APT19 is a threat group based out of China, they have targeted a variety of industries, including defense, finance, energy, pharmaceutical, telecommunications, high tech, education, manufacturing, and legal services. In 2014, APT19 was responsible for the Forbes.com breach. APT19 threat group was able to chain together two zero day vulnerabilities, one against Adobe’s Flash Player and one against Microsoft’s Internet Explorer, to compromise the popular news website in late 2014.
In 2017, a phishing campaign was used by the APT19 threat group to target seven law and investment firms. The APT19 threat group made use of obfuscated PowerShell macros embedded within Word documents generated by Empire. Some analysts track APT19 and Deep Panda as the same group owing to the overlap in toolkit and code re-use, but it is unclear from public sources, if these two groups are the same.
Targets: North America, Australia
Motivation: Intelligence / Espionage Operations
Toolkit: Derusbi Backdoor, Poison Ivy, Empire framework and Cobalt Strike (payload)
Static Analysis of APT19 Campaign
Sample Information
SHA256 : DE33DFCE8143F9F929ABDA910632F7536FFA809603EC027A4193D5E57880B292
Filetype : DLL
Attack : Chinese APT19 attack
It is possibly compiled in Microsoft Visual C++
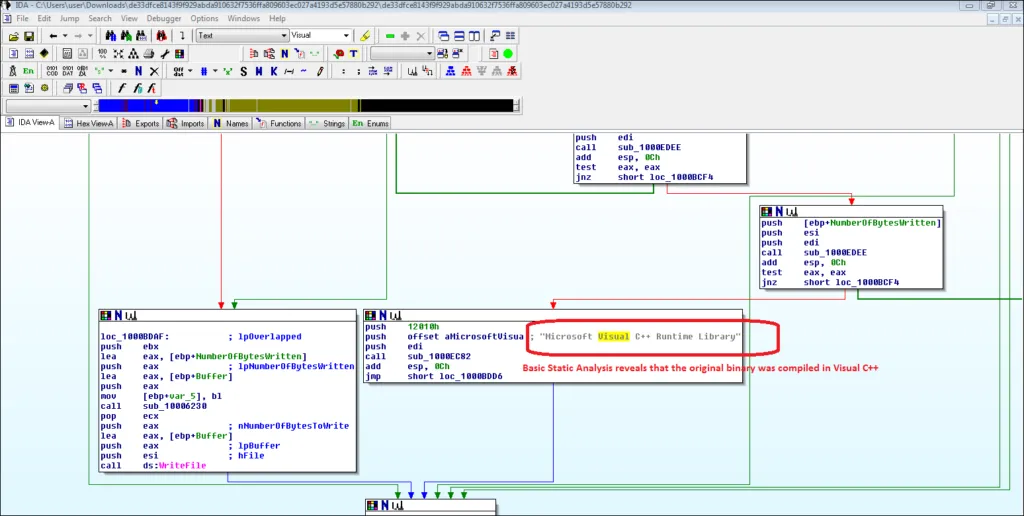
File we are analyzing with ref: APT19 is a DLL file,
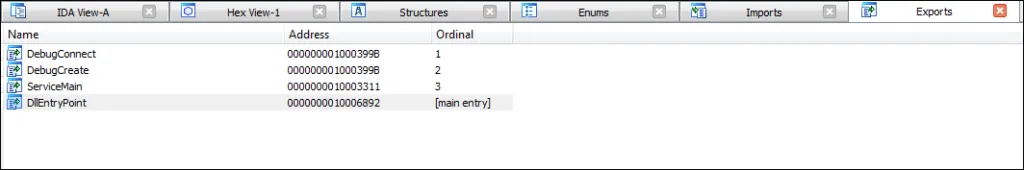
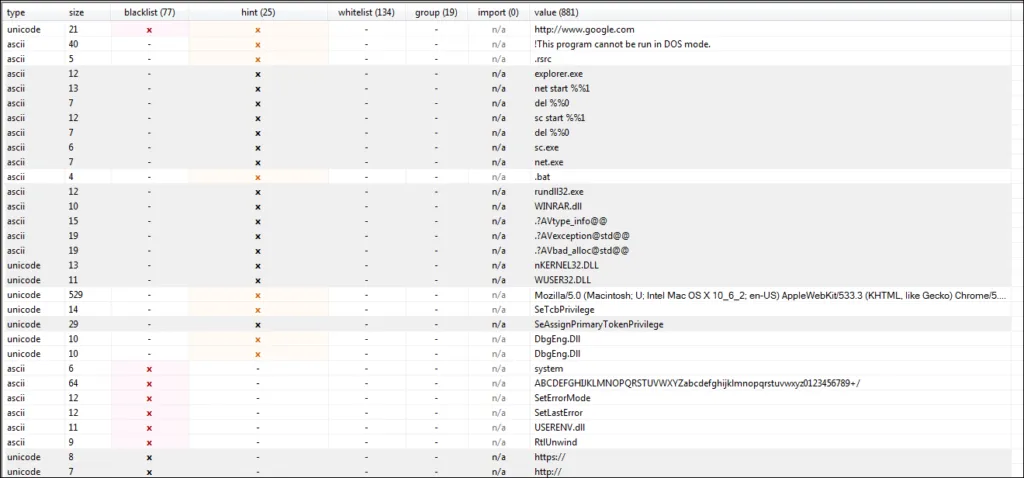
