The “HTA NetSupport Campaign” is a cyberattack scheme that exploits HTML Application (HTA) files to distribute malware linked to the legitimate NetSupport Manager remote administration tool. Cybercriminals have misused NetSupport Manager in different campaigns to deliver malicious software.
In such campaigns, cybercriminals typically distribute HTA files through phishing emails or malicious attachments. If a victim opens the HTA file, it can trigger harmful scripts or code, leading to the installation of malware on the victim’s computer. As LMNTRIX has observed in multiple lab articles, legitimate remote management tools like NetSupport can be exploited by malware to gain unauthorized access to systems. These tools are often used by attackers to move laterally within a network, escalate privileges, or maintain their presence on compromised systems.
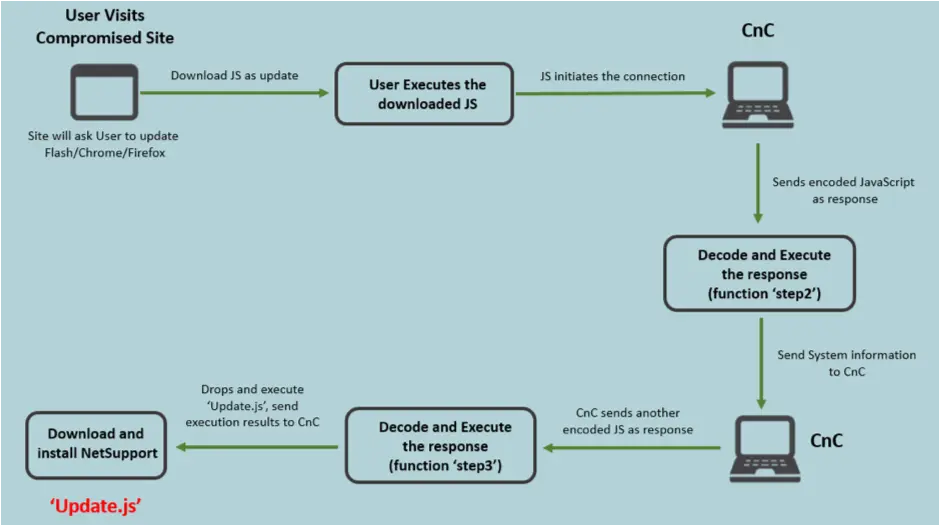
A typical phishing, or watering hole attack resulting in a Javascript payload is demonstrated below, the image shows how NetSupport can be abused by a threat actor such as Gamaredon (Russian APT) for example.

Infection Chain:
Target – MS Windows Platform
Infection Vector – Malspam campaign of phishing emails
Sample Information:
Threat Name: Netsupport | Classification: Backdoor
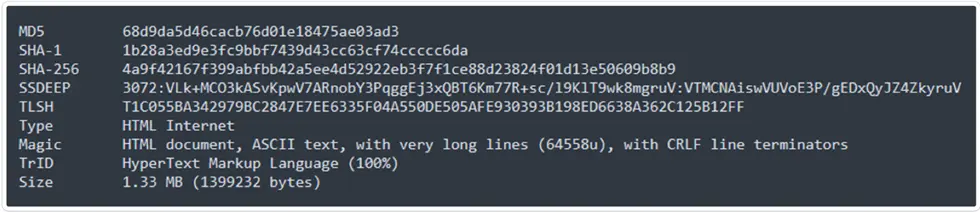
Technical Analysis of HTA Based NetSupport Campaign:
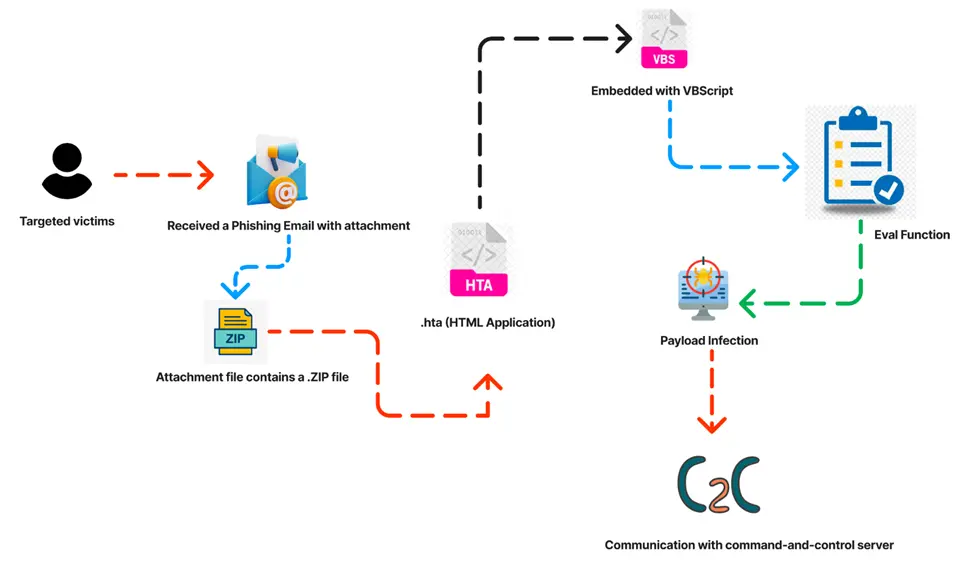
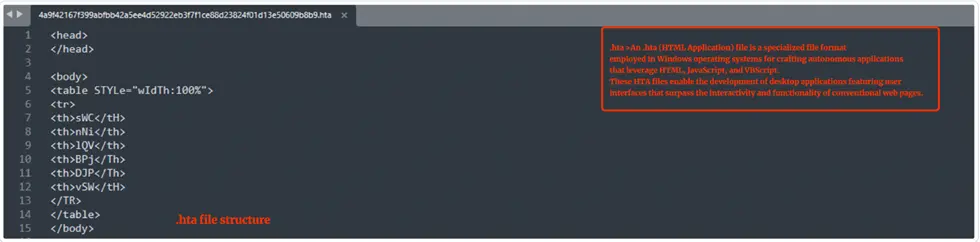
