Qakbot (aka Qbot or Pinkslipbot) is a banking trojan, which steals sensitive data from the targeted victims and attempts to self-propagate to other systems on the network. As we all know, second-stage modular malware with backdoor capabilities. Qakbot also provides remote code execution (RCE) capabilities, allowing attackers to perform manual attacks to achieve secondary objectives such as scanning the compromised network or injecting ransomware.
Qakbot’s modules also allows automated targeting of financial data, locally stored emails, system passwords or password hashes, website passwords, and cookies from web browser caches. The threat actor can also log keystrokes to steal any typed credentials.
QBot Infection Chain of 2022
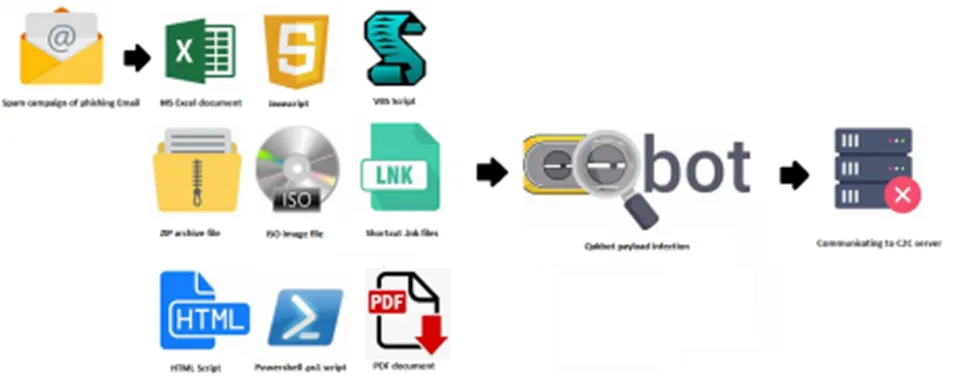
Distribution Techniques
In this blog, we will discuss two different recent distribution techniques of QakBot/QBot malware.
Technique 1: Distributed via OneNote file
OneNote is a digital note-taking app that provides a single place for keeping all of your notes, research, plans, and information where everything you need to remember and manage. An .one file is a notebook which is created by Microsoft OneNote, a note-taking program. It contains one or more pages of notes, which are organized into sections. ONE files may contain text, digitized handwriting, and objects pasted from other applications, such as images, drawings, and audio or video clips.
OneNote Infection Chain
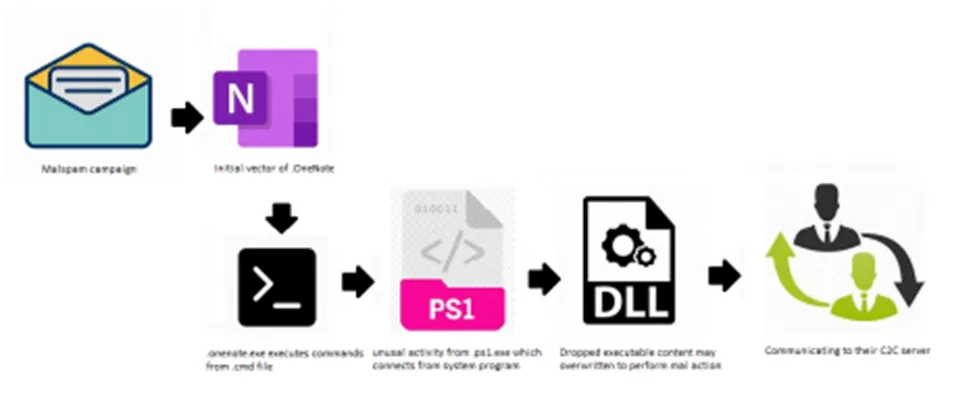
As usual, campaigns begin with the source of the first spam email. This time, they were able to get away by using Microsoft’s OneNote. Once the user opens the.onenote file, the.CMD file’s commands will be run . ps1 does something strange: it connects to the system program and drops the executable payload at the targeted path. It does this by overwriting the content of the onenote executable, which is how it performs the malicious action. When the payload file is run, the QBot infection starts communicating with their C2C server to trade the stolen information and data.
