
Version:1.0 StartHTML:000000289 EndHTML:000019321 StartFragment:000007098 EndFragment:000019253 StartSelection:000007098 EndSelection:000019249 SourceURL:https://www.lmntrix.com/Lab/Lab_info.php?id=71&url=Locky%20emerges%20out%20of%20hibernation,%20hits%2020%20million%20mailboxes LMNTRIX Labs LMNTRIX Labs
After disappearing for months, Locky ransomware is back… and in force. The strain first made headlines in February 2016 when a US medical centre paid a US$17,000 bitcoin ransom to retrieve patient data – operators said paying the ransom was the quickest way to resume caring for patients.
In this latest campaign, Locky is primarily being distributed via email as a word document invoice. In just one day last month, more than 20 million phishing emails suddenly appeared, flooding inboxes with the ransomware.
Delivery: The following table shows a list of malicious domains from which the Locky ransomware has been downloaded:
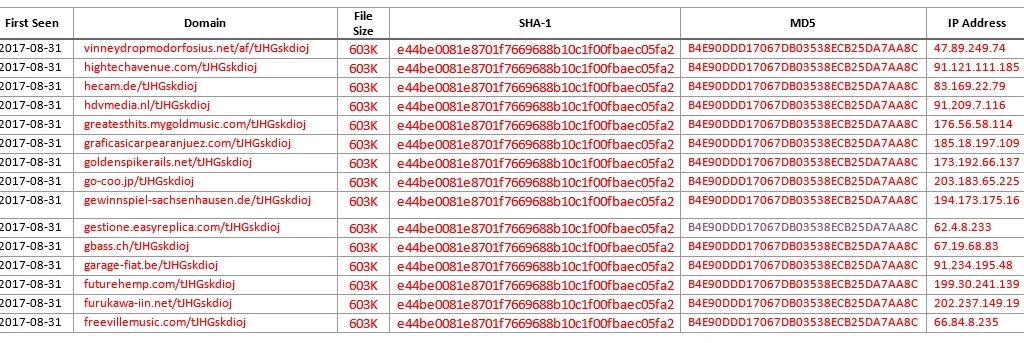
Figure 1 Malicious domain which downloads Locky ransomware
Security researchers have observed a number of distribution methods, the most popular of which has been an email phishing campaign:
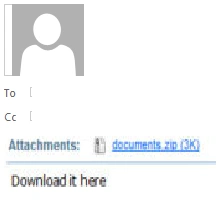
Figure 2 Malicious Email Attachment
