
QakBot, aka QBot, QuakBot or Pinkslipbot, is a banking trojan malware that has existed for over a decade. The main purpose of Qbot is to steal banking credentials and other financial information (e.g., login credentials, passwords etc), while being able to deploy additional malware, log a user’s keystrokes, and create a backdoor to the compromised machines.
Some highlights of Qbot (Qakbot) malware are as follows,
The malware operates with a modular framework to inject DLL (payload) in to an existing Windows process,
Deploy any ransomware such as Blackbyte, Blackbasta (Conti Affiliates) or, Royal Ransomware on will,
Persist and survive reboots with Cobalt Strike payloads, and/or scheduled tasks on Windows,
Last but not least, through the cookie grabber and password stealer – it can steal passwords from popular browsers.
Did You Know? Malware authors also love continuous development lifecycles such as devops! Anecdotal evidence suggests around the first half of 2018, Qbot’s major version was 324! The most recent version of Qbot observed by LMNTRIX CDC was 401 to 403 in Jan 2021.
Infection Chain:
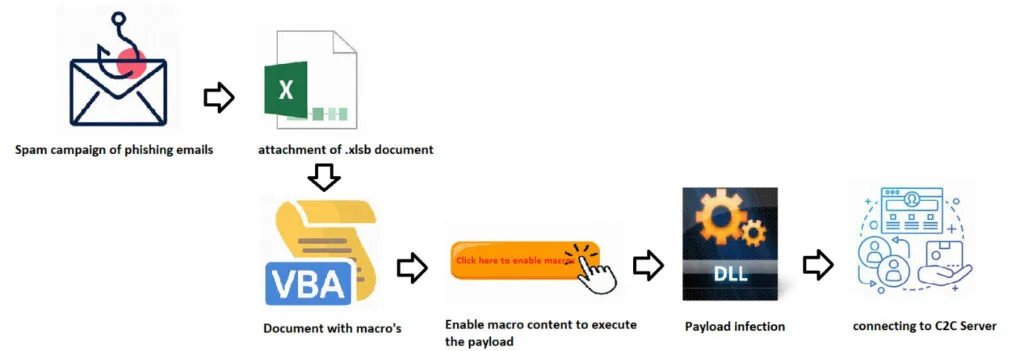
The initial attack vector may vary depending on the targets as we all know, the threat actors perform basic reconnaissance after initial access is established to decide their next steps. We have observed 3 variations of Qbot (Qakbot) being delivered namely,
Malspam -> Zip -> Javascript -> Qbot Infection
Malspam -> Zip -> VBS -> Qbot Infection
Malspam -> Word DOC (Macro) -> Qbot Infection
Qbot was previously distributed by Emotet, as observed by LMNTRIX CDC. Generally, QBot infects the victims by initial infection vector of malspam e-mails. This kind of e-mail contains Microsoft Office documents (Excel) or sometimes comes with password-protected archives format attachments. Usually, the document contains macros, and the victims are tricked to enable the macro content leading to the malicious actions. (e.g., an invoice or shipping attachment).
Sample Information:
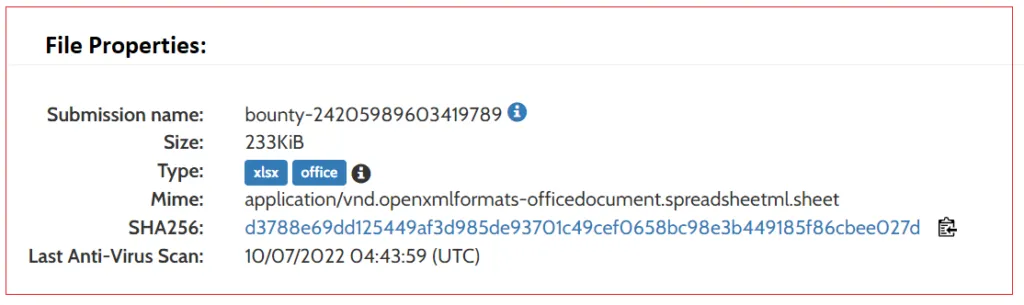
Why are malware authors using this file format?
XLSB is an Excel Binary Workbook file. They store information in binary format instead of XML like with most other Excel files (like XLSX). They can be read from and written much faster, making them extremely useful for very large spreadsheets. Also, the file sizes are smaller in XLSB, when compared with XLSX. Mainly .XLSB files have macros embedded in it, where they can store potentially malicious code.
