Remcos is a remote access trojan (RAT), or malware that takes remote control of infected computers. A “company” called Breaking Security creates and sells this trojan to customers. Although the malware distributor claims that the REMCOS program is only available to those who intend to use it for legal purposes, Remcos RAT provides clients with all of the features required to launch potentially damaging attacks on the victim’s system.
The malware can be purchased using various methods, and bootlegged versions of the malware are available via dark web. It can also take screenshots and record keystrokes on infected machines before exfiltrating the data to designated command & control servers.
Typically, Remcos RAT infects a system by embedding a specially crafted file into an Office document, either a MS Word, or MS Excel document, which permits the attacker to lure the user to execute malicious code without any warning or notification. The code is in XML which allows for any binary with parameters to be executed. Further, the same code is used to download and execute the REMCOS RAT.
In-Short: Remcos RAT allows full control over the victim’s machine and starts collecting sensitive information.
Language Used: .NET / Delphi and Powershell
Obfuscated: With Costura Assembly Loader
Encryption Used: RC4 Algorithm
Sample Version: 3.x
Infection Chain:
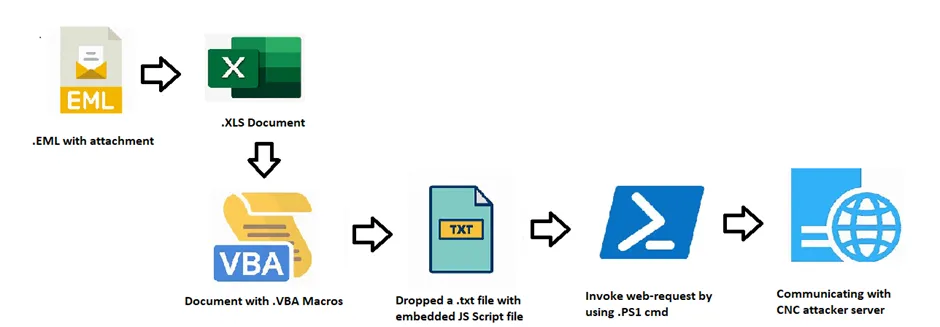
Here, REMCOS RAT infects its victim machine by initial infection vectors of spam campaign with attachment (EML). It contains a Microsoft Office documents (Excel) document with VBA macro enabled content. They tricked the user to enable the macros to perform their action. Once the user enables the content, it will drop a txt file embedded with .js script with invoke the web-request the malicious URI for further infection.
Sample Information:
Family: REMCOS RAT Campaign | Category: Dropper
Sample 1: Phishing Email Content
EML: cdd67c6483b4ed4e08c6ae437061f18a058263d800c2299f295b03c73520446c
Here, the EML comes with banking sector deposit advice receipt. Usually, many users act immediately when they receive any kind of banking related mails. Malware authors deceives the users and spread it further.
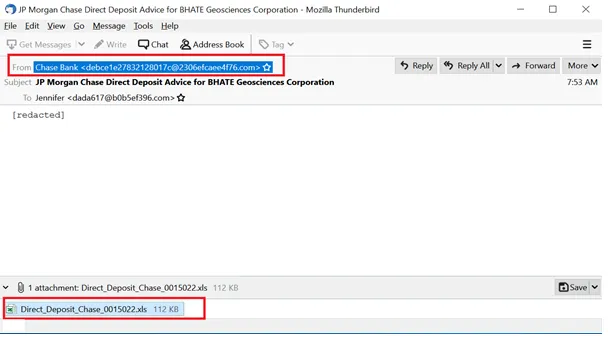
Sample 2: Attached XLS Document

Once the user opens the XLS document, there’s an option to enable editing. This will take us to the next step of the malware’s execution process.
Enable-Content:
Here, we can be able to see the macro enabled content. Basically, macro has a special function called “Wookbook_Active()” which will automatically open. Its main function is to extract VBA code from the cells into a corresponding file path usually in the “%AppData%\” roaming folder and then execute it.