This email attachment contains a zip file in which a Visual Basic Script (VBS) file is hidden. Once clicked, the victim downloads the latest Locky ransomware. The actual contact point for downloading the latest Locky sample is greatesthits(.)mygoldmusic(.)com – a known malware site, as shown below:
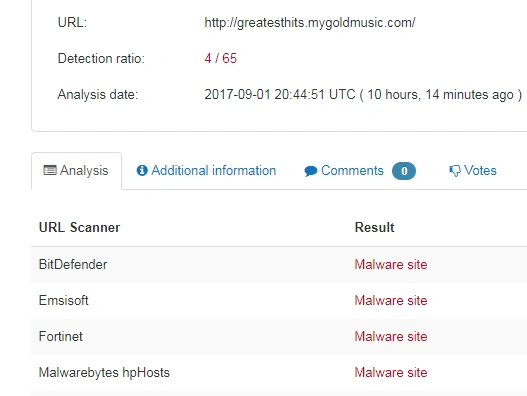
Figure 3 VT hits for malicious domain
Further analysis on the same domain shows it is linked to at least half a dozen malware samples:
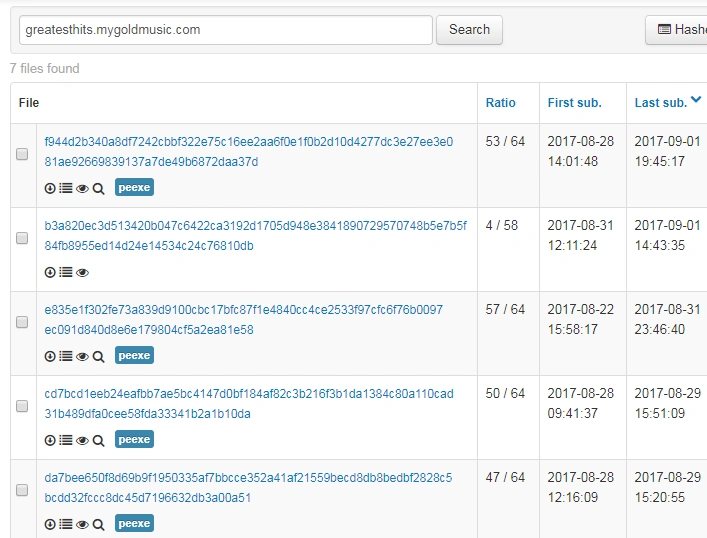
Figure 4 Latest Locky samples from greatesthits mygold music (malicious domain)
In addition to the malicious Word document, we have also seen a fake Dropbox account verification email used to distribute the malware. Upon clicking the link, the victim is directed to a spoofed Dropbox page. The user is told their account cannot be verified:
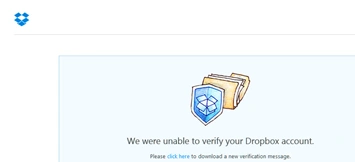
Figure 5 Fake Dropbox page
Below are the Virus Total hits for the fake Dropbox URL:
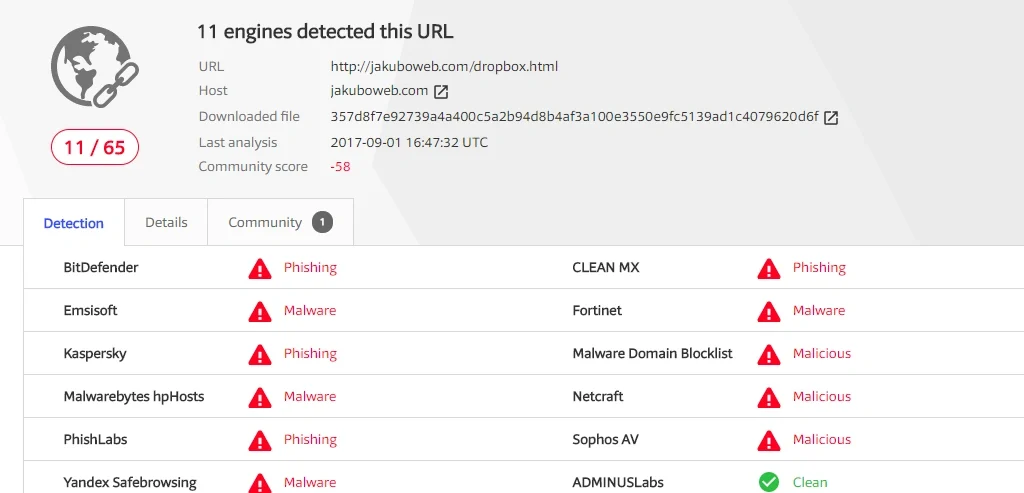
Figure 6 Fake Dropbox url (VT hits for malicious url)
The user is then told to download a javascript file. If the user opens this js file, their machine is locked with Locky ransomware.
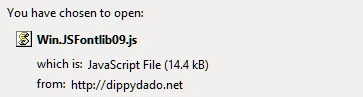
Figure 7 Downloading file
Infection – Behavioural Analysis:
MD5: 6480fc6b8c2d76965520d5184b5190a1
File type/size: VBS file/43 KB.