Interesting Strings we observed during analysis are given below,
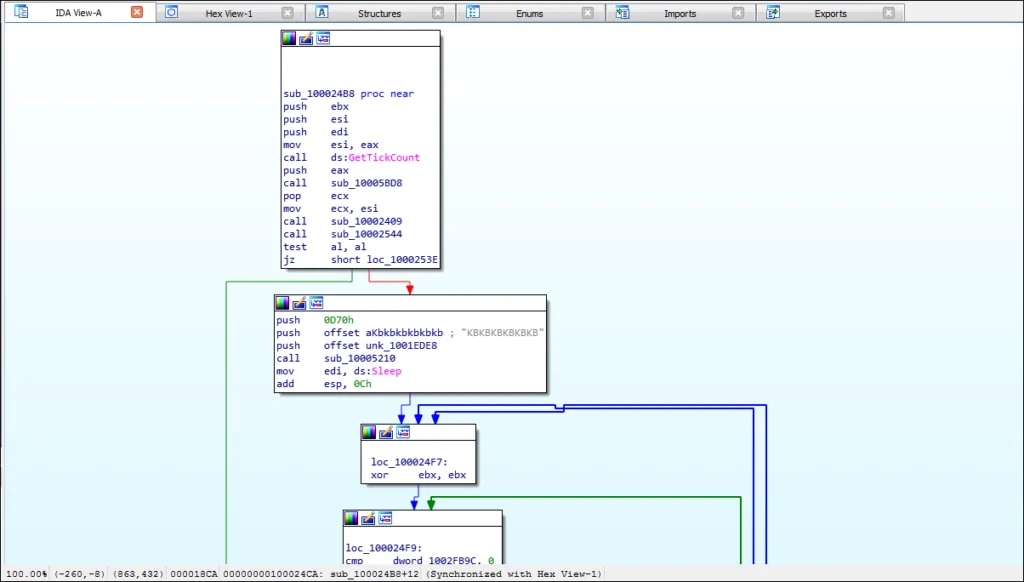
Malicious process uses the GetTickCount API call to compute a random string consisting of 3 characters,
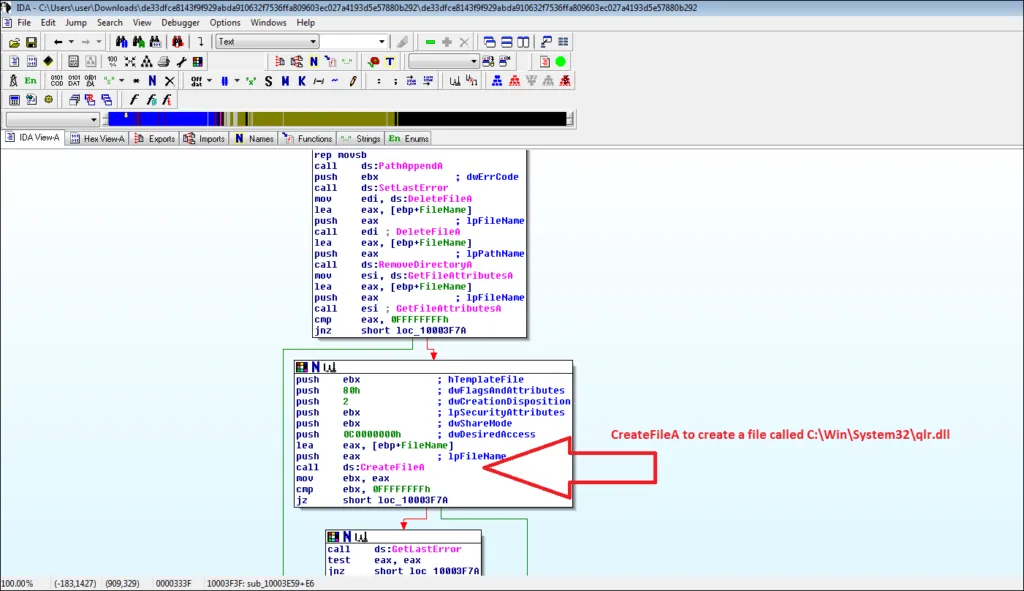
APT19 creates a DLL file called qlr.dll using CreateFileA,
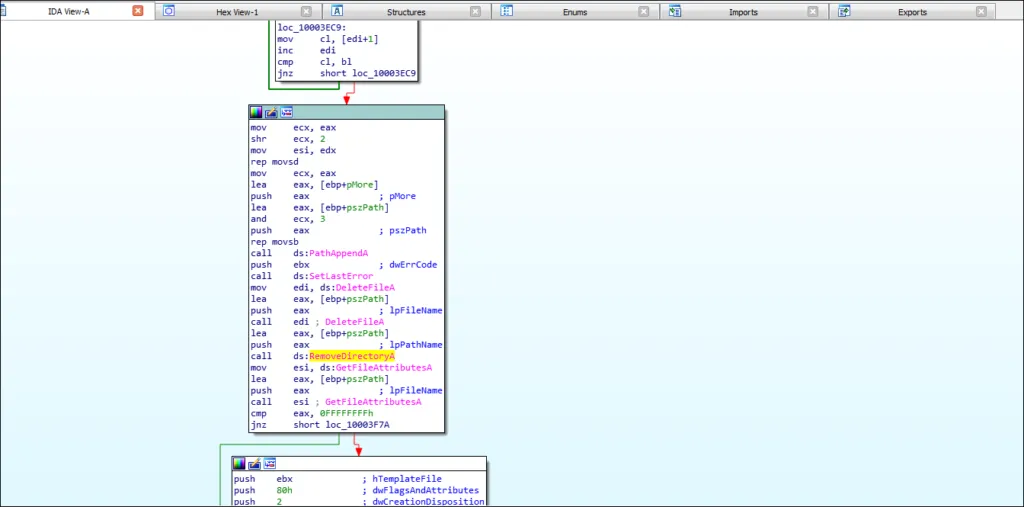
Next, it deletes the file/directory using RemoveDirectoryA,
User Impersonation
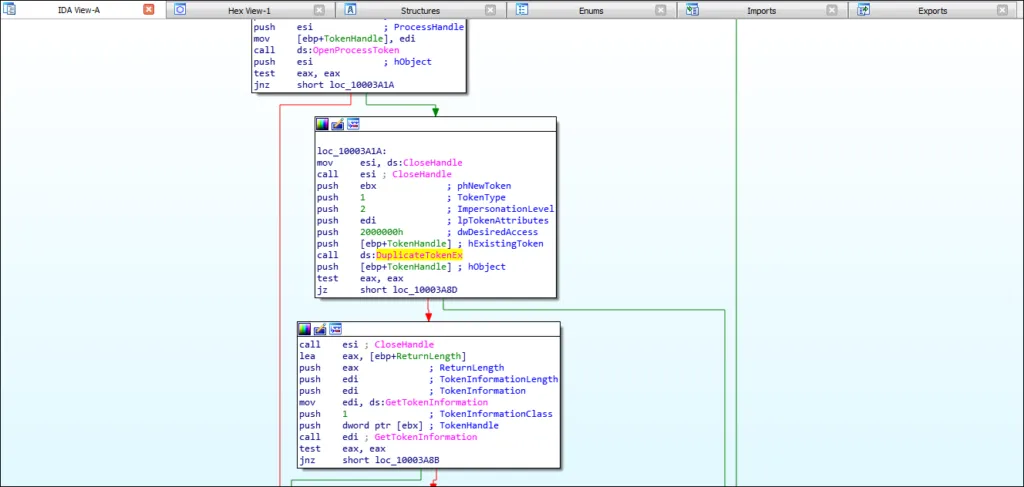
Here’s how the APT19 malware impersonates the logged on user,
- It determines the Process ID. Next it inherits the process handle and opens the process.
- It determines process privilege using GetTokenInformation.
- Subsequently, the malware elevates the token using parameter 0x14.
