
In its legitimate form, AutoIT is an incredibly handy automation language used for scripting Windows-based applications. In its malicious form, it is used to create malware with a variety of functionality. Once an AutoIT trojan has infected a victim’s PC, it can alter default browser settings and perform ad-injection, copy itself to USB memory sticks, delete anti-virus software, keep track of browsing activities, add unwanted extensions/plugins, and redirect users to unknown or malicious websites.
All in all, AutoIT trojans are a nasty ‘jack-of-all-trades’ malware. Variants have been used to download further malicious software on the infected PC and even grant attackers remote access – effectively operating as a back door.
Distribution
Just as AutoIT trojans have various functionalities, this multi-dexterity extends to distribution techniques.
The latest variant (which we’ll analyse today) has been distributed by spoofed e-mail messages, malicious links in Yahoo Messenger chats, or via malicious Java Script embedded on websites which allow remote code execution.
As if that weren’t bad enough, AutoIT also has the ability to copy itself to external or removable drives as a file called ‘system.exe’.
When successfully executed, it checks the currently running processes for the following programs:
Microsoft Management Console (mmc.exe)
Microsoft Restore Console (rstrui.exe)
Registry Editor (regedit.exe)
System Configuration utility (msconfig.exe)
Task Manager (taskmgr.exe)
If any of these programs are found running, the Trojan restarts the computer.
Further, if any of the following processes are discovered, they will be terminated:
cmd.exe
handydriver.exe
kerneldrive.exe
nod32krn.exe
nod32kui.exe
winsystem.exe
Wscript.exe
File Details
| File Type | Portable Executable (.exe) file |
| Md5 hash | ec721f6f111aae46f2ede8f70e435cc4 |
Static analysis
