In our previous analysis of Remcos RAT, we examined the XLS variant, this analysis will focus on a phishing email and a document (MS Word) infecting the victim’s computer with Remcos RAT payload. Remcos RAT, also known as Remote Control and Surveillance RAT, is a remote access Trojan (RAT) that enables attackers to take control and get unauthorised access to a victim’s computer. Malicious email attachments, software piracy downloads, and other social engineering techniques are frequently used to spread the malware.
Remcos RAT is a powerful & flexible tool that attackers can modify to meet their unique needs. It has been used in a variety of cyber attacks, including financial fraud, ransomware attacks, and espionage efforts over the last 3 years. According to observations by LMNTRIX CDC from infection data, they are collaborating with other APT organisations, including APT33 and The Gorgon Group.
Infection Chain
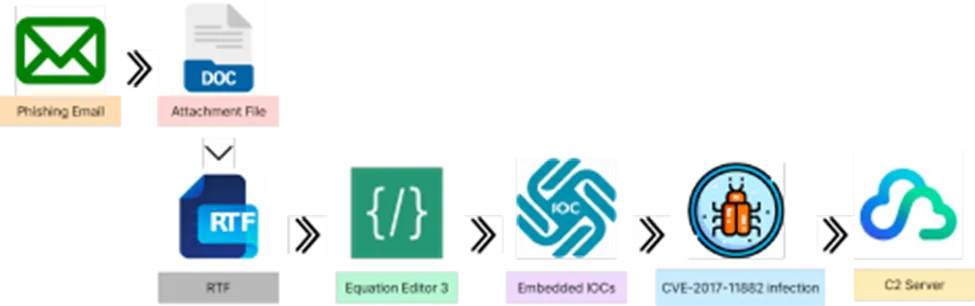
Target – Windows Platform
Infection Vector – Malspam campaign, or phishing emails
The initial vector for attacking users may vary depending on the threat actor’s motivation and targeted geography, we all know how cyber criminals perform basic reconnaissance against targets prior to attacking a range of victims with an infection vector of choice.
Sample Information
Threat Name: RemcosRAT | Category: Backdoor | Classification: Exploit
Technical Analysis of CVE-2017-11882
The Equation Editor is an exploit that refers to vulnerability in Microsoft Office’s Equation Editor component that was discovered in late 2017. The Equation Editor is a tool that allows users to insert mathematical equations into Office documents.
The vulnerability, known as CVE-2017-11882, allowed attackers to execute arbitrary code on a victim’s computer by exploiting a buffer overflow in the Equation Editor component. An attacker could exploit this vulnerability by sending a malicious RTF document containing a specially crafted Equation Editor object to a victim via phishing emails.
a) Phishing Email
Once the user opens the document, the exploit would execute at the backend, which allows the attacker to take control of the victim’s computer, steal data, and install malware. It’s very dangerous because it can infect all versions of Microsoft Office released since 2000, including Office 365.

b) Attachment RTF Document
RTF (Rich Text Format) is a file format used for storing and exchanging formatted text documents between different word processing software. It was developed by Microsoft as a cross-platform document format that could be used by multiple software applications.
Usually, the RTF document must start out with these six characters. ie: {\rtf1 – where, 1 is the RTF version number.