- To learn more visit https://learn.microsoft.com/en-us/windows/win32/api/securitybaseapi/nf-securitybaseapi-impersonateloggedonuser
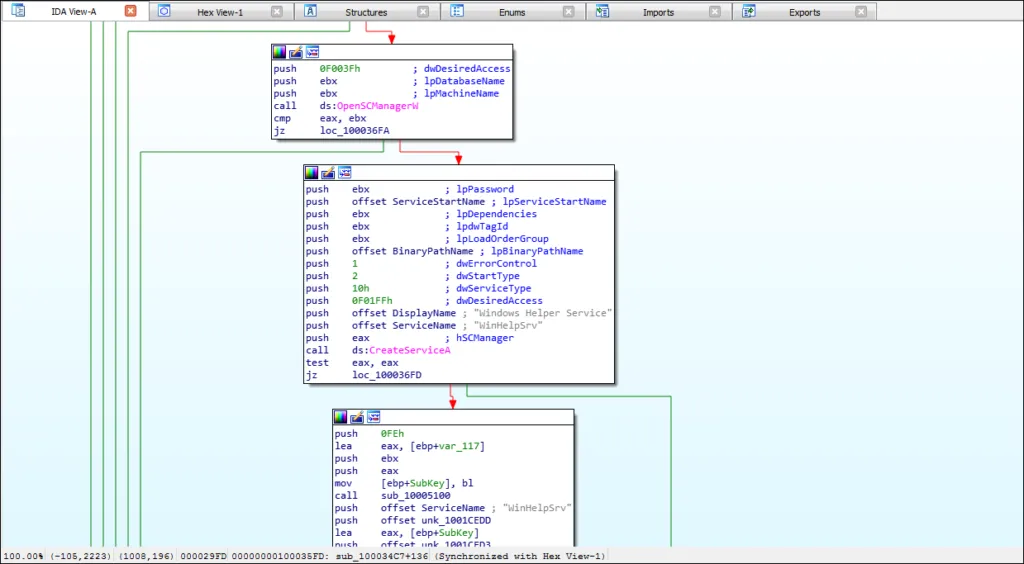
The malware then creates a new service named WinHelpSrv using CreateServiceA, as shown below,
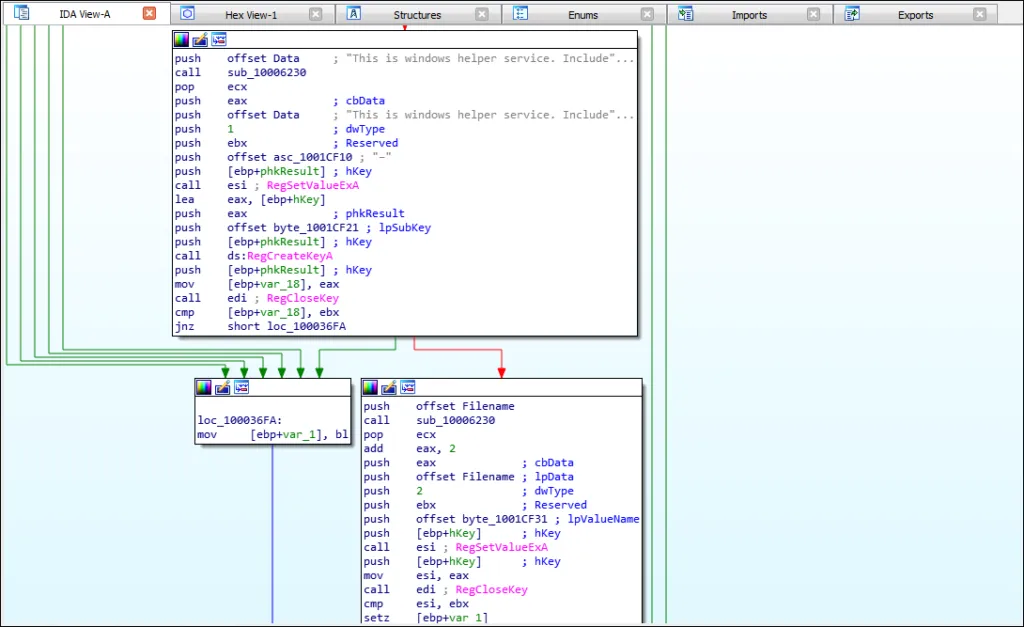
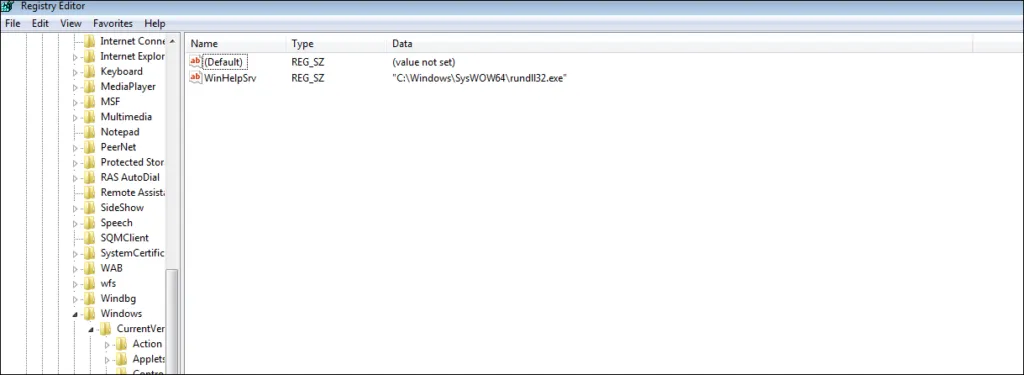
WinHelpSrv is made persistent by adding a registry key under HKEY_CURRENT_USER “\”C:\Windows\SysWOW64\rundll32.exe\””
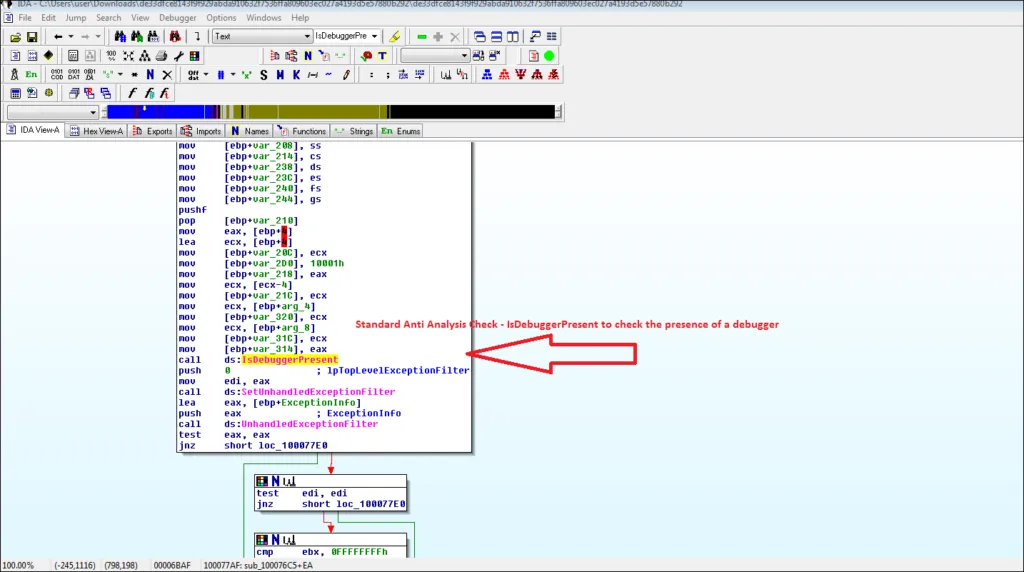
Common Anti Debugging Techniques
The malware employs a couple of well-known anti-analysis measures, including comparing the executable image path to rundll32.exe and checking