Technical Analysis of Qbot XLSB:
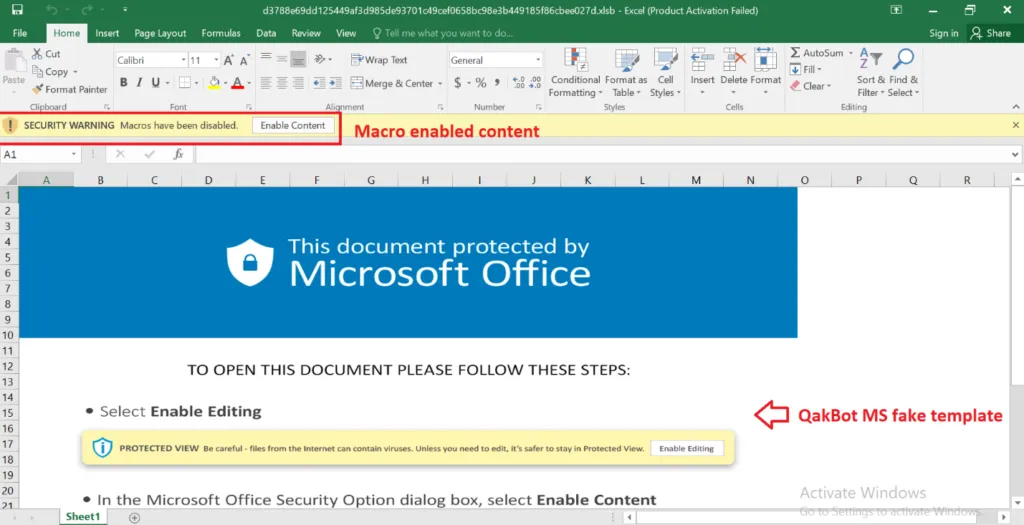
Snap 1: Enabled Content
Snap 2: Hidden Sheets
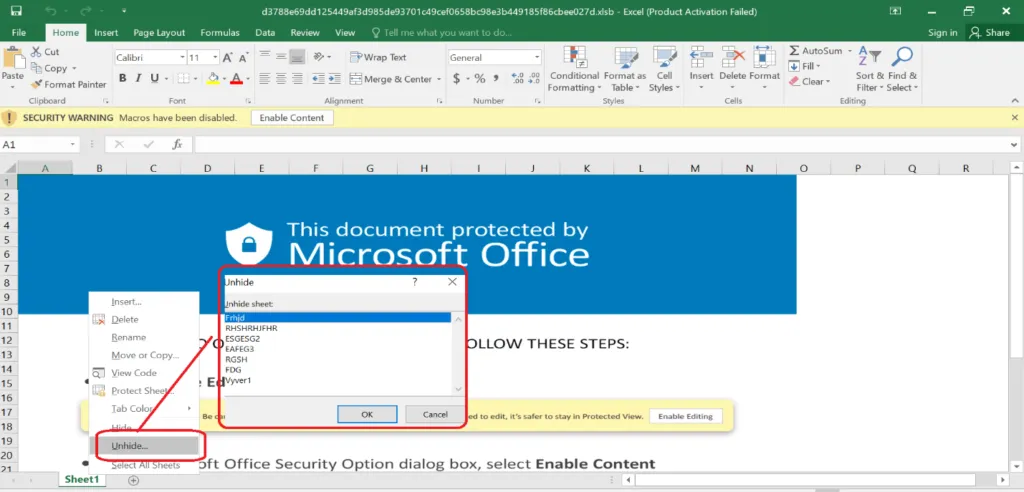
Excel worksheets are in hidden mode, and we need to unhide to see the contents embedding in the Sheets. Usually, it will contain URLs, Malicious/blacklisted IPs, and payload file paths etc., So far, QBot hasn’t changed the infection flow for macro styled attacks.