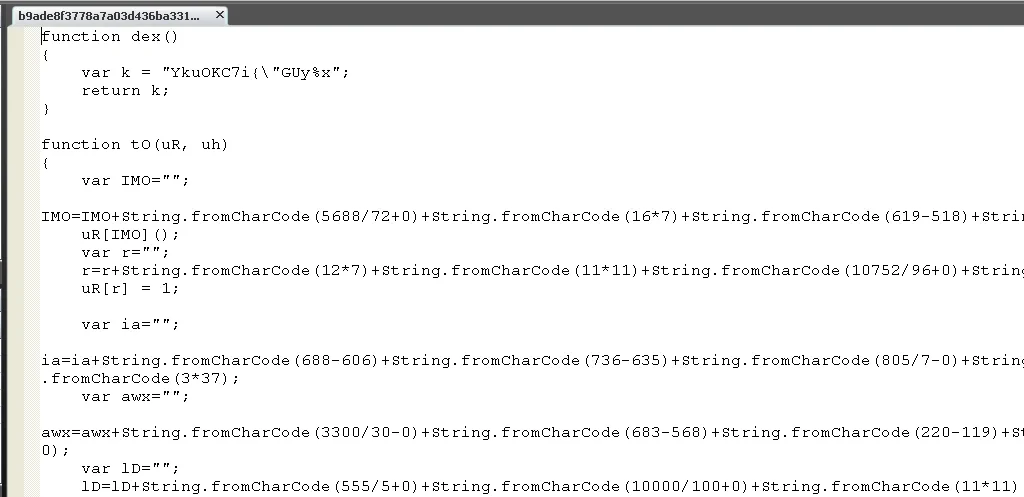
This script drops the ransomware and associated files: C44DEDDA.exe, csrss.exe, 814C2B0A.exe, 0208oi[1].exe and rad8D858.tmp. We then executed these files in our controlled environment:
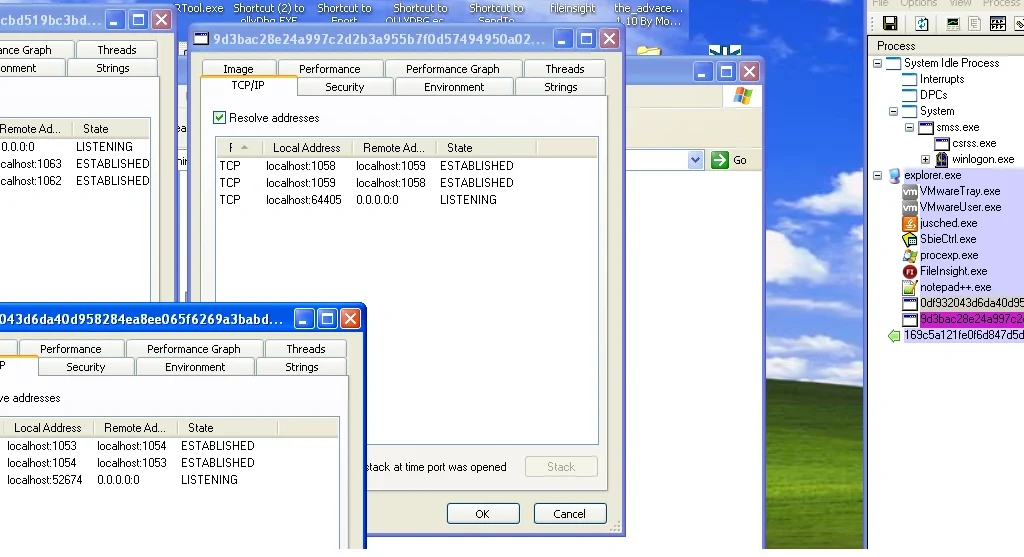
Figure 8 Execution of malicious files
All these files seek open ports and create new run entries:
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Client Server Runtime Subsystem” Type: REG_SZ Data: “C:\Documents and Settings\All Users\Application Data\Windows\csrss.exe” HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “CSRSS” Type: REG_SZ Data: “C:\Documents and Settings\All Users\Application Data\Drivers\csrss.exe” HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “NetworkSubsystem” Type: REG_SZ Data: “C:\Documents and Settings\All Users\Application Data\Csrss\csrss.exe” These new run entries allow Locky to keep persistence as each is copied into a separate location under the file name csrss.exe. |
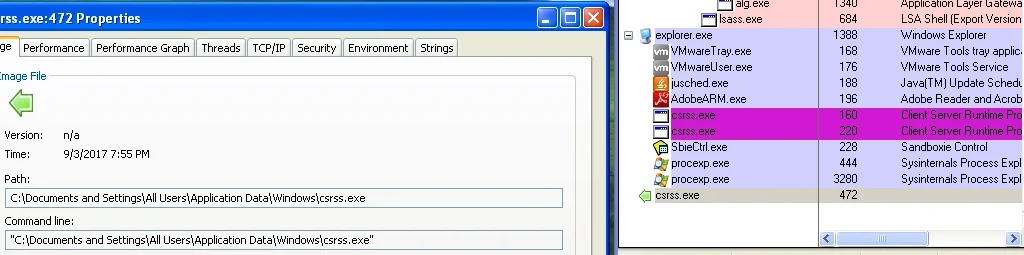
Figure 9 csrss.exe created in %appdata% location
In the memory strings, we found the following router list details:
• router_purpose_to_string
• router_get_all_orports
• D27178388FA75B96D37FA36E0B015227DDDBDA51
• B59F6E99C575113650C99F1C425BA7B20A8C071D
• A61682F34B9BB9694AC98491FE1ABBFE61923941
