Adwind RAT (Remote Access Trojan) is a cross-platform, multifunctional remote access program which is distributed through a single malware-as-a-service platform. One of the main features that distinguish the Adwind RAT from other commercial malware is its distribution openly in the form of a paid service, where the “customer” pays a fee for using the malicious program. The aliases for Adwind RAT include: Adwind, Alien Spy, JConnectPro, JBifrost, JSocket, UnknownRat & UnReCoM.
Static Analysis
Language Used: Java / JDK 1.6x/1.7x / Swing
Code base: Frutas Rat (2012-2013)
Target OS: Windows, Linux, Mac OS, Android
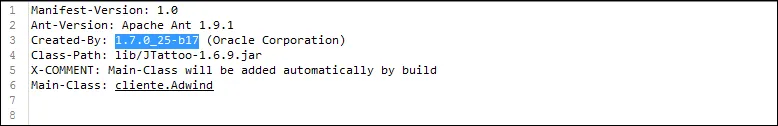
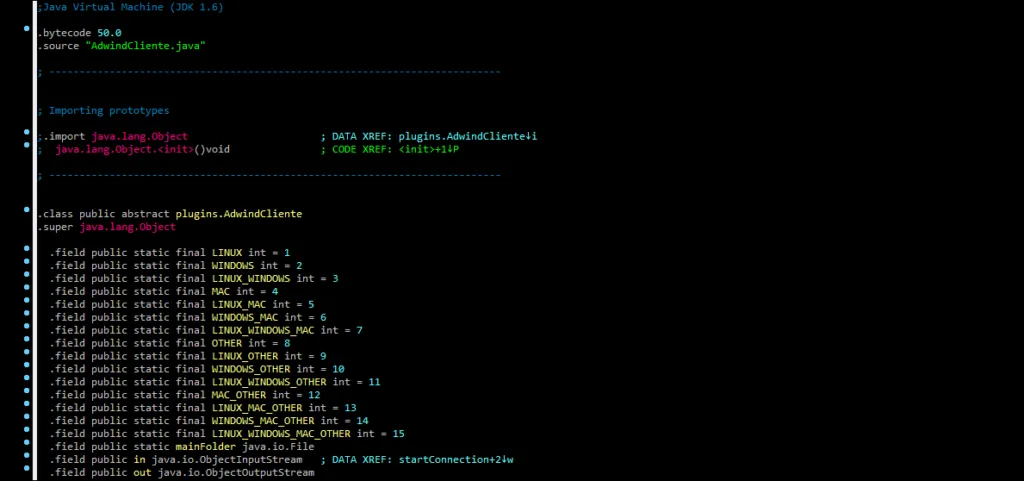
After 2012, throughout the subsequent rebranding, Adwind maintained control, and the aliases were sold separately, as products although they all share the same code base, that of jFrutas / Frutas RAT. This particular RAT played a significant role in attack campaigns against banks, and one of its variants was implicated in Alberto Nisman’s murder.
Anti-VMWare/Virtual Box Code
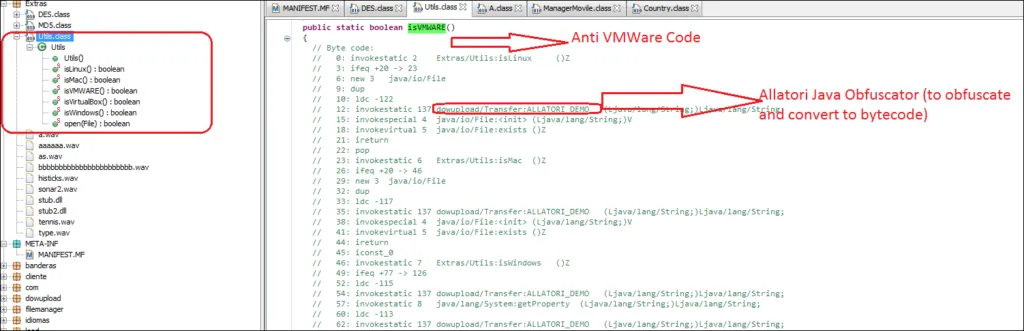
Although malware can be camouflaged in a variety of ways, testing for the presence of virtual environments reduces the possibility that it will get executed and thereby get detected. Adwind has a good illustration of this evasive behavior using byte code, before engaging in any malicious activity, Adwind code checks the system to see if it is running in a Virtual Box or VMware virtual machine.