An HTA (HTML Application) file is a Windows-specific format that blends HTML and JavaScript, packaged into a standalone executable file with a “.hta” extension. Developers use HTA files to craft Windows applications using web-based technologies, simplifying the creation of interactive programs with graphical interfaces.
HTA files possess the capability to interact with system resources and run with elevated privileges, which, if mishandled, can introduce security vulnerabilities. While HTAs serve legitimate purposes, they can also be exploited by malicious individuals to distribute malware or carry out attacks.
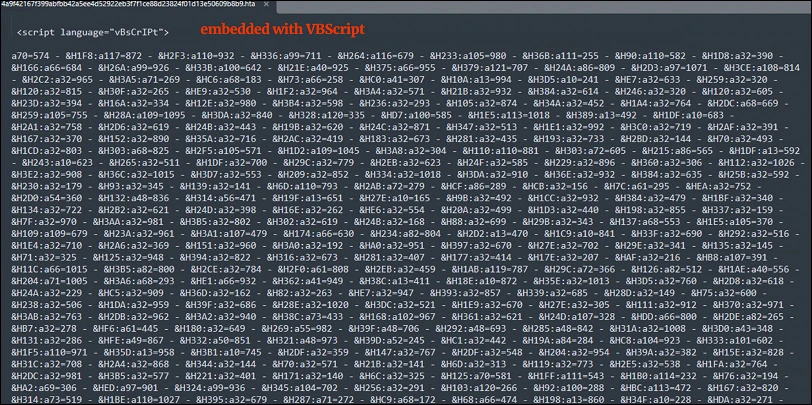
This campaign typically commences with the dissemination of spam emails. These emails frequently include a ZIP file containing an HTA application, which is embedded with a VBS script designed to execute malicious functions using the “eval” function within the targeted network.
Streamlined Structure of HTA:

Embedded VBScript:
VBScript is a scripting language frequently employed in Windows environments, making it highly suitable for handling scripting tasks on Windows systems. Consequently, it becomes a convenient option for malware authors seeking to exploit vulnerabilities or engage in malicious activities on Windows-based computers.
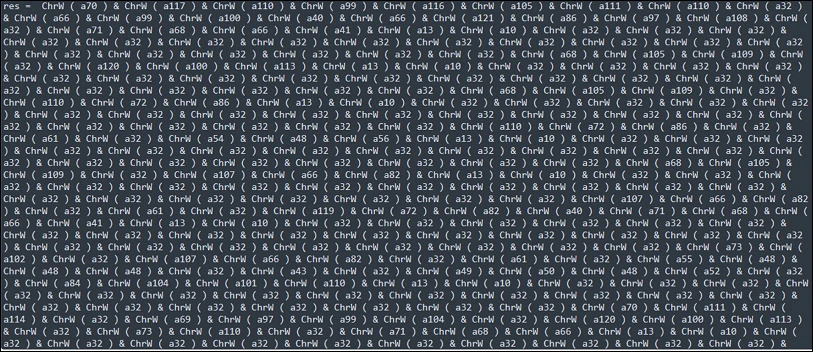
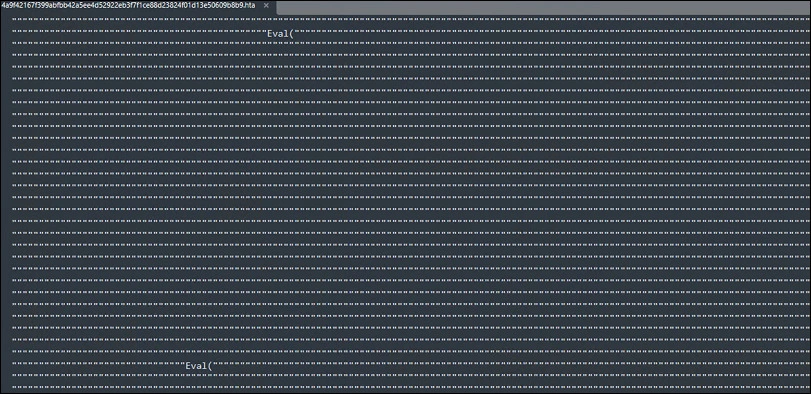
The Eval function serves the purpose of assessing or executing a designated expression or statement as though it were VBScript code. It expects a string argument that holds the expression or statement to be assessed and provides the outcome of that assessment as its result.
