
AZORULT malware was initially detected in 2016, and its primary function is to steal sensitive information from infected systems, including browsing history, login credentials & cryptocurrency data for possible identity theft and cyber criminal activity. Additionally, it is capable of downloading other types of malware onto compromised systems. AZORULT was marketed on Russian underground forums as a tool for collecting sensitive information from infected computers.
Early Azorult versions such as Version 2 and 3, were coded in Delphi 4, but later versions and clones have moved to the VB / VB.NET language.
Azorult Delivery Mechanism
- Azorult is commonly delivered, through the following methods,
- Exploit Kits (esp. the Fallout Exploit Kit)
- Affiliate Malware that acts as a dropper such as Ramnit & Emotet
- Phishing & Malicious spam emails
- Infected websites, Malvertisements & Fake installers
In some cases, a variant of this malware has been known to create a new, hidden administrator account on a machine and establish a Remote Desktop Protocol (RDP) connection by setting a registry key.
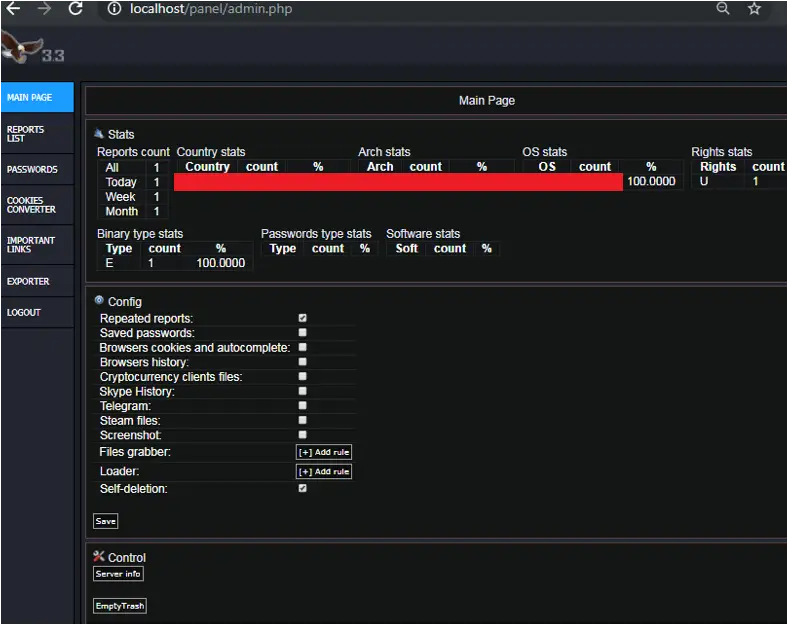
Infection Chain
Target – MS Windows Platform
Programming Language – Delphi / VB / VB.NET
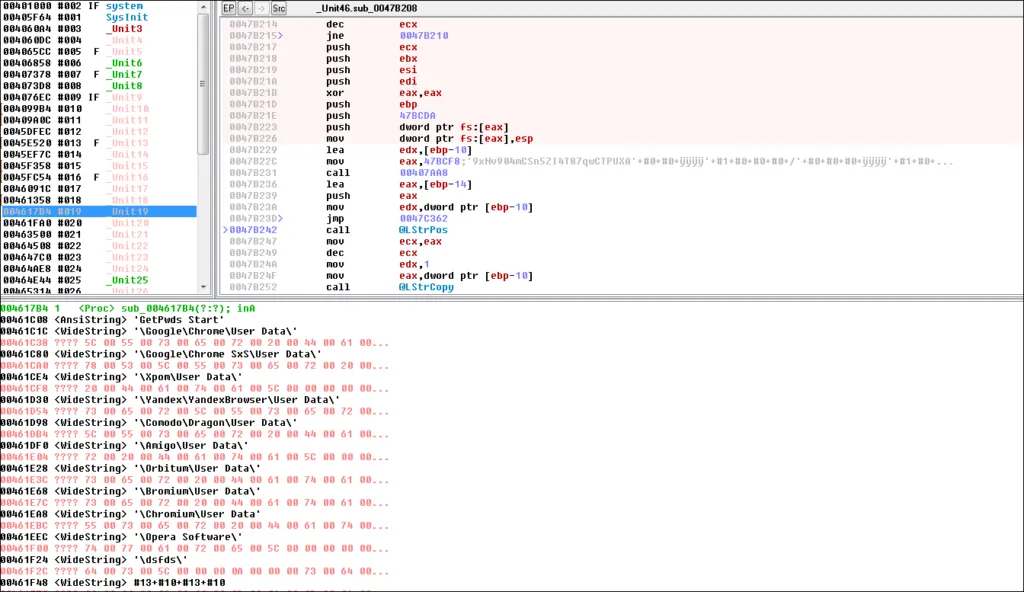
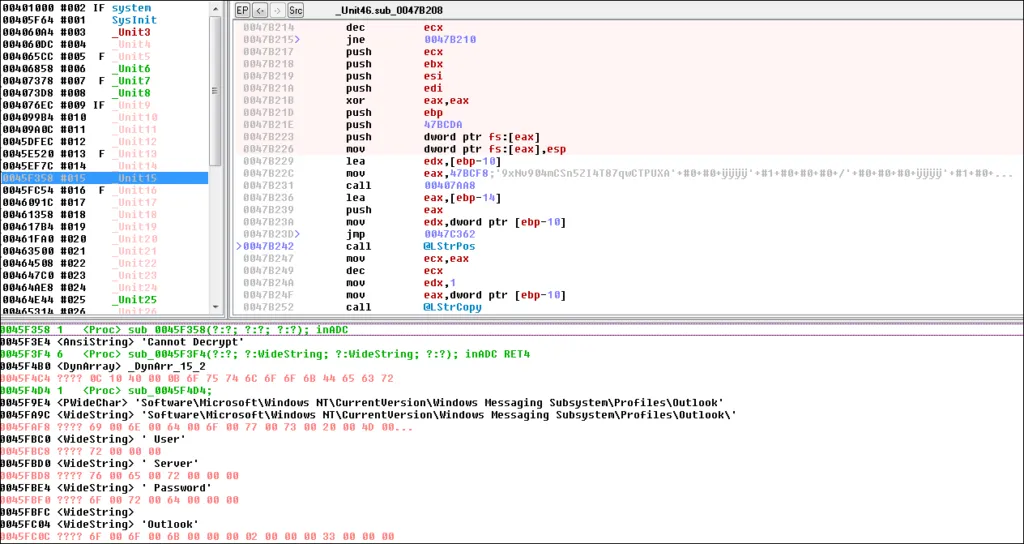
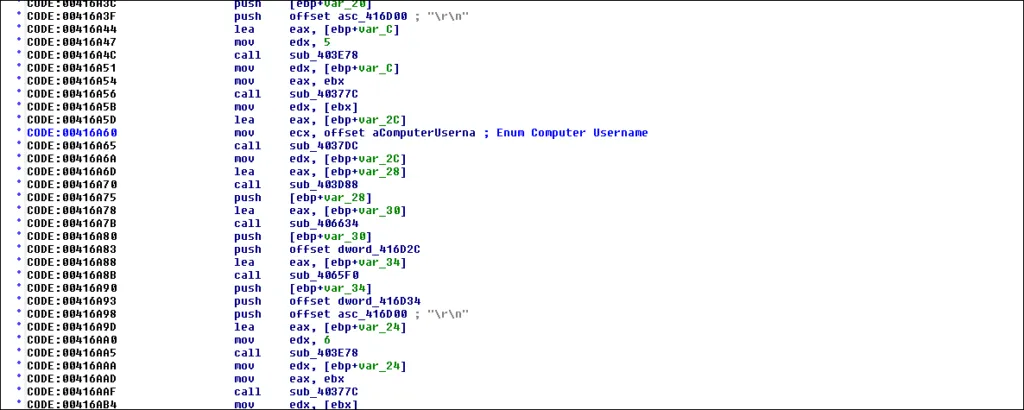
Static Analysis of AZORULT malware sample
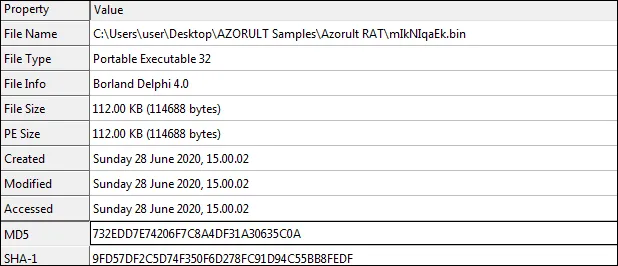
AZORULT Info Stealer – Functionality
