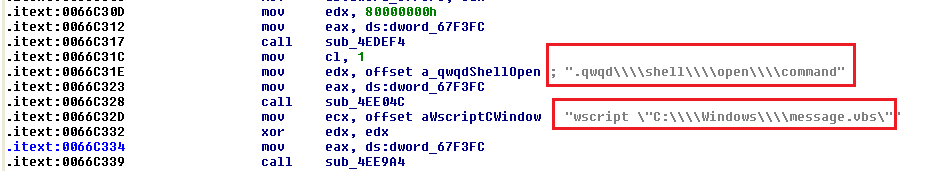
After performing the encryption, Dcry attempts to delete the volume shadow copies present in the victim’s machine:
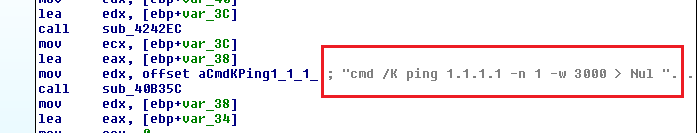
And then it initiates a ping request:
Dynamic Analysis
Executing the sample gives us a prompt with a key and a value number:
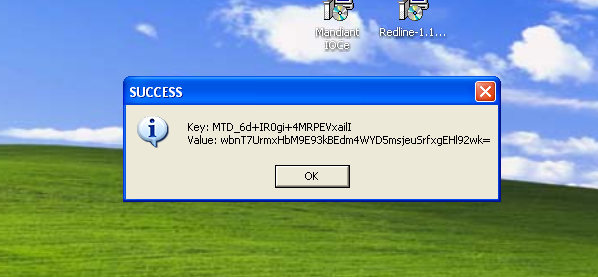
When we press ‘ok’ it executes and, as seen below, it doesn’t have a valid signature:
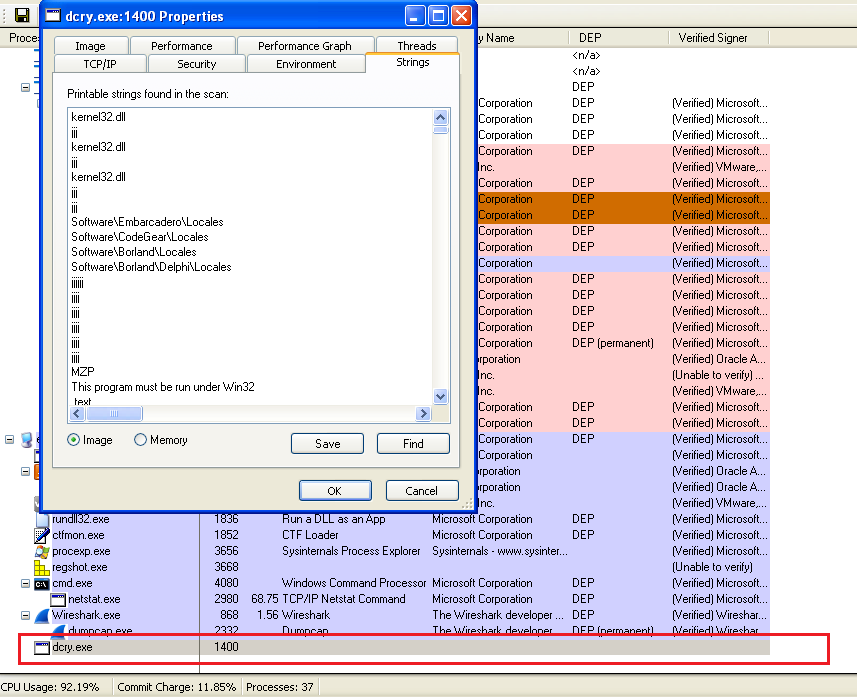
