
Agent Tesla is a widely recognized keylogger and password stealer that operates within the .NET framework. This malicious software possesses the ability to monitor keystrokes, capture screenshots, extract passwords from various applications, and transmit stolen data to threat actors using standard protocols. According to available information, this keylogger was initially promoted on a Turkish website as a remote access tool for monitoring personal computers.
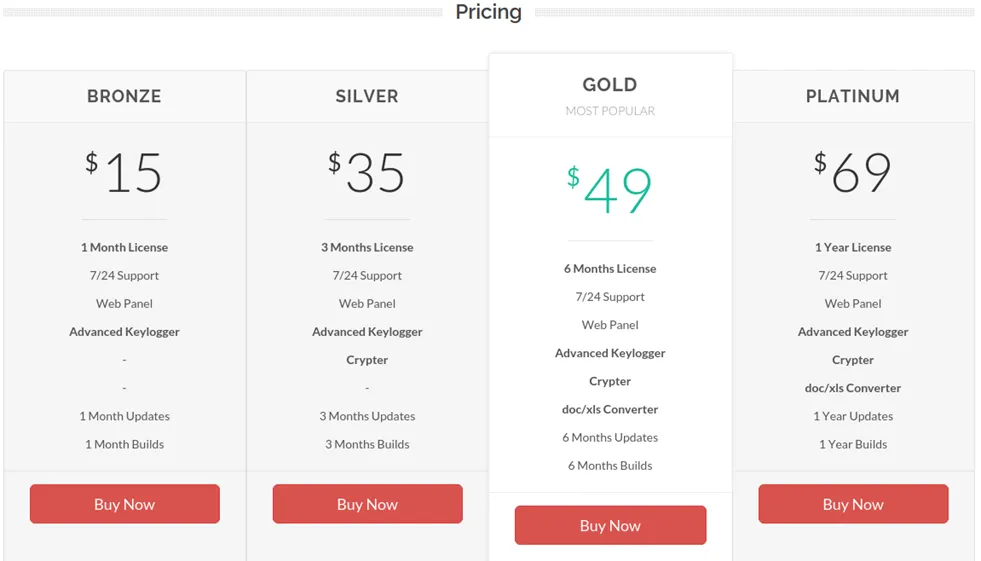
Agent Tesla – Administration Panel
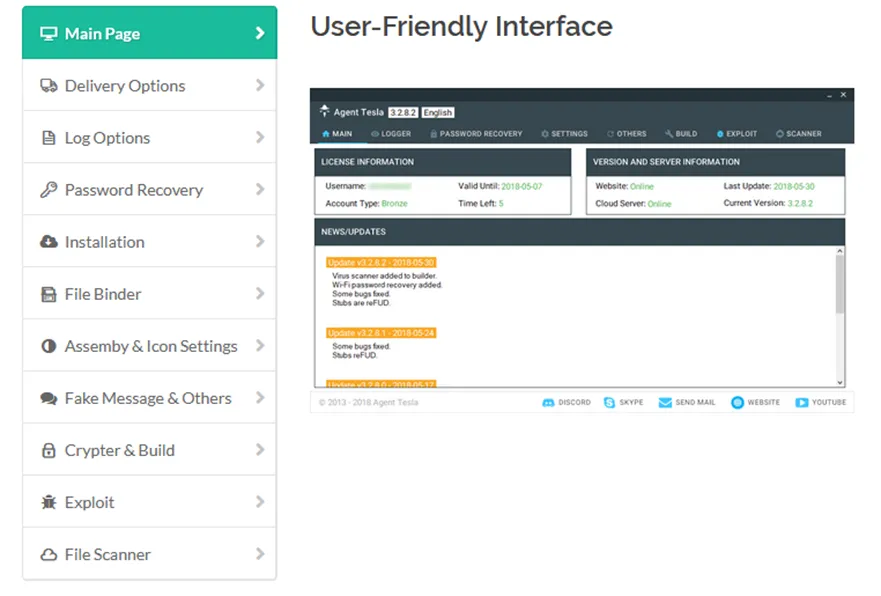
The Hidden Realm (C2 Server) for Tesla’s Admin Panel
At the heart of every RAT lies its command and control infrastructure, and for Agent Tesla, this central hub is its admin panel. The admin panel is a web-based interface that empowers attackers to manage infected machines, steal sensitive data, and orchestrate various malicious activities. Unlike some other RATs, Agent Tesla’s admin panel boasts a user-friendly design that enables even less technically-inclined attackers to navigate it with ease. The interface is divided into distinct sections, each serving a specific purpose, such as viewing captured data, managing infected endpoints, and setting up campaigns.
