
Earlier this year, the creator of the Nanocore Remote Access Trojan (RAT), Taylor Huddleston, pled guilty to aiding and abetting computer intrusions by selling his creation online for as little as $25. He’s due for sentencing later this week and faces up 10 years in prison.
As an interesting side note, before pleading guilty Huddleston’s defence argued that Nanocore was created as a legitimate program, designed to give users a simple way to control their computers remotely.
Despite being collared by authorities, his legacy lives on. Nanocore is still one of the most popular RATs, and is being used by hackers around the globe.
Developed in dot NET, it is one of the most sophisticated RATs we’ve seen. On top of the standard functionality you’d expect to see (key-logging, and mic and webcam access), it also includes an external Distributed Denial of Service (DDoS) plugin which enables hackers to use victim machines as a proxy to bring down a third-party server, as well as a ransomware-like feature to lock people out of their PCs.
Overview
Once Nanocore compromises a system, it gives attackers almost complete control over the infected machine. In addition to the features mentioned above, it opens a back door on the computer, enabling an attacker to perform the following actions:
• Transfer and execute files
• Enter and execute commands
• Edit the registry
• View the desktop
• Create instant message windows
• Update the Trojan
• Manage running processes
• Steal passwords stored in web browsers and email clients
Distribution
Nanocore is usually spread via spam emails with malicious attachments or an embedded JavaScript file (.js).
In a campaign discovered by LMNTRIX researchers late last month, French users were targeted with a PDF file with embedded JavaScript. Once opened, a HTA (HTML Application) file payload was downloaded from Google Drive. This method bypassed Adobe security warnings by taking advantage of Google’s reputation.
The PDF displayed a fake notification stating the user’s Flash Player was outdated, prompting the installation of an updated version.
The downloaded .HTA file contained VBScript which decoded the embedded binary payload, and downloaded it into the %TEMP% directory of the target machine before execution.
Persistence
Upon infection, the malware drops winlogon.exe in the Startup Folder so it executes on every reboot:
C:\Users\<user-name>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\winlogon.exe.lnk
File Details
| File Type | Portable Executable (PE) file |
| Md5 hash | 25640ca48d3fbfd7e070b7685c053b51 |
Static Analysis
