
Introduction
LokiBot was first advertised and it originated in underground forums in 2015 as an information stealer and keylogging software. Since then, it has added various capabilities and affected many people globally. Lokibot was deployed as a botnet initially, in which a number of compromised systems infected with the malware communicate with command-and-control (C&C) servers in order to send stolen data and receive commands from the C2 Server.
Lokibot was developed in PHP, it can be hosted in React JS like framework, with additional code in C++ and C#. Lokibot is a complex and very technical piece of malware, with Base64 encoded strings and 3DES Encryption employed for code obfuscation, forming 3 layers of packed malware code, and it exploits known memory corruption vulnerability with CVE-2017-11882.
LokiBot is perceived to be an information stealer, but it’s a hybrid Android and Windows infection-capable malware that steals credentials, logs keystrokes from the most widely used web browsers, FTP, and email clients. It also doubles up as a Banking Trojan that can launch drive by attacks, steal information, mine cryptocurrency, act as a ransomware and has advanced features such as UAC bypass to get past Windows 7, Windows 8 and Windows 10 if the user denies administrative rights to the malware.
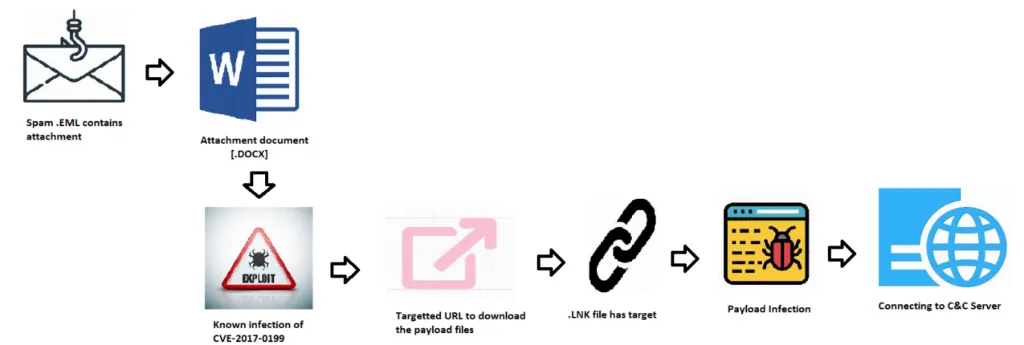
Infection Chain:
Here, the exploit arrives as a spear-phishing email attachment. This kind of email contains Microsoft office word documents (.docx) which is in archives file format. It contains a simple purchase order Invoice attachment; this kind of exploit doesn’t require enabling the macros. Once the user opens the document, it will connect to the target URL to download its subsequent vector such as RTF, LNK files etc., then those files communicate with the payload to perform the malicious actions.
Sample Information
Sample 1: Phishing Email Content
EML: 4f9d48eaa3daae385fc39ce9d3618b61938e184f016a3b821136a97f51463a26
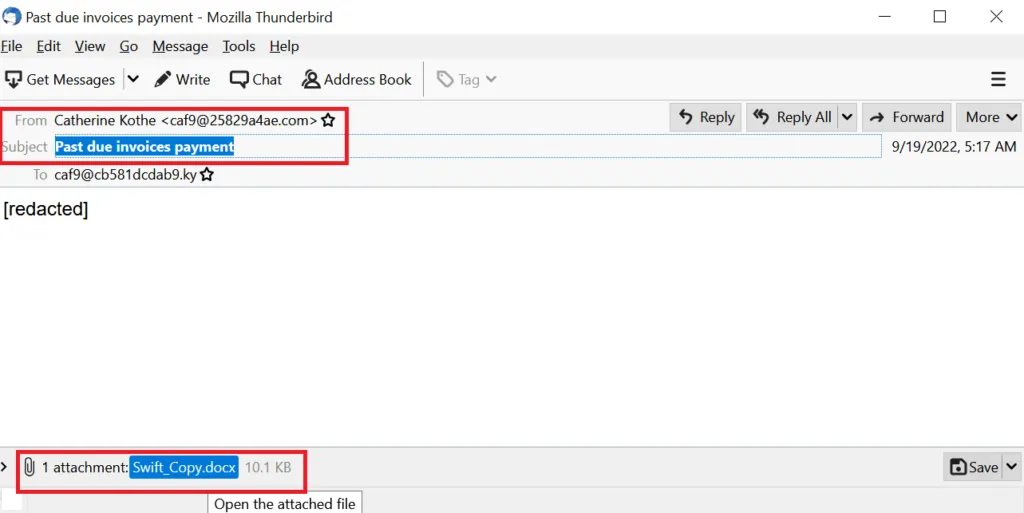
Here, the malware author very cleverly used a well-known technique to spam a victim by simply sending an invoice payment. Mainly there’s no sense of urgency, just an invoice attachment. What will the users normally do? They simply open the attached document to view the invoice message. This is one of the common evasion techniques used to proliferate spam emails.