Visual Aesthetics with Sinister Intent
Agent Tesla doesn’t merely stop at functionality; it also pays careful attention to aesthetics. One of its unique traits lies in its visually appealing interface. Designed to mimic legitimate software, the admin panel exudes a professional appearance that may deceive unsuspecting victims into believing it is a harmless application. This deceptive design further enhances the malware’s success rate in infecting and compromising target systems.
While the visual design might seem contradictory to its malicious intent, it’s important to remember that attackers often exploit psychology to manipulate victims. The professional and benign appearance of the admin panel can lull users into a false sense of security, facilitating successful infiltration and data theft.
Unique Features of Agent Tesla that can raise eyebrows!
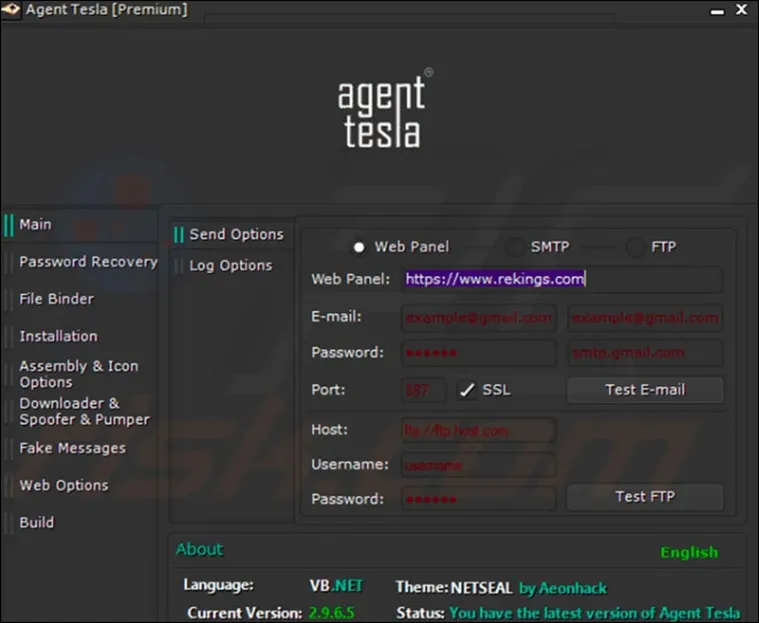
Beyond its visual aesthetic, Agent Tesla boasts several lesser-known features that make it a formidable threat in the malware landscape:
Keylogger Capabilities: Agent Tesla is equipped with a powerful keylogging feature that records every keystroke made on the infected system. This includes passwords, credit card information, and other sensitive data, enabling attackers to gain unauthorized access to user accounts and confidential information.
Multilingual Support: In a globalized world, cybercriminals target victims from all corners of the globe. Agent Tesla recognizes this and offers multilingual support in its admin panel, allowing attackers to customize their phishing campaigns and communication to different regions and languages.
Form Grabbing: This unique feature allows Agent Tesla to intercept and capture data entered into web forms. This includes information submitted on websites such as login credentials, personal details, and payment information.
Automatic Updates: Keeping up with the times, Agent Tesla ensures its capabilities are up-to-date by offering automatic updates to its admin panel. This ensures attackers can utilize the latest techniques and evasion methods to avoid detection.
