
Recently LMNTRIX threat intelligence has observed a sudden spike in open-source ransomware across the Dark Web, and HiddenTear is topping the list. The initial propagation of HiddenTear was from a Github project started by UtkuSen, with a disclaimer that the code was published for educational purposes.
Korean threat actors are believed to have taken over the HiddenTear project and have developed multiple variants of the ransomware in different programming languages. These variants now appear to be being traded openly on the Dark Web, raising the spectre of impending harm to a range of industries as the volume of harder-to-detect ransomware increases.
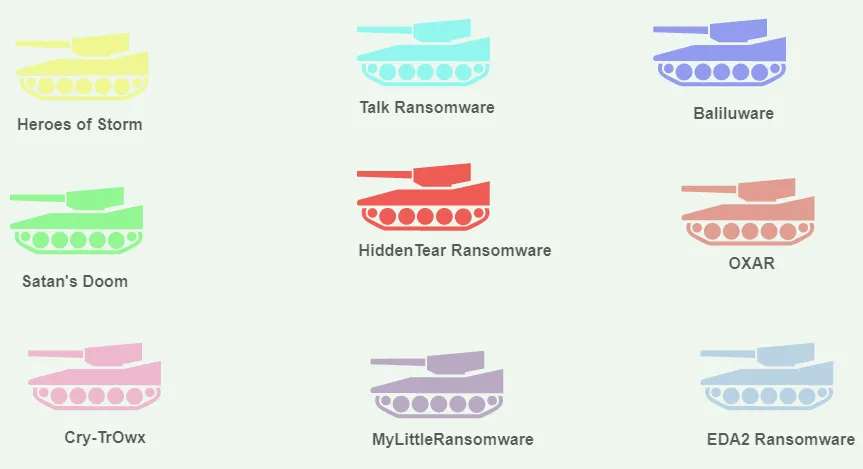
Our team has observed multiple such variants in the Dark Web. Below is a list of of HiddenTear ransomware variants that are available as of today:
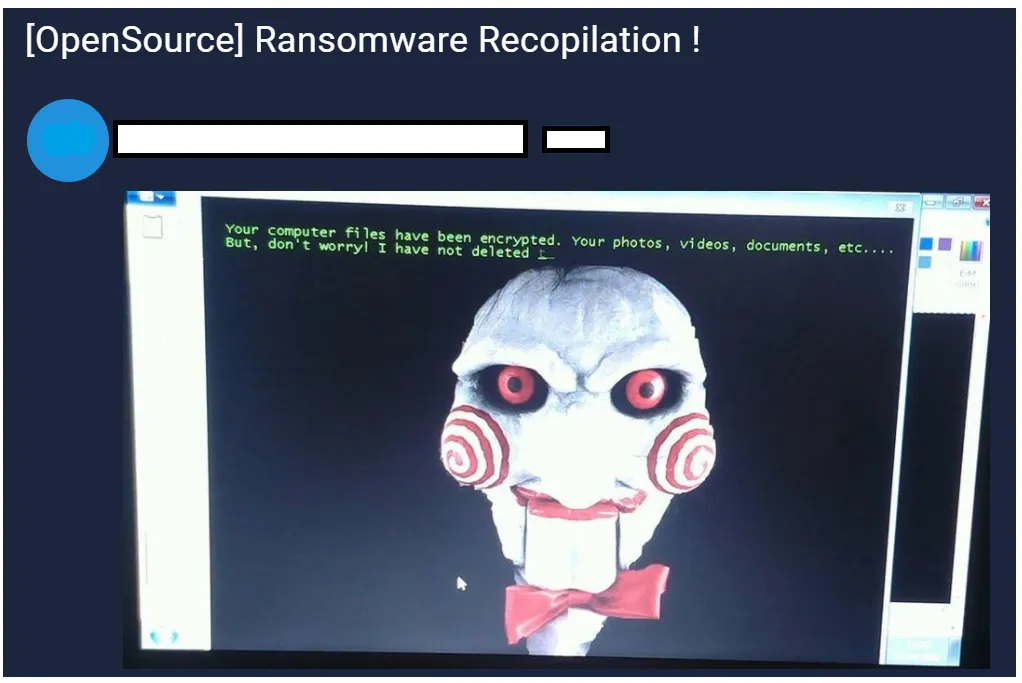