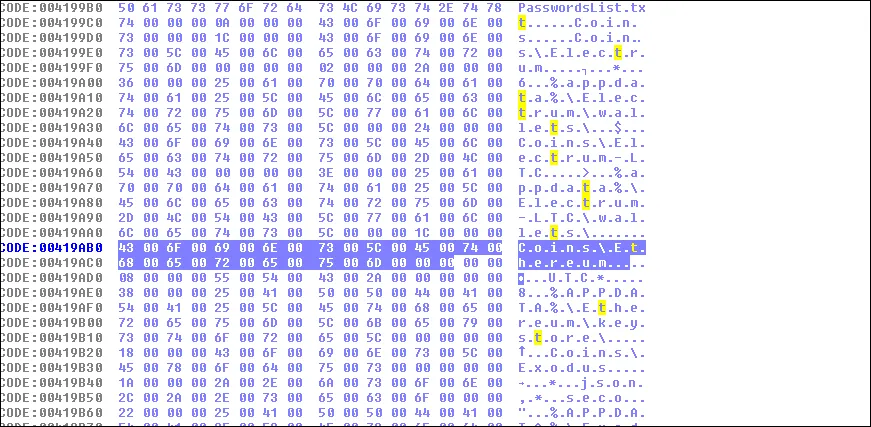
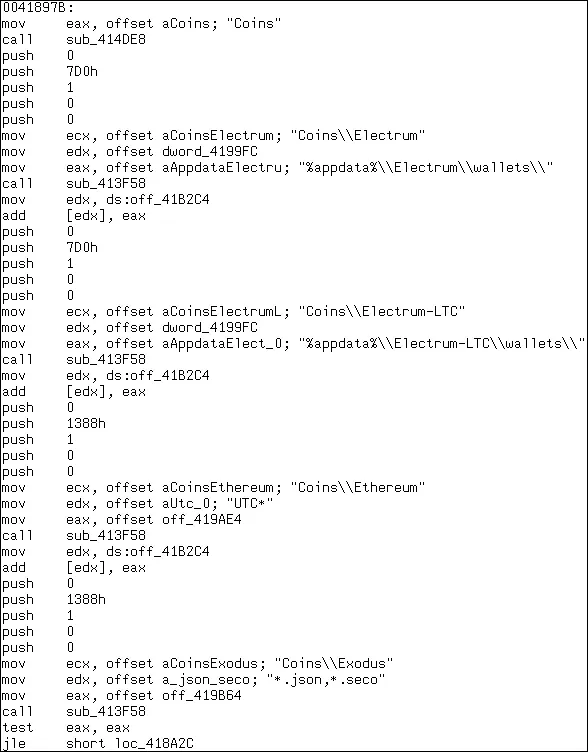
The theft of passwords and potential identity theft can occur with applications like Chrome, Mozilla Firefox, Opera, Yandex Browser, Comodo Dragon, Internet Explorer, Microsoft Edge, Outlook, Thunderbird, Amigo, Pidgin, PSI on the target list.
- Theft of banking / credit card information from Chrome, Firefox, Edge & similar browsers.
- Theft of cookies files, data from autocomplete forms in browsers including Chrome, Mozilla Firefox, Opera, Yandex Browser, Comodo Dragon, and Amigo.
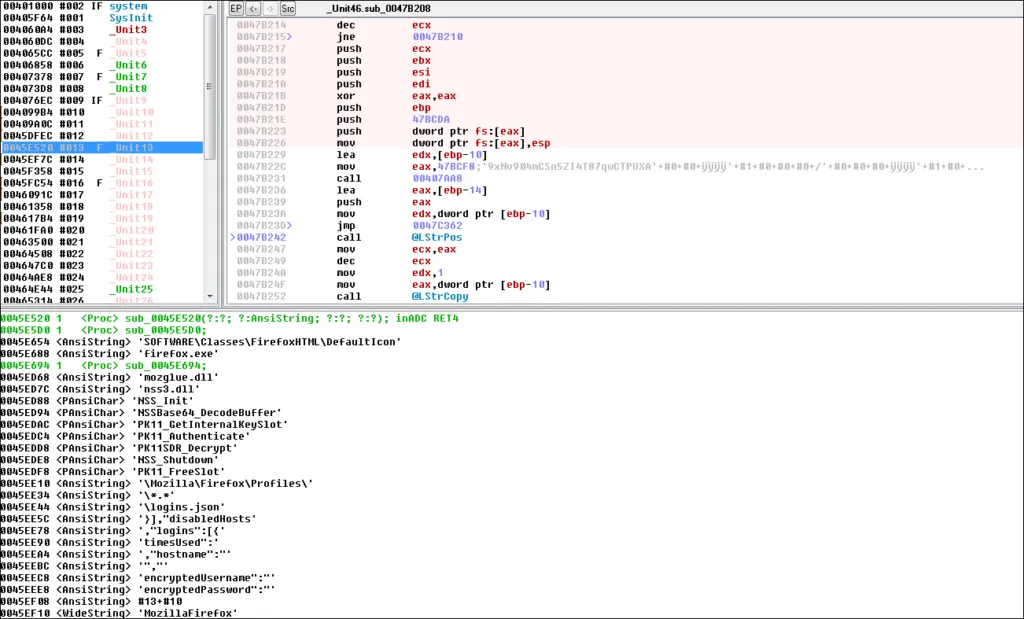
• Capturing information about the victim’s system (IP addr/computer name/username, process and application lists etc.)