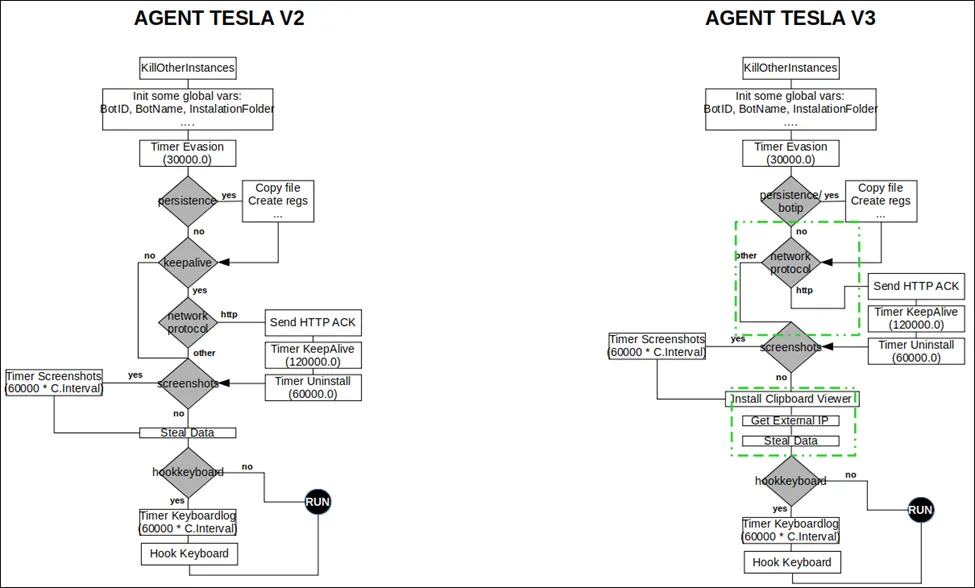
Infection Chain:
Target – MS Windows Platform
Infection Vector – Malspam campaign of phishing emails
Sample Information: Threat Name:
Agent Tesla | Classification: Spyware or Exploit | Category: Dropper
Technical Analysis of Macro XLS:
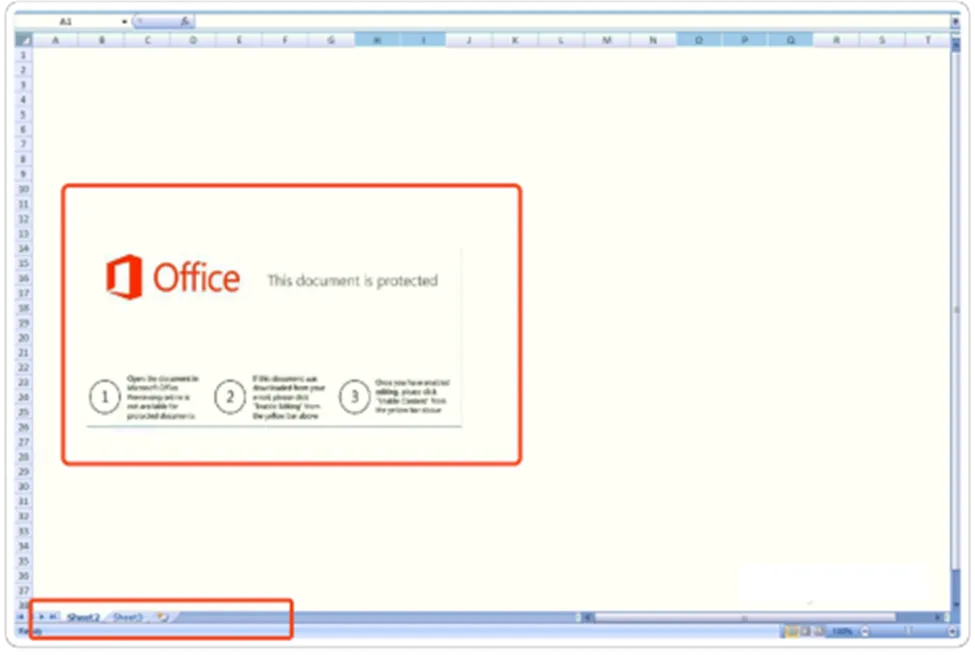
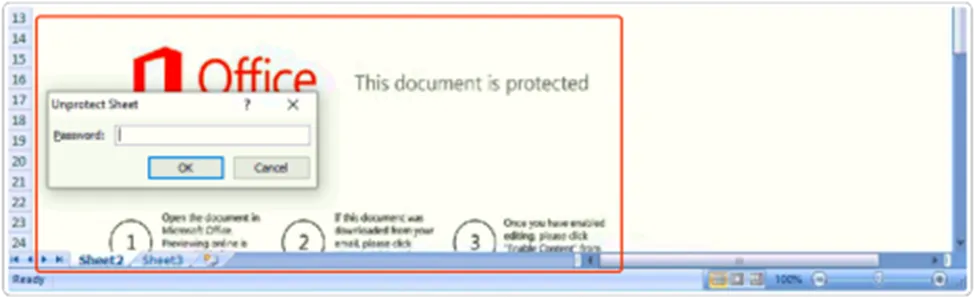
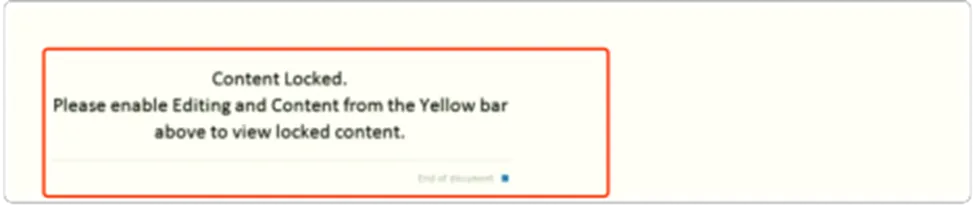
As usual this campaign commences through the distribution of spam emails, featuring the blurred image which states that, “Office This document is protected”. In-order to view the content, Enable it.
VBA Macro code is a type of code written in Visual Basic for Applications, designed to automate tasks and enhance the functionality of Microsoft Office applications like Excel, Word, PowerPoint, and Access. By utilizing VBA, users can create custom macros and automate repetitive tasks through coding.
