
The Babuk Ransomware Russian speaking Cyber Criminal gang has been operating and actively infecting networks for the past year while adopting the multiple extortion model for its victims. This is a similar trend used by other Ransomware gangs in recent times.
The Babuk Ransomware gang operational model can be considered an enterprise model where multiple threat actors are involved with a promise of higher profits in return to perform various tasks of the infection cycle. This includes adding a dedicated negotiation team to pressurise the victims and threaten them with data leak consequences in case of non-payment of ransom.
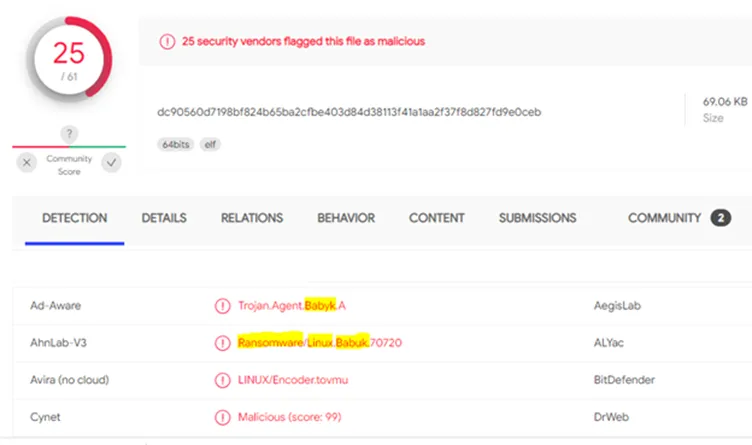
LMNTRIX researchers while performing investigation on this gang encountered an interesting variant of Babuk Ransomware which targets Linux machines. The sample found is a 64 bit ELF file and many AV vendors have started identifying it as “Ransomware Linux Babyk”. This ransomware variant is known for targeting a wide array of industries and not tied to any specific targets.
Sample details
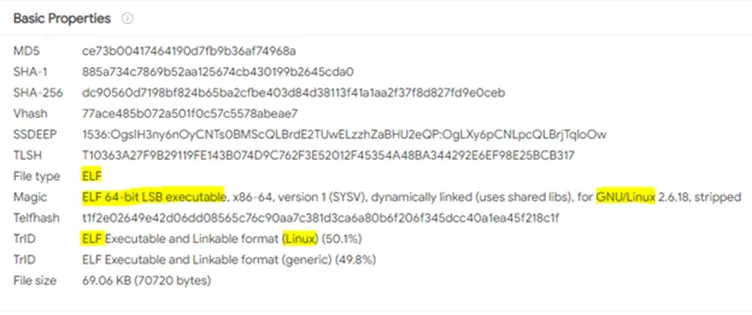
File Hash: dc90560d7198bf824b65ba2cfbe403d84d38113f41a1aa2f37f8d827fd9e0ceb
File Size: 69 KB
File Type: ELF
Code Analysis
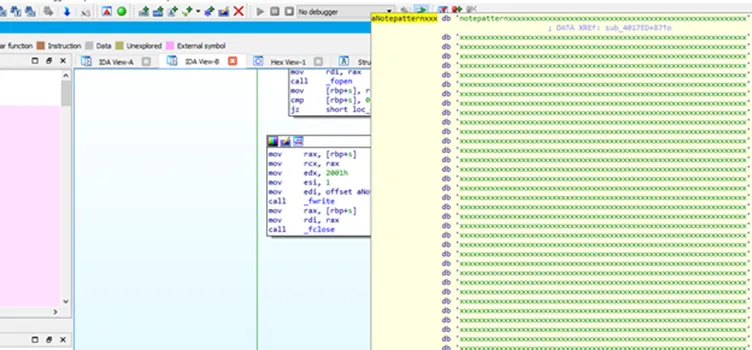
During basic static analysis, it can be seen that the sample contains code to encrypt the content, looking for specifying file types (mostly related virtual images), and ransom note (how_to_restore_your_files.txt).