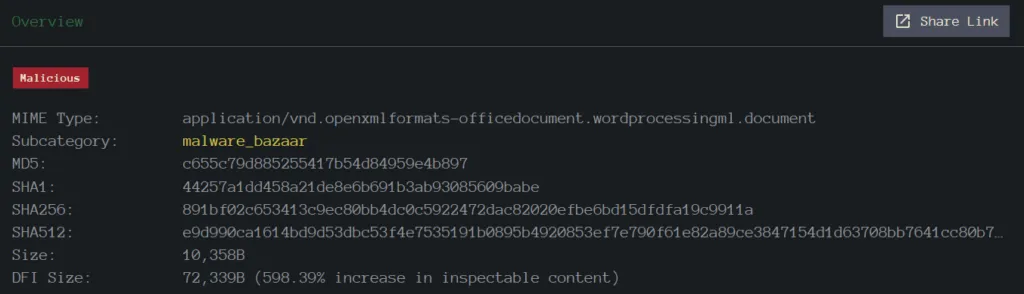
Sample 2: Attached DOCX
DOCX: 891bf02c653413c9ec80bb4dc0c5922472dac82020efbe6bd15dfdfa19c9911a
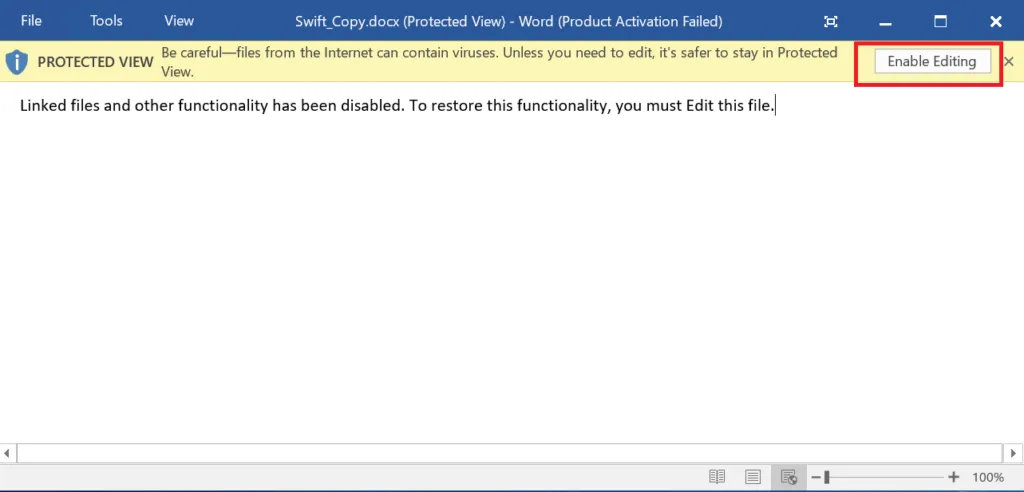
Here, there’s not much content inside the document. Simply, enable editing content in-order to enable the macro functions.
Enable-Editing:
Once editing is enabled, the targeted URL inside the websetting.xml will trigger to perform the malicious actions.
