
Over the last three days LMNTRIX Labs has been tracking an influx of GandCrab ransomware. The ransomware samples are being pushed by RIG Exploit delivery channels.
The sample we discovered for analysis is: 5d53050a1509bcc9d97552fa52c1105b51967f4ccf2bde717b502605db1b5011
File size: 129 KB
Infection
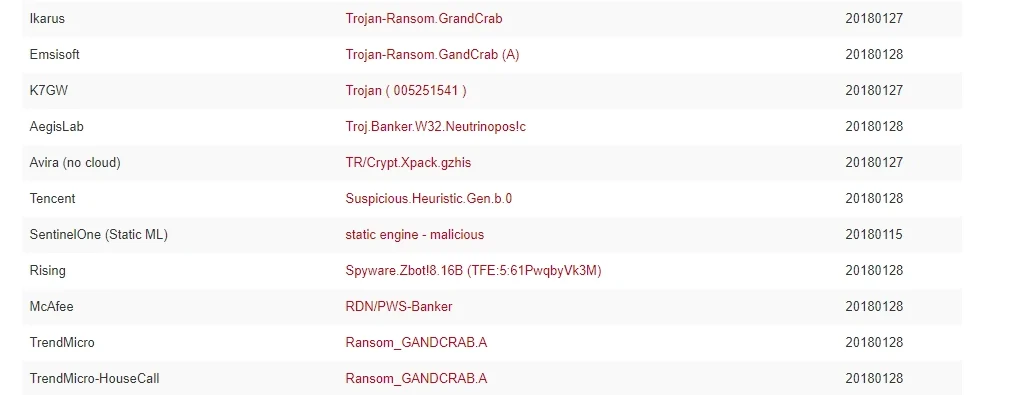
Figure 1 Ransom_GANDCRAB detection
Versions and resources of both the files are same:
Figure 2 Resource -Icon of the file
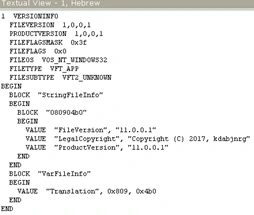
Figure 3 Versions details of both the ransomware samples
Encryption
We loaded the sample in our debugger to further explore the malware’s behaviour:
00401424 |. FF15 54F04000 CALL DWORD PTR DS:[<&KERNEL32.GlobalAlloc>] ; \GlobalAlloc
GlobalAlloc functions are used in memory management, mostly in decrypting or decoding the codes in the file.
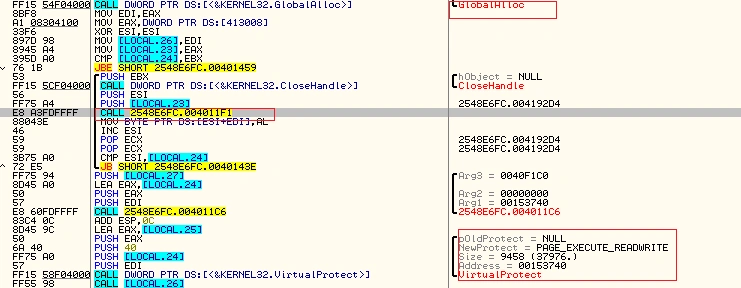
Figure 4 decoding functions
We traversed to the highlighted subroutines in the above snapshot: Address 4011F1. When we execute all those instructions, we arrived at the below location:

Figure 5 Jmp to decrypting code
After further debugging the code, we found the file included a number of anti-debugging tricks:
| 0405927: call dword ptr [0040F0CCh] //IsDebuggerPresent@KERNEL32.DLL |
| 040592d: mov dword ptr [004153B8h], eax |
| 040593a: push 00000000h |
| 040593c: call dword ptr [0040F0C8h] //SetUnhandledExceptionFilter@KERNEL32.DLL |
| 0405942: push 0040F530h |
| 0405947: call dword ptr [0040F0C4h] //UnhandledExceptionFilter@KERNEL32.DLL |
| 040594d: cmp dword ptr [004153B8h], 00000000h |
| 0405954: jne 0040595Eh |
| 0405956: push 00000001h |
| 0405958: call 00409B47h |
| 040595d: pop ecx |
| 040595e: push C0000409h |
| 0405963: call dword ptr [0040F0C0h] //GetCurrentProcess@KERNEL32.DLL |
| 0405969: push eax |
| 040596a: call dword ptr [0040F068h] //TerminateProcess@KERNEL32.DLL |
The above code all centres on anti-debugging tricks. We also observed multiple network-related artefacts in the code:
| 0406ddb: push dword ptr [esi+04h] |
| 0406dde: call dword ptr [004091D0h] //InternetConnectW@WININET.DLL |
| 0406e2a: push 00410938h //HTTP/1.1 |
| 0406e30: push dword ptr [ebp+28h] |
| 0406e34: call dword ptr [004091C4h] //HttpOpenRequestW@WININET.DLL |
| 0406e4d: call dword ptr [004091C0h] //HttpSendRequestW@WININET.DLL |
| 0406e96: call dword ptr [004091D4h] //InternetReadFile@WININET.DLL |
