As organizations continue to face an increasing number of cyber threats, it is becoming more important than ever to have a robust security strategy that includes Network Detection & Response (NDR). NDR is a crucial component of any XDR solution as it provides real-time visibility and threat detection capabilities to help organizations identify and respond to network-based attacks. In this blog post, I will discuss what NDR is, how it works, its importance in an XDR solution, the types of threats it can detect, key features to look for in an NDR solution, and which vendors to consider when evaluating NDR solutions.
What is Network Detection & Response (NDR)?
Network Detection & Response (NDR) is a security solution that helps organizations detect and respond to network-based attacks. NDR solutions analyze network traffic in real-time to identify anomalies, suspicious behavior, and other indicators of compromise that may signal a security threat. The goal of NDR is to detect and respond to security threats in real-time before they can cause any significant damage to the organization.
How does NDR work?
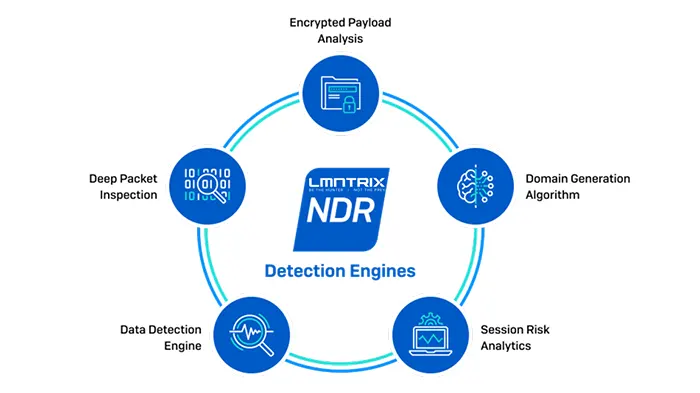
NDR solutions work by analyzing network traffic to detect potential security threats. NDR solutions typically use a combination of different techniques such as network traffic analysis, behavioral analysis, and machine learning to detect threats. The process typically involves the following steps:
- Traffic Analysis: NDR solutions analyze network traffic to identify any anomalies or suspicious behavior.
- Threat Detection: The solution uses various techniques to detect potential threats, such as looking for indicators of compromise or identifying behavior that is consistent with a particular attack.
- Alert Generation: Once a threat is detected, the NDR solution generates an alert, which is sent to the security team.
- Investigation: Security teams investigate the alert and determine whether it is a legitimate threat.
- Response: If the alert is confirmed to be a threat, the security team takes appropriate action to contain and remediate the threat.
The Importance of NDR in an XDR Solution
NDR is a critical component of any XDR solution. An XDR solution combines various security products and services to provide complete visibility and protection across an organization’s entire IT infrastructure and threat vector. NDR helps organizations identify and respond to network-based attacks, which are often the first point of entry for many attackers.
NDR provides real-time visibility into network traffic, allowing organizations to identify and respond to threats in real-time. By integrating NDR with other security products and services, organizations can create a comprehensive security strategy that covers all aspects of their IT infrastructure.
Within an XDR, each component is powerful on its own, but when integrated with other components that share context and intelligence between the detection engines, this creates a force multiplier that allows one to see the entire chain of an attack like a story. Imagine an attacker who establishes a point of breach that easily bypasses the AV and EDR tools that are in place but is then detected by deceptions when they try to move laterally, they trigger the NDR when they try to exfiltrate data to a C&C. During the post-breach investigation, the NDR is able to replay the attack, clearly showing the point of entry, lateral movement, and subsequent exfiltrated communication, followed by the dark web activity of the attacker trying to sell the newly established remote access they have gained to the enterprise.
Types of Threats that NDR Can Detect
NDR solutions can detect a wide range of security threats, including:
- Malware: NDR solutions can identify and block malware as it tries to enter the network.
- Botnets: NDR solutions can detect botnets and block them from communicating with their command and control (C&C) servers.
- Advanced Persistent Threats (APTs): NDR solutions can detect and track APTs as they move through an organization’s network.
- Insider Threats: NDR solutions can detect and alert on suspicious behavior from employees or contractors who may be attempting to steal data or damage systems.
Key Features to Look for in an NDR Solution
When evaluating different NDR solutions, there are several key features that enterprises should consider to ensure that they choose the right solution that meets their security needs.
- Real-Time Monitoring and Alerting: An NDR solution should provide real-time monitoring and alerting capabilities to help detect and respond to threats in a timely manner. The solution should be able to analyze network traffic and identify anomalies, alerting security teams when it detects potential threats.