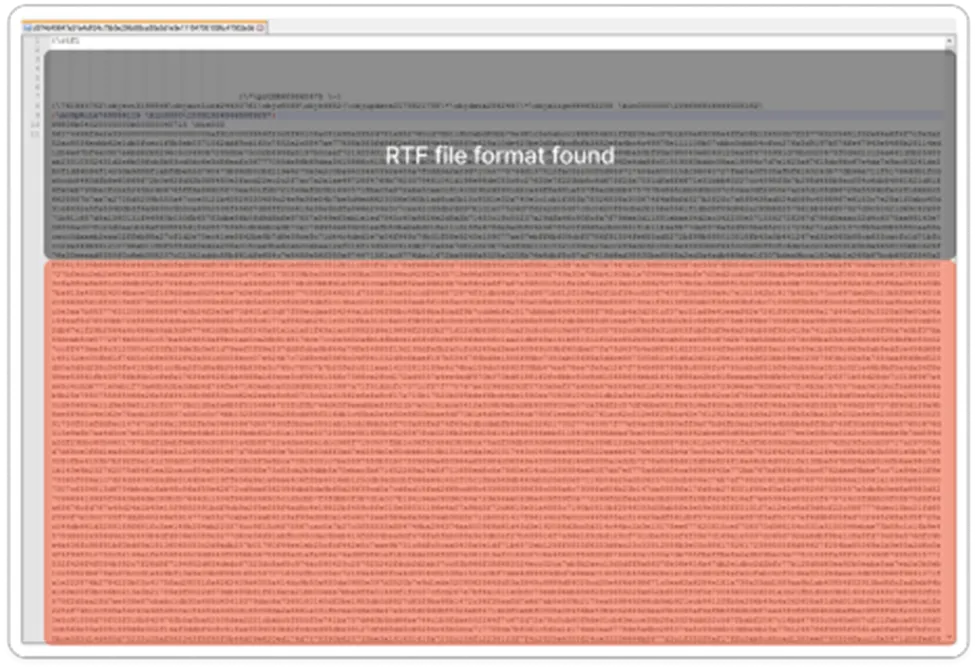
As we saw many randomized numbers in the RTF document, here we need to find out the embedded Equation Editor.3 in this document.
RTF Header has the following representation

Hardcoded RTF file
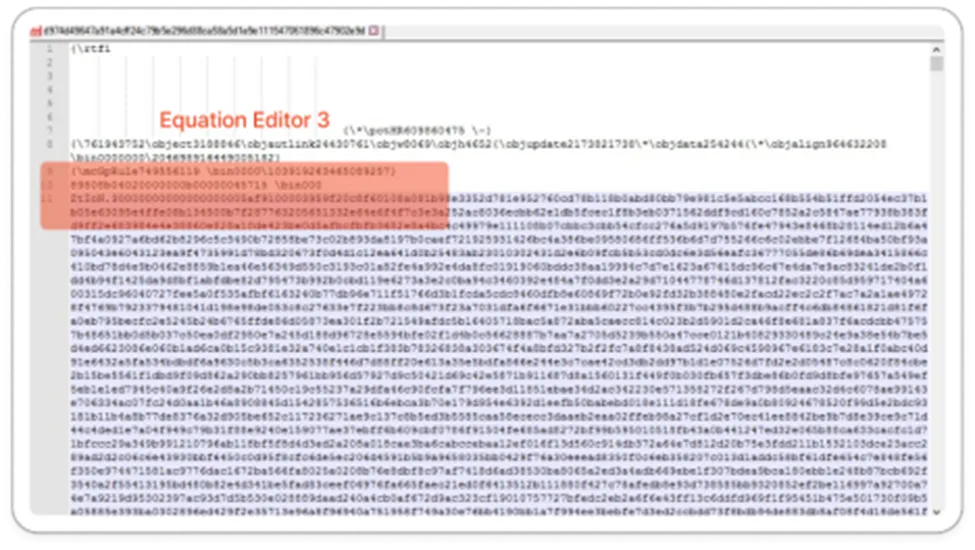
Here we successfully found the hard-coded ZtIoN.3 in the document. Still using this exploit some attackers continue to use the exploit to target systems which have not been updated yet.