Code hints at a Spanish author
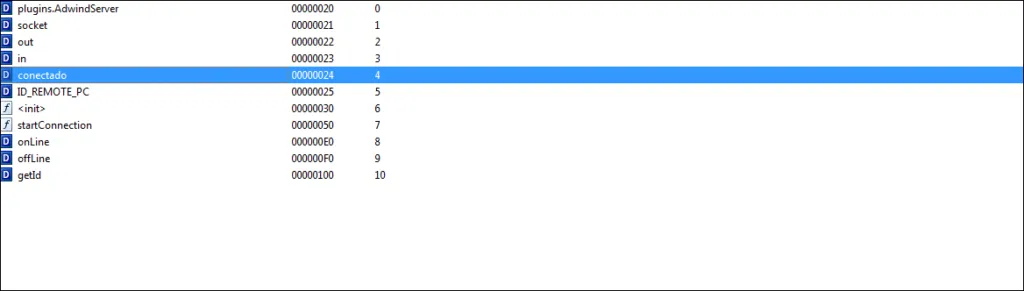
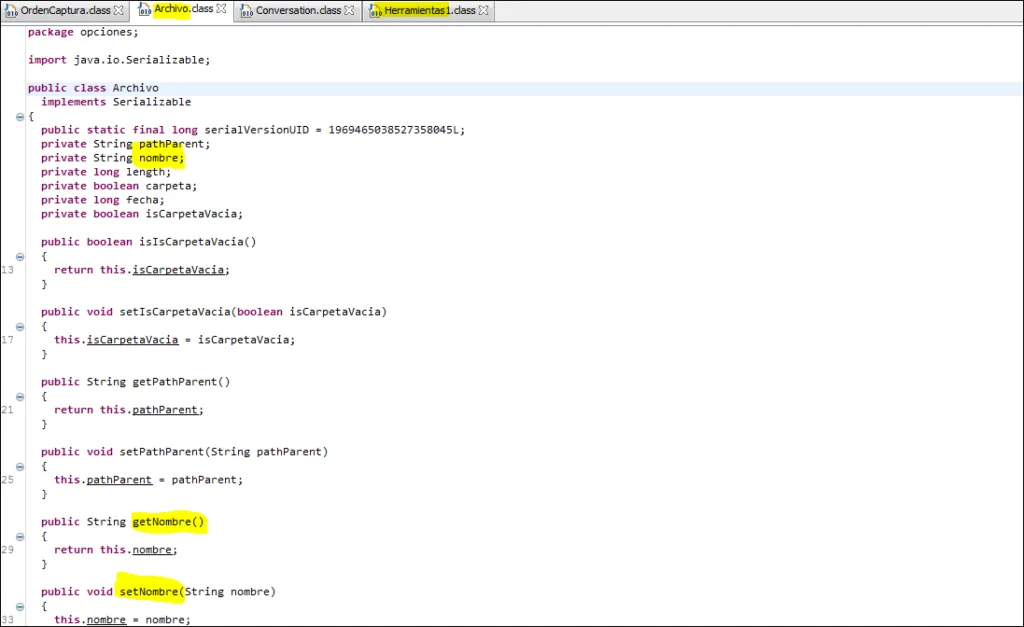
Class names, variables, function names declared and used in Java are from Spanish language, Example; Archivo, conectado, herramientas, nombre etcetra.
