In this research, we have primarily focused on the Turkish APT group APT-C-41 (aka StrongPity and Promethium). The modus operandi of this group has been to install a backdoor on its victims machine to perform Cyber espionage operations. The main targets of this APT group have been Financial organisations, Industrial plants and Educational institutes. LMNTRIX threat research team brings together some of the payloads used by APT-C-41 (aka StrongPity and Promethium) in different campaigns across Europe in last quarter of the year 2020 by this threat actor group.
Payload details:
| Payload Hash | Command & Control Domains |
| d7aae4694291a7811c18ccc0af9d4b53 | mentiononecommon[.]com |
| 06752c080a5c00baf971243be65a49b8 | ms21-app3-upload[.]com |
| 52a895199380705c514dd0a23ba52414 | mailtransfersagents[.]com |
| c930f328b5b3894feced92d04908b256 | applicationrepo[.]com |
| 469c0460e4c1fefd01db4ae9f79c53c7 | uppertrainingtool[.]com |
| d7c62bc2a06d5abd872152ec87c64c8b 07ee8219801ec09951b8609142639480 c009b0bcf1c02503fff0d0e511188b68 a57e5f2011d04117c28982a68db28e23 ff9b1e2d7ad8b022f3fd3d9395382cf5 | hostoperationsystems[.]com |
| 989af6e0bb7fa4d62815f4fdc4696b85 | Protectapplication[.]com |
Sample Analysis
LMNTRIX Threat research team performed a binary analysis of one of the collected to understand different functions used by APT-C-41 (aka StrongPity and Promethium) in their payload.
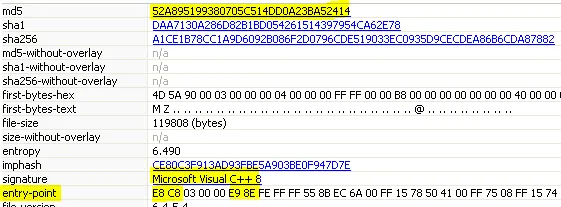
Hash (MD5): 52a895199380705c514dd0a23ba52414
File size: 117 KB
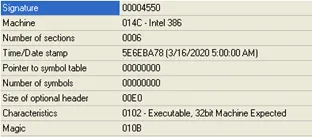
The collected specimen is an exe file (32 bit) and while checking the entry point, we confirmed that the file was compiled using VC++.
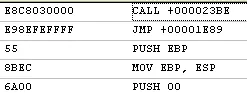
The above disassembled code is the entry point (call function followed by Jmp instruction) known for VC++ compiled file. We confirmed the compiler detail again with the help of other static analysis tool.
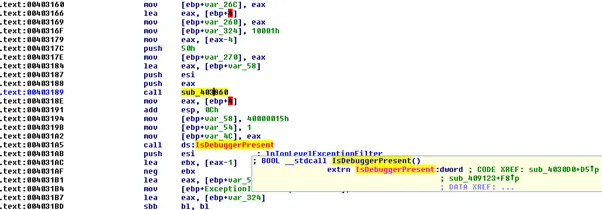
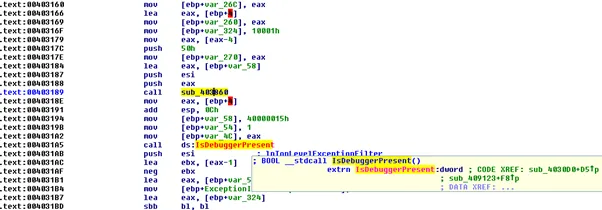
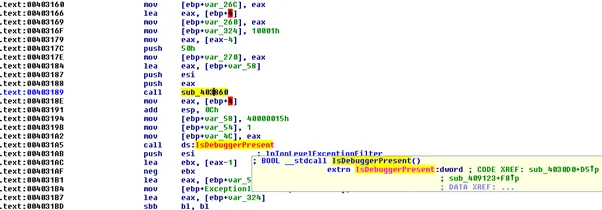
We further dissected the sample in the controlled environment to study the tactic used by the malware. We see the techniques like the discovery of file and directories, defence evasion mechanisms like VM aware, file obfuscation found in the sample. The sample has an anti-debugging function as:
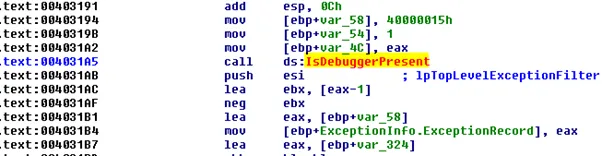
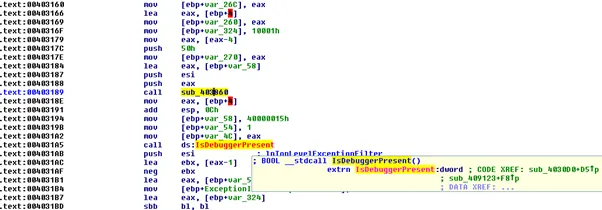
Further, we found the function to detect the presence of the virtual environment (VM aware functionality), it executes the anti-VM instructions.