Structure of the DOCX file:
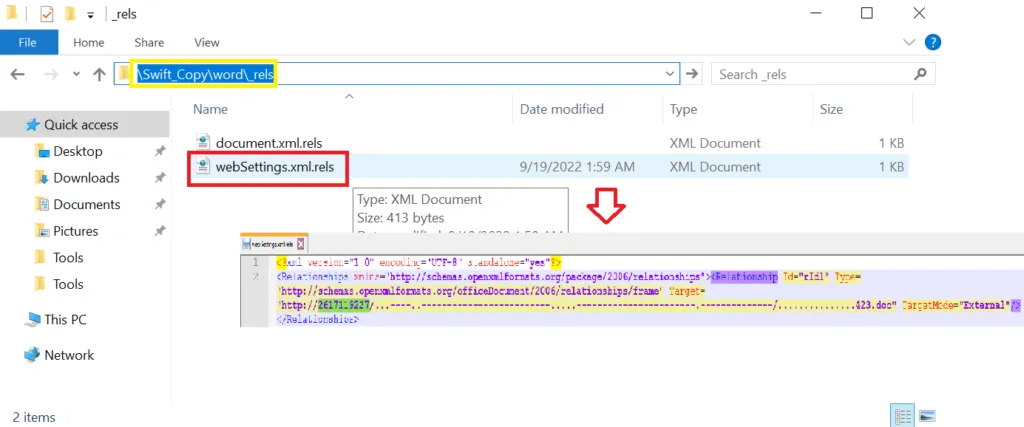
XML has a variety of uses in the sectors like Web, e-business, and mobile applications. Few XML-based Languages include XHTML, RSS, SMIL, WSDL, WAP, and SOAP. XML files are used to develop database-driven types. Due to their Flexibility, they could transfer data without missing descriptive information among corporate databases. So, this takes advantage for the malware author to target its victim’s system easily.
websettings.xml > It’s a web page setting, which specifies the set of web page settings including the root element, that have been specified for a single Word-processing XML document.
Target URL:
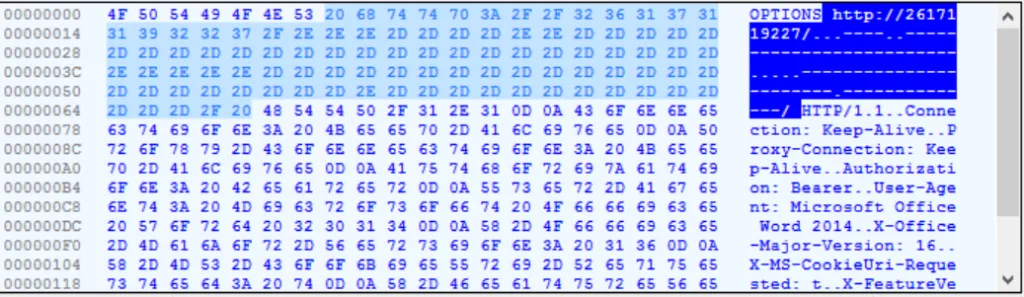
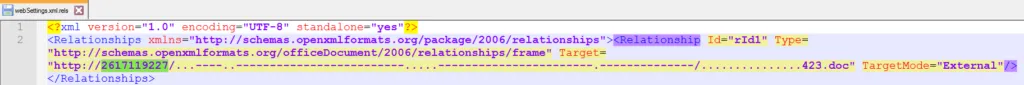
Here, we can see the word HTTP followed by random numbers?? No, it’s a not a normal number, rather it’s an IP address, the author tricked the user to believe that the source is a legitimate one.
Technique: They just used the IP Shortener to hide their malicious IP address.
Initial – Indicator of Compromise [IOC]:
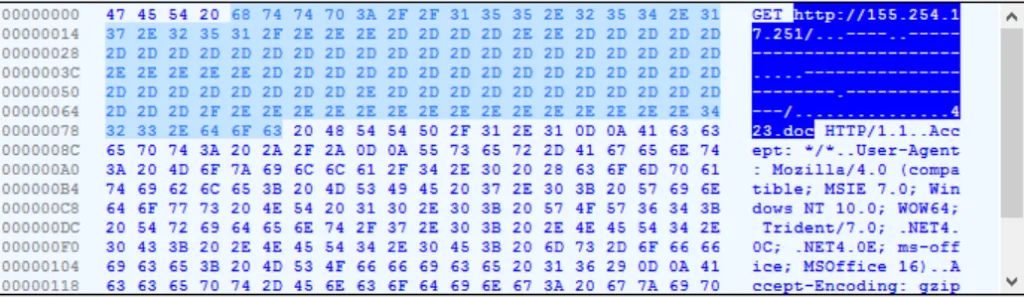
Dropper File:
Once the file is executed, then it will create an internet shortcut file, and which will call the targeted URL.

Generally, Internet Shortcut files are used to create shortcuts on your computer to Internet websites. They are like normal shortcut files, but while shortcut files are links to files stored locally on your computer, Internet shortcut files point to a file or resource that exists at a remote location accessible through the Internet.