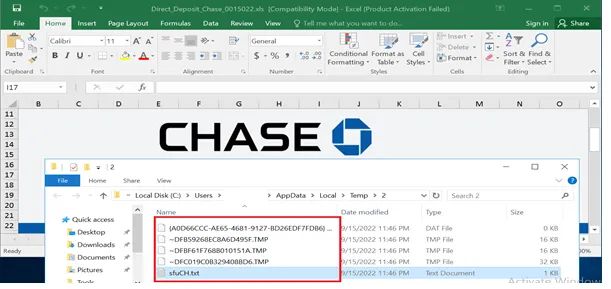
Dropped .TXT file:
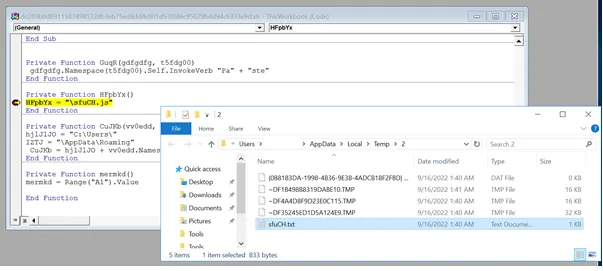
Once the user enables the macro content, the above-mentioned files are dropped in the temporary folder. Generally, .tmp files are automatically created and deleted from a computer. It’s a common function. But this uses the malware author to drop another XLS file as a TMP file. Also, it will take more memory accessible to execute a task.
For Example: If we close the XLS file, the entire .tmp files will automatically deleted. The temp folder is a prime target for malwares. Usually, malware is often attached to or embedded in legitimate programs and applications. We can see in the below screenshot. This makes us believe, there’s nothing unknown/SUS applications are running in the background.
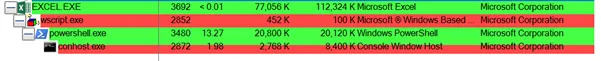
Sample 3: Embedded JS file
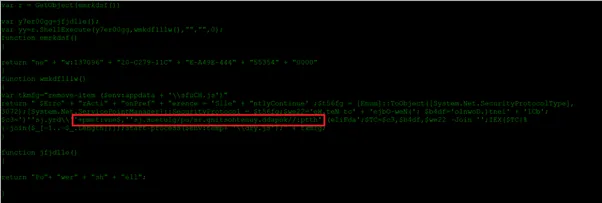
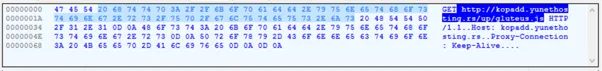
This content is clear cut about the URL but it’s in String reverse format. Once we re-order it we will get the exact URL. This will help the attacker to control the victim’s device and sends sensitive information to their reserved C2 server.