These instructions are picked selectively to spot network connection calls. During our analysis, we observed the malware contact the following domains:
• ipv4bot.whatismyipaddress.com – this is used to detect the network’s IP address.
• a.dnspod(.)com – we checked this in Virustotal which Fortinet AV flagged as malware.
Registry entries and file creation:
A duplicate MD5 of the parent file is dropped in the %appdata%\Microsoft folder with a random name.
| C:\Documents and Settings\UserName\Application Data\Microsoft\wgpspj.exe |
And same file is targeted in the created registry key:
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce “ulclieptfog” Type: REG_SZ Data: “C:\Documents and Settings\UserName\Application Data\Microsoft\wgpspj.exe” |
To find the randomness of the file name and registry key value, we reverted to the clean state before executing the file. A duplicate file gets created with <random name.exe>. The ‘Runonce’ key’s value part is also randomly generated. An example is below:
| C:\Documents and Settings\UserName\Application Data\Microsoft\<random file name.exe> |
Random value:
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce “<random value part>” Type: REG_SZ Data: “C:\Documents and Settings\UserName\Application Data\Microsoft\<random file name.exe>” |
In %appdata% location, the malware drops a text file called ‘GDCB-DECRYPT.txt’. This contains the malware’s ransom note. The user is instructed to purchase a private key after downloading the Tor browser:
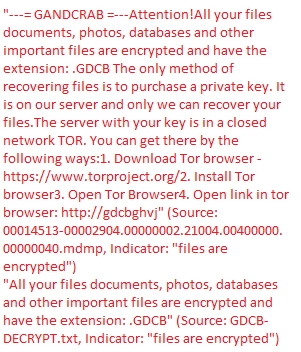
Figure 6 GDGB-DECRYPT.txt
Threat Indicators – IOC details
File Hashes:
SHA 256: 5d53050a1509bcc9d97552fa52c1105b51967f4ccf2bde717b502605db1b5011
Malicious domain:
a.dnspod(.)com
TOR Link:
hxxp://gdcbghvjyqy7jclk.onion.top/259a4fdc3766943
hxxp:// gdcbghvjyqy7jclk.onion.casa/259a4fdc3766943
hxxp://gdcbghvjyqy7jclk.onion.guide/259a4fdc3766943
File extension added by this variant of ransomware:
.GDCB
Registry key:
Key: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE”
Value: “Random value name on each execution”
Physical location: %appdata% under <Microsoft folder> <Random file name on each execution>
Conclusion
We advise users to apply the IOC details and set alerts in order to prevent infection. Further, users should always exercise caution when receiving attachments from unknown users.
Updated anti-malware with anti-ransomware modules can also help combat ransomware attacks.