Translation: Nombre – Number, Archivo – Archive, Herramientas – Tools
Dynamic Analysis
Infection Chain
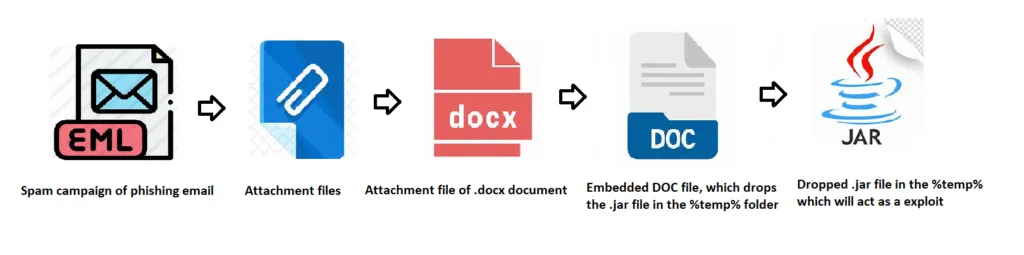
Adwind RAT infects the victim’s machine by initial infection vectors of spam campaign with attachment (EML), and a suspicious URL to download the malware. The attachment is a MS Word document (.DOCX). The threat actor can trick the user to click on the blurred image to view the document’s content. Once the user opens the .img content, using embedded doc to drop the .JAR file in the %temp% folder to start infecting and perform threat actor’s action on objective.
Sample Information
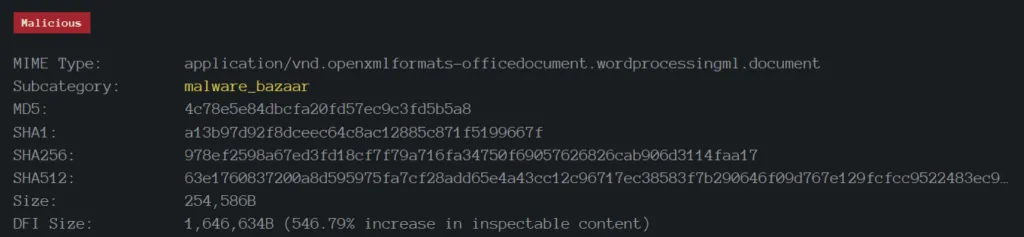
SHA256: 978ef2598a67ed3fd18cf7f79a716fa34750f69057626826cab906d3114faa17
Category: Remote Access Tool / Spyware
Threat Name: Adwind RAT
Technical Analysis of DOCX
Snap 1: Attachment document of [.docx]
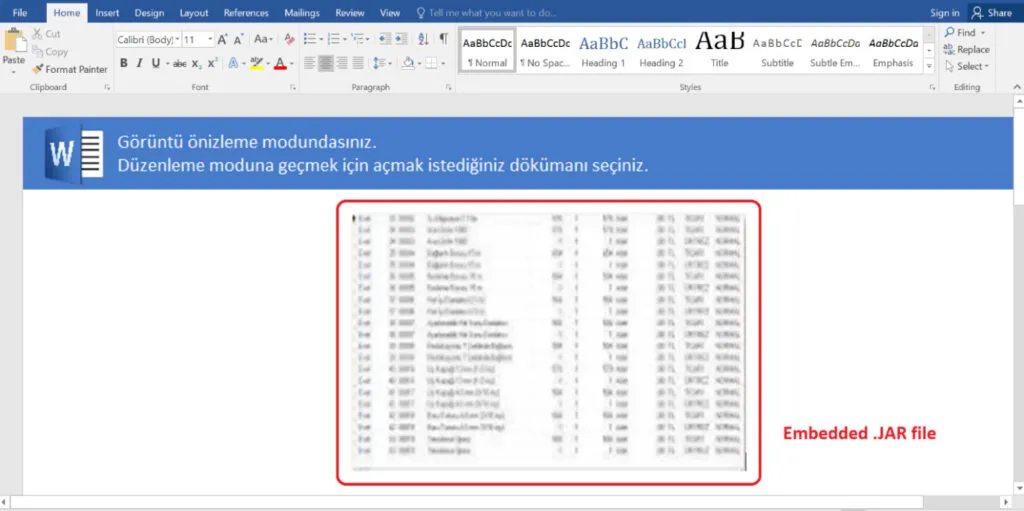
Once the user opens the attachment file, we can see there’s a blurred image, resembles some MS Excel work. What do we usually get? Click the enable content/enable editing to view the actual content of the image. Now, the document displays a blurred image embedded in the .JAR file.