- Network Visibility: A good NDR solution should provide complete network visibility, including monitoring both on-premises and cloud environments. It should provide visibility into all endpoints, devices, and applications, regardless of their location.
- Advanced Analytics and Machine Learning: An effective NDR solution should use advanced analytics and machine learning to detect and respond to threats. The solution should be able to learn from past incidents and use that knowledge to identify and respond to future threats.
- Threat Detection and Response: An NDR solution should be able to detect and respond to various types of threats, including malware, ransomware, phishing attacks, and other cyber threats. It should be able to isolate infected devices and prevent the spread of malware across the network.
- Incident Investigation and Forensics: An NDR solution should have the ability to investigate incidents and provide detailed forensic analysis to help security teams understand how the threat entered the network, what data was compromised, and the extent of the damage caused.
- Integration with Other Security Tools: A good NDR solution should integrate with other security tools such as firewalls, endpoint protection, and SIEM solutions. This integration allows for better threat detection and response across the security stack.
- Usability and Ease of Deployment: An NDR solution should be easy to deploy and use, with an intuitive user interface and straightforward configuration. It should also provide sufficient training and documentation to ensure that security teams can use the solution effectively.
Vendors to Consider when Evaluating NDR Solutions
When it comes to selecting a Network Detection and Response (NDR) solution, there are numerous vendors available in the market, each offering different features, capabilities, and price points. Enterprises should carefully evaluate their options to ensure they select the right NDR vendor that meets their security needs.
Here are some NDR vendors that enterprises should consider when evaluating different solutions:
- LMNTRIX: LMNTRIX XDR natively unifies Machine and Underground Intelligence, NGAV, EDR, NDR, UEBA, Cloud Security, Mobile Security and Deception Everywhere with completely automated attack validation, investigation, containment, and remediation on a single, intuitive platform. Backed by a 24/7 Managed Detection and Response service – at no extra cost – LMNTRIX provides very comprehensive protection of enterprises for even the smallest security teams that covers the entire attack surface. The LMNTRIX NDR strategy separates the NDR function into NTA (LMNTRIX DETECT) and Network Forensics (LMNTRIX HUNT).
- FireEye: FireEye is a well-known security vendor that provides a range of security solutions, similar to LMNTRIX, FireEye separates the NTA and network forensic functions into separate sensors namely the FireEye Network Forensics and FireEye Network Security. FireEye offers complete network visibility, threat detection, and response capabilities. The solution uses advanced threat intelligence to detect and respond to known and unknown threats.
- Cisco: Cisco is a well-known and established vendor in the network security industry. The company offers a range of security solutions, including an NDR solution called Cisco Stealthwatch. Stealthwatch provides network visibility, threat detection, and response capabilities by monitoring network traffic and analyzing behavior anomalies.
- Darktrace: Darktrace is an artificial intelligence (AI) powered NDR vendor that uses machine learning to detect and respond to cyber threats in real-time. The solution offers complete visibility across the network, including cloud and virtual environments. Darktrace’s unique approach to threat detection and response makes it a strong contender in the NDR market.
- ExtraHop: ExtraHop is a leading vendor in the network analytics and security industry. The company offers an NDR solution called Reveal(x), which provides complete visibility into network traffic, including encrypted traffic. Reveal(x) uses advanced analytics and machine learning to detect and respond to threats in real-time.
- Vectra AI: Vectra AI is an NDR vendor that uses AI to detect and respond to cyber threats in real-time. The solution provides complete visibility across the network, including cloud and virtual environments. Vectra AI uses AI algorithms to detect and respond to threats, making it an effective solution for detecting advanced threats.
- RSA: RSA is a well-known security vendor that offers a range of security solutions, including an NDR solution called NetWitness. NetWitness provides complete network visibility, threat detection, and response capabilities. The solution uses advanced analytics and machine learning to detect and respond to threats in real-time.
- Palo Alto Networks: Palo Alto Networks is a leading vendor in the network security industry. The company offers an NDR solution called Cortex XDR. Cortex XDR provides complete visibility into network traffic, including encrypted traffic. The solution uses advanced analytics and machine learning to detect and respond to threats in real-time.
When evaluating NDR vendors, enterprises should consider the vendor’s reputation in the industry, the completeness of their solution, their ability to detect and respond to advanced threats, and their price point. Enterprises should also evaluate the vendor’s support, training, and documentation offerings to ensure they have the necessary resources to effectively use the solution.
In conclusion, selecting the right NDR vendor is essential for any enterprise looking to strengthen their cybersecurity posture. Enterprises should evaluate different vendors, consider their capabilities, and make a well-informed decision based on their unique security needs.