A .vbs file is dropped into the user’s system after which the encryption process starts:
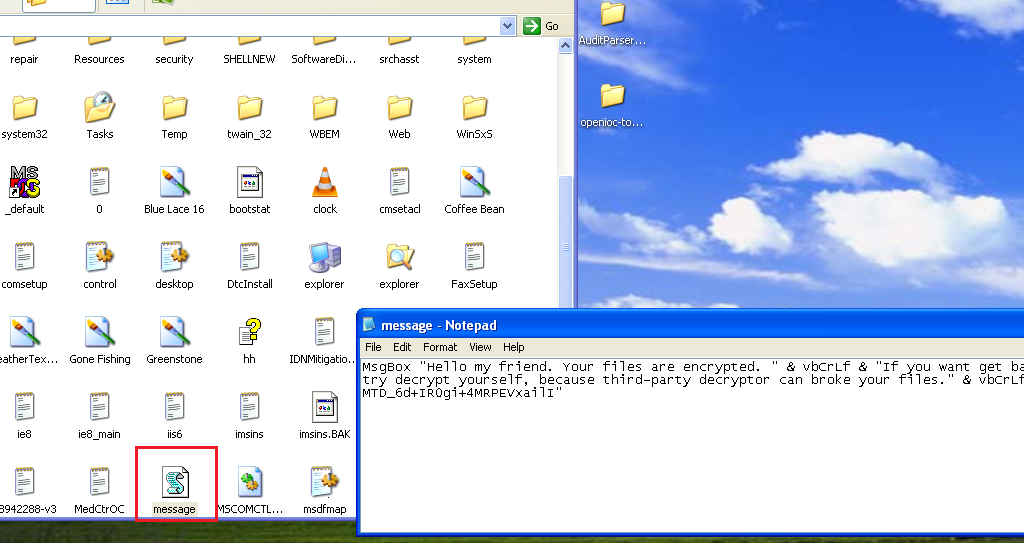
Next, the ransomware message is displayed:
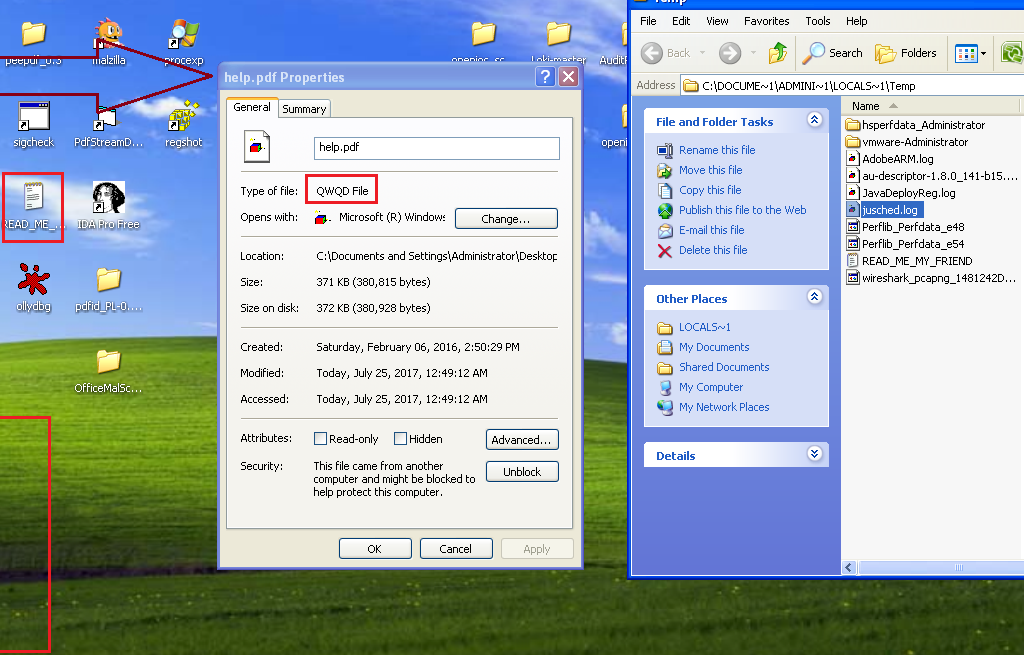
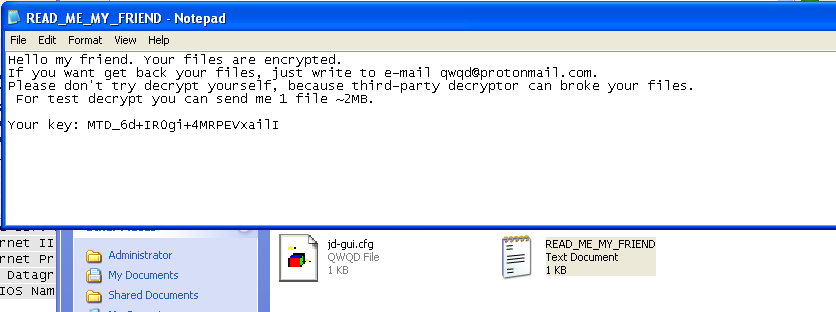
As a result, the following files were dropped onto the user’s system, all files were encrypted with .qwqd extensions:
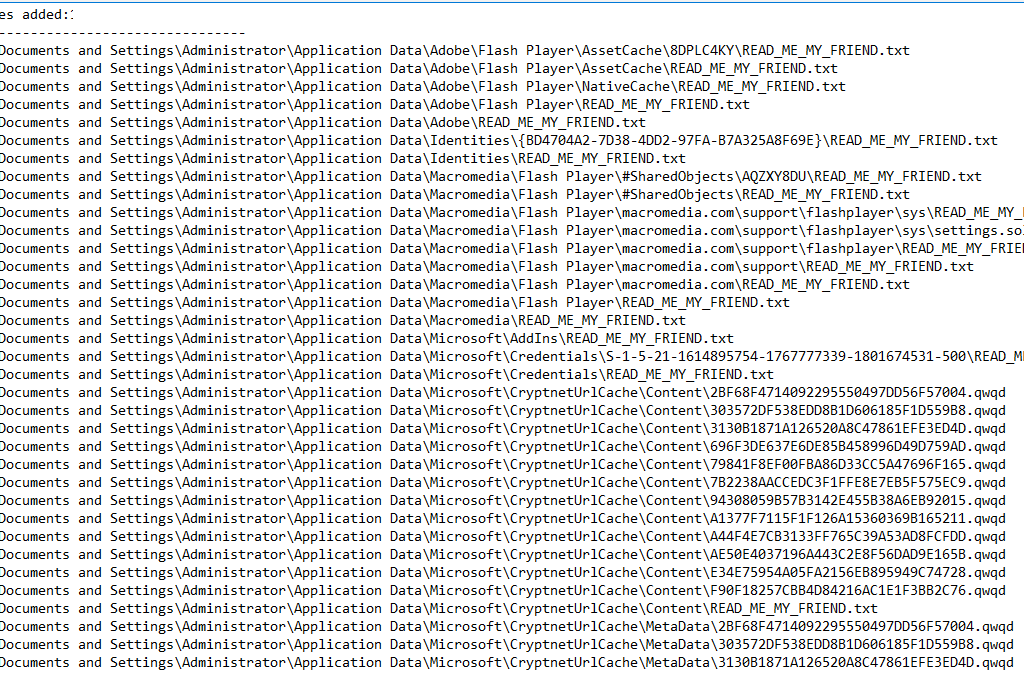
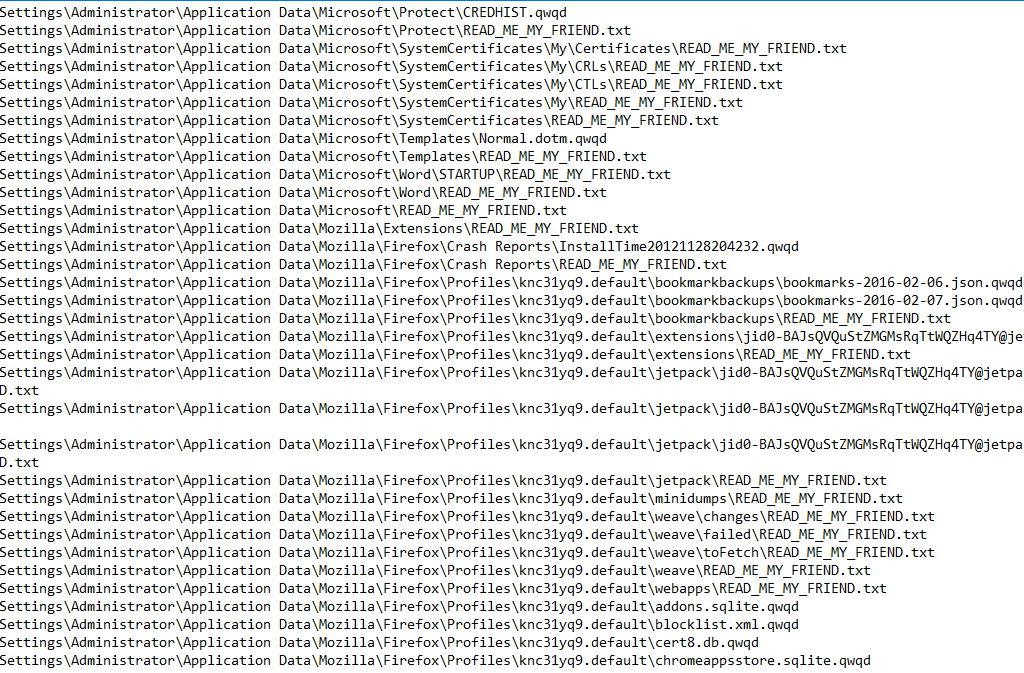
The following registry entries were also created by Dcry:
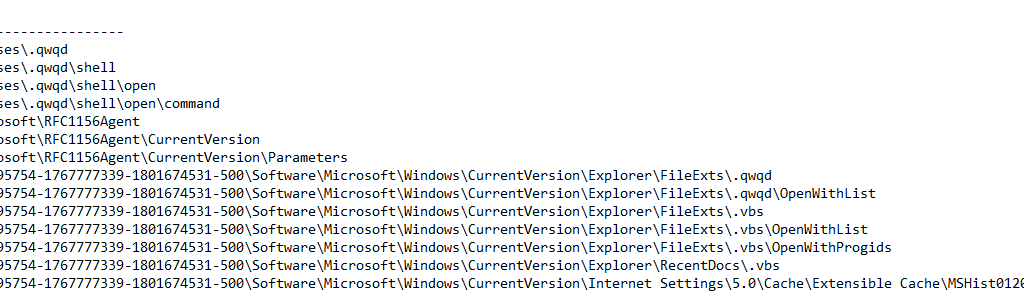
Network activities
No IP/Domains involved
Conclusion
Once Dcry successfully gains a foothold on a victim machine, it drops a “message.vbs” on execution, after which it performs a full system encryption with .qwqd extensions.
If the current tide of ransomware is any indication, we’re nowhere near the high-water mark. One of the best measures you can take to protect yourself from these attacks is to backup critical files at regular intervals. If you do happen to fall victim, then you can always restore your files from the most recent back up.