Snap 2: Generation of .JAR file
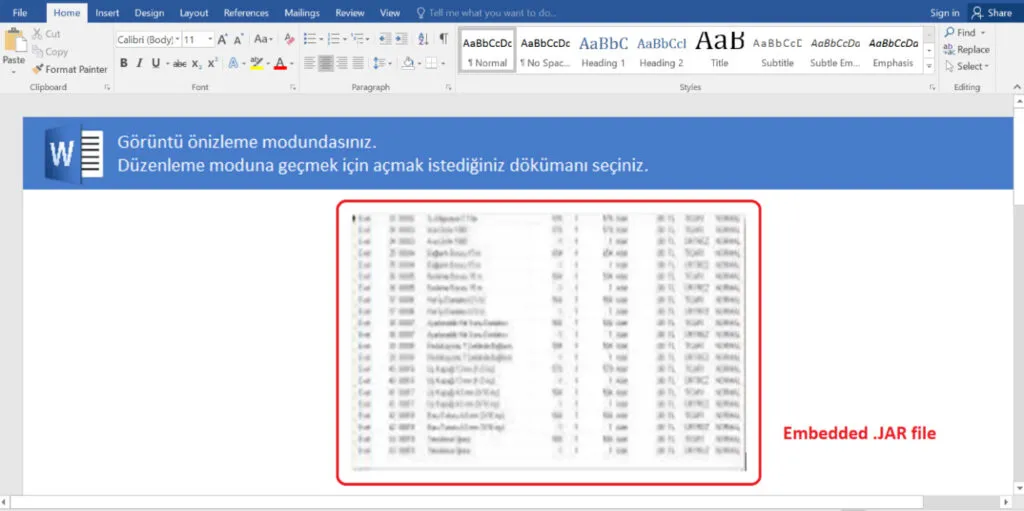
Once the user clicks on the blurred image, then a pop-up will be generated, it loads the JAR file and requests the user’s permission to open. If you run the malware manually, it will infect your system and even crash it when permissible.
Snap 3: .JAR properties
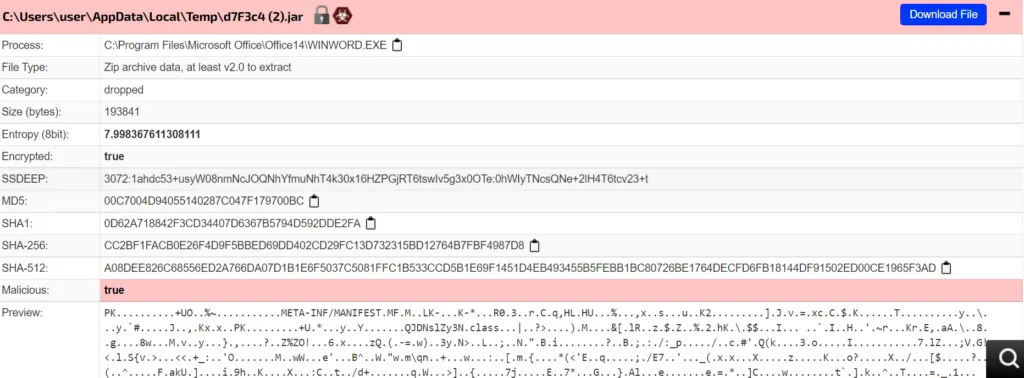
JAR files are .zip files that contain a compressed version of .class files, audio files, image files, or directories. The main advantage of JAR files such as lossless data compression, archiving, decompression, and archive unpacking. Not to mention, JAR files (Java code) can be run on any platform, code once and infect multiple operating systems.
