
When it comes to protecting yourself online, the first line of defence is your password. In fact, creating a strong password might be the simplest method of securing your online accounts. Time, and time again, we see eye-wateringly weak passwords lead to devastating data breaches – but what exactly makes a password “strong”?
To answer this question, we first need to look at how passwords are breached. The first, low-tech attack is simply guessing. If an attacker wants to access your accounts, they’ll probably attempt several guesses before mounting a more sophisticated attack. The reason for this is simple; most people are just too lazy to remember a strong password, much less several strong passwords, so they opt for convenience over security. For reference, according to password manager Keeper, the 10 most common passwords used online include “12346”, “qwerty”, “111111”, “123123”, and “password”.
If you use one of these passwords, stop reading and change it now! Any attacker could “hack” (although this hardly counts) into your accounts in about a minute, just by guessing.
If this initial ‘guess and check’ attack fails, the next step is some simple social engineering. By using information you’ve made public online (pet names, children’s names, birthdays, street names, etc.) a nefarious netizen could use combinations of this information to continue trying to crack your password.
Assuming this attacker is hellbent on accessing your accounts, and has to this point failed to guess your password, they will move on to a more sophisticated “dictionary” or “brute-force attack”. In these attacks, a dictionary (for the former) or a list of every possible character combination (for the latter) is used to attempt every possible password you could use.
Generally, dictionary attacks are faster because they attempt only words, words followed by numbers, and personal information to guess your password. A brute-force attack, on the other hand, just tries every possible combination: a, aa, ab, etc.
Given enough time, a brute-force attack will eventually breach your password – always.
So how does one defend against an attack that is guaranteed to work, given time? Well, the situation isn’t as bad as it sounds because you have a key advantage.
This is where math comes in.
Common sense dictates a longer password takes longer to crack. This is because for each additional character in a password, many new password possibilities are created. Let’s assume your password is case sensitive (‘A’ and ‘a’ are different characters), and can use numbers 0-9. This means for one-character passwords, there are 62 possibilities (a-z is 26, A-Z is 26, and 0-9 is 10). Now, assuming the machine can check 1 billion passwords per second, your 1-character password will be cracked in: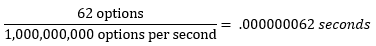
Or, no time at all. But here’s your key advantage: you get to pick the numerator. Essentially, you can add characters to make this equation return as many seconds as you want.
Let’s look at what happens when you add a second character to your password. Now you have 62 possibilities for the first character, and 62 for the second, for a total of: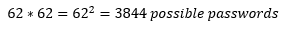
In this case, exponential functions are your best friend. Exponential functions grow fast, faster than nearly every other function. What this means is the longer your password, the longer it takes to solve. To see how powerful a few extra characters can be, let’s reverse our previous formula to find a password length that makes you feel secure.
Let’s use the equation to find a password length that would take one billion years to brute force.
First, find how many seconds are in a billion years: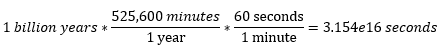
That’s 31,540,000,000,000,000 seconds. So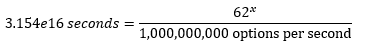
To solve for x, we rearrange and use a logarithm: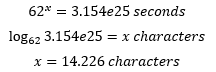
And there you have it, with a 14-character password, assuming you don’t use full words or personal information that could be easily guessed, you are basically safe from brute-force attacks.
Now, best practice dictates you have a unique password for each service you use, but remembering several 14 character passwords can prove problematic. This is where password managers, mnemonic devices or variations on a theme can help.
For example, let’s say your favourite show is Doctor Who. Including Jodi Whittaker who will become the first female Doctor later this year, the initials of past six Doctors are JWPCMSDTCEPM. That gives us 12 characters, so let’s add ‘63’ at the end for when the series first aired. All our characters are currently capital letters, so let’s change our one vowel to lower case.
Now, our 14 character password is ‘JWPCMSDTCePM63’. This could easily be modified for multiple sites by tweaking the variations slightly, for example by bookending the initials with our two numerals 6 and 3, ‘6JWPCMSDTCePM3’, or singling out other characters to be lowercased, such as the multiple instances of ‘M’, ‘C’, or ‘P’.
There you have it. Strong passwords don’t need to be rocket science. With a little creativity and at least 14 characters, you should be safe from brute force attacks for at least a billion years.