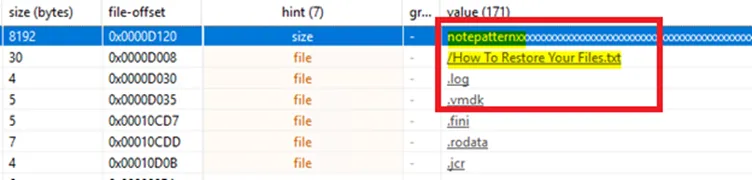
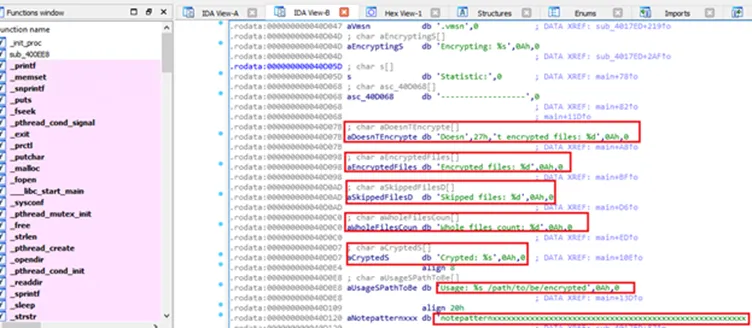
Further, on disassembling there were interesting strings and code snippets which is mentioned in the below snapshot:
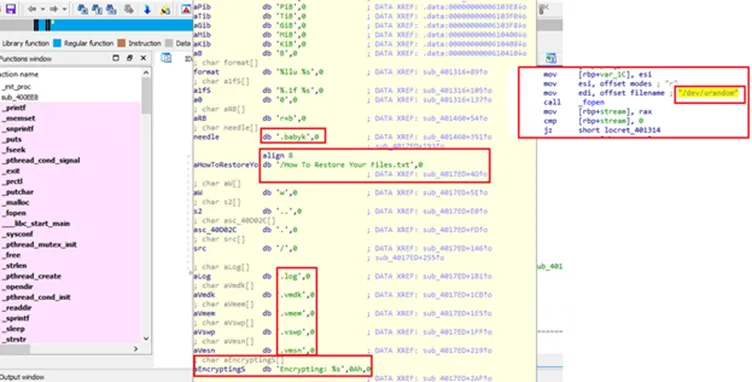
The disassembled code clearly stats out the flow like file extension to be added as ‘.babyk’, dropping the ransom note, looking for virtual image disks (known for production server holdings and it is key differentiator for a server and desktop machines). This variant has the code for getting the statistics of encrypted files, skipped files, and whole files count. Obvious reason behind these statistics will be the ransomware actor may show this data as an added threat, where they threaten its victims to leak the data dump in dark web or to their competitors in the market.
As the security researchers highlighted in various analysis of Bauk Ransomware that the ransomware variant will usually have the subroutines to read the directories and proceed for encryption of the files in them. Such a similar code is seen in this particular variant as well.
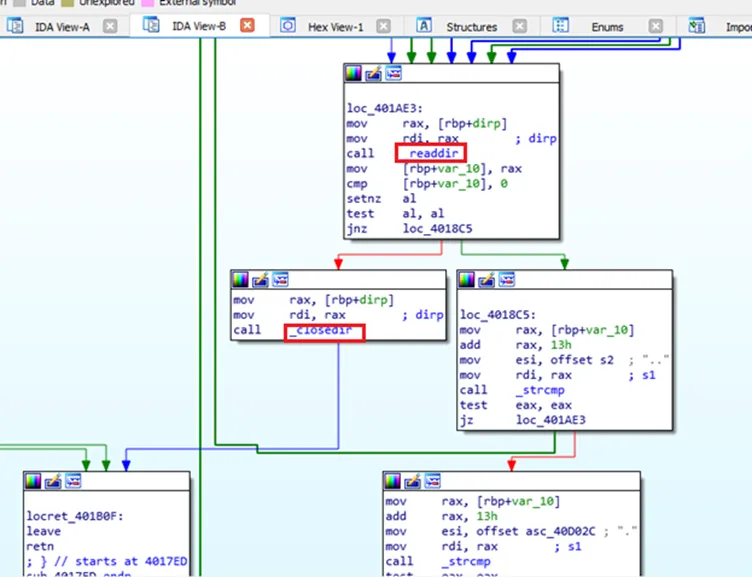
Further while reading from the directory, the malware code looks for string comparison using strcmp subroutine to check for the watermark of Babyk. If the Babyk string is present in the file extension, then the specimen won’t proceed for the encryption as it meant to be already infected with the same variant.
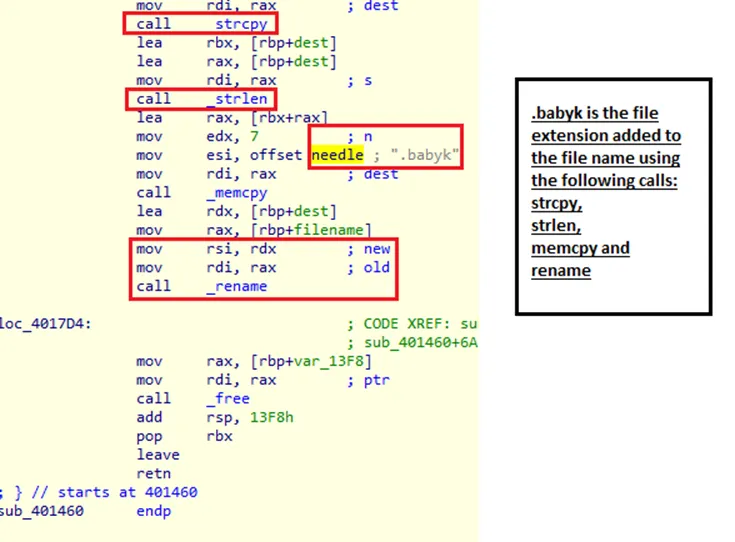
In case of absence of babyk string watermark, the subroutine proceeds for encryption as well as renaming the files.
Yara Rule
rule Ransom_linux_babyk
{
meta:
description = “Rule to detect Babuk Linux Variant”
malware _ family = “Ransom:Win/Babuk”
malware _ type = “Ransom”
mitre _ attack = “T1027, T1083, T1057, T1082,
T1129, T1490, T1543.003”
strings:
$restore= “/How To Restore Your Files.txt”
$linux_1= “/lib64/ld-linux-x86-64.so.2”
$ransom= “.babyk”
$linux_2= “/dev/urandom”
condition:
$restore and $ransom and ($linux_1 or $linux_2)
}
————————————————-xxxxxxxxxxxxxxx———————————————