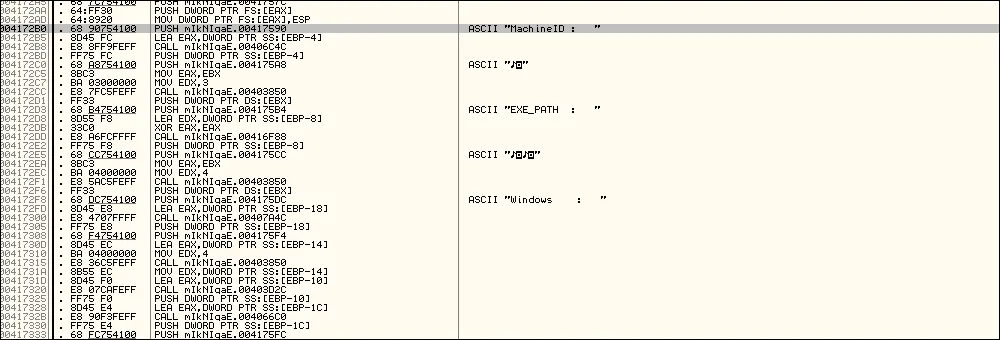
• If these weren’t enough, the threat actor can also continue obtaining files from Skype, local files from telegram (app data), screenshot and files on the victim’s desktop with AZORULT.
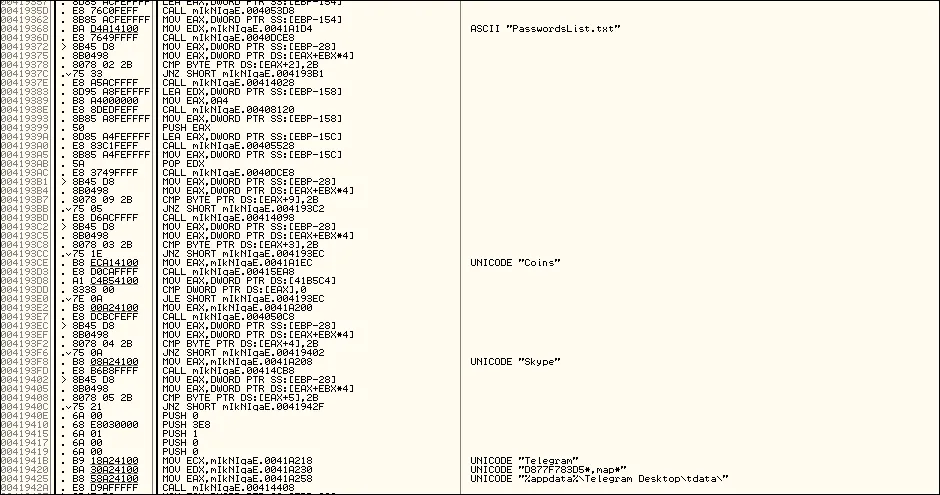
Strings from the Azorult malware sample
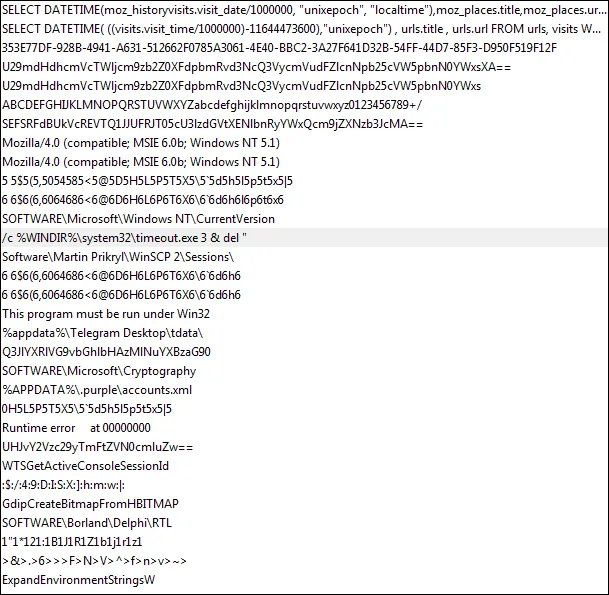
Process Melting
Azorult command found in over 30 samples analyzed by LMNTRIX CDC:
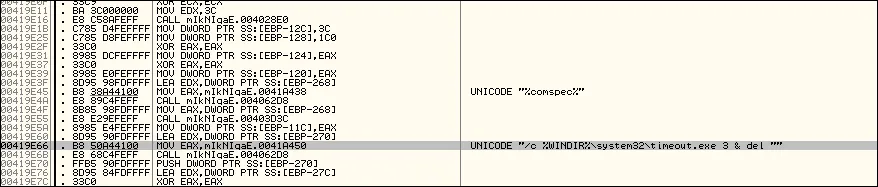
Azorult appears to be “melting”, deleting the file upon execution of the original sample. The Azorult builder allows the threat actor to specify, if required, the threat actor can “melt” the sample build, this command could serve as a potential option to add as part of a Yara rule, along with other publicly available IOCs.
Technical Analysis of XLSM Azorult
Sample Information
Infection Vector – Malspam campaign and/or phishing emails.
Threat Name: Azorult | Category: Downloader | Classification: Backdoor.