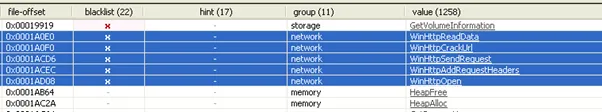
After bypassing these functions, we found the command and control domain embedded into the code. The snapshot shows the communication happens to the malicious domain which we highlighted below [mailtransfersagents(dot)com]:
This communication was initialized by using WINHTTP libraries to add the header requests, WinHttpSetOption, WinHttpSendRequest-WriteData and finally performed the receive response.
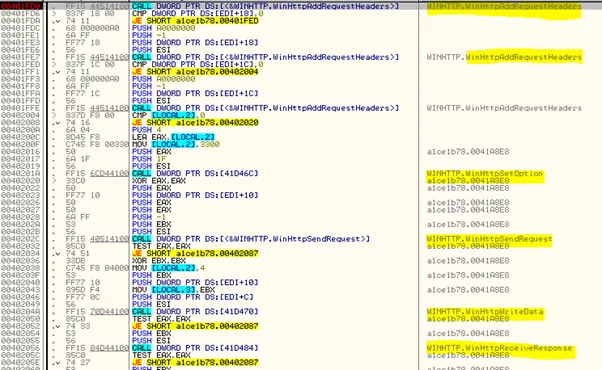
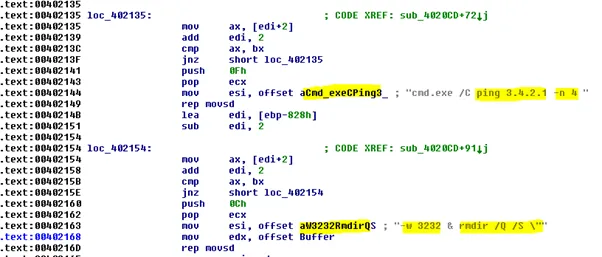
The functions highlighted above in the disassembled code was used for data exfiltration. The below code further shows the ping command and directory remove command used by the malware sample as well.
This clearly states that the sample has the functionality of deleting the directory trees in the victim machine and perform it in quiet mode. These actions are done with the help of command “rmdir” and parameters (/q and /s). This deletion with quiet mode didn’t ask for any confirmation to the user.
MITRE ATTACK ID Mapping
| Techniques ID | Name |
| T1547 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| T1543 | Create or Modify System Process: Windows Service |
| T1578 | Develop Capabilities: Digital Certificates, Code Signing Certificates |
| T1189 | Drive-by Compromise |
| T1036 | Masquerading: Match Legitimate Name or Location, task or service |
| T1553 | Subvert Trust controls; Code Signing |
| T1205 | Traffic Signaling: Port Knocking |
| T1204 | User Execution: Malicious File |
| T1078 | Valid Accounts: Local Accounts |
Mitigations:
The following is the Yara Detection Rule for APT-C-41 :
rule win_strongpity_auto {
meta:
date = “2020-12-22”
version = “1”
tool = “yara-signator v0.6.0”
signator_config = “callsandjumps;datarefs;binvalue”
malpedia_rule_date = “20201222”
malpedia_hash = “52a895199380705c514dd0a23ba52414”
malpedia_version = “20201023”
malpedia_license = “CC BY-SA 4.0”
malpedia_sharing = “TLP:WHITE”
strings:
$sequence_0 = { 56 8b7508 f7d1 85f6 }
// n = 4, score = 500
// 56 | push esi
// 8b7508 | mov esi, dword ptr [ebp + 8]
// f7d1 | not ecx
// 85f6 | test esi, esi
$sequence_1 = { a1???????? 33c4 89442450 8b03 55 8ba828010000 8b4d00 }
// n = 7, score = 300
// a1???????? |
// 33c4 | xor eax, esp
// 89442450 | mov dword ptr [esp + 0x50], eax
// 8b03 | mov eax, dword ptr [ebx]
// 55 | push ebp
// 8ba828010000 | mov ebp, dword ptr [eax + 0x128]
// 8b4d00 | mov ecx, dword ptr [ebp]
$sequence_2 = { e8???????? 8bd8 83c408 85db 0f85f5020000 8b442420 }
// n = 6, score = 300
// e8???????? |
// 8bd8 | mov ebx, eax
// 83c408 | add esp, 8
// 85db | test ebx, ebx
// 0f85f5020000 | jne 0x2fb
// 8b442420 | mov eax, dword ptr [esp + 0x20]
$sequence_3 = { 52 ff15???????? 83c404 837c241000 750a 837d0400 0f852e020000 }
// n = 7, score = 300
// 52 | push edx
// ff15???????? |
// 83c404 | add esp, 4
// 837c241000 | cmp dword ptr [esp + 0x10], 0
// 750a | jne 0xc