for the presence of a debugger (IsDebuggerPresent). These methods enable the software to use ExitProcess to terminate itself and ensures that a threat researcher cannot execute the file.
Dynamic Analysis of APT19 Campaign
Infection Chain
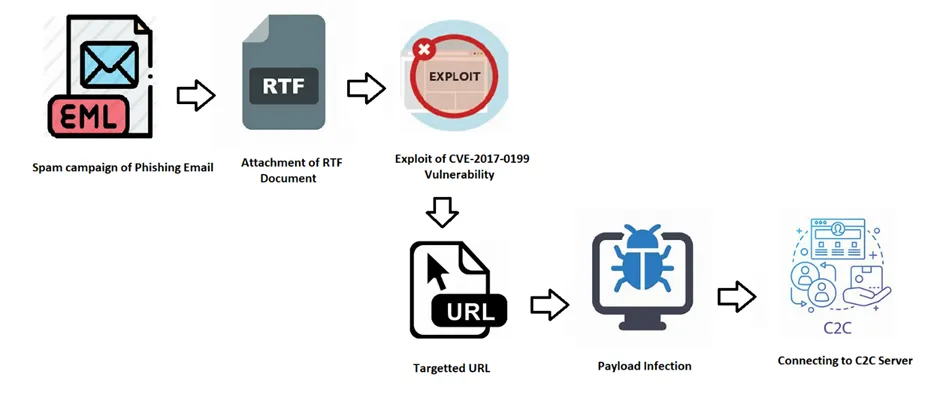
By using spam campaigns with attachments as its initial infection vectors, the APT19 malware infects the victim machine (EML). Typically, it includes RTF documents from Microsoft Office that have macro content. This time, they linked with the intended object via an external URL. Thus, the victim must perform their necessary tasks by hand. Once finished, it will carry out the action on objectives.