The strength of VBA Macro code lies in its ability to expand the capabilities of Microsoft Office applications beyond their default features. This programming language enables automation, boosts productivity, and provides the flexibility to tailor applications to meet specific requirements.
File Structure of the XLS:
An XLS file is a structured binary file format used for storing spreadsheet data in Microsoft Excel. It consists of a collection of worksheets, each containing cells organized in rows and columns.
The XLS Sample file contains an embedded VBA Project code which has a below given specific file structure.
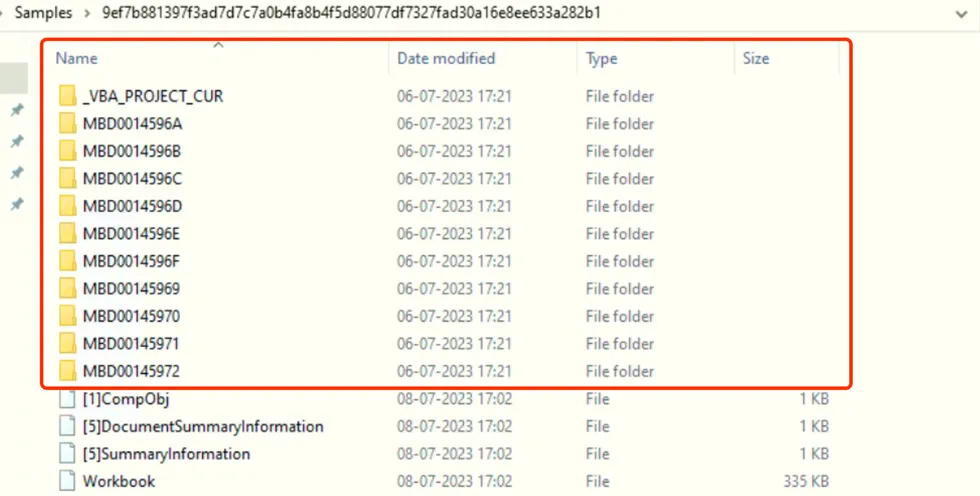
Currently, there are multiple folders present, each with a randomly generated name. We will proceed to inspect them individually.