• 9DCD8E3F1DD1597E2AD476BBA28A1A89F3095227
• 9904B52336713A5ADCB13E4FB14DC919E0D45571
• 98CC82342DE8D298CF99D3F1A396475901E0D38E
• 87326329007AF781F587AF5B594E540B2B6C7630
• 57B85409891D3FB32137F642FDEDF8B7F8CDFDCD
• 0E7E9C07F0969D0468AD741E172A6109DC289F3C
• 09CD84F751FD6E955E0F8ADB497D5401470D697E
• download_status_reset_by_sk_in_cl
• routerlist.c
• dlstatus
• download_status_is_ready_by_sk_in_cl
• certs_out
• authority_cert_get_all
• fp-sk/
A static search of the memory strings found there is already information on github (https://github.com/kaist-ina/SGX-Tor/blob/master/Enclave/TorSGX/routerlist.c) which maintains a global list of router information for known servers.
• $F397038ADC51336135E7B80BD99CA3844360292B~F397038ADC51336135E at 76.73.17.194
• C:\Documents and Settings\Application Data\tor
• C:\Documents and Settings\Application Data\tor\torrc
• C:\Documents and Settings\Application Data\tor\torrc-defaults
• WARN BOOTSTRAP PROGRESS=5 TAG=conn_dir SUMMARY=”Connecting to directory server” WARNING=”No route to host [WSAEHOSTUNREACH ]” REASON=NOROUTE COUNT=3 RECOMMENDATION=warn
• Windows XP
• F397038ADC51336135E7B80BD99CA3844360292B
The above global router information shows the application path and connection information for the available directory server. These can be exploited in the ransomware payload to make successful TOR connections.