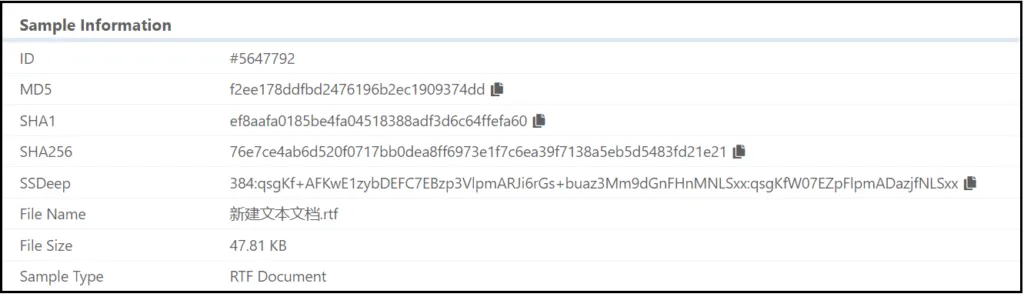
Sample Information:
Sample : 76e7ce4ab6d520f0717bb0dea8ff6973e1f7c6ea39f7138a5eb5d5483fd21e21
File-Type: RTF
Category: Exploit CVE-2017-0199
Attack : Chinese APT19 attack
Technical Analysis of RTF:
Rich Text Format (RTF) is a file format that controls how texts are formatted. It is made up of groups, control words, control symbols, and unformatted text. They are used by RTF readers to enable a specific format for the text display. RTF files can include additional information such as font style, formatting, graphics, and more in addition to plain text, which is not possible with regular text files. Since many applications support them, they are excellent for cross-platform document sharing.
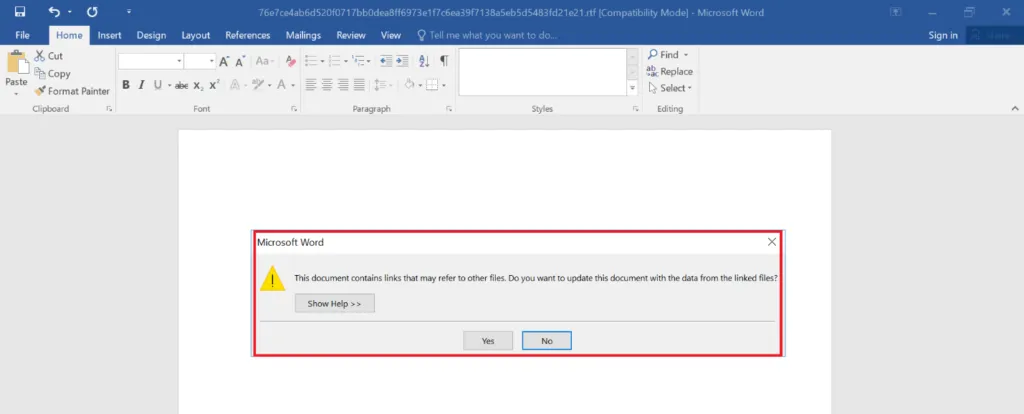
The document features a pop-up window asking the user whether they wish to update because it contains links to other files. What this means is that this document may open or include another embedded document within an RTF file, but the user is unaware that the document was silently installed in a hidden folder.
On Opening the Linked Data
Once linked, the user has access to the document. However, they are unaware that the object is linked to an external unknown or hidden document.
Actual file content:
Rich Text Format (RTF) files are typically used by threat actors to store exploits that target flaws in Microsoft Office and other software.
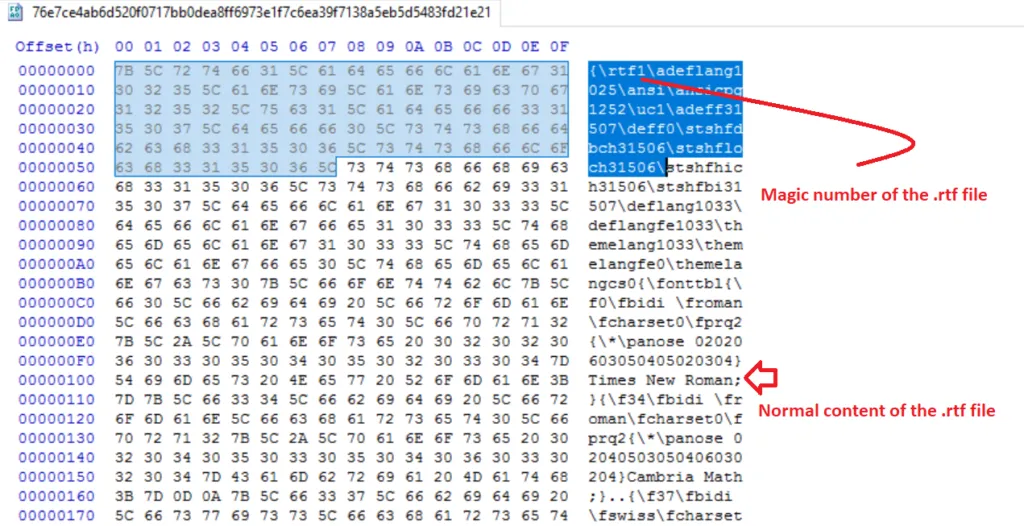
HTTP Request:
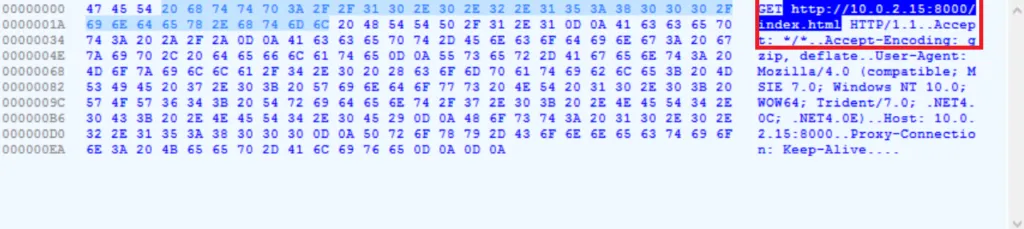