Snap 4: Structure of MS Word [DOCX] document
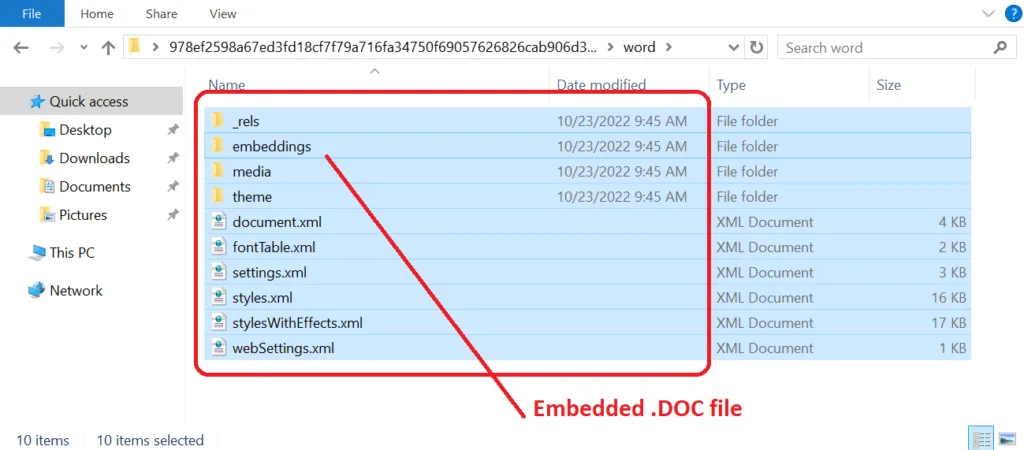
DOCX files store data in Open XML Document format, which was introduced by Microsoft from MS Word 2007. It replaced the .DOC file format as the standard format for saving documents in MS Word. Unlike DOC files, which store document data in a single binary file, DOCX files save data as separate files and folders in a compressed ZIP package. Within a DOCX file are XML files and three folders: Word, docProps, and _rels, which store the content, document properties, and relationships between the files. The Open XML format is designed to make document content more open and accessible.
For example, document text is saved in plain text files, and document images are stored as individual image files, such as .JPG or .PNG, within the DOCX file. The included files may also contain page formatting information, authorship data, and document review notes.
Snap 5: Embedded DOC file
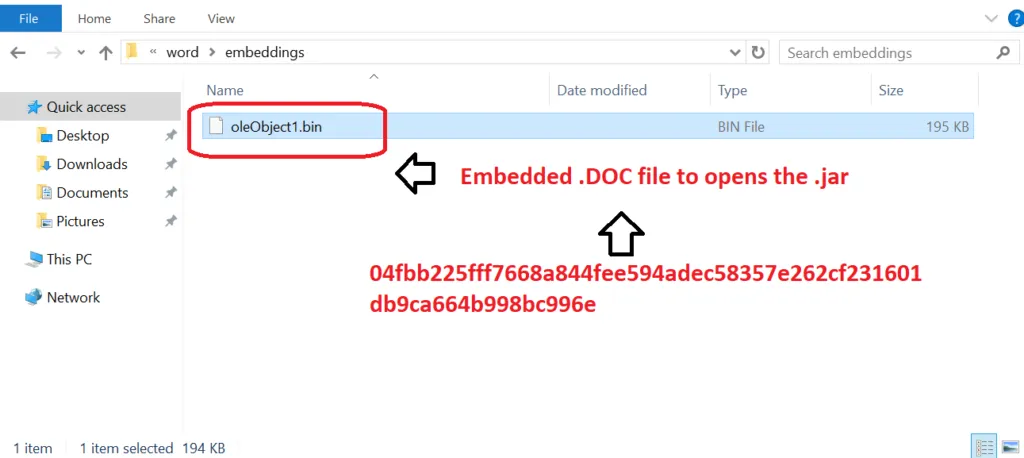
DOC files are created to save various documents, including letters, resumes, essays, and invitations. When we create a document in MS Word, we can then choose to save it in either the DOC, or DOCX file format. Adwind JAR then creates a DOC file to store the document’s contents, which can be closed and opened again for further editing. When you are done editing your DOC file you can print it or save it as another file, such as .PDF document or .DOT (template) document.
