
Introduction
When looking to defend your IT infrastructure from ransomware, easily one of the top threats if not the top threat faced by enterprises in 2023, you will see the same advice worded differently time and time again. Advice like better access controls, routine patch management, adding an extra dose of phishing training, and, having a working backup at hand are continually recommended. For good reason, they will harden your infrastructure against an attack but is it enough? Ultimately, no. We have found that to combat ransomware you have to approach the matter differently to enable effective detection and a comprehensive response to a ransomware attack in the first place. Let us explain.
Despite popular belief, implementing the tried and tested best practices has not reduced the frequency of ransomware or mitigated its devastating effects on victims’ businesses. Meanwhile, relying on cyber insurance, awareness training and daily incremental backups only provide a “temporary” relief after the ransomware has wreaked massive amounts of collateral damage.
What these pearls of wisdom fail to recognize is that prevention frequently fails against motivated threat actors (who look to extort money in ransomware’s context), there is more to the fight than meets the eye. Preventing initial access is only half the battle relying on prevention has left several leaders running for cover when the media shenanigans get started.

Modern ransomware attacks are carried out in 3 stages;
- Opening Gambit – where the infection occurs, and initial access is established
- Mid Game – where the post compromise and lateral movement has started
- End Game – where the victim gets bullied with extortion and threat actors hope to get their money!
Each phase has its experts and tooling ecosystem, Eg: Info Stealing/Banking malware having two parts – one, perform the infections and two, perform the actual attack. Fighting in two of the three rounds hasn’t worked successfully so far according to a recent survey by LMNTRIX. Cyber defenders must fight at each stage to thwart the extortion scheme by human-operated ransomware actors.
The Opening Gambit
The attackers control the ransomware’s attack rhythm, throughout the three stages and they always have the upper hand from the start. As scary as it may sound to think about people breaking in and exfiltrating data, the infection doesn’t mean you’ve hit the end of the road. Your best bet to STOP ransomware from causing crippling damage to IT systems starts with your ability to see (threat visibility) and decisively respond to the infection “in progress” (threat response).
A common security phrase oft repeated in the last 5 years is “Shift Left Security”. Firewalls, IDS / IPS, SIEM, IAM, anti-phishing education, SOAR, and the humble EDR are preventive measures suggested to thwart the attack before they gain a foothold. A better idea would be to conduct a baseline test and perform vulnerability scans and remediation to reduce the overall attack surface. An unwelcome downer for Shift Left Security is a challenge faced in the security community, we call it the defender’s dilemma. It highlights the fact that the attacker, by virtue of overseeing of the what, when, and how of the attack, can gain an edge at the perimeter. While the attacker just needs to be right half the time, the defense must have all the controls in place before the attack. Preventive defenses against a persistent attacker are doomed to fail, as demonstrated by the cyber defender’s conundrum. Cybercriminals with advanced skills are aware of the resources that are essential to your organization’s success, including timely access to data, reliable software, and hard-working employees to get things done. Cybercriminals therefore, start taking advantage of such weaknesses as the path of least resistance to get inside.
As an industry, we despise accepting it, although history has repeatedly demonstrated that it is true. Consider the following statistics,
(1) How can initial access be prevented if humans are involved? After one year of phishing training, 4.8% to 5.0% of users from 23,000 enterprises will click. If an attacker sends 100 well-crafted emails with a 4.8% click rate, 99.27% will open the bait.
(2) Without social engineering, 93% of penetration tests succeed. Considering an average pen tester’s limited time, scope, and rules of engagement, a financially motivated criminal exercising stealth and patience has a higher chance of success.
(3) As we mentioned in another blog post, a skilled security team would be able to stop an attacker at the beginning of the kill chain, but it’s more realistic to attack where you have the edge. Persistent attackers will always find a way in no matter what, therefore the perimeter is merely a blurred line in protection. Thinking about this reality and adapting to this fact may affect how your company invests in security.
