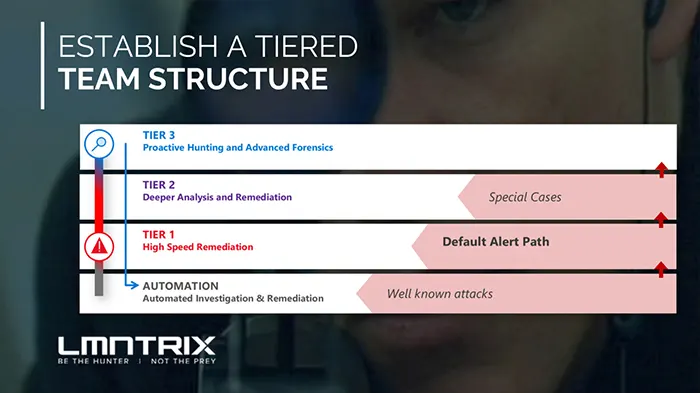
A tiered team structure is a common approach for organizing security operations centers (SOCs) as it allows for the efficient handling of incidents based on their severity and complexity. The tiers are usually defined as Level 1, Level 2, and Level 3, with each level having a specific set of roles and responsibilities.
As we have at LMNTRIX, you may also create incident management queues to align to this tiered team structure.
Level 1 (Frontline): The Level 1 team is responsible for the initial triage of security incidents. They are responsible for monitoring security systems, identifying potential security incidents, and escalating them to the next level if necessary. They are also responsible for basic incident response activities such as auto containment and isolating compromised systems and collecting initial data for incident analysis.
At LMNTRIX we refer to this team as the Threat Detection Team. This team handles the bulk of our incidents and conducts containment across endpoint, network, cloud and mobile using automation and API based integration we have built into our platform.
Roles and Responsibilities: -Monitoring security systems -Identifying potential security incidents -Escalating incidents to Level 2 -Performing basic incident response activities
Incidents handled: -Low-severity incidents such as phishing attempts, attempted unauthorized access, and simple malware infections.
Level 2 (Analysis): The Level 2 team is responsible for conducting detailed analysis of security incidents and determining the appropriate course of action. They are also responsible for developing and implementing incident response plans.
At LMNTRIX we refer to this team as the Threat Response Team and they support the Threat Detection Team for any major or complex incidents where malware analysis, IR and forensic skills are necessary. So when hiring for this team we look for folks from these type of backgrounds.
Roles and Responsibilities: -Conducting detailed analysis of security incidents -Determining the appropriate course of action -Developing and implementing incident response plans -Providing guidance to Level 1 team -Escalating incidents to Level 3
Incidents handled: -Mid-severity incidents such as advanced malware infections, targeted attacks, and data breaches.
Level 3 (Expertise): The Level 3 team is responsible for providing advanced technical expertise for incident response and investigations. They are also responsible for developing and maintaining security systems and tools.
At LMNTRIX we refer to this team as the Threat Hunting Team, who are responsible for both our active and pro-active hunting activities. They are our most senior team members with 10+ years industry experience. They come from a background in APT hunting, red teaming, scripting/coding, IDS signature development, binary triage, in depth knowledge of OS internals/file system/registry and advanced protocol analysis.
Roles and Responsibilities: -Providing advanced technical expertise for incident response and investigations -Developing and maintaining security systems and tools -Providing guidance to Level 2 team -Conducting forensic analysis -Providing incident reporting.
Incidents handled: -High-severity incidents such as APT attacks, nation-state level threats and complex data breaches.
It’s important to note that each organization may have different incident handling process and different incident severity levels. Additionally, different teams can be added based on organization’s need and maturity. As a major MDR and SOC operator, at LMNTRIX, we also have teams that are responsible for Threat Intelligence, Metrics and Communications as well as Engineering.
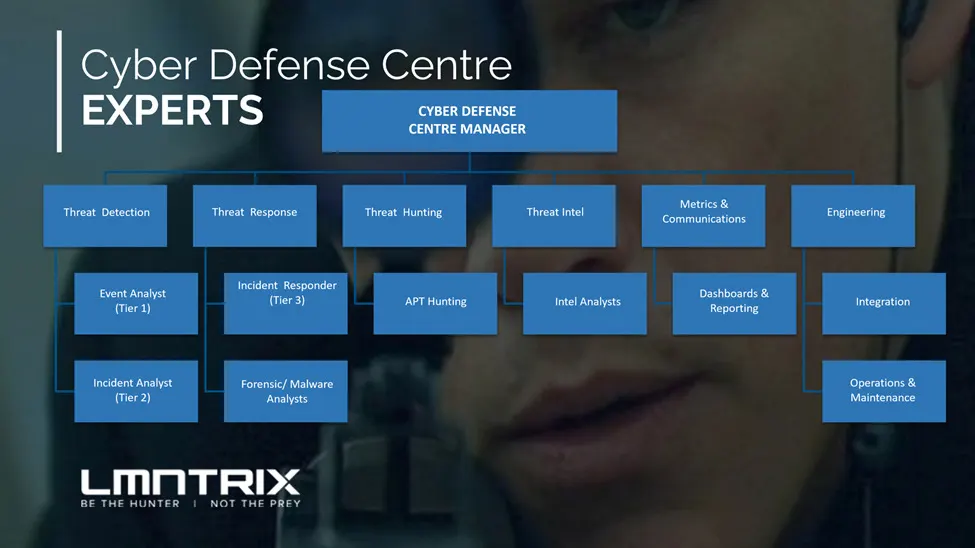
The LMNTRIX Cyber Defense Centre Team Structure
In conclusion, a tiered team structure for a SOC allows for efficient incident handling based on the severity and complexity of the incident. The Level 1 team is responsible for initial triage, the Level 2 team conducts detailed analysis and determines the appropriate course of action, and the Level 3 team provides advanced technical expertise and support. This structure ensures that incidents are handled quickly and effectively, and that the most critical incidents receive the necessary attention and resources.