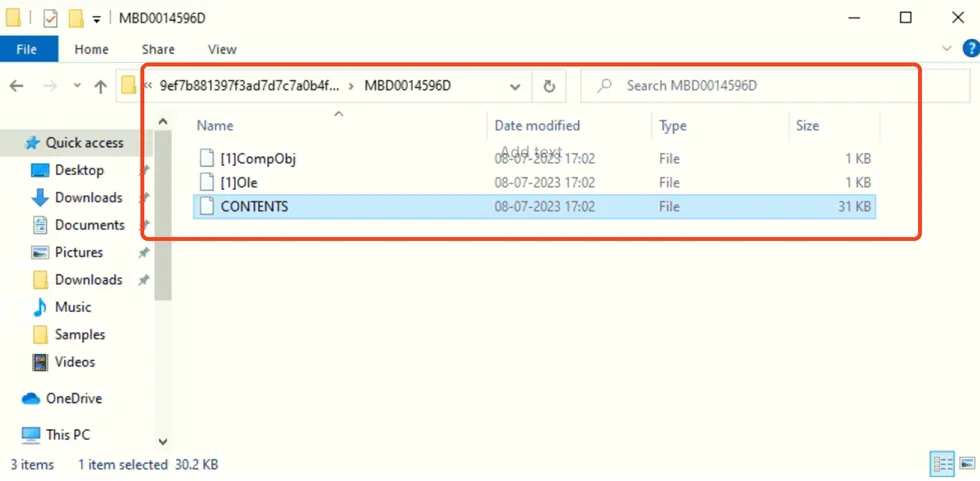
Let’s open them one by one:
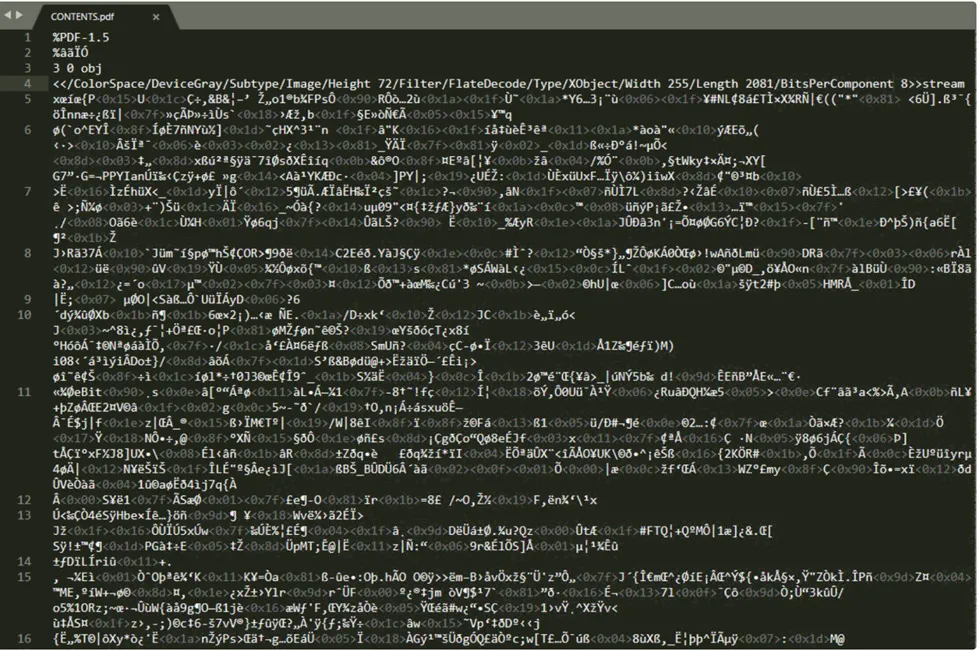
Once the file extension has been corrected, we can proceed to view the contents of the PDF file.