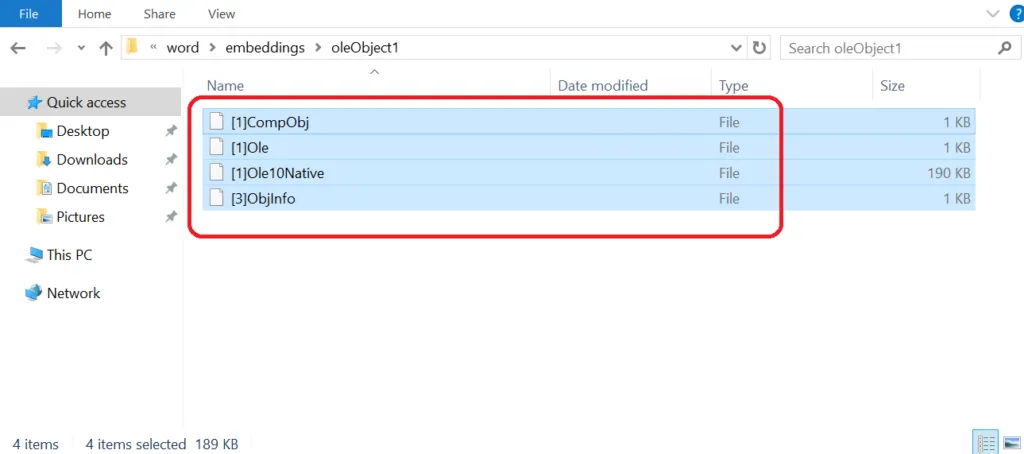
Snap 6: Embedded OLE_native files
Snap 7: Dropped .JAR in %temp%
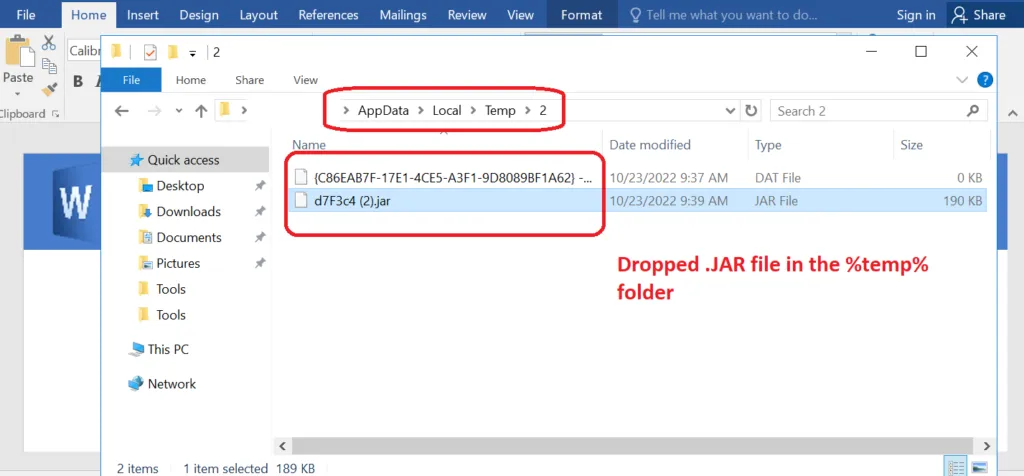
After the completion of step 2 once the user accepts & opens the document content. Then, the .JAR file will be dropped in the %temp% folder.
