
STRRAT is a multi-functional Java-based Remote Administration Trojan (RAT) which is capable of stealing login credentials saved on browsers, logging keystrokes, and remotely controlling infected systems running on Windows platform. Also, it has the capability of servicing ransomware attacks which render files stored on victims’ computers inaccessible. The sample we examined attempts to target German user base predominantly.
Targeted OS – MS Windows Platform
Target Geography: Austria, Canada, Germany, Spain, UK, USA
Languages used by the authors – Java, VBS (Visual Basic) & Powershell
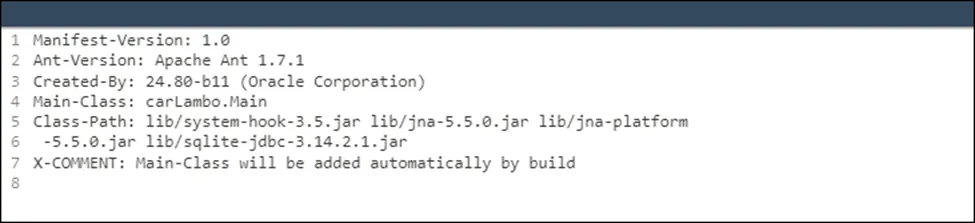
Static Analysis of STRRAT (JAR) sample
Java Version Details of sample examined
MD5 Hash – 5f4dcc3b5aa765d61d8327deb882cf99
SHA256 – c7ed1cec47b5f8d575e739d4c77d86a6222a64539e5870229fc4488bb0b50b05
Here are additional insights about this campaign after examining the source code:
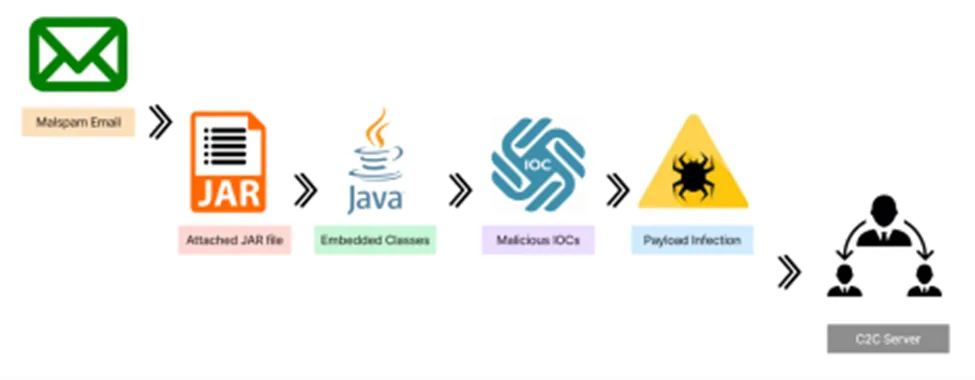
- The attackers behind this campaign used compromised email accounts to send out spam messages, including an image that was portrayed as a PDF attachment or any blurred images.
- When an unsuspecting recipient opens the image, the malicious code makes a connection to a domain for downloading STRRAT payload on the victim’s machine.
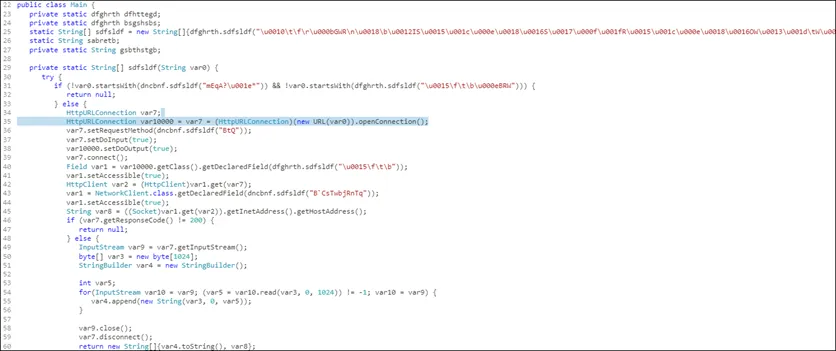
- From the image below, it can be inferred that a ‘remote’ command is used to initiate a ‘RDP’ connection to the system and enable remote control of the mouse and keyboard input.