The sample we’re analysing has an icon showing it as a document, but when we view its header it was found to be a proper .exe sample:

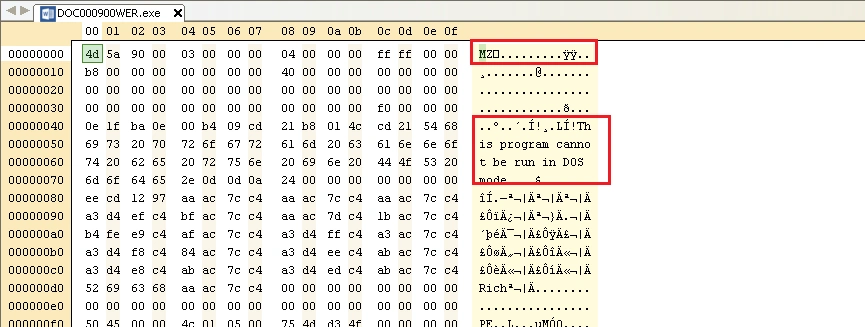
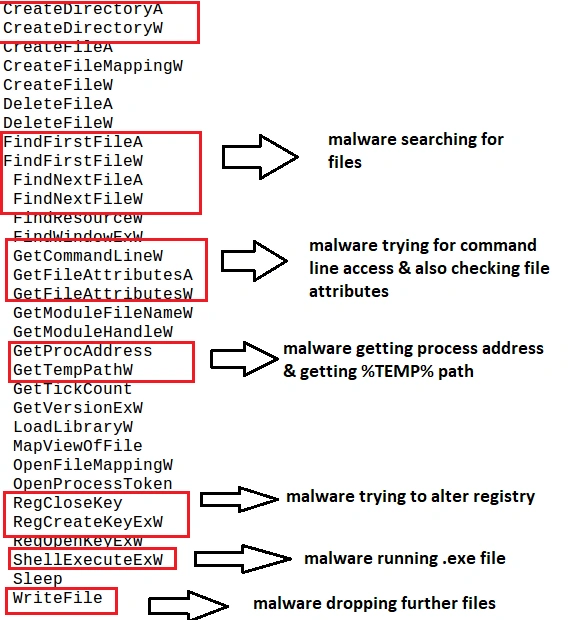
Static analysis uncovered the following suspicious API calls, all of which indicate malicious properties:
After opening the file with winrar, we found it was in fact a combination of multiple file types including document, image, and DAT:

Below are more suspicious characteristics we discovered:
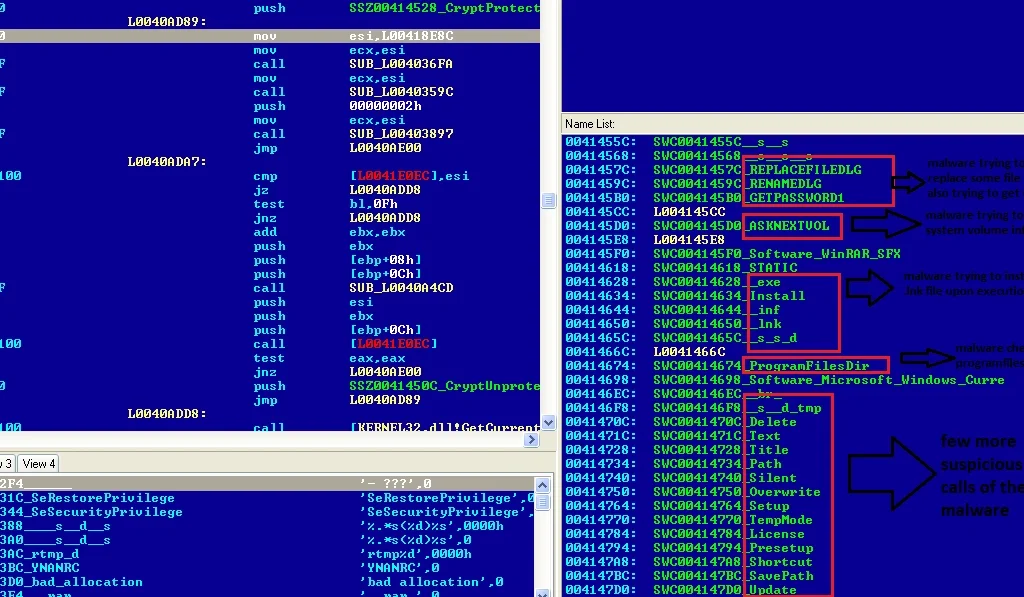
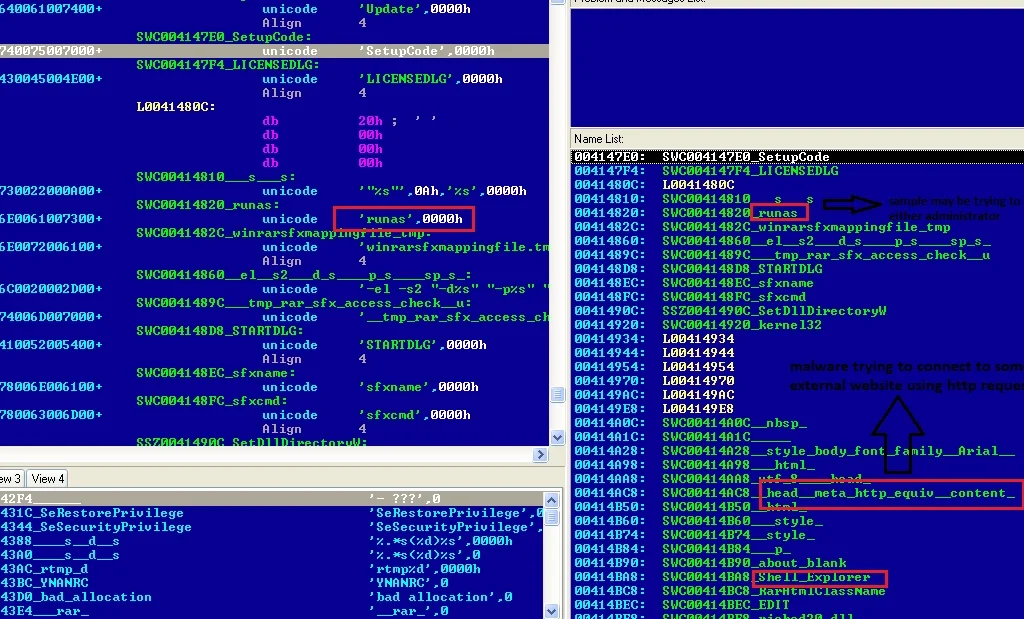
Dynamic analysis
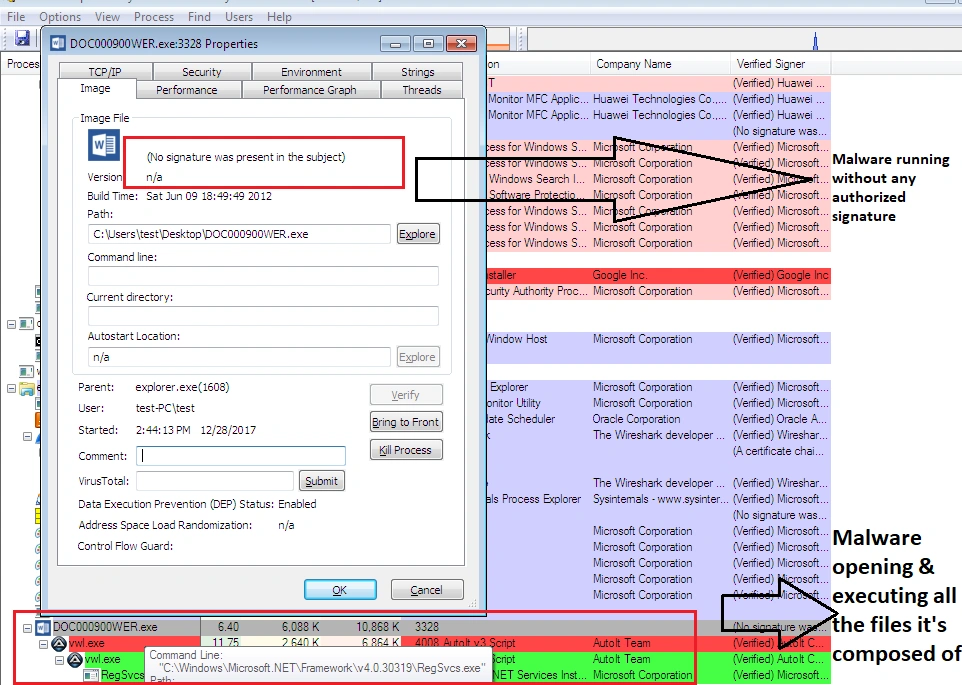
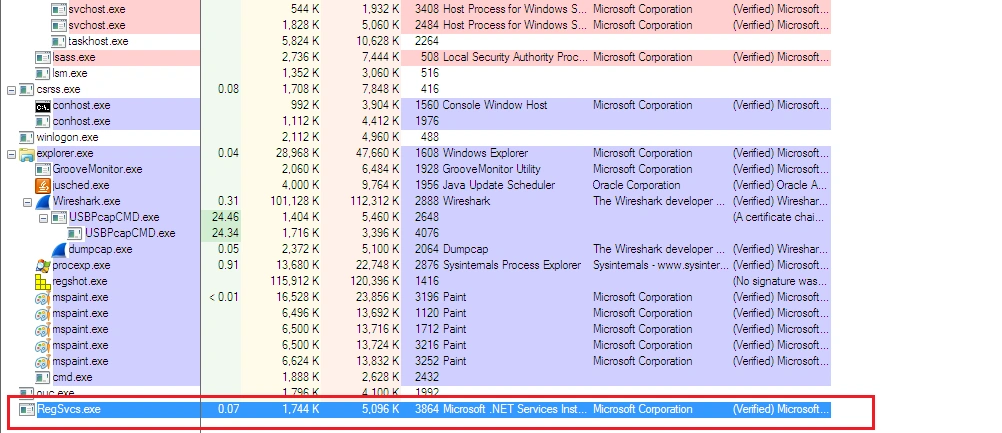
After executing the sample in a dedicated malware analysis environment, we found AutoIT initiating various child processes including ‘vwl.exe’ and ‘RegSvcs.exe’:
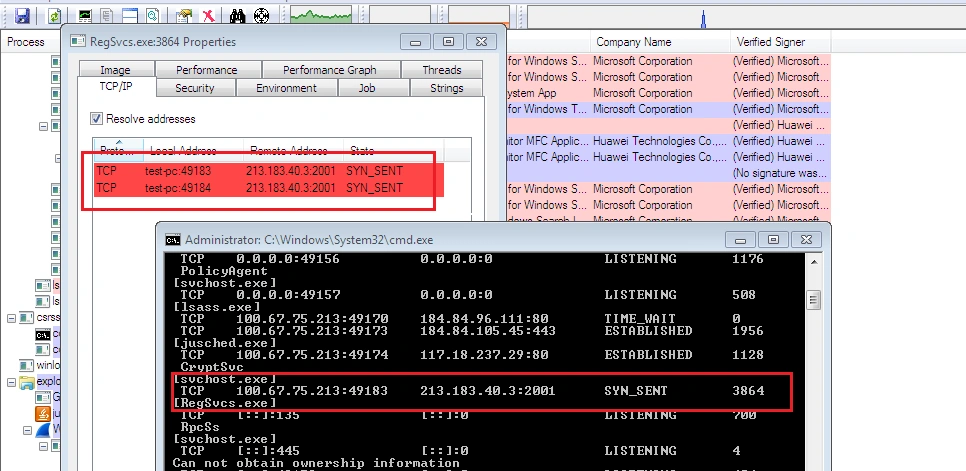
Within a few minutes, all processes except Regsvcs.exe were killed. This process maintains a persistent connection to the IP address “213.183.40.3” over port “2001”:
Trojans commonly access this port to gain backdoor entry into victim PCs:
Throughout the infection cycle, the following files were dropped:
• C:\Users\<user-name>\AppData\Local\Temp\77923311\but.xl
• C:\Users\<user-name>\AppData\Local\Temp\77923311\daa.dat
• C:\Users\<user-name>\AppData\Local\Temp\77923311\dal.ico
• C:\Users\<user-name>\AppData\Local\Temp\77923311\dhu.dat
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ebf.mp4
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ebn.mp3
• C:\Users\<user-name>\AppData\Local\Temp\77923311\evk.jpg
• C:\Users\<user-name>\AppData\Local\Temp\77923311\evk.mp3
• C:\Users\<user-name>\AppData\Local\Temp\77923311\fip.mp4
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ftr.dat
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ghk.ico
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ghm.ppt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\gib.dat