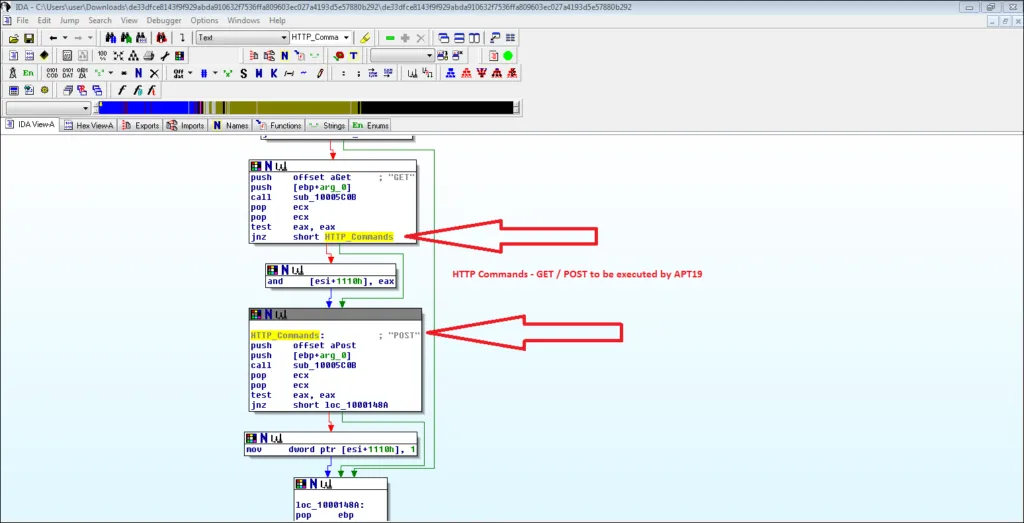
When the RTF file is opened, the macro runs a payload that was extracted to the user’s TEMP directory. Although the executable files are deleted when the Word instance is closed, the RTF files created by the macro in the temp directory could remain and be used as a host indicator during triage or response activities. APT19 sends a HTTP request to ensure that the target system has internet access (or is active) before proceeding with the attack.
Malicious Actions Performed,
APT19 used a watering hole attack on specified domain to compromise the targets.
APT19 concealed PowerShell code, possibly from the Empire framework -W Hidden by setting the Window-Style parameter to hidden, and launched a HTTP malware variant and a Port 22 malware variant using a legitimate executable that loaded the malicious DLL.
General Mitigation measures to prevent APT19,
If you do not trust the resource, do not open any attachments from external users.
Do not open any URLs from unknown senders.
Protect exposed web applications with web application firewalls, and close unnecessary firewall ports for the network and individual devices.
Use strong passwords and make Multi Factor Authentication, an organization wide habit
Maintain effective Endpoint Detection & Response applications such as (antivirus, EDR) and NDR, monitor your e-mails, and secure your email servers, when in doubt, opt for a compromise assesment to truly know the security posture of your network.