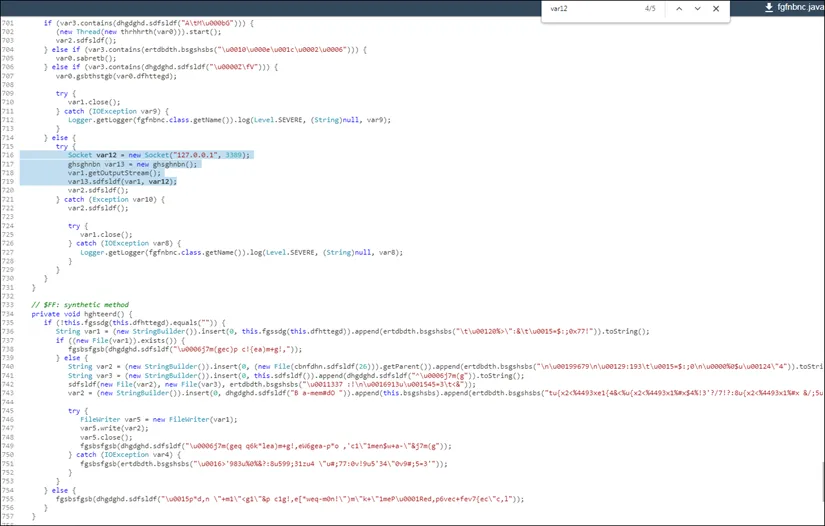
- The latest version of STRRAT (v1.5) is more obfuscated and modular than the previous one. It supports various features such as logging keystrokes, collecting browser passwords, and running remote commands and PowerShell.
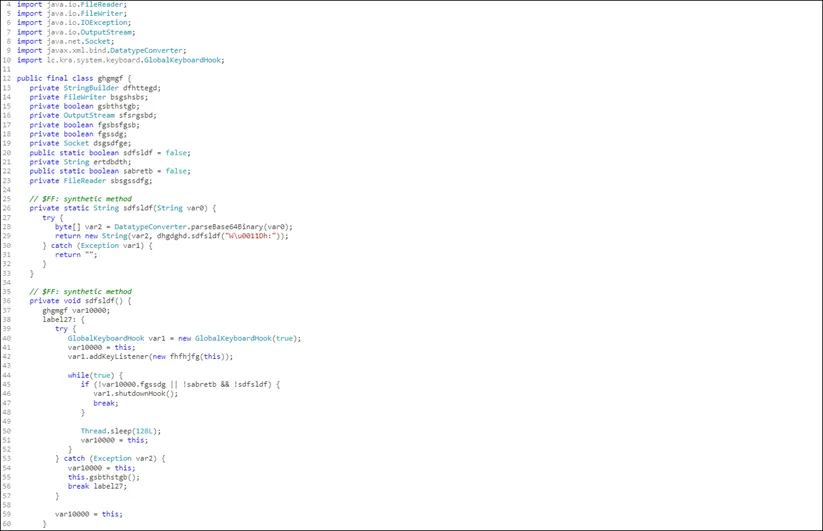
- The RAT focuses on stealing credentials of browsers (IE, Chrome, Firefox) and email clients (Outlook, Thunderbird, Foxmail).