// 837d0400 | cmp dword ptr [ebp + 4], 0
// 0f852e020000 | jne 0x234
$sequence_4 = { 83c408 83f8ff 0f845d050000 ff442410 85f6 7fe0 }
// n = 6, score = 300
// 83c408 | add esp, 8
// 83f8ff | cmp eax, -1
// 0f845d050000 | je 0x563
// ff442410 | inc dword ptr [esp + 0x10]
// 85f6 | test esi, esi
// 7fe0 | jg 0xffffffe2
$sequence_5 = { 57 50 8944246c 89442450 }
// n = 4, score = 300
// 57 | push edi
// 50 | push eax
// 8944246c | mov dword ptr [esp + 0x6c], eax
// 89442450 | mov dword ptr [esp + 0x50], eax
$sequence_6 = { 397704 0f8493000000 eb6b 8b54241c 6a04 }
// n = 5, score = 300
// 397704 | cmp dword ptr [edi + 4], esi
// 0f8493000000 | je 0x99
// eb6b | jmp 0x6d
// 8b54241c | mov edx, dword ptr [esp + 0x1c]
// 6a04 | push 4
$sequence_7 = { c3 837c240800 56 57 8b7c240c 8db710050000 7534 }
// n = 7, score = 300
// c3 | ret
// 837c240800 | cmp dword ptr [esp + 8], 0
// 56 | push esi
// 57 | push edi
// 8b7c240c | mov edi, dword ptr [esp + 0xc]
// 8db710050000 | lea esi, [edi + 0x510]
// 7534 | jne 0x36
$sequence_8 = { 68???????? 50 e8???????? 83c40c 8d85e0fdffff ffb574f7ffff }
// n = 6, score = 200
// 68???????? |
// 50 | push eax
// e8???????? |
// 83c40c | add esp, 0xc
// 8d85e0fdffff | lea eax, [ebp – 0x220]
// ffb574f7ffff | push dword ptr [ebp – 0x88c]
$sequence_9 = { 899570f7ffff 3b5708 0f82c3feffff e9???????? }
// n = 4, score = 200
// 899570f7ffff | mov dword ptr [ebp – 0x890], edx
// 3b5708 | cmp edx, dword ptr [edi + 8]
// 0f82c3feffff | jb 0xfffffec9
// e9???????? |
$sequence_10 = { 6a5c 668945f2 58 56 }
// n = 4, score = 200
// 6a5c | push 0x5c
// 668945f2 | mov word ptr [ebp – 0xe], ax
// 58 | pop eax
// 56 | push esi
$sequence_11 = { 83ee01 75f8 e8???????? c3 8b770c 8d4710 8bd6 }
// n = 7, score = 200
// 83ee01 | sub esi, 1
// 75f8 | jne 0xfffffffa
// e8???????? |
// c3 | ret
// 8b770c | mov esi, dword ptr [edi + 0xc]
// 8d4710 | lea eax, [edi + 0x10]
// 8bd6 | mov edx, esi
$sequence_12 = { e8???????? 83c410 ebe6 8b45e4 8b0c85a8bf4100 8b45e8 f644012880 }
// n = 7, score = 200
// e8???????? |
// 83c410 | add esp, 0x10
// ebe6 | jmp 0xffffffe8
// 8b45e4 | mov eax, dword ptr [ebp – 0x1c]
// 8b0c85a8bf4100 | mov ecx, dword ptr [eax*4 + 0x41bfa8]
// 8b45e8 | mov eax, dword ptr [ebp – 0x18]
// f644012880 | test byte ptr [ecx + eax + 0x28], 0x80
$sequence_13 = { c746345c4b4100 57 ff7634 c6463c01 e8???????? 59 59 }
// n = 7, score = 200
// c746345c4b4100 | mov dword ptr [esi + 0x34], 0x414b5c
// 57 | push edi
// ff7634 | push dword ptr [esi + 0x34]
// c6463c01 | mov byte ptr [esi + 0x3c], 1
// e8???????? |
// 59 | pop ecx
// 59 | pop ecx
$sequence_14 = { 6a2f 59 668908 33c9 8b4608 66890c78 668b45d8 }
// n = 7, score = 200
// 6a2f | push 0x2f
// 59 | pop ecx
// 668908 | mov word ptr [eax], cx
// 33c9 | xor ecx, ecx
// 8b4608 | mov eax, dword ptr [esi + 8]
// 66890c78 | mov word ptr [eax + edi*2], cx
// 668b45d8 | mov ax, word ptr [ebp – 0x28]
condition:
7 of them and filesize < 999424
}