File Structure of the .xlsb:
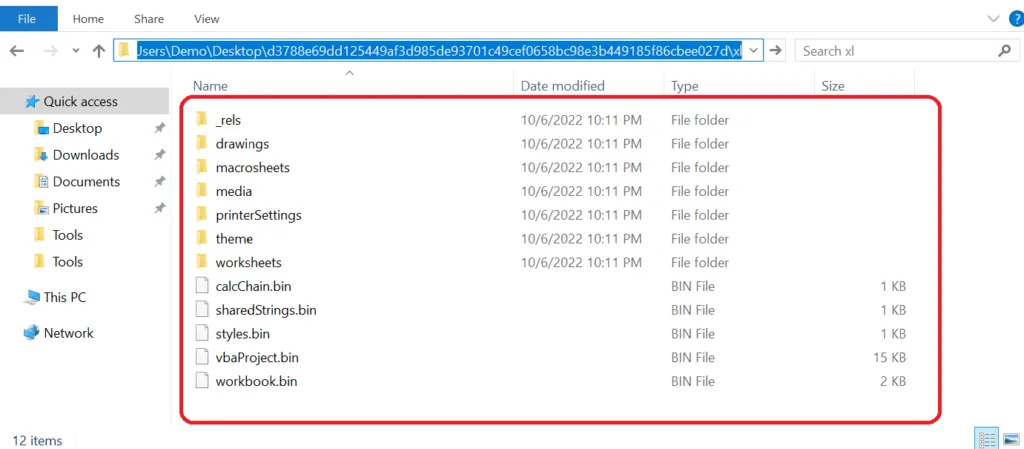
Macrosheets:
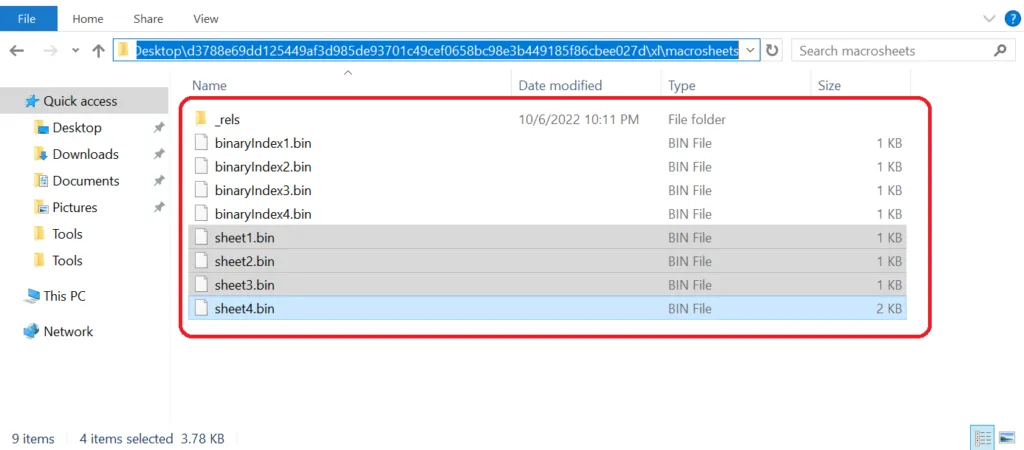
In fact, for huge Excel files used for accounting or statistical purposes, the XLSB format is very beneficial considering the amount of memory used by an XLSX file. With respect to this, the malware authors enter their malicious code directly into the cell formulas, which are hidden.
- By changing the font color.
Ex: [Sheet White color & Font white color]. - By making hidden sheets with empty data but usually containing malicious contents.
Hidden Content:

Payload files:
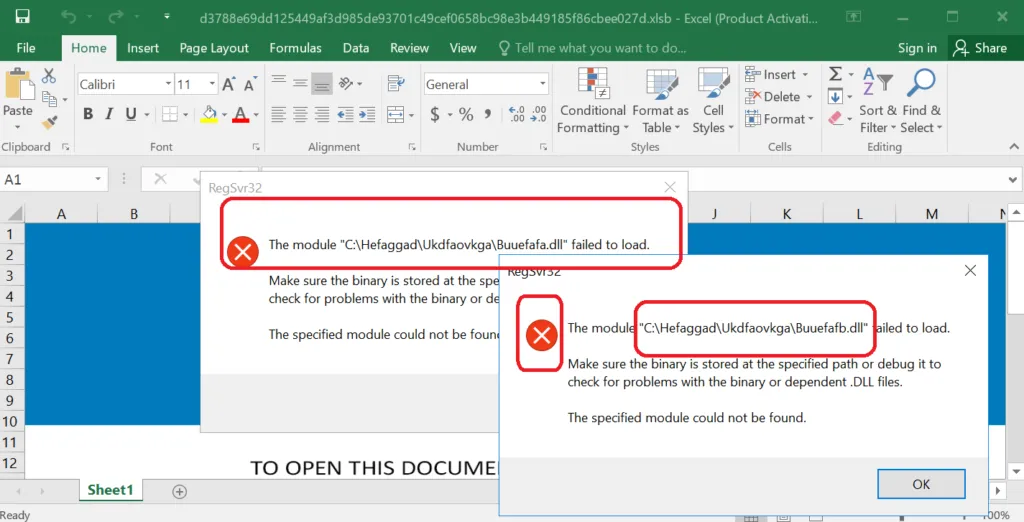
Once the user enables the content, then the payload files will execute on the victim’s computer.