Snap 8: Structure of .JAR file
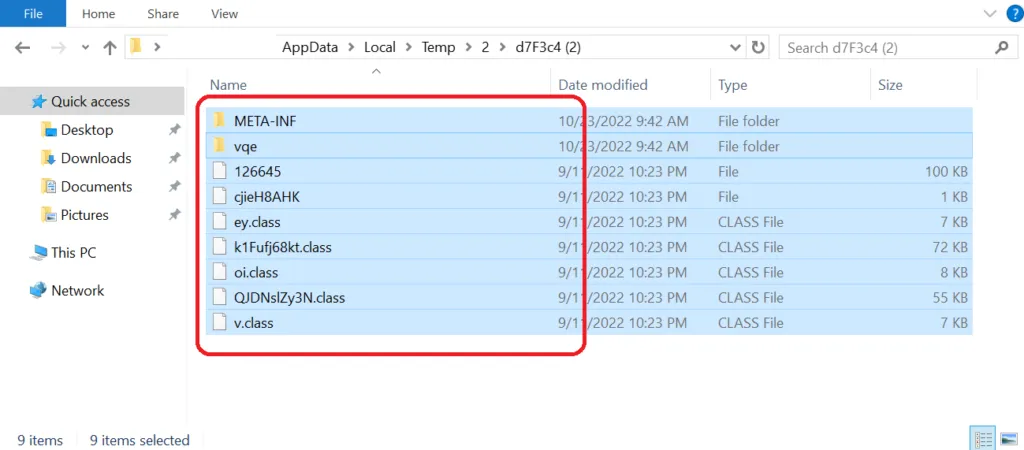
JAR file is a Java archive (JAR) file used by the Java Runtime Environment (JRE), a framework used for executing Java programs. JAR files may serve as program libraries or as standalone programs that run if the JRE is installed on the computer or mobile device. After 2015-2016, a lot of the cracked versions of Adwind malware being circulated are used by hundreds of threat actors, which means that there are multiple hundreds of command-and-control servers. Some of them are down, some are up, the others are turned on as required by the threat actors.
Once infected, the following process/functions are carried out by Adwind RAT,
- Collecting information about the compromised host.
- Creating scheduled tasks (privilege escalation and persistence).
- Credentials harvesting.
- Taking screenshots, pictures, and recording video & sound from a microphone/webcam.
- Credential dumping (.exe access).
- Password stealing (from browser history and cookies).
- Steal VPN certificates.
- Targeting web banking links (web injects).
- Stealing keys of cryptocurrency wallets.
- Password brute forcing.
- Process injection to conceal the malicious actions.
MITRE ATT&CK Mapping for jRAT / Adwind RAT
| ID | Technique | Functionality |
| T1123 | Audio Capture | jRAT can capture microphone recordings. |
| T1037 | Boot or Logon Initialization Scripts: Startup Items | jRAT can list and manage startup entries. |
| T1115 | Clipboard Data | jRAT can capture clipboard data. |
| T1059 | Command and Scripting Interpreter: Windows Command Shell | jRAT has command line access. |
| Command and Scripting Interpreter: Visual Basic | jRAT has been distributed as HTA files with VBScript. | |
| Command and Scripting Interpreter: JavaScript | jRAT has been distributed as HTA files with JScript. | |
| T1555 | Credentials from Password Stores: Credentials from Web Browsers | jRAT can capture passwords from common web browsers such as Internet Explorer, Google Chrome, and Firefox. |
| T1083 | File and Directory Discovery | jRAT can browse file systems. |
| T1070 | Indicator Removal: File Deletion | jRAT has a function to delete files from the victim’s machine. |
| T1105 | Ingress Tool Transfer | jRAT can download and execute files. |
| T1056 | Input Capture: Keylogging | jRAT has the capability to log keystrokes from the victim’s machine, both offline and online. |
| T1027 | Obfuscated Files or Information | jRAT’s Java payload is encrypted with AES. Additionally, backdoor files are encrypted using DES as a stream cipher. Later variants of jRAT also incorporated AV evasion methods such as Java bytecode obfuscation via the commercial Allatori obfuscation tool. |
| Software Packing | jRAT payloads have been packed. | |
| T1120 | Peripheral Device Discovery | jRAT can map UPnP ports. |
| T1057 | Process Discovery | jRAT can query and kill system processes. |
| T1090 | Proxy | jRAT can serve as a SOCKS proxy server. |