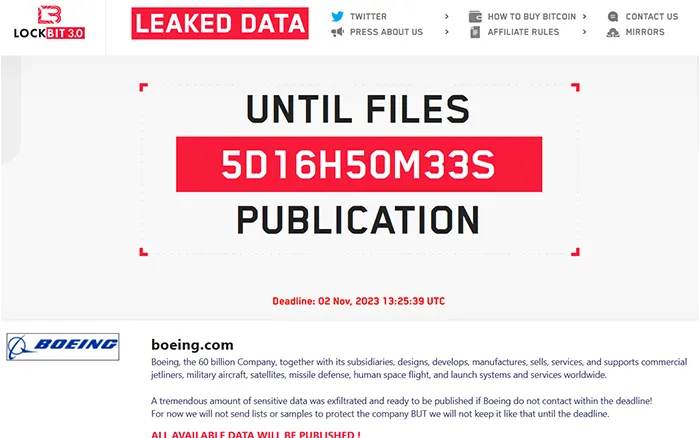
Representative Image: Lockbit – Data Leak
Why backup isn’t enough today?
Having backups and cyber insurance is prudent. The math, however, does not match when your insurance company will underwrite data that are infected with ransomware. This is because the extortion demand does not reflect the damage produced by modern ransomware operations, in which extortionists use manipulative human psychology (tactics like name & shame) to ensure you pay.

In 2021, for example, the average ransom payment was $170,000, negotiated down from astounding millions of dollars previously seen. However, the average ransomware impact in the same year was $1.85 million.
During the crisis, the media, insurance-sponsored negotiators, and most likely your company’s executives will be focused on the outrageous ransom demand. Backups and cyber insurance are unquestionably important components of your negotiating power. Although blackmail feels strange, unclean, and disgusting, it only amounts to 10% of overall weighted damage.
Once the ransomware attack begins, the impact of downtime, lost business, and other indirect effects including reputational harm and recovery expenses must be addressed. Stopping the attacker, reducing the dwell time, before the data is encrypted and the ransom notification is sent is the only method to be completely immune to ransomware. As we can observe, relying on perimeter security and then trying to recover data from your backup serves the interest of ransomware operators.
The Mid Game
In the middle phase, the ransomware intruder arrives blindly at the victim’s infrastructure and sets out to achieve their goals. Their requirements and tooling to find and pivot towards vital assets are recorded in leaked playbooks & insights offered by post-mortem reports from incident responders.
Ransomware teams, unlike advanced persistent threats (APT) or cyber espionage campaigns, are less concerned with the quality of what they compromise. They are more concerned with the quantity of data exfiltrated or, the consequence of the resulting compromise. Ransomware operators are likewise in a hurry, with an average of only five days to complete their play before raising their extortion stakes.
The inside of the victim network seems to an attacker to be a wide-open field to maraud through, or as LMNTRIX XDR would work – we deploy a maze of decoys, and breadcrumbs, which is being observed, providing the intruder a dilemma of sorts.
Five Opportunities to Detect Attackers & Stop Them In Their Tracks
Tellingly, in the middle of a strategic game, the advantage might shift from the attacker to the defender. Defenders should have a home-field advantage, be familiar with the environs, know what is expected of them, and, if they are observing, be aware of the internal users, resources, and workloads.
The ransomware midgame is driven by the need for attackers who want to get money to find, get into your network, and set up data all over the network before encryption starts. Each part of the network will use the same five strategies and procedures to simulate these acts until a critical mass of harm is reached. Every time an attacker gets into the network, the defense has a different chance to stop them before any damage is done or the ransom note is sent.
Reconnaissance / Enumeration
Once an attacker lands and starts growing their footprint within the environs, target detection and enumeration begin. Attackers using ransomware must learn about the environment because they arrive blind into the network. To obtain a sense of the situation, they begin by using conventional network scanning tools, such as Nmap, ping, scan, and pbnj as well as several other open-source tools readily available. Then to maximize damage while reducing dwell time, attackers target Active Directory (AD) services, according to playbooks observed by LMNTRIX for ransomware operators.