The Dark Web appears to be fascinated with open-source ransomware, with selling boards everywhere calling it an “[OpenSource] Ransomware Recopilation”
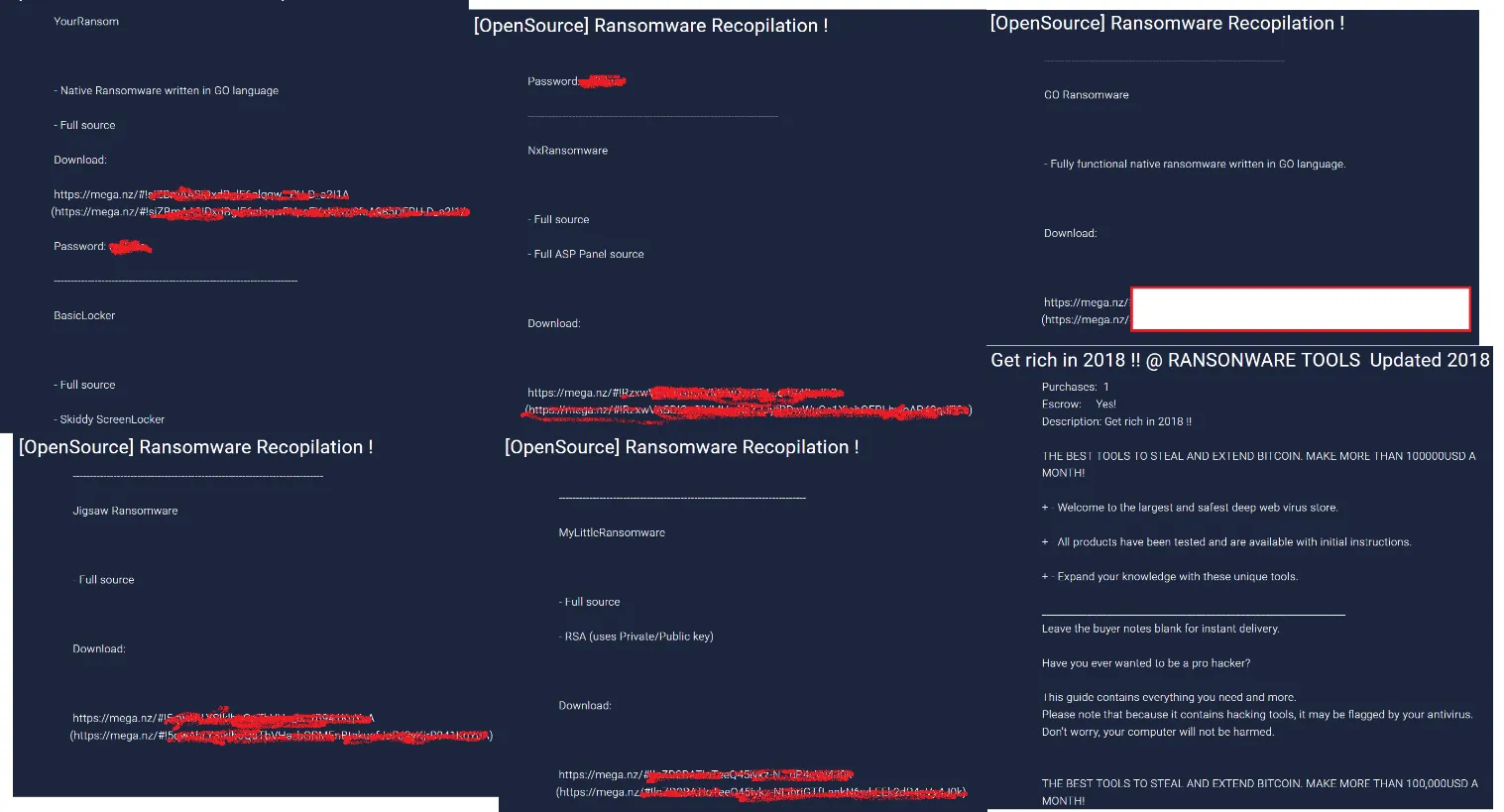
There are various types of open-source ransomware being sold in the dark markets, complete with download links and passwords. Some of the variants include the following:
Andr0id L0cker – Panel + Source Java
BasicLocker – Source C#
CryptoLocker – Source C#
CryptoWire – Source AutoIT
GO Ransomware – SourCe GO
HiddenTear – Source C#
M.D.Groot Ransomware – Source C#
MyLittleRansomware – Source C#
NxRansomware – Source + Panel C#
Shell Screen Locker – Source VB
YourRansom – Source GO
Here are a few screenshots showing some of them:
In order to validate the authenticity of some of these download links we tried to download the “Go Ransomware” sample – and –Bingo!– the download link proved active.