Sample Information
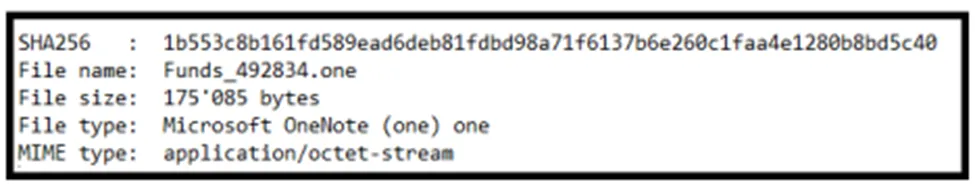
Technical Analysis
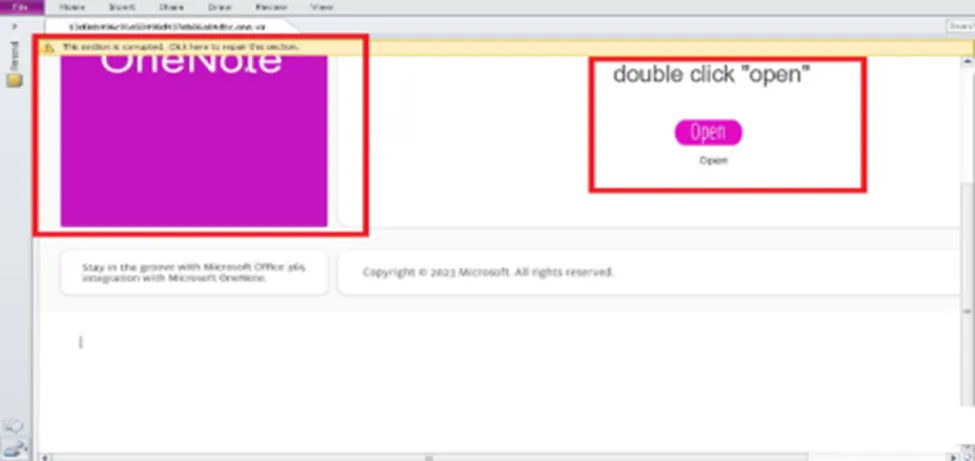
Here’s the mock OneNote page with a dialogue message box. When the victim clicks on the attachment file. Actually, the message box instructs the victim to double-click to open the pages in order to view their content. One interesting feature is that we can see MS copyright 2023, which leads them to believe that it is legitimate.
Once the file is executed then, automatically Qbot will open the powershell command. Most of the malware campaigns are using powershell .ps1 commands to initiate the initial process i.e. communicating with the external URLs to download the 1st level payload/dropper files etc.
Why is powershell used?
Powershell is commonly used for automating the management of systems. It is also used to build, test, and deploy solutions, often in CI/CD environments. By using the same scripting language, malicious threat actors leverage scripts, such as WScript and CScript, to escape script-host constraints on Windows and other operating systems. Now, Powershell is used to carry out the critical pieces of the attack. The Powershell script used in this instance was to disable Windows Defender’s antivirus prevention capabilities like real-time detection, script and file scanning and a host-based intrusion prevention system.
Powershell > Base64 Decoded
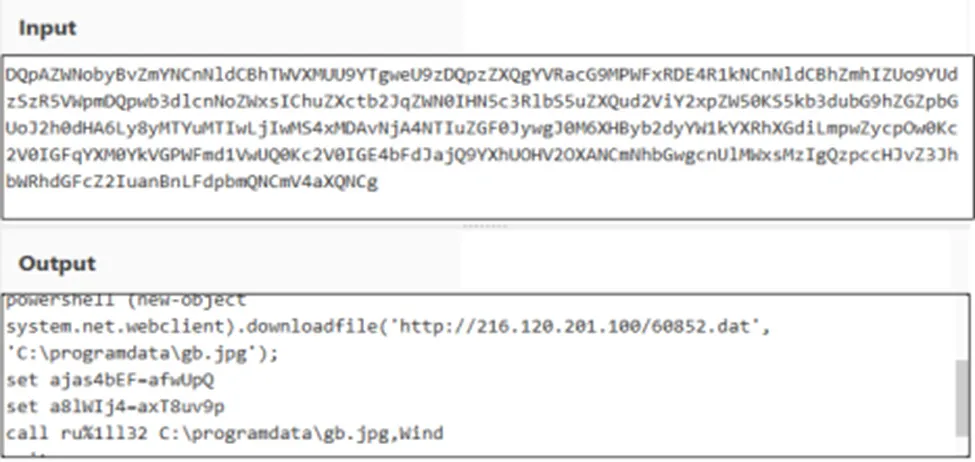
Hard Coded .ps1 command
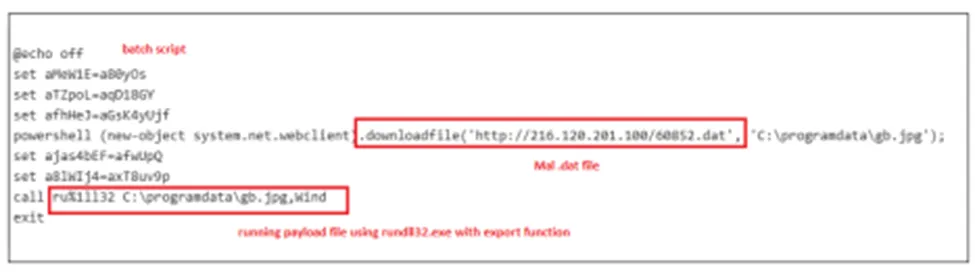
We can see the powershell command which calls the randomized .dat file with the malicious IOC where it’s going to store into the hidden folder of %ProgramData% in C drive under the name of gb.jpg file. After that it will execute the payload file using rundll32.exe.