An XLSM file is a macro-enabled spreadsheet, a widely used spreadsheet program included in the Microsoft Office package. It contains worksheets of cells arranged by rows and columns, and most importantly, it contains embedded macros programmed in the Visual Basic language for Applications (VBA).
In general, VBA macros can perform a variety of tasks, interact with other applications, automate web interactions, and perform more advanced functions. By using macros, we can save significant amounts of time and improve productivity by automating repetitive tasks, reducing errors, and allowing users to focus on more important tasks. This feature can be abused by malware authors, affording them the ability to embed their malicious code inside the macro functions.
Let’s begin with the sample analysis.
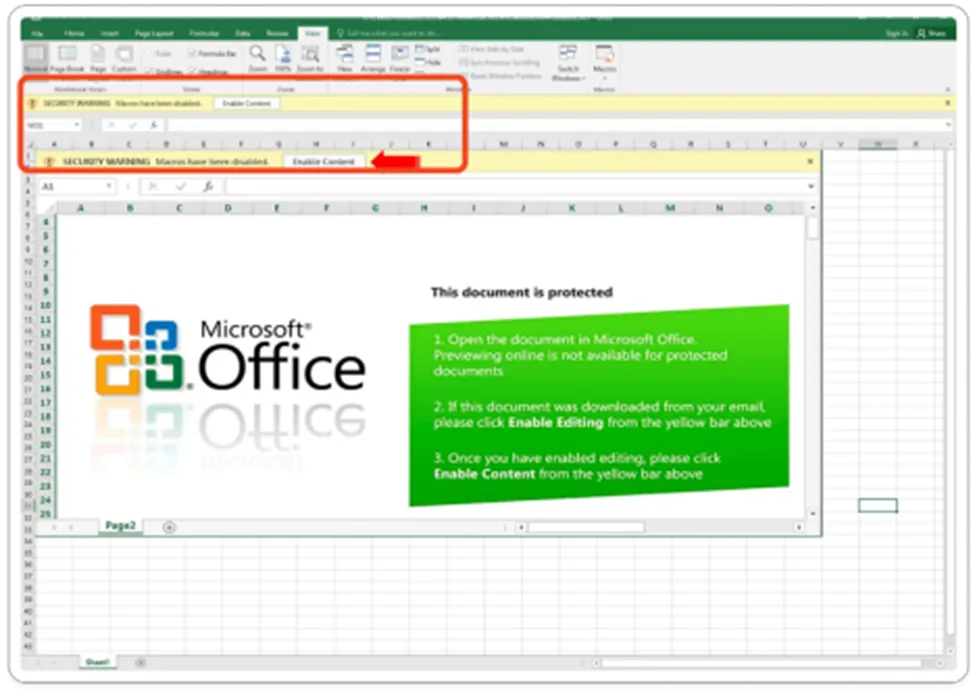
Recent Azorult template
As per usual, this campaign infects its victim with the initial vector of a phishing email, which contains an attachment file of an MS Excel spreadsheet (.XLSM). Once the victim opens the XLSM spreadsheet, where it urges the user to enable the macro content, the VBA macros trigger the powershell command, which will execute in the background. Then it will connect to the malicious IOC to communicate with their malicious C & C servers to download the payload file to start infecting…