| T1021 | Remote Services: Remote Desktop Protocol | jRAT can support RDP control. |
| T1029 | Scheduled Transfer | jRAT can be configured to reconnect at certain intervals. |
| T1113 | Screen Capture | jRAT has the capability to take screenshots of the victim’s machine. |
| T1518 | Software Discovery: Security Software Discovery | jRAT can list security software, such as by using WMIC to identify anti-virus products installed on the victim’s machine and to obtain firewall details. |
| T1082 | System Information Discovery | jRAT collects information about the OS (version, build type, install date) as well as system up-time upon receiving a connection from a backdoor. |
| T1016 | System Network Configuration Discovery | jRAT can gather victim internal and external IPs. |
| T1049 | System Network Connections Discovery | jRAT can list network connections. |
| T1007 | System Service Discovery | jRAT can list local services. |
| T1552 | Unsecured Credentials: Credentials In Files | jRAT can capture passwords from common chat applications such as MSN Messenger, AOL, Instant Messenger, and and Google Talk. |
| Unsecured Credentials: Private Keys | jRAT can steal keys for VPNs and cryptocurrency wallets. | |
| T1125 | Video Capture | jRAT has the capability to capture video from a webcam. |
| T1047 | Windows Management Instrumentation | jRAT uses WMIC to identify anti-virus products installed on the victim’s machine and to obtain firewall details. |
Indicator of Compromise
Hashes
7e4bdf62d3ecd78b3f407f6ec1158678
0a5f34440389ca860235434eea963465
1da18ec639f7ec2a8aad58655d846e23
d7489b47e17630e5594a320b43b201db
da52c24302a03626d2175123b751f466
b766cf6695730b74a107cb73157262b1
919f2d0043f063a90702fb36887699e8
d470d5a428f99818278fb2816a8d03e9
8f5e55fbb1bee93dc5912dcbd0092519
4a97b2d004d72b69aa64f621b5b74775
051b4da1f0079c6f60d6c8eb62b3f586
2020551b5373121053abdbf3eaafa02d
a4da22e269b93148eb9857036b9a072a
876eb4208ef2eec6e9f12b13f764a975
1d77e96974e1e2301ed78cec19e8710b
IP Address / Domains
212[.]114[.]52[.]236:9932
unks123[.]duckdns[.]org:46865
lay[.]dubya[.]us:8181
fresh[.]ygto[.]com:1010
gwiza1988[.]hopto[.]org:6025
praisesalways[.]ddns[.]net:1010
wawa[.]cleansite[.]us:1010
dlee889.mywire[.]org:5858
URLs Hosting the JAR files
hxxp://haus-pesjak[.]at/Covid-19Update.jar
hxxps://digitaltextile[.]com[.]ru/lk/Deutsche%20Telekom.jar
hxxps://digitaltextile[.]com[.]ru/n/DHL%20paket.jar
hxxp://haus-pesjak[.]at/04-07-20Intuitinvoices.jar
hxxp://teddyshatsworld[.]pl/Reylontransport-covid19-statement20.jar
hxxp://thaivictory[.]co[.]th/pageconfig/album/dir/5/order.jar
hxxp://cherryemoore[.]com/USPS/RedeliveryUSPS.jar
hxxps://feylibertad[.]org/Amazon-PO20023938.jar
hxxp://mahalowood[.]com/USPS/USPSReschedulerLabel.jar
hxxps://newsha[.]jsonland[.]ir/wp-includes/css/DHLPaket.jar
hxxps://www[.]stillval[.]com/USPS/RescheduleUSPS.jar
hxxps://thediscoveryrun[.]com/UPS/ShippingInfo.jar
hxxp://jeddahcrumbly[.]com/DHLPAKET.jar
hxxp://dev[.]medialogistics2020[.]ca/wp-content/plugins/ubh/Quickbooks-INV5066.jar