Ready, Set, Qbot: Following an infection, Qbot acts rapidly to accomplish privilege escalation, and 10 minutes later, it can steal your e-mail, passwords, banking credentials and start a full-fledged reconnaissance scan in 30 minutes or less.
Using Regsvr32, payload files will be present in the C:\\ Drive:
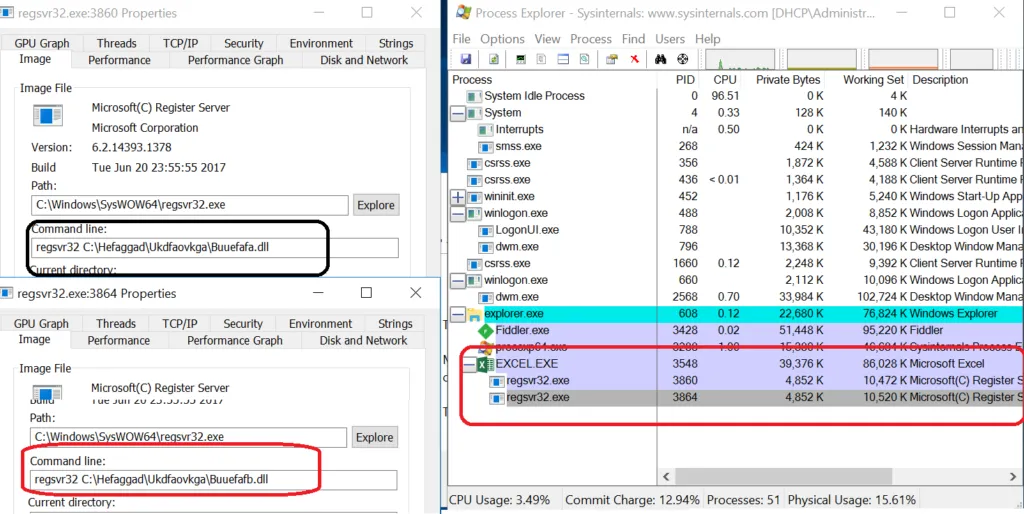
Payload files (in DLL format) – Dropped in the C Drive:
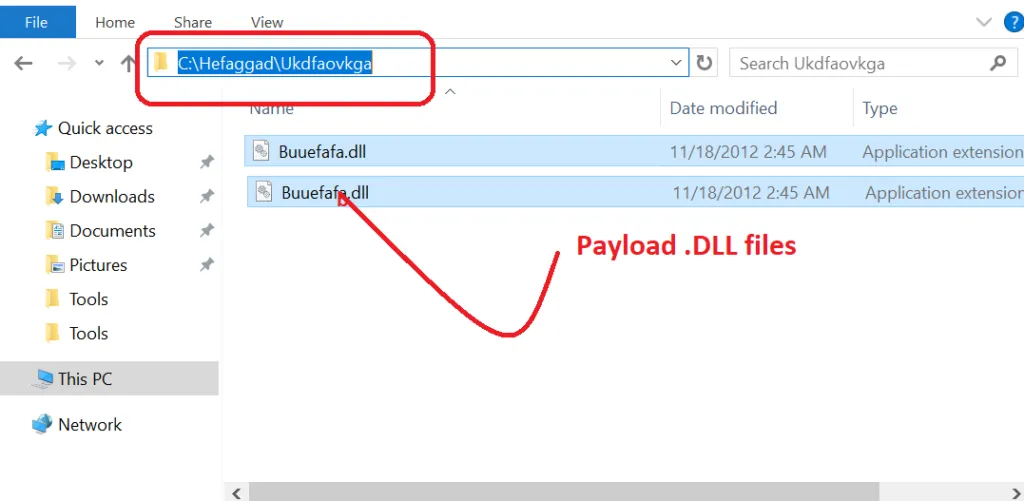
A brief description of anti-analysis techniques used by Qbot,
Instance 1: Encrypted Strings.