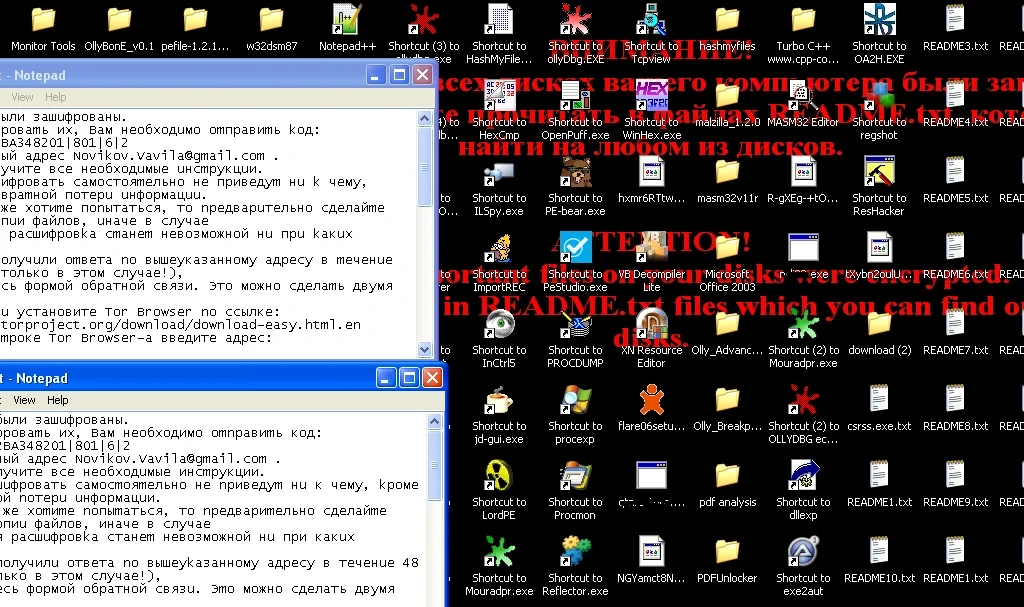
Figure 10 after infection of Locky ransomware
After successful infection, the victim’s desktop wallpaper is changed to a Locky ransomware message. It asks the victim to open one of a dozen readme files. These can be found on the desktop and in the C: folder:
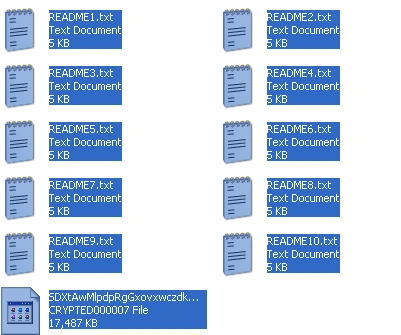
Figure 11 Readme files and crypted file
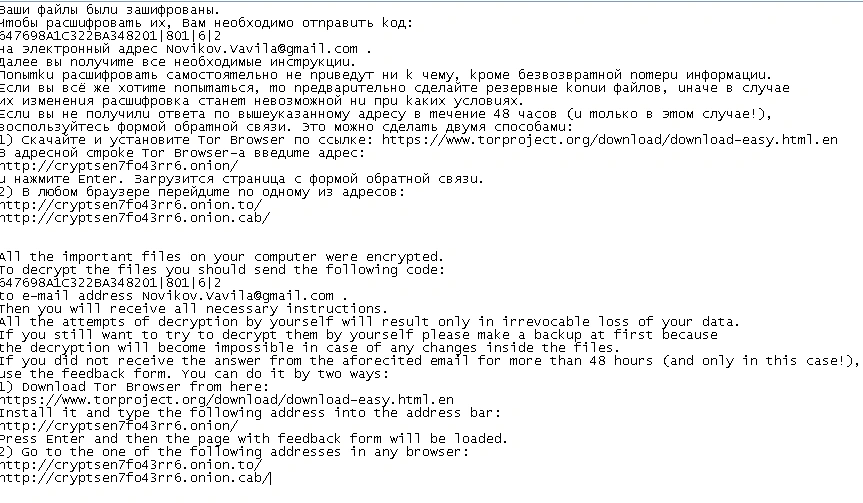
Below is the ransom note victims see:
Threat Indicators – IOC details:
Fake Dropbox URL:
hxxp://busad(.)com/dropbox.html
hxxp://autoecoledufrene(.)com/dropbox.html
hxxp://autoecoleboisdesroches(.)com/dropbox.html
hxxp://tasgetiren(.)com/dropbox.html
hxxp://potamitis(.)gr/dropbox.html
hxxp://jaysonmorrison(.)com/dropbox.html
hxxp://arthurdenniswilliams(.)com/dropbox.html
hxxp://gruporoados(.)com/dropbox.html
hxxp://patrickreeves(.)com/dropbox.html
hxxp://eifel-netz(.)de/dropbox.html
hxxp://albion-cx22(.)co.uk/dropbox.html
hxxp://jakuboweb(.)com/dropbox.html
hxxp://flooringforyou(.)co.uk/dropbox.html
hxxp://binarycousins(.)com/dropbox.html
hxxp://dar-alataa(.)com/dropbox.html
hxxp://gestionale-orbit(.)it/dropbox.html
hxxp://aegelle(.)com/dropbox.html
hxxp://griffithphoto(.)com/dropbox.html
hxxp://fachwerkhaus(.)ws/dropbox.html
hxxp://melting-potes(.)com/dropbox.html
hxxp://willemshoeck.nl/dropbox.html
hxxp://benjamindiggles(.)com/dropbox.html
hxxp://avtokhim(.)ru/dropbox.html
hxxp://autoecoleathena(.)com/dropbox.html
hxxp://bayimpex(.)be/dropbox.html
IP addresses:
176(.)56(.)58(.)114
185(.)18(.)197(.)109
173(.)192(.)66(.)137
203(.)183(.)65(.)225
194(.)173(.)175(.)16
62(.)4(.)8(.)233
67(.)19(.)68(.)83
47(.)89(.)249(.)74
199(.)30(.)241(.)139