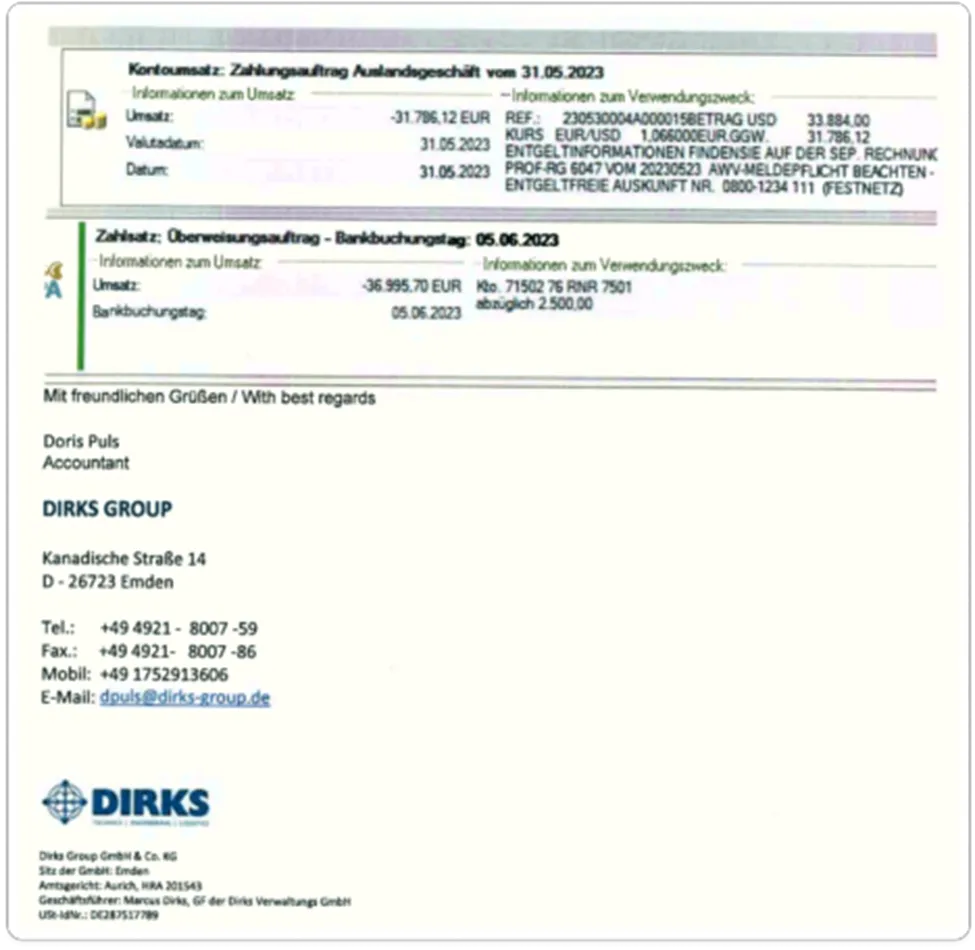
Then, we can quickly disassemble the XLS Document.