Technique 2: Distributed via .hta file
The .hta file extension is a file format used in html applications. HTA embodies the program that can be run from the HTML document. HTA contains hypertext code, VBScript or JScript code depending on the program set up. A .hta file executes without being confined to the limiting factors of the security context of the browser that it is also treated as a fully trusted application. HTA are in text format so text editing programs can be used to edit the raw / source files.
The default file-association for the .hta extension is the Microsoft HTML Application Host (mshta.exe). HTA files store executable code that can be run from an HTML document.
HTML Infection Chain
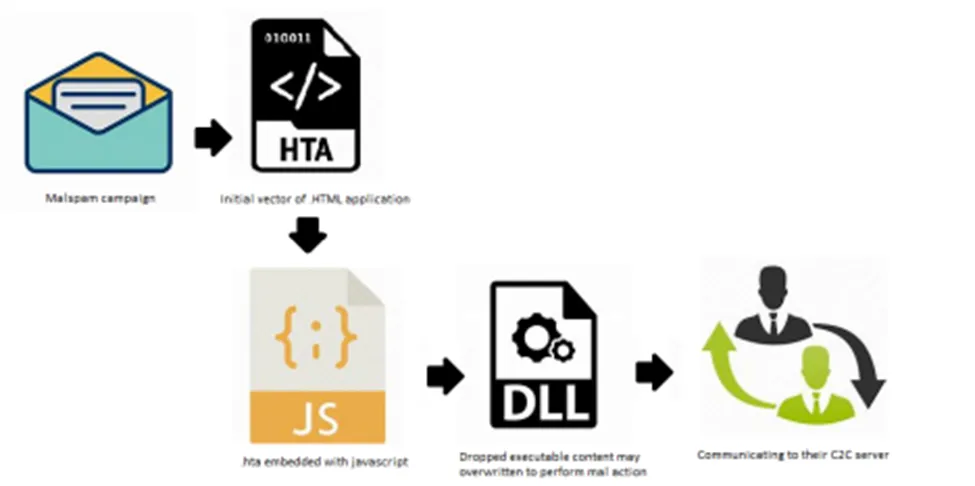
As usual, this campaign also starts from the initial vector of spam emails. This time the threat actor uses .hta as their evasion technique to bypass security controls. Once the user opens the.hta file, the commands from the.CMD file will be run, and then the.js script will do something strange, it connects to the system program and drops the executable payload at the targeted path. Upon launching of the payload file, QBot infection starts & communicating to their C2 server to exchange the stolen data & information.
Sample Information
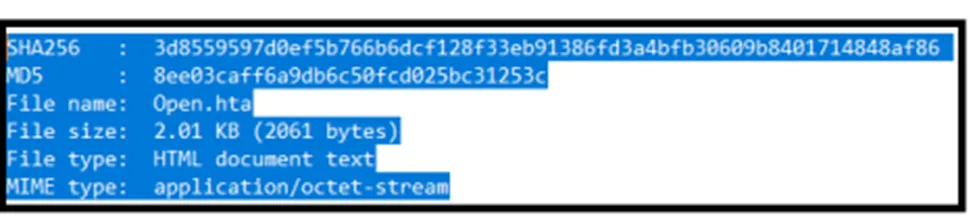
File Contents

Here is the full content of the .hta file, where it’s containing the junk 5& as the repeating factor, if we remove the factor we will get the exact function. Once the user launches the .hta application then the mshta.exe will execute at the C:\Users\User_name\Desktop\Open.hta to communicate with their phishing IOCs to perform the intended malicious action.
Indicator of Compromise
Here we can see the .dat file, once the user opens the file. In general, A DAT file is a data file that contains specific information about the program used to create it. This file has the .DAT file extension, which is a generic format that can contain any information – video, audio, PDF, and virtually any other type of file.
MITRE ATT&CK Tactics & Techniques
| ID | Tactic | Technique |
| TA0001 | Initial Access | T1566.001 – Spearphishing Attachment |
| TA0002 | Execution | T1027 – Obfuscated Files or Information T1204.001 – Links via OneNote/.hta file T1204.002 – Attachment file via OneNote/.hta file |
| TA0003 | Persistence | T1053.005 – Scheduled Task T1547.001 – Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | T1053.005 – Scheduled Task |
| TA0005 | Defense Evasion | T1027.002 – Software Packing T1055 – Process Injection T1218.005 – Onenote spawns MSHTA to execute embedded .hta file. T1497.001 – System Checks |
| TA0006 | Credential Access | T1003 – OS Credential Dumping T1110.001 – Password Guessing T1555.003 – Credentials from Web Browsers |
| TA0007 | Discovery | T1016 – System Network Configuration Discovery |
| TA0011 | C&C Server | T1071.001 – Web Protocols T1090 – Proxy T1090.002 – External Proxy |