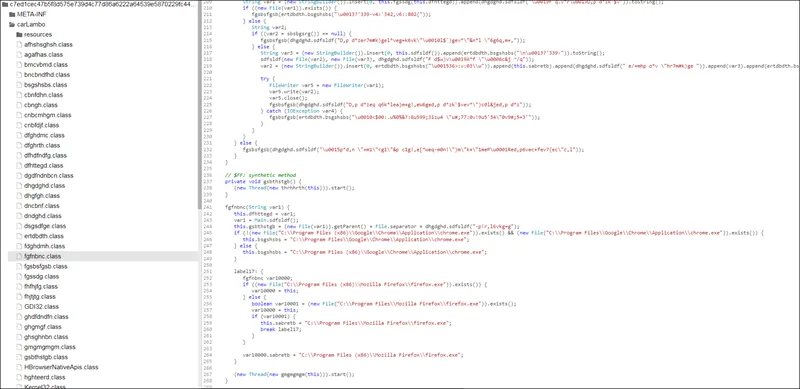
Dynamic Analysis of STRRAT (JAR) sample
Infection Chain
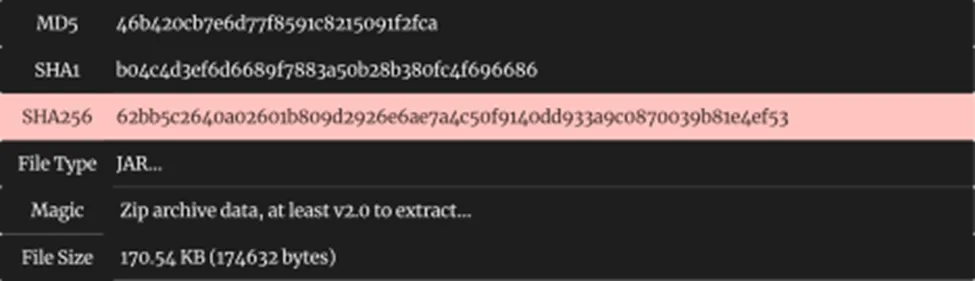
Sample Information
Threat Name: STRRAT | Classification: Dropper| Category: Dropper / Remote Administration Tool
Technical Analysis of JAR file;
JAR (aka Java Archive) is a file format that aggregates several files into one file. Let’s begin with our sample.
This Java environment differs from other programming environments in that the Java compiler does not generate machine code for a hardware-specific instruction set. Instead, the Java compiler converts Java source code into Java virtual machine instructions, which Java class files store. Basically, we can use JAR files to store class files. The class file does not target a specific hardware platform, but instead targets the Java virtual machine architecture.
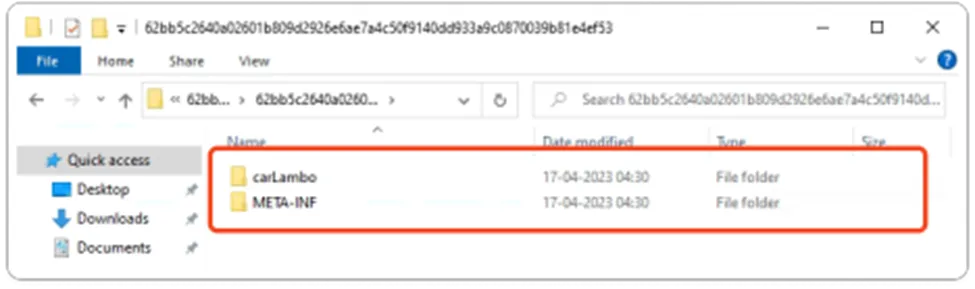
Java Class files
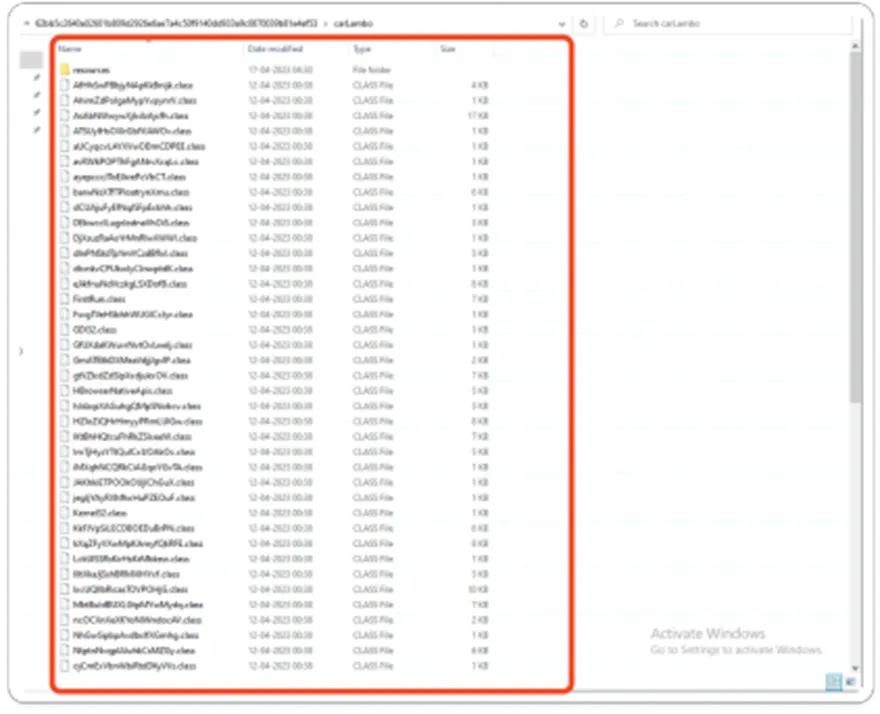
Importance of Class files
Java class files are stream files that are produced when a source file is compiled by the Java compiler. The class file contains tables that describe each field and method of the class. The file also contains the byte-codes for each method, static data, and descriptions that are used to represent Java objects.