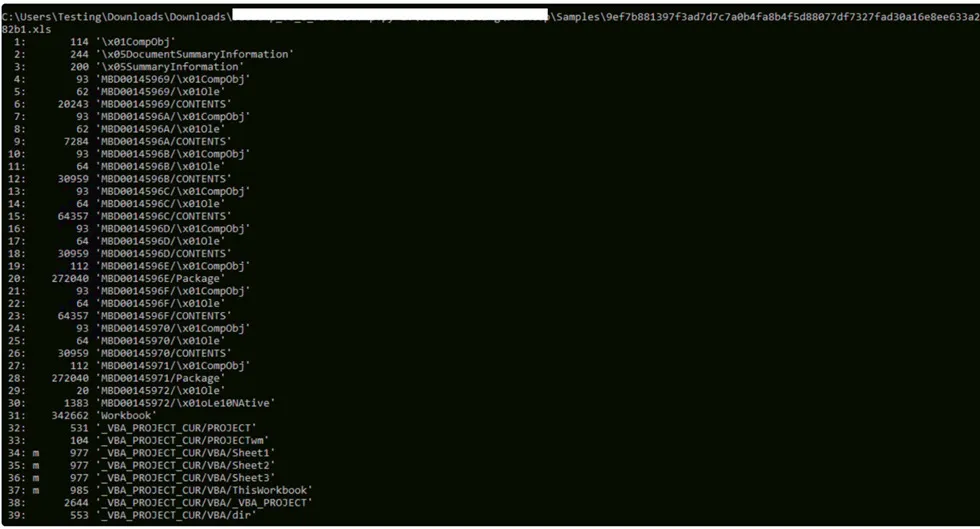
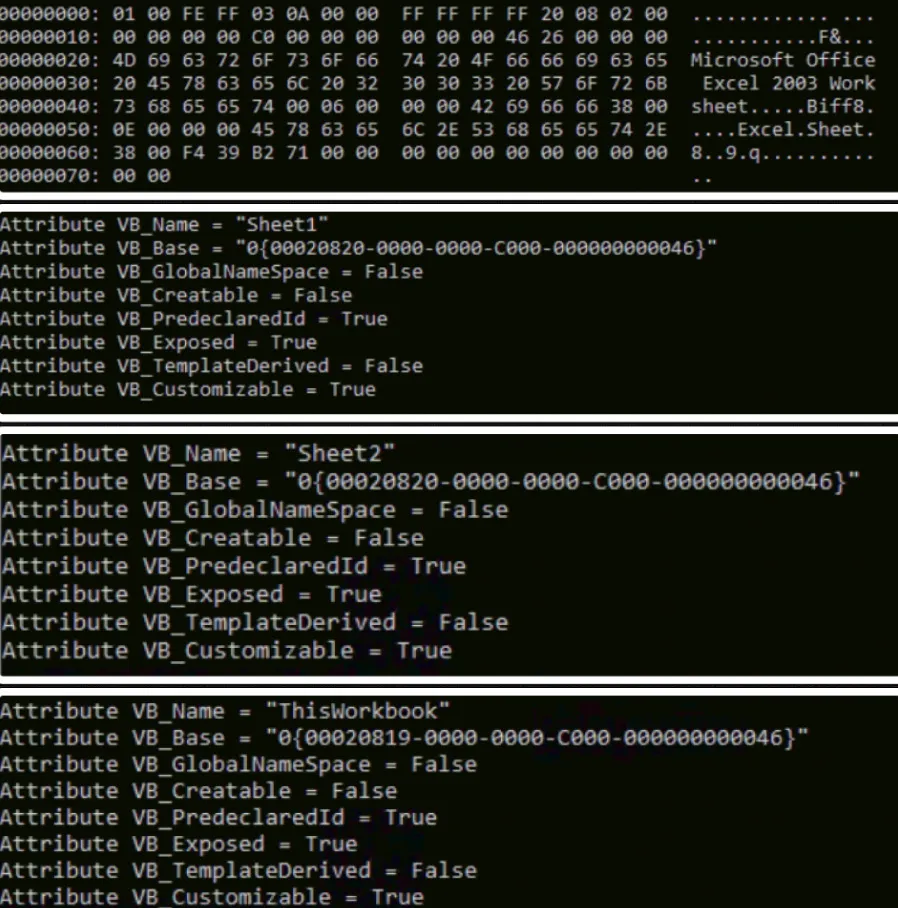
Entire – XLS Document with Embedded Modules > Sheet 1, 2 and 3 with Workbook
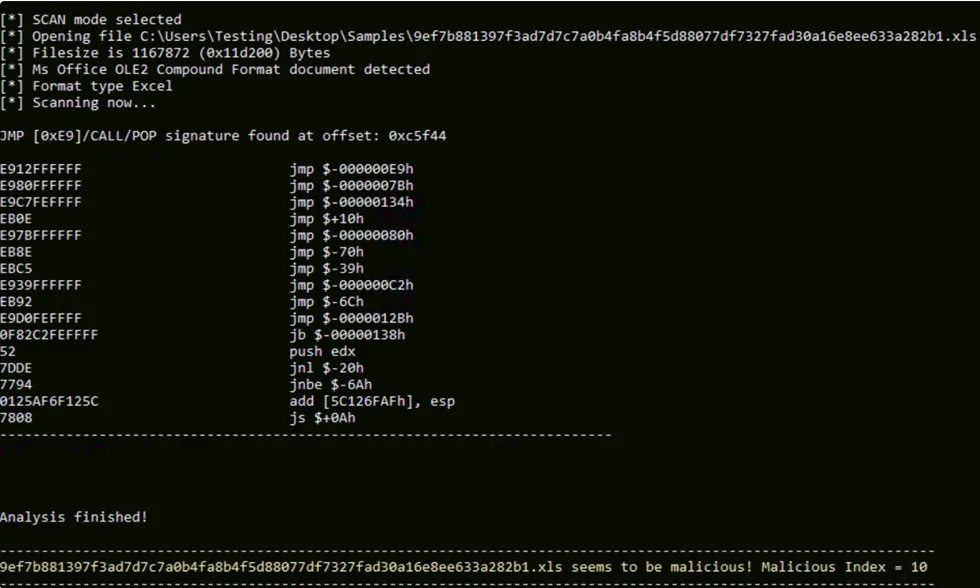
Let’s scan the XLS Document with inflate mode.
Typically, Agent Tesla performs a reconnaissance on the compromised system, initiating its new infection by “fingerprinting” the victim’s machine. This involves gathering information such as system memory, operating system details, computer name, user profiles, IP information, internet connectivity status, processor details, and browsing history. The objective of this reconnaissance is to steal various sensitive data, including banking credentials.
Indicator of Compromise for Agent Tesla sample:
The world of cyber security is akin to a battleground where hackers and defenders engage continually an ongoing struggle for supremacy. In this arena, Agent Tesla has emerged as a formidable adversary, boasting an admin panel that marries functionality with a deceivingly benign aesthetic. Its lesser-known features, including powerful keylogging, multilingual support, form grabbing, and automatic updates, cement its position as a potent threat that continues to evolve and adapt. As defenders strengthen their security measures, it is imperative to remain vigilant and informed about the capabilities of malware strains like Agent Tesla.
MITRE ATT&CK Tactics & Techniques for Agent Tesla sample,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting – XLS VBA Macro Codes Windows Management Instrumentation Native APIs Exploitation of Client Execution |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task / Job Access Token Manipulation Process Injection |
| TA0005 TA0006 TA0007 | Defense Evasion Credential Access Discovery | Virtualization and Sandbox Evasion Technique Obfuscated file or Information Software Packing Process Injection OS Credential Dumping Credentials in Registry System Time Discovery File and Directory Discovery System Information Discovery Query Registry Security Software Discovery |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Archive Collected Data Data from Local System Email Collection Clipboard Data |
| TA0011 | C&C Server | Ingress Tool Transfer Encrypted Channels Web Protocols – Standard Application Layer Protocol Non – Application Layer Protocol |


