
Overview
The latest malware to cross our desks is the alliterated Rapid Ransomware – a strain that seemingly rolls off the tongue easier than it rolls into computers. From its earliest days, anti-virus vendors were successful in identifying the strain based on heuristic rules.
As yet, little is known about the strain’s distribution method, but analysis on the sample itself uncovers some interesting characteristics.
Sample Details
File Hash (SHA-256): cdd7cde605f034698b9f6502e71154c250143b98dc677fecb18f1d376e0617c2
File Size: 886272 bytes
PE type: EXE
Static Analysis
Before disassembling the sample, our researchers collected the static properties such as compiler used, creation details, and the sample’s blacklisted APIs:
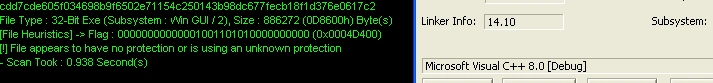
Figure 1 Compiled by VC++
Timestamp details show us the malware was created on December 29 last year, but it is still being seen in the wild more than a month later.
It was first uploaded to VirusTotal on New Year’s Eve, and while it was initially flagged by AV tools on heuristic rules, it is now detected specifically as ‘Rapid Ransomware’.
Below, we outline the sample’s blacklisted APIs which also identifies its anti-debug functionalities. As well as the common APIs we’d expect to see in a ransomware sample such as GetLogicDrive, CryptEncrypt, CryptImportKey, CryptExportKey, CryptSetKeyParam, CryptDestroyKey, CryptGenKey, and CryptAcquireContextA, we also see:
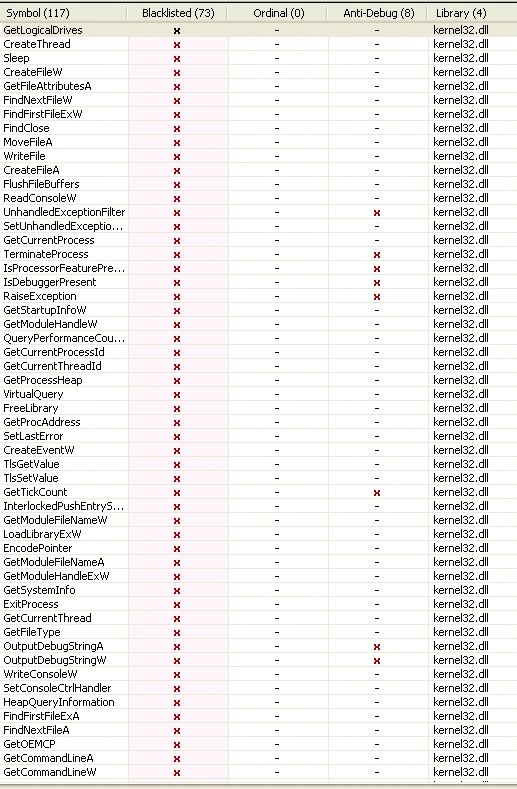
Figure 2 Usage of Blacklisted API and Anti-debug API
Static analysis also uncovered a number of interesting strings, listed below:
| .text:0xABACE ! How Decrypt Files.txt .text:0xABC48 \info.exe .rdata:0xAC41B Software\Microsoft\Windows\CurrentVersion\Run .rdata:0xACA95 RegOpenKeyEx .rdata:0xACB76 RegQueryValueEx .rdata:0xACB89 RegCloseKey .rdata:0xAD7CE f:\dd\vctools\crt\vcruntime\src\eh\std_type_info.cpp .rdata:0xAD91D f:\dd\vctools\crt\vcruntime\src\internal\per_thread_data.cpp .rdata:0xAF99F minkernel\crts\ucrt\src\appcrt\misc\dbgrpt.cpp .rdata:0xAFAEF minkernel\crts\ucrt\src\appcrt\stdio\_file.cpp .rdata:0xB810B minkernel\crts\ucrt\inc\corecrt_internal_stdio_output.h .rdata:0xBCD28 Client hook allocation failure. .rdata:0xBDE93 Object dump complete. .rdata:0xBE2CB minkernel\crts\ucrt\src\appcrt\startup\argv_parsing.cpp .rdata:0xBE308 minkernel\crts\ucrt\src\desktopcrt\env\environment_initialization.cpp .rdata:0xBE4DE minkernel\crts\ucrt\src\appcrt\startup\onexit.cpp .rdata:0xBF0B7 minkernel\crts\ucrt\src\appcrt\locale\wsetlocale.cpp .rdata:0xBF22D minkernel\crts\ucrt\src\appcrt\internal\per_thread_data.cpp .rdata:0xC2237 minkernel\crts\ucrt\src\appcrt\misc\signal.cpp |
In the below snapshot, we can see the ransomware adds the extension ‘.rapid’ to encrypted files, the file drop location is %appdata%, as well as the contact email address for file restore.