• C:\Users\<user-name>\AppData\Local\Temp\77923311\glt.icm
• C:\Users\<user-name>\AppData\Local\Temp\77923311\gph.ppt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ini
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ixi=xob
• C:\Users\<user-name>\AppData\Local\Temp\77923311\jcj.bmp
• C:\Users\<user-name>\AppData\Local\Temp\77923311\jjb.docx
• C:\Users\<user-name>\AppData\Local\Temp\77923311\jpi.txt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\jrj.mp3
• C:\Users\<user-name>\AppData\Local\Temp\77923311\kma.icm
• C:\Users\<user-name>\AppData\Local\Temp\77923311\lci.docx
• C:\Users\<user-name>\AppData\Local\Temp\77923311\mnb.dat
• C:\Users\<user-name>\AppData\Local\Temp\77923311\mto.docx
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ngb.mp4
• C:\Users\<user-name>\AppData\Local\Temp\77923311\omu.bmp
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ooc.icm
• C:\Users\<user-name>\AppData\Local\Temp\77923311\pjq.pdf
• C:\Users\<user-name>\AppData\Local\Temp\77923311\qbc.txt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\qom.jpg
• C:\Users\<user-name>\AppData\Local\Temp\77923311\rlc.ppt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\sdo.mp4
• C:\Users\<user-name>\AppData\Local\Temp\77923311\sug.txt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\tnl.icm
• C:\Users\<user-name>\AppData\Local\Temp\77923311\tte.txt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\twl.ppt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ukj.mp3
• C:\Users\<user-name>\AppData\Local\Temp\77923311\uko.txt
• C:\Users\<user-name>\AppData\Local\Temp\77923311\unm.mp3
• C:\Users\<user-name>\AppData\Local\Temp\77923311\ute.docx
• C:\Users\<user-name>\AppData\Local\Temp\77923311\vwl.exe (md5: 71d8f6d5dc35517275bc38ebcc815f9f)
• C:\Users\<user-name>\AppData\Local\Temp\77923311\wux.bmp
• C:\Users\<user-name>\AppData\Local\Temp\77923311\wxl.pdf
• C:\Users\<user-name>\AppData\Local\Temp\77923311\xxh.ppt