Active Directory Exploitation
Ransomware attackers build a base on any host that is vulnerable to reaching your network, systems, and data. But from that position, they might not have the rights they need to reach their goals. Intruders use weaknesses in the active directory hierarchy, decode hashed passwords left on hosts (LSASS), reuse stolen credentials, or take advantage of the many configuration mistakes on domain controllers to get in. With an increased set of privileges, attackers can now control additional resources and data services within the domain or a given network, changing their focus to lateral movement.
With an XDR solution such as LMNTRIX, though the attacker may feel he has total control, he may click on decoy resources in a bid to infect more systems or login to decoy user accounts resembling real users to spread the malware as a software update like a domain administrator. Hence vertical privilege escalation to Domain Admin is one of the most lucrative situations from a defender’s standpoint for detecting a human ransomware attacker.
Lateral Movement
Modern ransomware looks for a lot of information and assets before it starts encryption of said data. This helps the ransomware figure out how much money to ask for. Attackers extend their power past the base of operations by moving laterally through the victim’s environment and taking advantage of unreported and assumed-trusted east-west contacts. Ironically, attackers often use tools for living off the land that IT operations make available for managing systems across the whole network.
The tools most often observed by LMNTRIX CDC are PSexec, Remote Procedure Call, Powershell, WMI & Cobalt Strike.
C2 Server / Command & Control Obfuscation
After mapping the environment, making a list of assets, and marking data to compromise, the attacker calls home to the command and control (C2 server) infrastructure to get instructions and fetch more tools. Attackers use C2 server obfuscation techniques to avoid being found as they get through firewalls. One of the most popular methods to get past security controls is to build tunnels over protocols such as DNS / HTTP.
Extortion Data Staging
I am sure all of us can agree that data is aptly called the lifeblood of corporations. The leverage ransomware extortionists have over their victims is their inability to obtain their data. Ransomware extortion strategies target compromising file systems, databases, and backup platforms in addition to Active Directory as a quick way to improve their chances of getting paid.
In the mid-game, ransomware attackers use trusted connections between users and apps to get their hands on data inside the perimeter. This is called “land and pivot strategy in tech speak. Since these assumptions made in data access management “fail altogether”, attackers can use data & systems to store data before exfiltration.
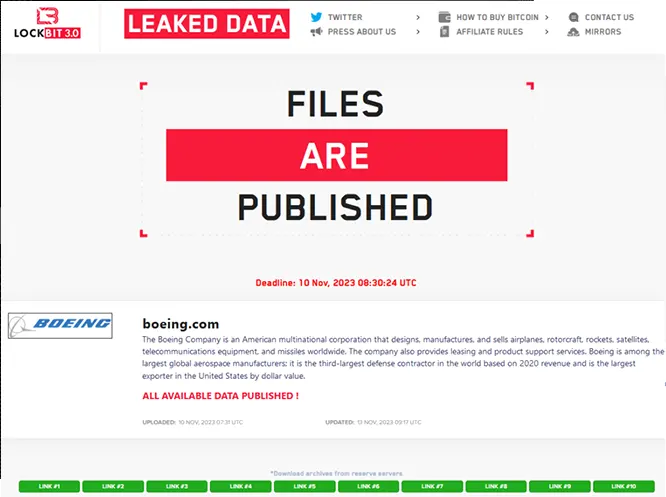
In Aug 2023, Graham Cluley, a senior researcher in the AV community had published an article – LockBit’s dirty little secret, detailing how the Lockbit ransomware gang is failing to publish victims’ data as part of their double extortion scheme.
Fast forward to Nov 2023, the Lockbit gang has actually published 43 GB of stolen data from Boeing’s attack.
Conclusion
Your company like a million others, will face an existential threat from modern ransomware. Every security leader must explain how they are bolstering their resistance to ransomware for years to come.
Cyber Defenders have a significant advantage when targeting modern ransomware campaigns in the mid-game stage. Life expands in proportion to the courage exercised by cyber defenders if they are ready to turn inward, introspect their security strategies and fight on the inside.
LMNTRIX Cyber Defenders bravely inventory a network’s data & assets, use the home field advantage, and regularly perform continuous monitoring, threat hunting & incident response – working round the clock to beat ransomware attackers at their own game…