Dropped Payload file
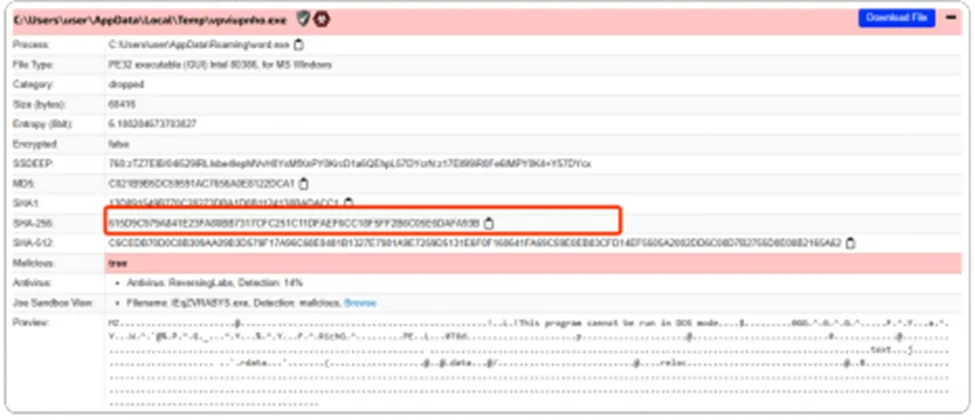
Payload File Names
{{
vpviupnho[[]].[[]]exe
13d891549b770c28273dba1d0b1124130badacc1[[]].[[]]bin
Plueajsoxt[[]].[[]]exe
}}
Indicator of Compromise for Remcos RAT
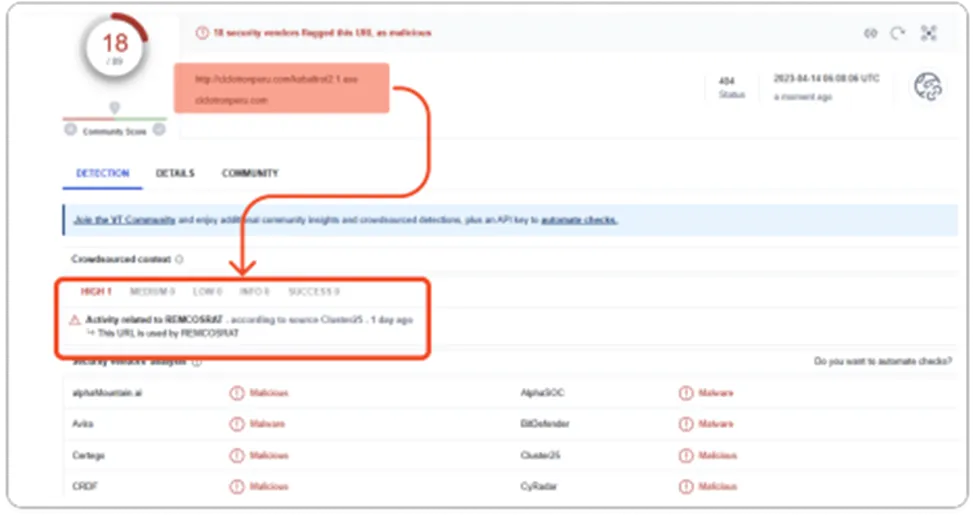
Once the Remcos RAT infects your system, the following actions can be performed,
● Monitoring user activity from time to time,
● Stealing passwords and logging keystrokes,
● Establish remote desktop connections,
● Bypass traditional antivirus and endpoint products,
● Maintaining persistence on the targeted machine,
● Runs as a legitimate process by injecting into the Windows process,
● Gains admin privileges and disables user account control (UAC),
● Editing the registry and using reverse proxy.
MITRE ATT&CK Tactics & Techniques to detect Remcos RAT
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | Windows Scripting Exploitation for Client Execution |
| TA0003 | Persistence | Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Scheduled Task |
| TA0005 | Defense Evasion | Modify Registry Virtualization Evasion Technique |
| TA0006 | Credential Access | Credentials in Registry Credentials in Files Credential Dumping |
| TA0007 | Discovery | System Network Configuration Discovery Process Discovery File and Directory Discovery Query Registry |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Automated Collections Data from Local System |
| TA0011 | C&C Server | Web Protocols Standard Application Layer Protocol Uncommonly used Ports Standard Cryptographic Protocol etc., |