The following folders were created:
• C:\Users\<user-name>\AppData\Local\Temp\77923311
• C:\Users\<user-name>\AppData\Roaming\remcos
And the following registries were added in order to maintain persistence:
• HKU\S-1-5-21-3006570754-2424674848-4088610848-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU\f: “C:\Users\<user-name>\AppData\Local\Temp\77923311\\1”
• HKU\S-1-5-21-3006570754-2424674848-4088610848-1000\Software\Microsoft\Windows\CurrentVersion\Run\WindowsUpdate: “C:\Users\<user-name>\AppData\Local\Temp\77923311\vwl.exe C:\Users\<user-name>\AppData\Local\Temp\77923311\IXI_XO~1”
Command and control
External connection to “213.183.40.3:2001”.
Indicators of compromise
Malware executable: ec721f6f111aae46f2ede8f70e435cc4
Vwl.exe: 71d8f6d5dc35517275bc38ebcc815f9f
IP address: 213.183.40.3
Registry values added:
• HKU\S-1-5-21-3006570754-2424674848-4088610848-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU\f: “C:\Users\<user-name>\AppData\Local\Temp\77923311\\1”
• HKU\S-1-5-21-3006570754-2424674848-4088610848-1000\Software\Microsoft\Windows\CurrentVersion\Run\WindowsUpdate: “C:\Users\<user-name>\AppData\Local\Temp\77923311\vwl.exe C:\Users\<user-name>\AppData\Local\Temp\77923311\IXI_XO~1”
Mitigation/protection
If you’re unlucky enough to fall victim to AutoIT trojan, the below steps will remove the malware:
• Reboot your system into Safe Mode with Networking;
• Enter the following registry areas;
o [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
o [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
o [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\
• Check for the display name “backgroundcontainer” and delete it
• Go to the location: C:\Users\{username}\AppData\Local and delete the folder “uqgtmedia”
• Open the file C:\Windows\System32\drivers\etc\hosts and remove any suspicious IP or domain belonging to some malware or ransomware