Malware authors opt for HTA (HTML Application) files in phishing schemes due to the following advantages:
Legitimacy: HTA files are recognized as valid Windows file formats, reducing suspicion when sent as email attachments or downloaded from websites.
Versatility: HTAs allow the execution of HTML and JavaScript, enabling the creation of realistic phishing pages that mimic legitimate websites, increasing the chances of deceiving victims into divulging sensitive data.
Interactivity: These files support interactive elements and forms, facilitating the creation of convincing login screens and payment portals to prompt users to share confidential information.
Customization: Malicious actors can easily tailor HTA phishing pages to imitate specific organizations, enhancing their success rates.
Persistence: HTAs can run locally on compromised systems, allowing cybercriminals to maintain a long-term presence.
Process Tree:
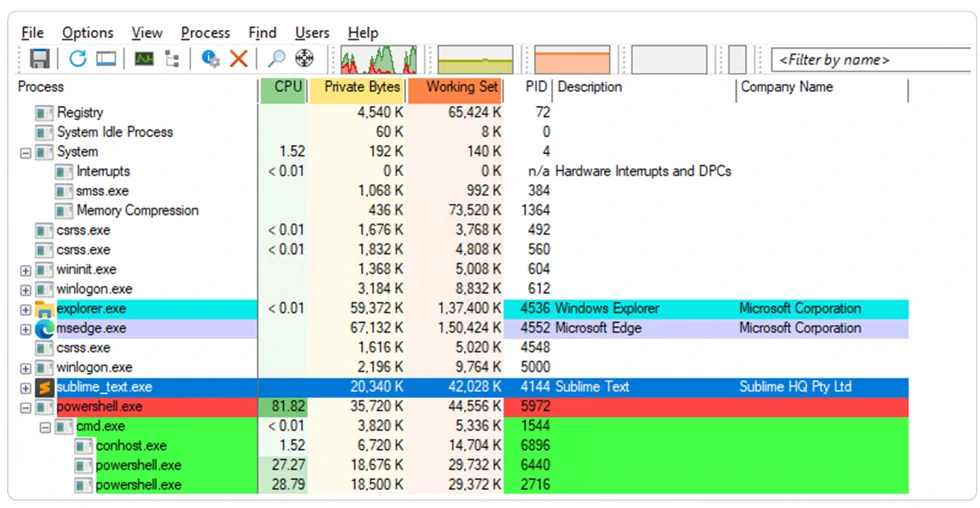
Indicator of Compromise:
To protect against these kinds of abuses, it’s essential to adhere to best practices such as;
Regular Software Updates: Ensure that both the operating system and all applications are up-to-date with the latest security patches.
Use Network Segmentation: Segmenting your network can help prevent lateral movement of malware. If one segment is compromised, it’s more difficult for the malware to spread to other segments.
Employ Whitelisting: Use application whitelisting to allow only authorized applications to run on systems. This can prevent unauthorized use of remote administration tools.
Monitor Network Traffic: Regularly monitor network traffic for any unusual patterns or activities, which might indicate unauthorized use of remote administration tools.
Educate Users: Provide cyber security training to employees, educating them about the dangers of downloading files from unknown or less trustworthy sources and clicking on suspicious links.
MITRE ATT&CK Tactics & Techniques:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Attachment |
| TA0002 | Execution | Windows Management Instrumentation Scripting – HTA |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task / Job |
| TA0005 | Defense Evasion | Virtualization and Sandbox Evasion Technique Obfuscated file or Information File System Logical Offsets |
| TA0006 TA0007 TA0008 | Credential Access Discovery Lateral Movement | OS Credential Dumping LSASS Memory Input Capture System Software Discovery Process Discovery File and Directory Discovery Query Registry Remote file copy |
| TA0009 TA0011 | Collection C&C Server | Credential API Hooking Archive Collected Data Data from Local System Remote file copy Web Protocols – Standard Application Layer Protocol |