Sample 3: RAR Archive
18cf375e022d0eec7a05b243a1e884318180a20f7d1479668be900b058280381
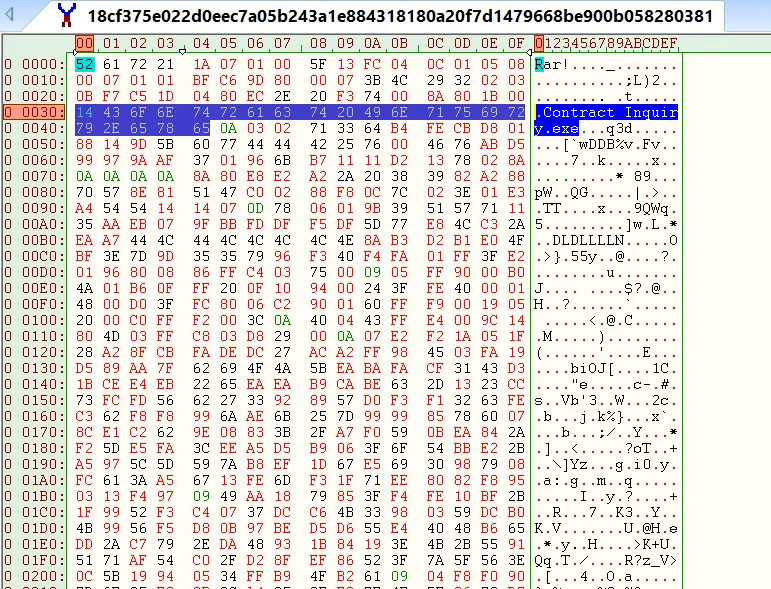
Inside the RAR file, we can see there’s a payload file – Contract Inquiry[.]exe
Sample 4: Payload file [.EXE]
107b6b206140ed200f6440f30077c53ed7db2447c04cde954c52437962ea0fcb
The file has base64 encoded strings and 3DES cryptography for code obfuscation and its functionality is provided in details as part of the MITRE ATT&CK mapping. It uses HTTP protocol to communicate with the C2 server.
Once infected, the following actions are carried out by the Loki Bot malware;
Collect system fingerprint information and sends it to C2 server,
Checks for debugger evasion, and executes the malware,
Creates hidden files, links, and directories, (Eg: %AppData% folder)
Sample tries to set the executable flag,
Executes commands using a shell command line interpreter,
File and Directory Permissions Modification.
Then, depending on if the current user is privileged, the virus sets persistence either under HKEY_LOCAL_MACHINE or KEY_CURRENT_USER,
For persistence, the keylogger then applies the 3DES encryption technique to the URL and the registry key;
After this, the virus starts waiting for commands from C2 server, creating a new thread to detect the C2 server’s response.
Mitigations for Loki Bot
LMNTRIX recommends that federal, state government, and private sector users to apply the following best practices to strengthen the security posture of your organization’s systems. System owners and administrators should review, document and schedule configuration changes with a risk matrix prior to implementation to avoid irreversible damage.
- Maintain up-to-date antivirus signatures and engines. Consider using an EDR solution.
- Keep operating system patches up to date.
- Disable file and printer sharing services, unless they are absolutely necessary. If these services are necessary, please use strong passwords to secure these services.
- Enforce multi-factor authentication through a token, or mobile implementation.
- Restrict user’s privilege to install and run unwanted software applications.
- Do not add users to the local administrator group unless required.
- Exercise caution when opening email attachments, even if the attachment is expected, and the sender appears to be known.
- Disable unnecessary services on your workstations and servers.
- Exercise caution when using removable storage media (USB pen drives, external drives, CDs/DVDs).
- Scan all software downloaded from the internet prior to executing.
- Maintain situational awareness of the latest threats and implement appropriate security controls to restrict access.