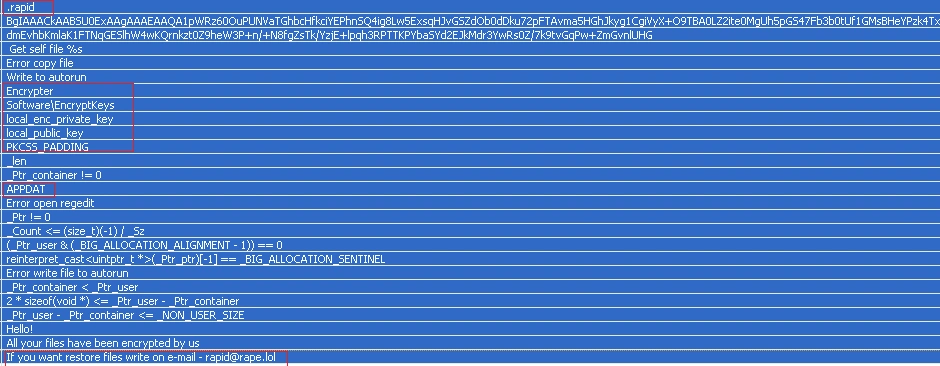
Figure 3 Interesting strings
Having analysed the string details and blacklisted API usage, we next disassembled the sample to study its characteristics:
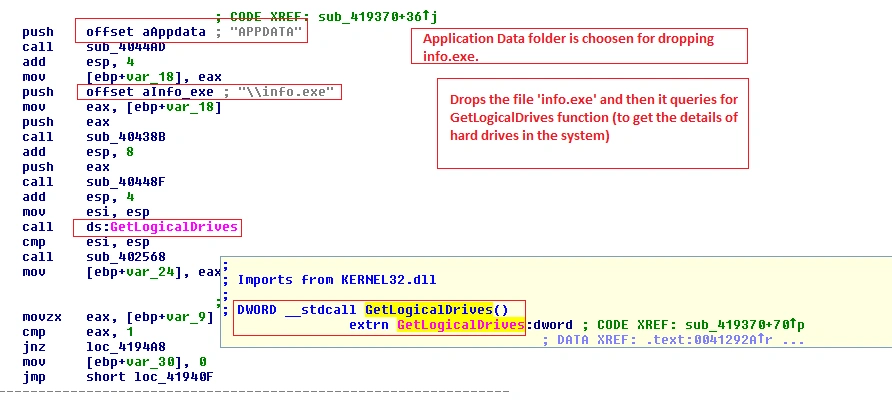
Figure 4 File ‘info.exe’ and queries logical drive info
The query ‘GetLogicalDrives()’ collects information for the logical drives that can be found in the victim system. It does so by retrieving an integer as bitmask value.
For example, if the function returns a value of ‘4’, then its equivalent binary is 100 – this could mean either C, B, or A (though A and B are not present) so the only available drive is C.