202(.)237(.)149(.)19
66(.)84(.)8(.)235
83(.)169(.)22(.)79
91(.)121(.)111(.)185
91(.)209(.)7(.)116
91(.)234(.)195(.)48
Locky download and related URL:
gbass(.)ch/tJHGskdioj
garage-fiat(.)be/tJHGskdioj
futurehemp(.)com/tJHGskdioj
furukawa-iin(.)net/tJHGskdioj
freevillemusic(.)com/tJHGskdioj
vinneydropmodorfosius(.)net/af/tJHGskdioj
hightechavenue(.)com/tJHGskdioj
greatesthits.mygoldmusic(.)com/tJHGskdioj
graficasicarpearanjuez(.)com/tJHGskdioj
goldenspikerails(.)net/tJHGskdioj
hecam(.)de/tJHGskdioj
hdvmedia(.)nl/tJHGskdioj
go-coo(.)jp/tJHGskdioj
gewinnspiel-sachsenhausen(.)de/tJHGskdioj
gestione.easyreplica(.)com/tJHGskdioj
Pattern of php files in malicious URL:
Regex for the php file: \/w\/[0-9a-z]{4}\.php
konferencjaora[.]pl/w/523f.php
autonikos[.]pl/w/6dty.php
oxfordschoolkotputli[.]com/w/vait.php
j3[.]rodolfogn[.]com/w/qn0b.php
martinagebhardt[.]hu/w/uol4.php
Ransom note:
To decrypt the files you should send the following code: 647698A1C322BA348201|801|6|2
Email: Novikov(.)Vavila(at)gmail(.)com
Tor addresses in the ransom note:
hxxp://cryptsen7fo43rr6(.)onion/
hxxp://cryptsen7fo43rr6(.)onion.to/
hxxp://cryptsen7fo43rr6(.)onion(.)cab/
Extension: 647698A1C322BA348201.crypted000007
Conclusion: As long as Locky continues to successfully encrypt victim machines, it will continue resurfacing. We recommend users apply the IOC details as alerts, in order to block the infection methods (in this case, the malicious zip file and fake Dropbox links used to distribute Locky).
As always, exercise caution when receiving emails with attachments from unknown users. Finally, updated anti-malware with anti-ransomware modules can help protect against ransomware attacks.