Indicators of Compromise – IOC to detect APT19 Attack
| SHA256 |
| 76e7ce4ab6d520f0717bb0dea8ff6973e1f7c6ea39f7138a5eb5d5483fd21e21 |
| 68205817faa46e7217c4a624b8c316c7ffce5775f3afe703f90c039fd1817076 |
| 01f3d36e17d60fc9a15014c50f373917b52b0b2214acf03798f21df94911f562 |
| 660cc12c20eda8f6ded1f718c6bdfc04b49a50e0077fb60c5e599e061f6ea0f9 |
| 545e4242eef69954dde30e547a070b276458b874a8ad8f521ffb30f4590ba6c5 |
| d54b720511091c47a46b69ba5ef86d49dc3570f89206c8984beae53274d04145 |
| 4f544e8756373520e98ed12b921ea7e05a93cf0152405ef3ac65133f7c8660a1 |
| 0f6ea6af97edfafe33d0506bdf06443e05063815088ed7db302c54b6e8d26bf2 |
| 9011380f1a01314d06bf0af030dc9017b63089c115fce0d1bca69610318e017b |
| c56900f2454bb99d8fd41b72f6e4ceb9506018c650bc55a21dd395af0f6c849e |
| bd1d090cdf03216acf14b63c14ae1d77bb404f4cbbeefa83476c8ad69da33abe |
| aad51dc7d7dc75acb6529b5b56fd11075a779e2cf31a35af6b1e2b7af07f8dcd |
| 6cd9d6d2a12e7685a7be49ae9d74711e5ce9e0e0442b775bea4a8ab6b6daa758 |
| a4bb89cf05e78be24852c60fb39e39a83bb2c3da732b734ff09902e776d1e0cc |
| d9a0331ad039f45f847de28f03f0a676b295a201aa9bfd285949e326c6bf76bb |
| ec22e09730bd3ad539494ad67bb7c1d9e90d8da455d5f59427b5ebc610872fca |
| b7f7948a0b20370719628196382c5411cb5e10de22dc2785aa8ed110a98bf5f6 |
| 5c3a3771b7f5545469fa1f34bb19a4e41e5401b774c2c7ec10e3301400cf6027 |
| 18fd49a43d48331fd8063a4f5c40f26aebcfd5e473a36b157ac75a5a2587017f |
| 572af23e8b39462e13c498fda6c8a33eb5e71517430867382d3f0b25da94886e |
| 432960ff01678dbb0c031797a19f6bd00345cad8a06f1d671e0c152429442e52 |
| ff5d8c92cdb853c4c7f7a6db775043626f376e37bf4352b009654bc48d7458ef |
| cd1a9ae4a3968643a6fb41b36b67838d952dac83ad63c63ce4ad3c672fac31b8 |
| 023e3270a88183958db7e49602227b010c6e75d9874f4d950ce7f5d3c356186f |
| c94bd7e24f227bf8fd6aadf643f7bfcf8269c235397248587f62cdd312d022c3 |
| e458afd353ca233062f54efbaee7130dba3b26edc48d2abfbaa42d9fa26e4be2 |
| 67730f05990a640d2c683be532447f7cd525e9f2ec24dcedac45a56d309c6462 |
| 61a6d8c1e9ff2a1d6e171af64646b3d621f58d4fb2f8c7a1612a1be988de6cae |
| 5cb20922b57f49768105b4700d58718595a6f371d11219cabb67a25a4e2b516d |
| b7fe639178efce76fb21bf29fa7909582c2dfe40e602994f9f046a5604ce24f1 |
| be05deaf61e674469c268671d72ed3326d55a6f06fe9a18da68592689fa4b9be |
| 88315e270faa82146bd3d612c14d500c0daaaf7cc6d5c4feb1136cd08cc54bf1 |
| 52061b89eea6713279a56c1d0075b94c2dbda96772592271b9200c81a0941426 |
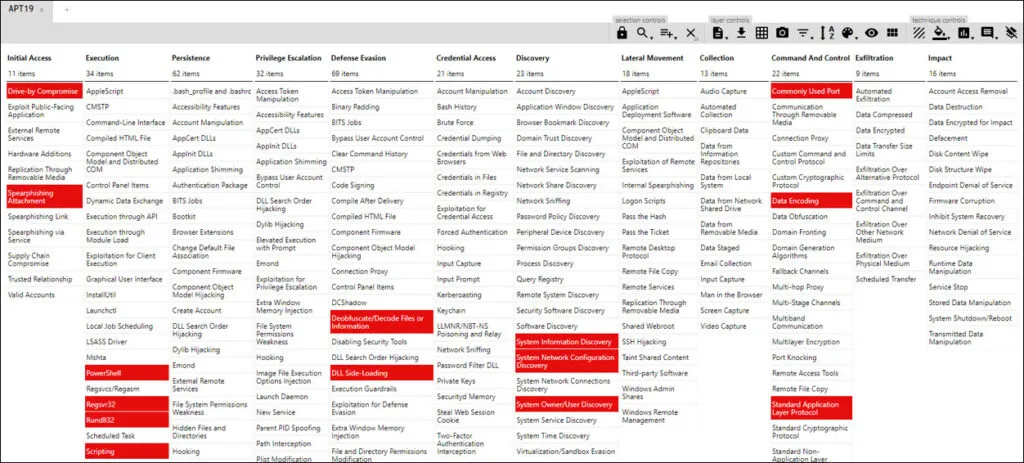
MITRE ATT&CK Mapping for APT19