Indicator of Compromise [IOC]:
Remcos IOC
URLs involved in the Remcos campaigns observed:
hxxp://209[.]127[.]19[.]101/flip.vbs
hxxp://209[.]127[.]19[.]101/mem.txt
hxxp://209[.]127[.]19[.]101/faze.jpg
shiestynerd[.]dvrlists[.]com:10174
mimi44[.]ddns[.]net:2405
harveyautos110[.]ddns[.]net:2404
harveyautos111[.]hopto[.]org:2404
harveyautos112[.]ddns[.]net:2404
harvey205[.]camdvr[.]org:2404
harvey206[.]casacam[.]net:2404
harvey207[.]accesscam[.]org:2404
23[.]226[.]128[.]197:2404
achimumuazi[.]hopto[.]org:2311
xhangzhi[.]duckdns[.]org:2404
The following registry entries were added by Remcos RAT,
Key: HKCU \Software\Microsoft\Windows\CurrentVersion\Run
Value Name: SvchostHD
Data: %ProgramFiles%\SvchostHD\svchost.exe
Key: HKCU \Software\Microsoft\Windows\CurrentVersion\Run
Value Name: AudioHD
Data: %ProgramFiles%\ AudioHD\AudioHD.exe
Key: HKCU \Software\-
Value Name: EXEpath
Sample Hash (SHA 256 format)
[Remcos RAT Sample Info]8F6DD0DB9E799393A61D6C9CF6495C164E1B13CB8E6B153B32359D5F07E793D2
DA609D3211D60D5B11FEAEAA717834CBE86E18103A1ED4FC09C2EE3E1CFF9442
737E11913EFB64ACCF1B88532C7CE8606676684D8364DDD027926F9FFC6ECFFB
B263876EBC01B310A8BFC58477523981184EB7E8F2DC955F0CF8E62124EB679A
2C8B78FC6C4FE463DAC9D39FDE2871F1BB2605453BC0F2D57C7549CF5D07AA86
A1A1395D0602A473FCC81BA7D1D90C3FB154321D1721E0069722B902B1057CB0
6B816D84ACCC3E1EBCE3EF55B64B0C5E0485228790DF903E68466690E58B5009
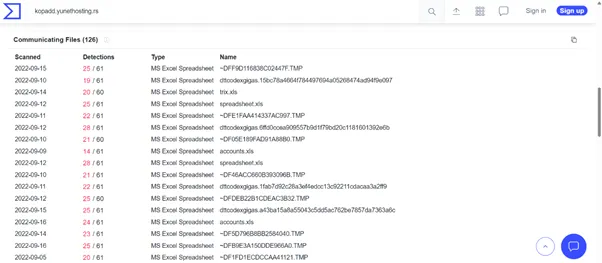
REMCOS Malicious IOC Collection:
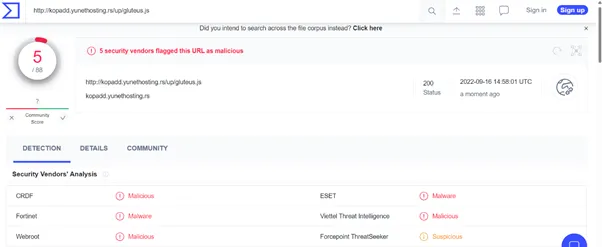
Communicating files: dc289b0d83115834981228b3eb75ed8dd4c001d53f086c95629b4d94c6333e9d
Conclusion
To conclude, LMNTRIX has explained how a phishing email delivers an MS Excel document containing malicious macro to the victim’s device. We also discussed how it executes multiple VBA scripts to download the Remcos payload and how the Remcos payload is deployed. We have described Remcos RAT workflow and the malware’s ATT&CK MATRIX for remediation.
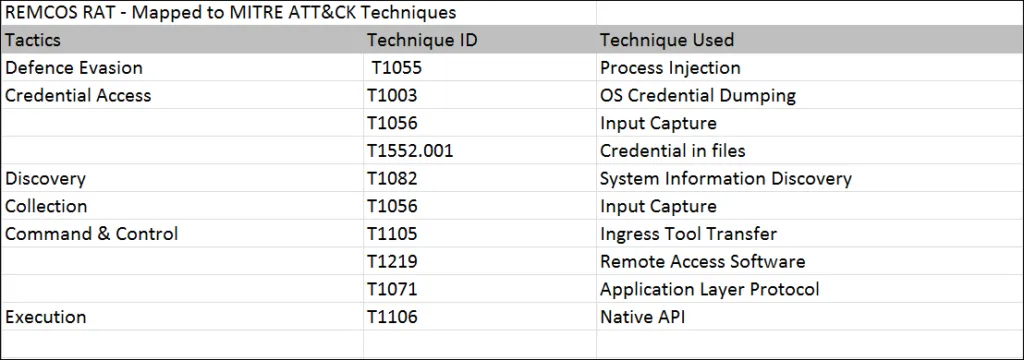
MITRE ATT&CK MATRIX