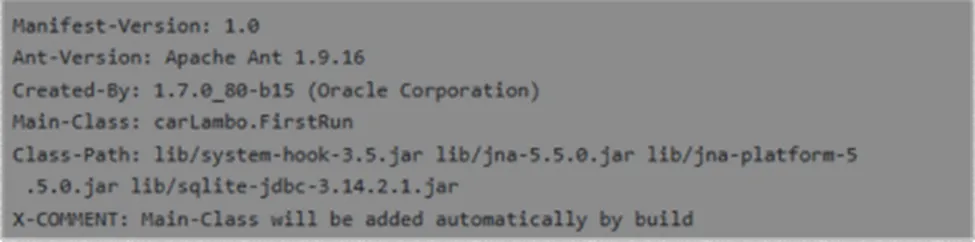
Manifest – JAR File info
Manifest is an important one where any executable JAR file that contains a stand-alone application, a Main-Class attribute should exist that provides the name of the first piece of code for the Java Runtime Environment (JRE) to invoke when the application is run.
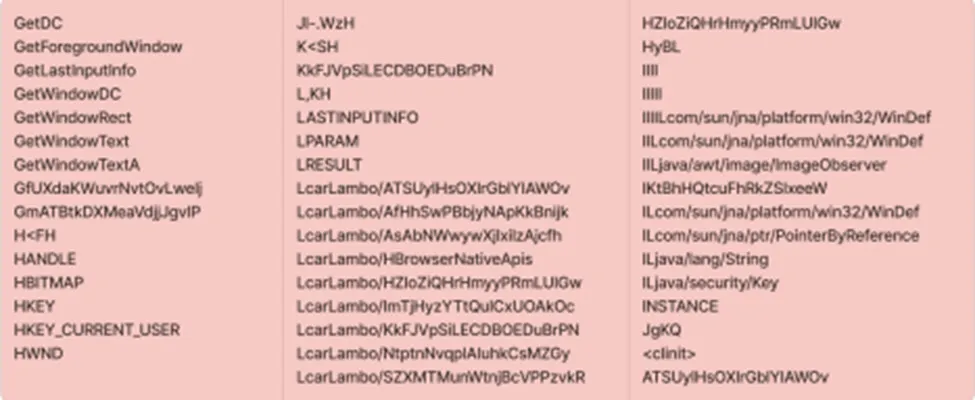
Suspicious Strings
Process Tree for STRRAT
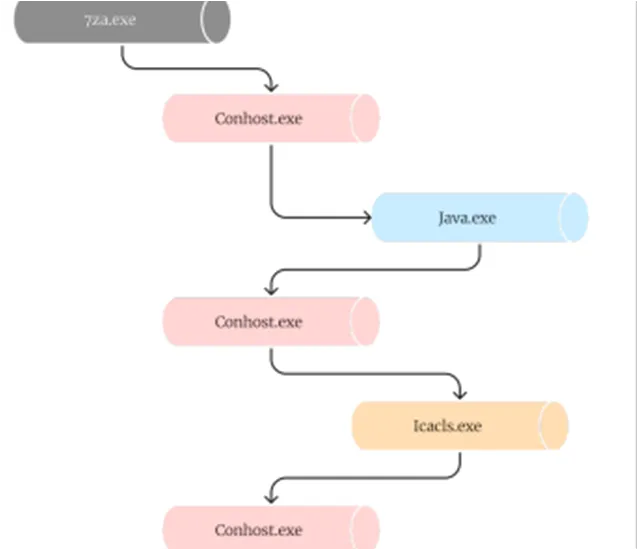
Once the system is infected, here are few activities carried out by STRRAT,
STRRAT gathers the following information, upon execution,
- Username
- System OS Version
- System Architecture
- Presence of antivirus software
- Version of STRRAT installed/used
- Geolocation of the victim (i.e.; Country)
- Whether STRRAT is already installed or not?