Below we see the functions responsible for replacing file extensions with ‘.rapid’:
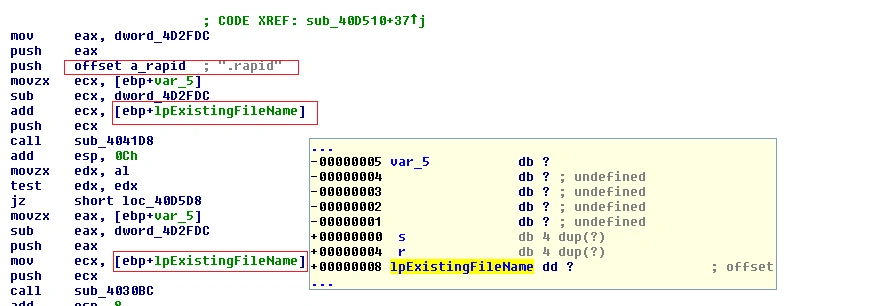
Figure 5 ‘.Rapid’ file extension
As mentioned in the blacklisted API, we found the ‘cryptencrypt’ function in the disassembled code which is used to encrypt the data. Its associated function, ‘Cryptgenkey’, generates a cryptographic session key. The below snapshot shows the ‘cryptencrypt’ function in use:
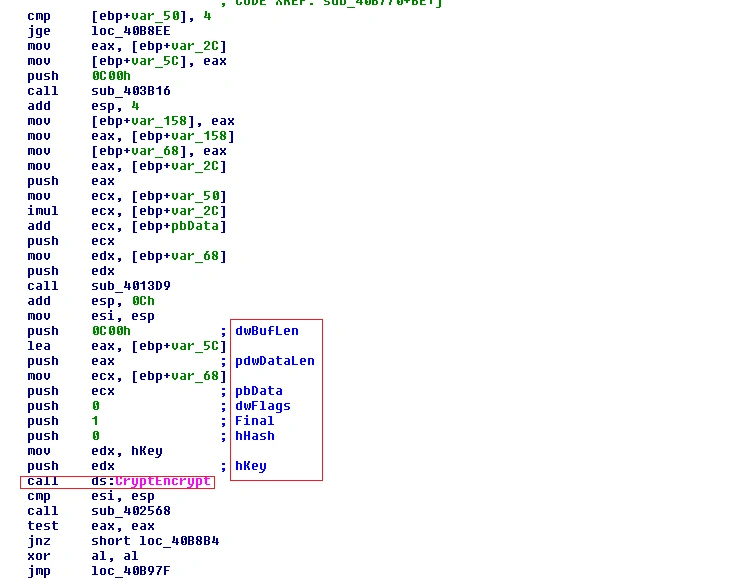
Figure 6 CryptEncrypt ()
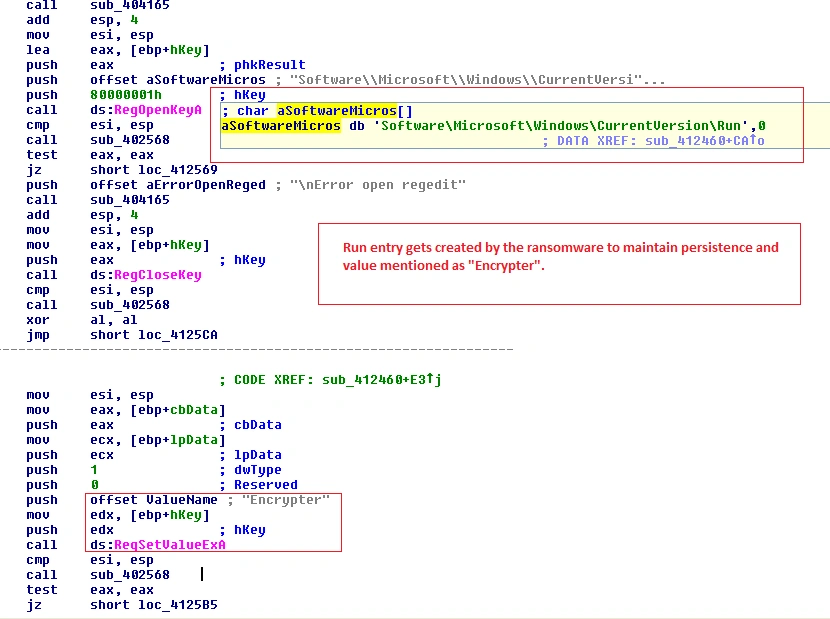
Figure 7 Run Registry entry
For maintaining persistence, the malware uses the above run registry entry, while info.exe is dropped in the %appdata% location. With the value of the registry entry as ‘Encrypter’, this gives the appearance that the registry entry belongs to a legitimate application, rather than a malicious one.
Contents of how to decrypt files:
| Hello! All your files have been encrypted by us If you want restore files write on e-mail – rapid(at)rape(.)lol |
Threat Indicators/IOC Details
File Hash (SHA-256):
• cdd7cde605f034698b9f6502e71154c250143b98dc677fecb18f1d376e0617c2
Dropped Files:
• info.exe (under %appdata% location)
• ‘! How Decrypt Files.txt’
E-mail:
• rapid(at)rape(.)lol
Registry entry:
• Run entry created with the value as “Encrypter”.
File extension:
• .Rapid
Conclusion
The above IOC details can help security professionals detect this ransomware.
Standard computer hygiene practices like regular backups and exercising caution when dealing with emails and attachments from unknown senders are the best defence against most ransomware attacks.
In this case, as most AV vendors detected this ransomware with heuristic rules from the day it appeared on the internet, updated anti-virus with latest definition should protect most users.