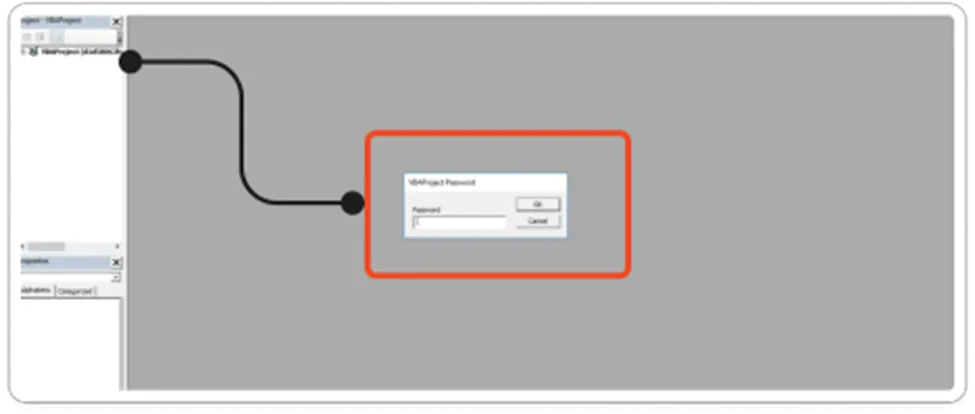
Password Protected – VBA Code
Unfortunately, the VBA code is password protected, and we have to crack the password to open this VBA project. After successful completion, we can view the macro code or simply extract the file by using 7Zip, and we are able to see the vbaproject.bin and other folders. By using this information, we can perform further analysis on the sample.
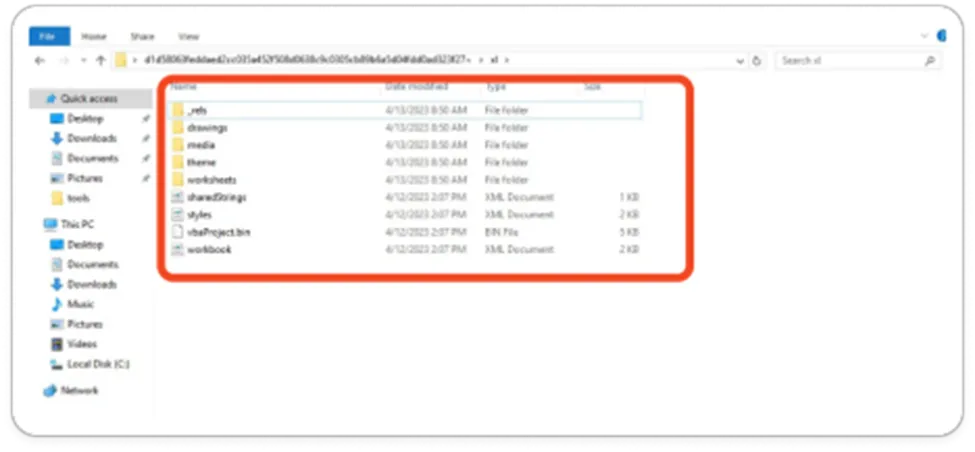
Embedded folders
File Structure of XLSM Azorult
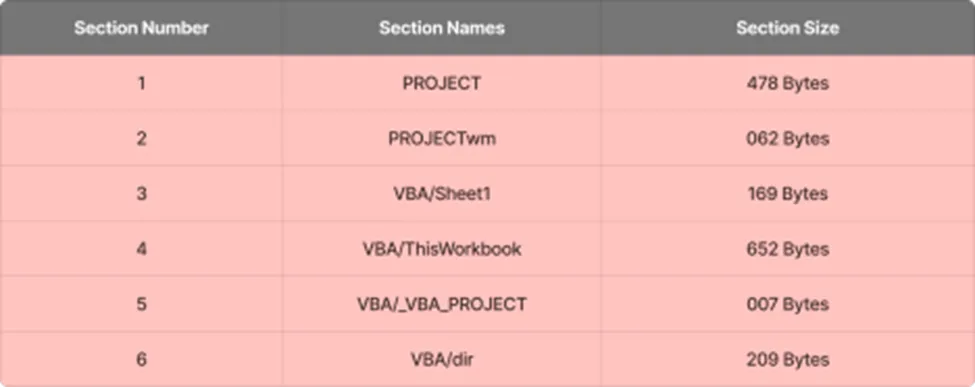
OLE Embedded functions with keyword
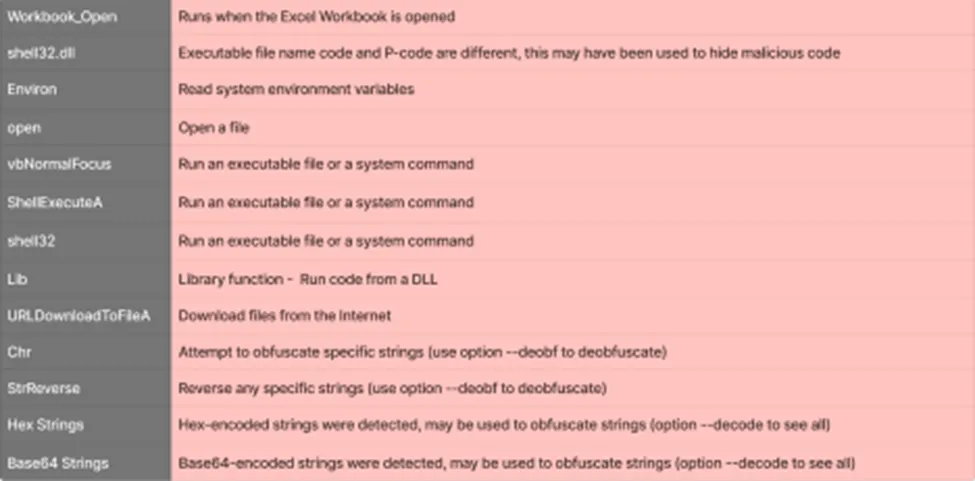
Using these API calls, the macros will execute.
Especially URLDownloadToFileA: Once the user opens the Excel spreadsheet, this Windows API function downloads a file from the Internet to a local file quickly. Luckily, we can capture that file using a network capture tool.
Macro-Content with Process Tree

Here we can easily capture the powershell command after executing the .xlsm file.
Command & Control Server – HTTP Request