The screenshot below shows the recent Nanocore sample is written in dot NET:
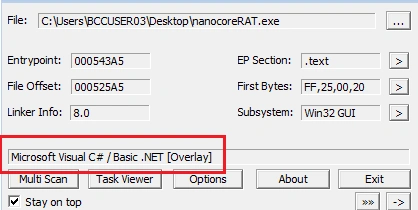
Static analysis immediately uncovered some suspicious strings which gave away the file’s malicious nature:
• GetProcAddress (gets current process address)
• KillOnExit (checks for some parameters, exits all processes if parameters are true)
• HttpWebClientProtocol
• set_Proxy (to use victim’s machine as proxy)
• CreateDecryptor
• CreateEncryptor (to encrypt files)
• GetCurrentProcess (checks current process)
• GetProcessesByName (checks process name)
Dynamic Analysis
The following diagram represents the chain of activities which occurred during infection:
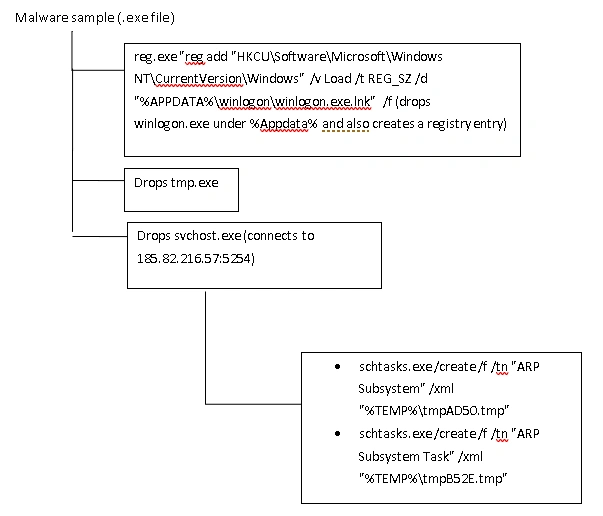
Once executed, the malware’s behavior can be seen in the below screenshot:
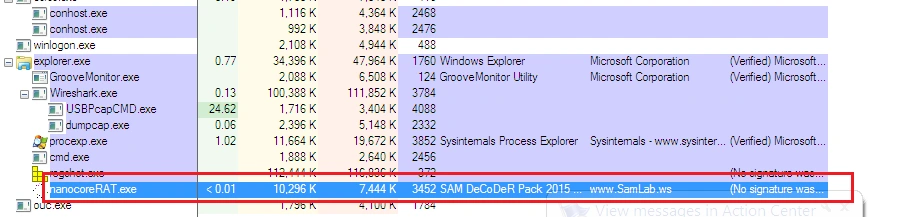
We witnessed the sample drop and execute “tmp.exe” and “svchost.exe”, and connect to the IP address “185.82.216.57” via port “5254”:
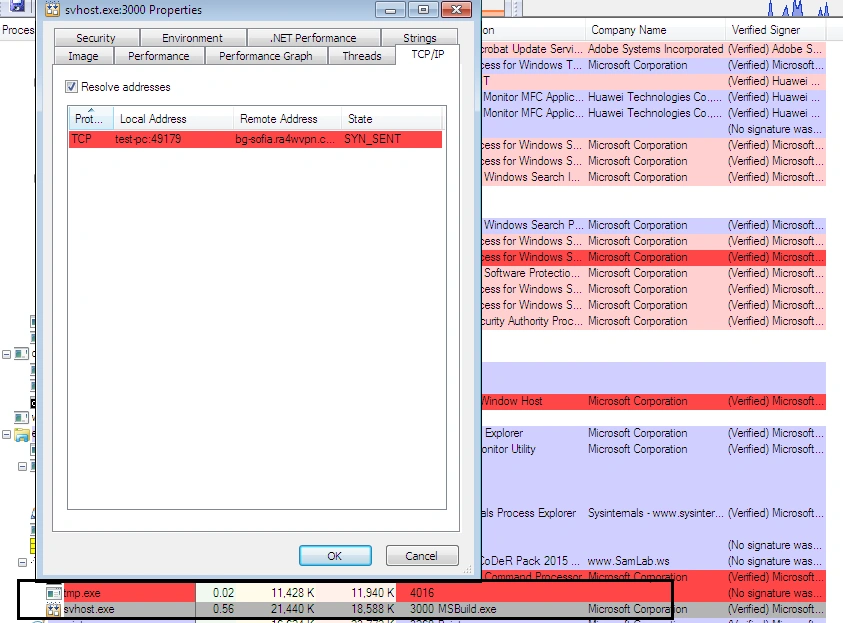
This IP was contacted in regular intervals:
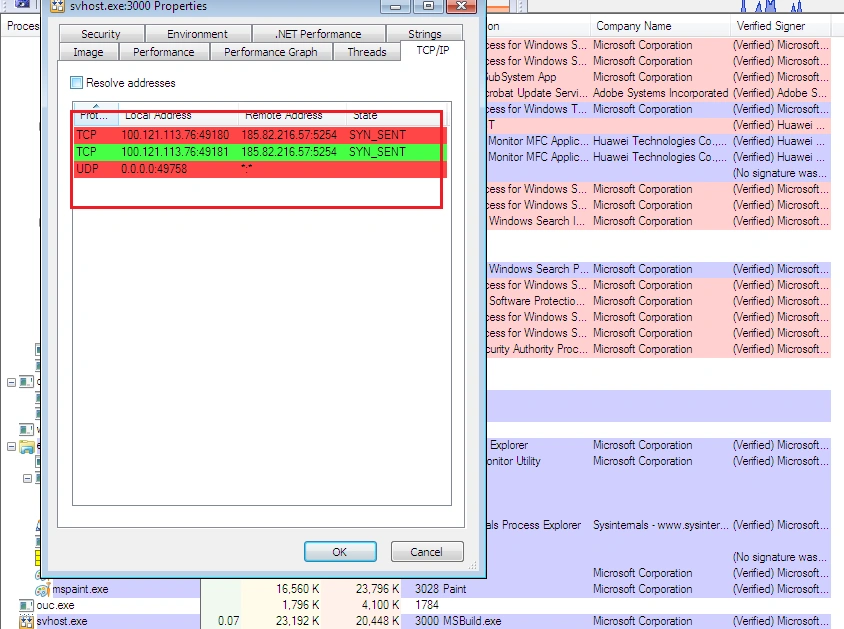
Once these steps were completed, “svchost.exe” started running as a background process:
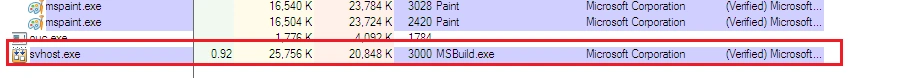
During the infection, the following files were dropped…
• C:\Users\<user-name>\AppData\Roaming\tmp.exe md5: df145cc72ceb0db5881ed33961e678b9
• C:\Users\<user-name>\AppData\Roaming\winlogon\winlogon.exe md5: 25640ca48d3fbfd7e070b7685c053b51
• C:\Users\test\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\winlogon.exe.lnk (to maintain persistence)
… and the following registry value was created:
HKU\S-1-5-21-132656071-2218712632-614148903-1000\Software\Microsoft\Windows NT\CurrentVersion\Windows\Load: “C:\Users\<username>\AppData\Roaming\winlogon\winlogon.exe.lnk”
Indicators of compromise
All files
• 25640ca48d3fbfd7e070b7685c053b51
• df145cc72ceb0db5881ed33961e678b9
• 9d9d45a925cec55f0b7456cf82c30f08
• 74e3f9da2862e544a1561af43a99da77
• 47d469fdff50ba8df9d474343896d27c
Command and Control
The below IP addresses and URL were contacted, indicating the malware’s C&C servers:
• 42.202.71.145
• 41.207.196.84
• 185.82.216.57:5254
ajam62[.]hopto[.]org
Registries added
HKU\S-1-5-21-132656071-2218712632-614148903-1000\Software\Microsoft\Windows NT\CurrentVersion\Windows\Load: “C:\Users\<username>\AppData\Roaming\winlogon\winlogon.exe.lnk”
Prevention
In addition to the fundamental basics (keep operating systems patched, security licenses updated and don’t open suspicious email attachments), users should disable Autorun to prevent any external devices from automatically executing and enforce file sharing protection policies.