Code Analysis:
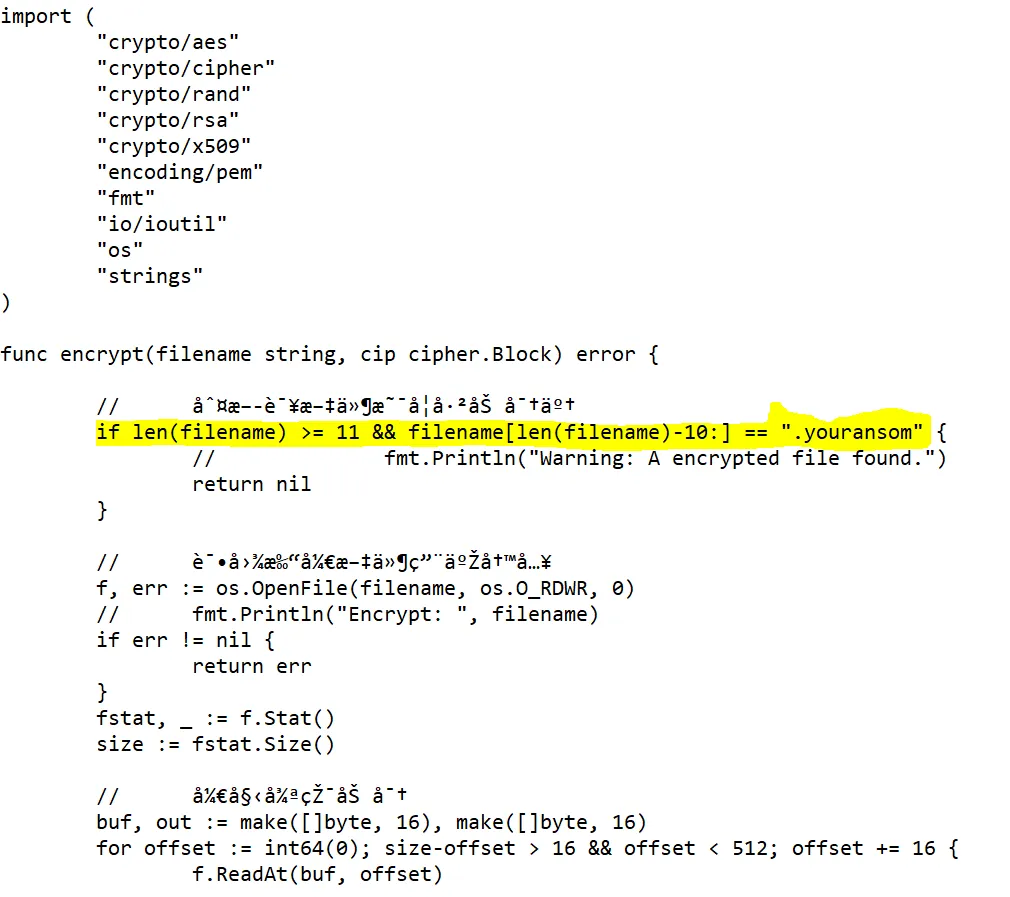
The “Main.go” module consists of an “If “ function (as shown in the highlighted section above) , and all files matching the condition are encrypted with the extension “.youransom”.
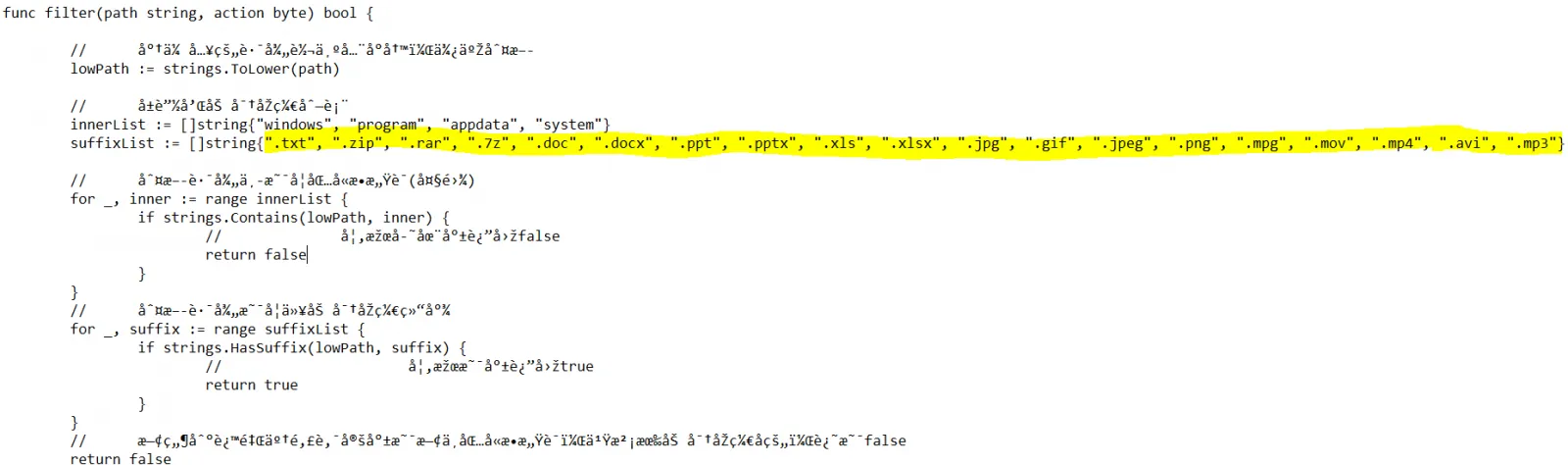
In the Filter function (below) we can see the suffix list, which are the file types for which the Ransomware performs the encryption.
The combination of open-source and the darknet is a significant one because it encourages the ready morphing of a possible limitless number of variants that will thwart detection. We will continue to monitor this trend.