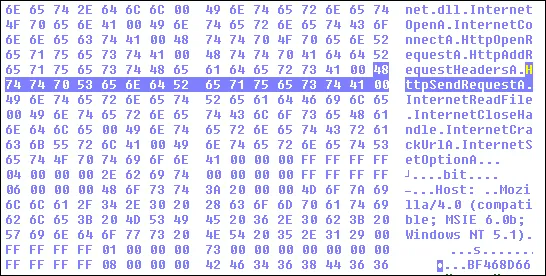
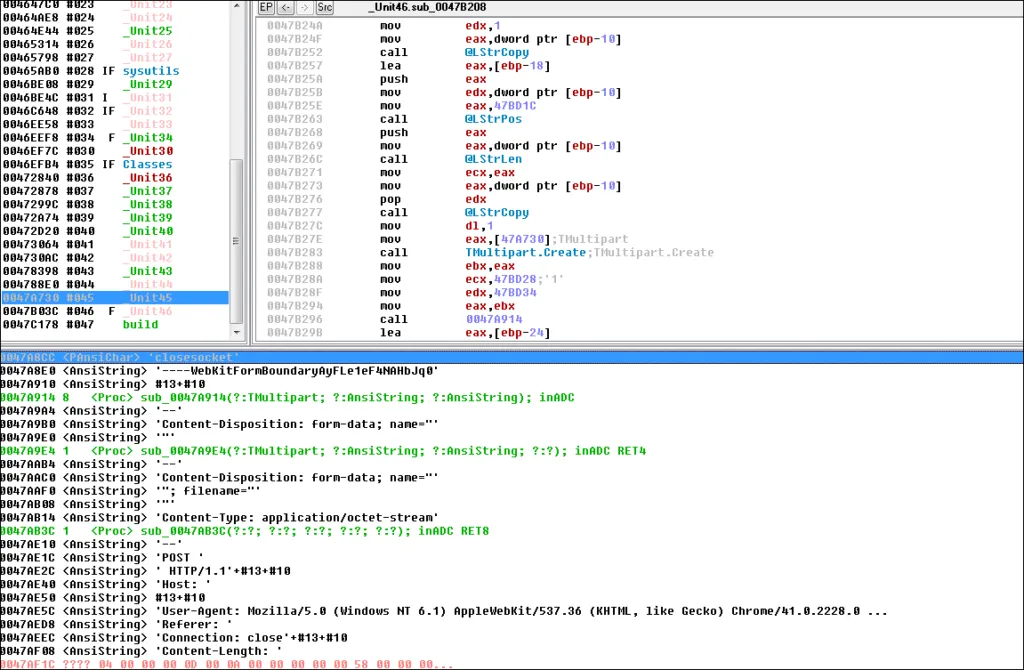
Indicator of Compromise for AZORULT malware
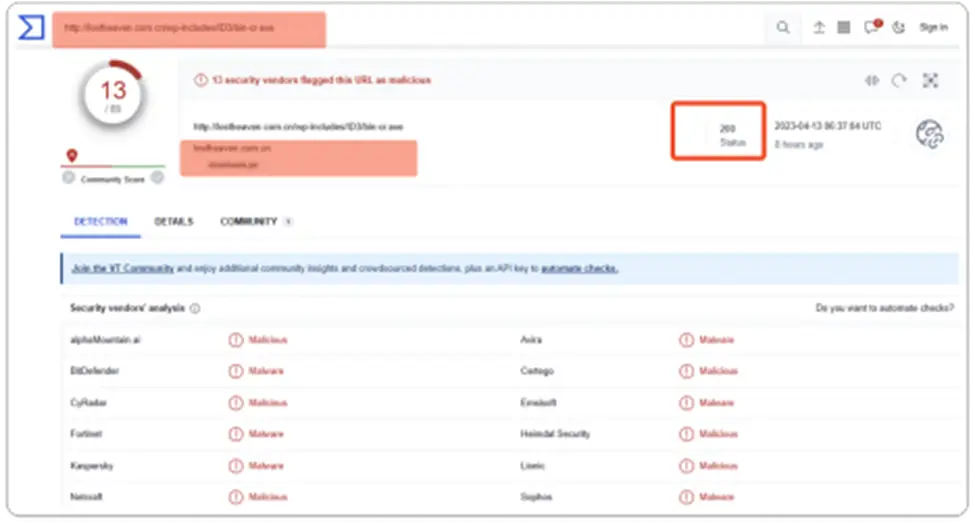
Behaviors of Azorult Malware
- AZORULT malware was designed to collect system information, such as installed programs, the system’s native architecture, the language (keyboard such as US/UK/DE/FR/CN etc) the user’s name & privilege, local hostname, and the operating system (OS) version of Windows.
- Using File Transfer Protocol (FTP) clients or any file manager software, AZORULT can steal user account information.
- It has a keylogger integrated within its code base, it enables the malware to record keystrokes and steal sensitive information like usernames, cookies and passwords.
- On any given infected system, AZORULT can download and install further malware code. This gives the threat actors an opportunity to launch further attacks and take over more control of the hacked machine.
- Spreads to additional systems that use the same network, granting the ability to infect a lot of devices and steal information from a larger variety of targets.
- Last but not least, AZORULT can execute a bunch of backdoor commands sent by a remote, malicious threat actor in order to download and/or destroy files, collect host Internet protocol (IP) information, or both.
MITRE ATT&CK Tactics & Techniques for Azorult
| ID | Tactics | Techniques |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | VBA Scripting Windows management Execution |
| TA0003 | Persistence | Registry Run Keys / Startup Folder Hooking |
| TA0004 | Privilege Escalation | Scheduled Task Hooking Process Injection |
| TA0005 TA0006 TA0007 TA0008 TA0009 | Defense Evasion Credential Access Discovery Lateral Movement Collection | NTFS File Attributes Process Injection Modify Registry Virtualization Evasion Technique Hooking Input Capture Credentials in Registry Credentials in Files Credential Dumping System Network Configuration Discovery Process Discovery File and Directory Discovery Query Registry Browser Bookmark Discovery Remote file copy Automated Collections – Input Capture Data from Local System |
| TA0011 | C&C Server | Web Protocols Standard application layer protocol Standard Cryptographic protocol etc., |