IOC – Indicators of Compromise for Detecting Loki Bot
IP Address
210.245.8.133
212.1.211.48
172.67.179.121
23.253.46.64
31.170.160.61
74.208.236.199
162.241.3.30
172.67.206.17
204.93.178.31
216.10.240.90
103.26.43.131
78.128.76.165
212.108.234.94
172.67.214.235
104.18.39.232
50.31.174.86
77.222.62.31
104.18.32.77
172.67.204.22
103.199.16.121
Hashes Observed
E9E14BAF4ADF6E1D45016C79EC09B7E5A36E1DEE272E1F335F96CE7CDFED127A
51F462CFFF7CCE2803C70069E302A86C66F43CEC35602171A4752A997013CA87
442730F6CF2A2FF1D7CA9E286F5BDCF99689CAE3C8B959F9B1DBBDDD6839F78A
52431707738F4962E6D465B66C5A8D56D36B0EDBCBC268002BC56C6F4B40A4D2
958595E2B49E0042FC6888D3CD008DCA5FD38BC79CD7574DD5031B27171ED811
A822B982EF431F0A6813EF38DD672151C786AADB71C0787F8419BD04B127A44D
DA65AEE4D8D8B4F979AB4176C9E69347E06187EF59C03914F278859ACADFF45A
AE4AD82FDBD7BE97E93A92555320E683EA177DE299F4A882411D652B464837F7
D361D688E58FAFB99967AFC805BD203C1F743A113B8C76C7E94B2960F40B285D
D072A28D28A7498F48B82D55BE214F4808F18EAEB1CBD6E414BD131CB507FC04
0D3E3B77F530D1D4AE4ABC3AC74283EA6E6FF41784A14447E925EE88E6D057C5
77C100C1960321C3FA9BE5157FB9F9E21D9C0AB60D1106DF819E431516462CE4
107B6B206140ED200F6440F30077C53ED7DB2447C04CDE954C52437962EA0FCB
050A053B4F14B010CFC82949BB761C209D1B4A8E98675E1E13FE072EF942B246
839119DE734C39B0C2F3C1391AED1F9F5BC6BD162DF9194743CF3EC6AF90BEF8
F172723AA5C023E6D22BDBBFA8DE48679C694AF6EAF6156142BABF4913F520CE
542219BA546FB9770B914CBC0F7FA117C1CF3FC2F8C4D58165E4884328196ABA
E4D40B456C9DA36ED8516C0B5A77819368020F6D386ED8955814CA77FFF5F58A
73B13CEA2C234CE674DAE5666BC66FE01BA387283672CCF2684735A1B8C9A643
Domains
data.jsdelivr.com
secureanalytic.com
ww1.tsx.org
ww1.virustoal.com
majul.com
css.developmyredflag.top
www.downloadnetcat.com
cdn.intedia.de
cdn.siteswithcontent.com
mail.tecniagro.net
kucukkoybutik.com
makemyroster.com
guose.intsungroup.com
app-a.customericare.com
mail.forumsboard.com
www.sgstockexpert.com
pnpboxes.com
wolneatomy.com
smtp.standardsintered.com
harbygazete.com
MITRE ATT&CK Mapping for Loki Bot
According to MITRE, the Loki Bot uses the following, tools tactics and procedures,
| Tactics/Techniques (TTP) | Malware Function |
| System Network Configuration Discovery [T1016] | Loki Bot has the ability to discover the domain name of the infected host. |
| Obfuscated Files or Information [T1027] | Loki Bot has encoded strings with Base 64 encoding. |
| Obfuscated Files or Information: Software Packing [T1027.002] | Loki Bot has used several packing methods for obfuscation. |
| System Owner/User Discovery [T1033] | Loki Bot has the ability to discover the system information and username on the infected host. |
| Exfiltration Over C2 Channel [T1041] | Loki Bot has the ability to initiate contact with command and control to exfiltrate stolen data. |
| Process Injection: Process Hollowing [T1055.012] | Loki Bot has used process hollowing to inject into legitimate Windows process vbc.exe. |
| Input Capture: Keylogging [T1056.001] | Loki Bot has the ability to capture input on the compromised host via keylogging. |
| Application Layer Protocol: Web Protocols [T1071.001] | Loki Bot has used Hypertext Transfer Protocol for command and control. |
| System Information Discovery [T1082] | Loki Bot has the ability to discover the computer name and Windows product name/version. |
| User Execution: Malicious File [T1204.002] | Loki Bot has been executed through malicious documents contained in spear phishing email. |
| Credentials from Password Stores [T1555] | Loki Bot has stolen credentials from multiple applications and data sources including Windows operating system credentials, email clients, File Transfer Protocol, and Secure File Transfer Protocol clients. |
| Credentials from Password Stores: Credentials from Web Browsers [T1555.003] | Loki Bot has demonstrated the ability to steal credentials from multiple applications and data sources including Safari and Chromium and Mozilla Firefox-based web browsers. |
| Hide Artifacts: Hidden Files and Directories [T1564.001] | Loki Bot has the ability to copy itself to a hidden file and directory. |