- Check the Browsing History & System idle time
Appendix A – Commands gleaned from deobfuscated java source code of STRRAT
| Remote Commands – STRRAT | Description of Command |
| reboot | Reboot the device |
| shutdown | Shutdown the device |
| uninstall | Remove the malware from the device |
| disconnect | Disconnect the device from the C2 server |
| down-n-exec | Download a file from a URL and execute it |
| update | Update the malware |
| up-n-exec | Upload a file directly to the device from the C2 server and then execute it |
| remote-cmd | Remote command prompt |
| power-shell | Remote PowerShell prompt |
| file-manager | View files on the device |
| processes | Lists running processes on the device |
| startup-list | Lists startup items enabled on the device |
| remote-screen | Remotely view the device screen |
| rev-proxy | Use the device as a reverse proxy server |
| hrdp-new | Utilize a Hidden RDP, enable a Remote Desktop client |
| hrdp-res | Utilize a Hidden RDP while taking argument |
| Keylogging | Description of Command |
| keylogger | Start keylogging on the device, send logs to the C2 server |
| o-keylogger | Start offline keylogging on the device, save the logs to the disk |
| Credential Stealer | Description of Command |
| chrome-pass | Extract Chrome passwords from device and send to C2 |
| foxmail-pass | Extract Fox mail passwords from device and send to C2 |
| outlook-pass | Extract Outlook passwords from device and send to C2 |
| fox-pass | Extract Firefox passwords from device and send to C2 |
| tb-pass | Extract Thunderbird passwords from device and send to C2 |
| ie-pass | Extract Internet Explorer passwords from device and send to C2 |
| all-pass | Extract all passwords from device and send to command and C2 |
Appendix B – Indicators of Compromise for STRRAT
Network Indicators
hxxp[://]wshsoft[.]company/jre7[.]zip
hxxps[://]pastebin[.]com/raw/Jdnx8jdg
hxxps[://]pastebin[.]com/u/wshsoft
pluginserver[.]duckdns[.]org
hxxp[://]str-master[.]pw/strigoi/server/ping[.]php?lid=
moregrace[.]duckdns[.]org
hxxp[://]jbfrost[.]live/strigoi/server/?hwid=1&lid=m&ht=5
palaintermine[.]duckdns[.]org
ip-api[.]com/json/
hxxp[://]wshsoft[.]company/multrdp[.]jpg
Host Indicators
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ntfsmgr
64578lock.file
3219lock.file
Scheduled Task – “Skype”
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System /v dontdisplaylastusername = 1
STRRAT JAR IOC
hXXp://jbfrost[.]live/strigoi/server/?hwid=1&lid=m&ht=5
carLambo
HBrowserNativeApis
config.txt
loorqhustq
MITRE ATT&CK Tactics & Techniques for STRRAT
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | Windows Scripting – JAR Exploitation for Client Execution |
| TA0003 | Persistence | Services File Permissions Weakness Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Scheduled Task |
| TA0005 | Defense Evasion | Modify Registry Obfuscated Files or Information Virtualization Evasion Technique |
| TA0006 | Credential Access | Credentials in Registry Credentials in Files Credential Dumping |
| TA0007 | Discovery | System Network Configuration Discovery Process Discovery File and Directory Discovery Query Registry |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols Standard Application Layer Protocol Standard Cryptographic Protocol etc., |