import idc
import idautilsdec_routine = 0x4065B7
enc_strings = 0x40B930
bytes_arr = 0x410120def decrypt_string(idx):
if idx >= 0x36F4:
return # out of bounds
res = “”
while True:
c = idc.get_wide_byte(enc_strings+idx) ^ idc.get_wide_byte(bytes_arr + (idx&0x3F))
if c == 0: break
res += chr(c)
idx += 1
return resxrefs = idautils.CodeRefsTo(dec_routine, 0)
for x in xrefs:
ea = idc.prev_head(x)
t = idc.get_operand_type(ea, 1)
if t == idc.o_imm:
idx = idc.get_operand_value(ea, 1)
dec = decrypt_string(idx)
idc.set_cmt(ea, dec, 1)
The majority of the embedded strings are encrypted and decrypted on demand by Qbot. The decryption routine takes one argument, the string index, and XOR function is used with an array until it encounters a null byte. Decrypting the strings can be aided by a framework such as IDAPython.
Instance 2: Simply put, it can stop functioning normally, when it’s being analysed.
Some of the interesting, anti VM features include,
(1) Qbot forcing an exception to exit when debugger is present,
(2) Blacklisting malware analysis tools such as fiddler, process hacker, ollydbg, windbg, wireshark, tcpview, resource hacker, and around 37 analysis tools have been blacklisted, by the malware authors.
(3) The “/C” parameter instructs QBot to spawn a new process thread, which aids in performing anti-analysis checks. Qbot executes assembly code with the keyword “VMXh,” which causes an exception when run in a Virtual Machine. If the exception handler is successful, it returns exit code 1, otherwise it returns 0. The parent process examines the spawned process’s exit code. If the exit code is 0, QBot continues to function normally; if the exit code is not zero (0), QBot is being analysed and thus ceases to function.
Initial IOC (Indicator of Compromise – HTTP)
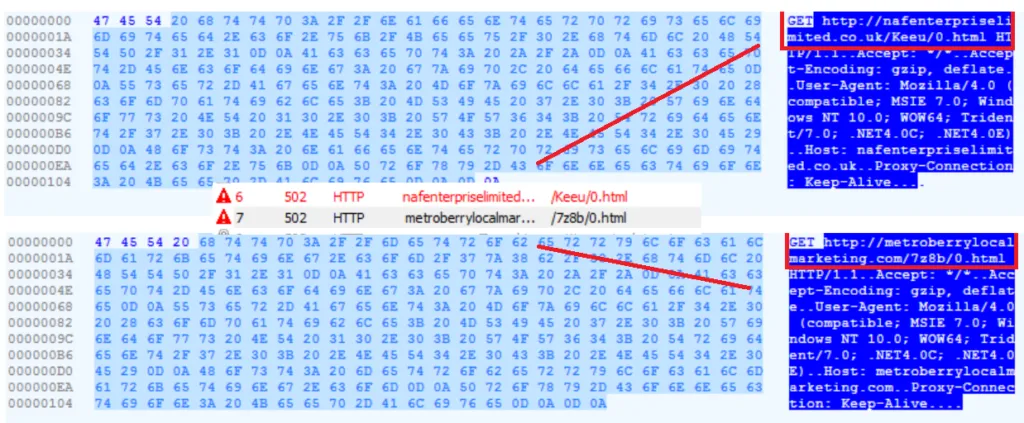
Once a victim is infected, the following process/functions are performed by Qakbot;
- Collecting information about the compromised host.
- Creating scheduled tasks (privilege escalation and persistence).
- Credentials harvesting & dumping (.exe access).
- Password stealing (from browser history and cookies).
- Targeting web banking links (web injects).
- Password brute forcing.
- Registry manipulation (persistence) to survive reboots.
- Replicating/relaunching it’s own copies through multiple instances using regsvr32.
- Process injection to conceal malicious actions.
Conclusion:
When the victim opens the latest variant’s HTML file, the javascript code (shellcode) is executed. The ZIP file includes a Windows shortcut file that looks like a text file. The most recent Qbot infections result in the execution of a loader program. As per our observations of Qbot’s recent operations, adversaries behind the distribution of Qbot have taken new approaches to take their evasion capabilities to the next level by imitating common formats with ZIP file extensions to lure targets with malicious attachments that install Qbot.
Not to forget, Qbot is also polymorphic in nature, which means it can change even after it has been installed on an endpoint. LMNTRIX CDC has observed that, Qbot has been recently used by Blackbasta, Blackbyte and Royal ransomware groups in 2023 for launching multi stage attacks after initial infection.
The threat actors behind the Qbot banking trojan keep constantly changing files, infection vectors and the dropper (payloads) in the newer versions of Qbot is constantly cycling through command-and-control servers. We consider Qbot as a highly dangerous malware, because of the combination of anti-analysis, anti-vm and polymorphic capabilities.
Indicators of Compromises [IOC] to detect Qakbot/Qbot;
| SHA256 |
| 77be6944abc910b26f861b4f7e92312b3587866f62df822dab82f263a2abc30e |
| 85568068da6d4822b42621edc3e3a2e2a9305f19aa83b1d6901a9b5b5d192427 |
| 543a6979f645d48d87b27bf4f4745542a0f259ad3f30958d94370d2a5a47e1dc |
| 2b25d6b0d7e175b21f6ef78f18a609b9f9099e3d83dd3d80475bedb2bbe501c0 |
| 2ae7122a31087d4af5cb9975fde6d875391b76f312003452eb22b7cd1c9ed7c6 |
| c0175a4b424083ecfb6ed9fafb2beb7be4e92f4937ef73948f2225a6161127ee |
| 881307774570c509616466363b86163f82b01248d3fb4f084598dcccb2f9b92a |
| f5d1f79c5ae796efffc2649fe6d61b1f6e1017061f573545e3038cb7729928c2 |
| 4c59f956bdf4569e2fade1dc737494fda7300933a75bb0b4b2da1651b84952dc |
| 72b2ba0f0a21cd30e9ecc18e2db0b8e6b553b81ea4b25450093d03420dca8bda |
| 59558951a8f67deb88d7aba394c10e5cc1ff8034526c2abce74ca98be8288ce2 |
| f41c34247b99d977d027a2d71b6d5e9f4538594e075aa99aa8cede3ca7c0b68b |
| bb15f44ddfd5061d32da1ad3441643d4b2a3ae2a29e15b994b47cd6544a4464a |
| f58f33af6fcd57fd5696621fb6363a110444212d2e4cf414c6b5733351630b6b |
| 3463615b1e091e9d28c724181f6e622e437d61c20375877dbae882d0571c4037 |
| c94f22c56e964d49947002774fc30ba887f72bd458bae9a9fb959cc475b1001a |
| d24d58d48ac759c504408b26ec6c80b9165042758b001b1f84682adc96162c90 |
| 02c8410377d4ebe450bab9f1ebff93363876433995868def38b16f3b0af0e11c |
| 5f3dea46780846464cdb3386fd7a1a24881964b91cf307765af46db3ed328c70 |
| 0da5eff6246fc7f33a324833274fc402abf69864195b7b505ec15d7ca2bcc7ac |
MITRE ATT&CK Tactics & Techniques used by QBot:
| ID | Tactics | Technique |
| TA0001 | Initial Access | T1566.001 – Spearphishing Attachment T1566.002 – Spearphishing Link |
| TA0002 | Execution | T1027 – Obfuscated Files or Information T1059.005 – Visual Basic T1204.002 – Malicious File |
| TA0003 | Persistence | T1053.005 – Scheduled Task T1547.001 – Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | T1053.005 – Scheduled Task |
| TA0005 | Defense Evasion | T1027.002 – Software Packing T1055 – Process Injection T1055.012 – Process Hollowing T1497.001 – System Checks |
| TA0006 | Credential Access | T1003 – OS Credential Dumping T1110.001 – Password Guessing T1555.003 – Credentials from Web Browsers |
| TA0007 | Discovery | T1016 – System Network Configuration Discovery |
| TA0011 | C&C Server | T1071.001 – Web Protocols T1090 – Proxy T1090.002 – External Proxy |
This lab article is a living blog post… We will update this blog post, as appropriate.


